
- Introduction to AWS
- Definition of AWS Security Groups
- Types of AWS Security Groups
- Default AWS Security Groups
- Manage security groups with AWS Firewall Manager
- Best Practices of AWS Security Groups
- Applications of Security Groups in AWS
- Benefits of AWS Security Groups
- Security Group vs Network ACL
- Conclusion
Introduction to AWS
AWS (Amazon Web Services) is an extensive, ever-converting cloud computing platform provided through Amazon that consists of infrastructure as a service (IaaS), platform as a service (PaaS), and packaged software program as a service (SaaS) offerings. AWS offerings can offer corporations gear like compute clusters, database storage, and content material transport offerings. Amazon Web Services is a complete and extensively followed cloud computing platform that provides several services, such as computing power, storage, databases, networking, device learning, and security. AWS offers scalable, flexible, and cost-powerful answers for companies of all sizes, allowing them to construct and set up programs without the need for on-premises infrastructure. With information facilities dispensed throughout more than one area worldwide, AWS guarantees excessive availability, reliability, and security. Its pay-as-you-pass pricing version permits groups to optimize prices whilst leveraging superior cloud technologies. AWS is used throughout diverse industries, from startups to enterprises, to aid virtual transformation and innovation.
Definition of AWS Security Groups
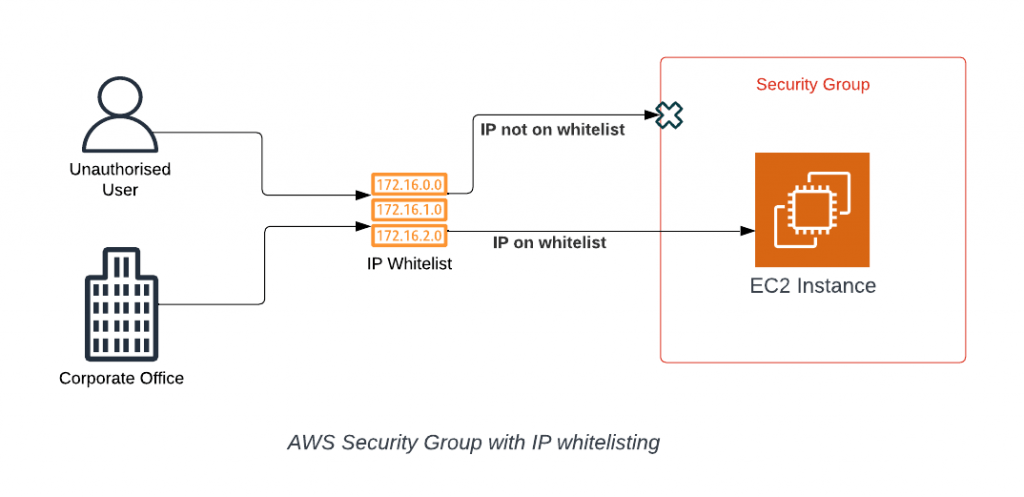
An AWS safety institution enables to government incoming and outgoing site visitors on your AWS EC2 safety institution times by performing as a digital firewall. The float of site visitors to and out of your example is managed through inner and outside guidelines, respectively. Every Security Group capability in addition to a firewall consists of a fixed set of guidelines that clear out site visitors coming into and exiting the Amazon Web Services Architecture EC2 times. As formerly stated, safety businesses are related to EC2 times and offer safety on the port and protocol to get the right of entry to levels. Normally, the firewall has a `Deny rule,` however the SG has a “Deny All” that permits statistics packets from the supply IP to be dropped if no rule is assigned to them. When you create a safety institution, you may assign it to a selected digital personal cloud VPC. It`s additionally an amazing concept to present every institution a call and outline in order that they may be determined without problems inside the account menus. It`s additionally really well worth noting that after developing a safety institution, make certain it`s assigned to the VPC it’s speculated to defend to keep away from errors.
Types of AWS Security Groups
- These are currently divided into two types:EC2-Classic, EC2-VPC
- If you`re acquainted with Amazon EC2, you`ve in all likelihood heard of a safety institution. However, you can’t use a safety institution created for EC2-Classic in EC2-VPC or vice versa. Even when you have a comparable safety rule to your EC2, you need to create one for your VPC.
- There are a few similarities and variations among those kinds of safety agencies. You can most effective create inbound policies with EC2-Classic, however, you may create each inbound and outbound policies with EC2-VPC.
- You can’t alternate the safety institution of an example that has already been launched. However, with an EC2-VPC, Amazon Web Services DevOps institution of an example that has already been launched. With an EC2-VPC, however, you may alternate the assigned institution.
- You also can not upload policies to EC2-Classic safety agencies. It enables you to stabilize your cloud surroundings by permitting you to manipulate what visitors are permitted into your EC2 machines. You can use Security Groups to make certain that every visitor at the example stage flows most effectively via your described ports and protocols.
- When you release an example on Amazon EC2, you need to assign it to a selected safety institution. You can upload policies to every safety institution that lets visitors to or from precise offerings and times.
- Security institution policies, like whitelists, are continually permissive. It isn’t always viable to make policies that limit access. For example, visitors can be directed from an Elastic Load Balancer (ELB) to a subnet containing net servers. You can specify that ELB is the most effective accepted supply to your AWS Security Group.
- Because safety agencies are stateful, if an inbound request is successful, the outbound request may also be successful.
Are You Interested in Learning More About AWS ? Sign Up For Our AWS Online Training Today!
Default AWS Security Groups
Every digital non-public cloud has a default safety institution, and every example you release can be related to it. This manner that until you are taking action, consisting of associating a special AWS Course safety institution, all your times can be related to the default safety institution. All protocols and ports starting from times inside the equal safety institution can be allowed through default. Additionally, all visitors to zero.zero.zero.zero and::/zero can be authorized. You are unfastened to adjust those policies as you spot fit. However, you can’t delete a default safety institution from your VPC.
