
[30+] Blue Coat Interview Questions and Answers [ FRESHERS ]
Last updated on 12th Nov 2021, Blog, Interview Questions
If you’re looking for Blue Coat Interview Questions & Answers for Experienced or Freshers, you are at the right place. There are a lot of opportunities from many reputed companies in the world. According to research, Blue Coat has a market share of about 0.9%. So, You still have the opportunity to move ahead in your career in Blue Coat Administration. ACTE offers Advanced Blue Coat Interview Questions 2021 that helps you in cracking your interview & acquire a dream career as a Blue Coat Administrator.
1. What is Blue Coat, and what are its main products?
Ans:
Blue Coat, now part of Symantec Corporation, is a cybersecurity company that provides solutions for web security, network performance optimization, and advanced threat protection. Some of its main products include :
- Blue Coat ProxySG
- Blue Coat PacketShaper
- Blue Coat SSL Visibility Appliance
- Blue Coat Content Analysis System
- Blue Coat Web Security Service
2. Explain the purpose of a proxy server and how Blue Coat uses it.
Ans:
A proxy server is a go-between client gadgets (such as laptops or mobile phones) and the internet. It serves several purposes, including :
Security : Proxy servers can inspect and filter incoming and outgoing traffic, blocking malicious content and providing a layer of security.
Anonymity : Users can access the internet by proxy to mask their IP addresses and enhance privacy.
Content Filtering : Proxy servers can block or allow specific content, restricting access to certain websites or types of content.
3. Describe the functions of Blue Coat’s Web Security Service.
Ans:
Blue Coat’s Web Security Service is a cloud-based solution that provides comprehensive web security for organisations. Its essential functions include :
Threat Protection : Detects and blocks malicious websites, malware, and phishing attempts to prevent security breaches.
URL Filtering : Controls website access based on categories, helping organisations enforce acceptable use policies.
SSL Inspection : Provides visibility into encrypted SSL/TLS traffic to identify and block threats hidden in encrypted connections.
Content Control : Enables organisations to manage and control user access to specific web content, ensuring compliance with security policies.
Cloud Integration : A cloud-based service allows organisations to extend security to remote users and branch offices without additional infrastructure.
4. How does Blue Coat handle SSL traffic?
Ans:
Blue Coat handles SSL traffic through SSL interception. In this process, SSL/TLS traffic is decrypted at the proxy server, inspected for threats, and re-encrypted before being sent to its destination. This allows Blue Coat to analyse the content of encrypted traffic, providing visibility into potential threats hidden within encrypted connections.
5. What is SSL interception, and why is it essential for security?
Ans:
SSL interception, also known as SSL inspection or SSL/TLS decryption, is decrypting encrypted SSL/TLS traffic at a security device or proxy server for inspection. It is vital for security because it allows organisations to :
- Detect Threats
- Enforce Security Policies
- Protect Against Data Loss
6. Can you explain how Blue Coat’s Content Analysis System works?
Ans:
Blue Coat’s Content Analysis System is designed to provide advanced threat protection by analysing and detecting malicious content in files and web traffic. The system works as follows :
File Analysis : It examines files for known and unknown threats, using techniques such as sandboxing to execute files in a controlled environment and identify malicious behaviour.
Web Content Analysis : The system inspects web content for threats, including malicious scripts, URLs, and other web-based attack vectors.
Threat Intelligence Integration : It leverages threat intelligence feeds to enhance the detection of emerging threats and known malicious entities.
Reporting and Remediation : The Content Analysis System provides detailed reports on detected threats and supports remediation efforts by blocking or isolating malicious content.
7. What is the purpose of Blue Coat’s Advanced Threat Protection (ATP)?
Ans:
Blue Coat’s Advanced Threat Protection (ATP) is a comprehensive solution against advanced, targeted cyber threats. The purpose of ATP includes :
Detecting Advanced Threats : ATP employs advanced techniques such as sandboxing and behavioural analysis to identify sophisticated and evasive threats.
Blocking Malicious Activity : It actively blocks malicious content and prevents threats from infiltrating the network or endpoints.
Incident Response : ATP provides tools for incident response, allowing organisations to investigate and remediate security incidents effectively.
8. How does Blue Coat support cloud-based security solutions?
Ans:
Blue Coat supports cloud-based security solutions through offerings like the Blue Coat Web Security Service. Key features include :
Cloud Delivery : The service is delivered from the cloud, allowing organisations to extend security to remote users and branch offices without needing on-premises infrastructure.
Scalability : Cloud-based security solutions can scale dynamically to accommodate changing workloads and user requirements.
Global Threat Intelligence : Cloud-based services leverage global threat intelligence to provide real-time protection against emerging threats.