Manage security groups with the Firewall Manager
Firewall Manager is a safety control provider that permits you to centrally configure and manipulate firewall guidelines throughout your AWS Applications organization bills and programs. Firewall Manager makes it simpler to convey new programs into compliance with the aid of imposing a not unusual place set of baseline safety guidelines and making sure that overly permissive guidelines generate compliance findings or are robotically removed. With Firewall Manager, you’ve got an unmarried provider to construct firewall guidelines, create safety regulations, and put in force guidelines and regulations throughout your whole infrastructure in a consistent, hierarchical manner.
The firewall Manager`s safety organization talents are divided into 3 vast categories:
- Create and observe AWS accounts and aid baseline safety groups.
- Examine and cast off unused or redundant safety groups.
- Audit and manage safety organization guidelines to discover overly permissive and high-danger guidelines.
- Your VPC must have waft logging enabled. These logs offer full visibility into the visitors who pass via the VPC. Flow logging can help you detect difficult visitors and offer precious insights. It also can help you resolve entry and safety issues. For example, the waft log can display you whether or not any safety corporations might be overly permissive.
- Large port degrees must be averted in EC2 safety corporations. In this case, vulnerabilities are effortlessly uncovered and exploited.
- Allow the simplest restrained get entry to to RDS cases. RDS will log failed login tries however will now no longer save them from taking place again. If a case is left open to the internet, it’s far more susceptible to brute-pressure login attacks. You must additionally restrict entry to Amazon Cognito clusters.
- Use discrete safety corporations much less frequently to keep away from misconfigurations that would cause account compromise.
- Limit outbound ports to get entry to unique ports or locations simplest. Allowing unrestricted inbound entry to unusual ports is likewise now no longer recommended.
- Authorize no get entry to ports along with 445, which is usually used for CIFS (Common Internet File System). Allow FTP transfers simplest via ports 20 or 21, and simplest once they were constrained to required entities.
- Maintaining those first-class practices manually may be tough in large-scale AWS environments, or in conditions wherein builders and alertness proprietors are often deploying new programs. Organizations can cope with this difficulty by imposing centralized guardrails.
- At AWS, we see safety as an enabler of improvement velocity, permitting builders to transport programs into manufacturing quickly even robotically setting the vital safeguards in place.
- Granular Access Control: Allows fine-tuned control over inbound and outbound traffic at the instance level.
- Stateful Filtering: Automatically allows return traffic for allowed inbound requests, reducing configuration complexity.
- Integration with AWS Services: Works seamlessly with services like EC2, RDS, ALB, and EKS for enhanced security.
- Ease of Management: Security Groups can be modified dynamically without affecting running instances.
- Multiple Security Groups per Instance: Enables flexible rule configuration by assigning multiple groups to a single instance.
- No Manual Rule Reversal Required: Unlike Network ACLs, Security Groups automatically allow outbound responses to inbound requests.
- Default Deny Policy: Ensures a secure baseline by blocking all unauthorized traffic by default.
- Scalability: Supports auto-scaling environments where instances inherit Security Group rules without additional setup.
To Earn Your End to End Encryption Certification, Gain Insights From Leading End to End Encryption Experts And Advance Your Career With ACTE’s AWS Online Course Today!
Best Practices of AWS Security Groups
You can use the subsequent first-class practices and recommendations to make the maximum of AWS Security Groups and enhance your usual machine safety:
Looking to Master AWS? Discover the AWS Master Training Program Available at ACTE Now!
Applications of Security Groups in AWS
Security Groups in AWS are broadly used throughout diverse packages to decorate safety and manage community site visitors. They are implemented in Amazon EC2 instances, RDS databases, Elastic Load Balancers (ELB), and Amazon Elastic Kubernetes Service (EKS) AWS Training to adjust inbound and outbound connections. In internet packages, Security Groups assist in getting admission by permitting the simplest unique IP addresses or port ranges, making sure that the simplest legal customers can interact with the application. In Microservices architectures, they facilitate a steady communique among offerings through defining guidelines that allow site visitors simplest from dependent on sources. Additionally, Security Groups play an essential position in hybrid cloud environments, permitting managed connectivity among on-premises structures and AWS resources. By enforcing well-configured Security Groups, companies can guard their cloud infrastructure from unauthorized admission to and capacity cyber threats.
Benefits of AWS Security Groups
Want to Learn About AWS? Explore Our AWS Interview Questions and Answers Featuring the Most Frequently Asked Questions in Job Interviews.
Security Group vs Network ACL
While Security Groups act as firewalls at the instance level, Network ACLs (Access Control Lists) operate at the subnet level. Security Groups are stateful, meaning that return traffic is automatically allowed, whereas Network ACLs are stateless and require explicit rules for both inbound and outbound AWS Course traffic. Security Groups are applied directly to EC2 instances, while Network ACLs apply to entire subnets, affecting multiple instances within them. Organizations often use both Security Groups and Network ACLs together to provide a layered security approach to their AWS environments.
Conclusion
In conclusion, Security Groups in AWS play an important function in controlling inbound and outbound visitors to AWS resources. They act as digital firewalls, permitting customers to outline policies that beautify protection with the aid of using proscribing get entry to primarily based totally on IP addresses, protocols, and ports. Security Groups are stateful, which means that responses to allowed inbound visitors are mechanically permitted. By cautiously configuring Security Group policies, companies can make certain that their cloud infrastructure stays stable at the same time as permitting vital verbal exchange among resources. Regular tracking and updating of Security Groups are crucial to preserving a sturdy protection posture in AWS environments.