9. Explain the role of Blue Coat in threat intelligence.
Ans:
Blue Coat is crucial in threat intelligence by leveraging its global threat intelligence network. Key aspects include :
Threat Detection : Blue Coat collects and analyses data from a vast network of security devices to detect and identify emerging threats.
Threat Intelligence Feeds : Blue Coat integrates streams of threat data from several sources to be aware of the latest threats and methods of assault.
Security Analytics : Blue Coat uses analytics to identify patterns, anomalies, and indicators of compromise, contributing to threat intelligence.
10. What is the difference between a firewall and a proxy server?
Ans:
| Aspect | Firewall | Proxy Server | |
| Purpose |
Network security; filters traffic based on rules |
Acts as an intermediary between client and server. | |
| Functionality | Controls incoming and outgoing traffic | Facilitates requests on behalf of clients. | |
| Location | Placed at network boundaries | Placed between clients and the internet. |
11. How does Blue Coat contribute to securing a network infrastructure?
Ans:
Blue Coat contributes to securing a network infrastructure through various solutions and features :
Web Security : Blue Coat provides web security solutions, including URL filtering, malware detection, and content control, to protect against malicious websites and content.
ProxySG : Acts as a secure web gateway, enforcing security policies and inspecting web traffic to block threats and ensure safe internet usage.
SSL Inspection : Decrypts and inspects SSL/TLS traffic to detect and prevent threats hidden within encrypted connections.
Advanced Threat Protection (ATP) : Offers advanced threat detection and prevention capabilities to defend against sophisticated and targeted attacks.
12. Describe the concept of URL filtering and its significance in web security.
Ans:
URL filtering categorises and controls website access based on content and purpose. It involves maintaining a database of URLs and assigning them to predefined categories, such as social media, gambling, or malware. The significance of URL filtering in web security includes :
Access Control : Organisations can define policies to allow or block access to specific categories of websites, preventing users from accessing inappropriate or malicious content.
Compliance : URL filtering helps organisations enforce compliance with acceptable use policies and regulatory requirements.
Threat Prevention : URL filtering prevents malware infections and other web-based threats by blocking access to known malicious websites.
13. Explain the term “deep packet inspection” and its use in Blue Coat products.
Ans:
Deep packet inspection (DPI) is a method of analysing and scrutinising the contents of network packets at a granular level. DPI goes beyond traditional packet inspection by examining the payload of packets, including application-layer data. In Blue Coat products, DPI is used for :
Threat Detection : DPI enables the identification of malicious content, exploits, and other security threats hidden within network traffic.
Content Control : DPI allows Blue Coat solutions to inspect and control specific application-layer protocols, helping enforce security policies.
Visibility : DPI provides detailed visibility into the contents of packets, aiding in detecting anomalies and potential security issues.
14. How does Blue Coat handle malware detection and prevention?
Ans:
Blue Coat employs several techniques for malware detection and prevention: URL filtering: Prevents access to websites considered to be harmful. And prevents users from inadvertently downloading malware.
SSL Inspection : Decrypts and inspects encrypted SSL/TLS traffic to identify and block threats hidden within encrypted connections.
Content Analysis System : Analyses files for malware using techniques such as sandboxing and behavioural analysis to detect and prevent advanced threats.
Threat Intelligence : Utilises global threat intelligence feeds to stay updated on the latest malware signatures and indicators of compromise.
15. Discuss the importance of bandwidth management in network security.
Ans:
Bandwidth management is crucial in network security for several reasons:
- Optimising Performance
- Prioritising Traffic
- Preventing DDoS Attacks
- Ensuring Fair Usage
- Cost Control
16. What are the benefits of using Blue Coat’s Secure Web Gateway?
Ans:
Blue Coat’s Secure Web Gateway (SWG) offers several benefits :
- Web Security
- URL Filtering
- SSL Inspection
- Cloud-Delivered Security
- Threat Intelligence Integration
17. How does Blue Coat help organisations protect against data loss?
Ans:
Blue Coat helps organisations protect against data loss through various mechanisms :
Content Inspection : Blue Coat Solutions inspects content in transit to identify and prevent the unauthorised transfer of sensitive information.
SSL Inspection : Decrypts and inspects encrypted SSL/TLS traffic to ensure that sensitive data is not being exfiltrated through encrypted channels.
Content Analysis System : Analyses files and web content for potential data loss risks, preventing the transmission of sensitive data in malicious files.
Data Loss Prevention (DLP) Policies : Blue Coat solutions allow organisations to define and enforce DLP policies, specifying rules for preventing the unauthorised transmission of sensitive data.
18. Explain the main features of ProxySG.
Ans:
ProxySG is a secure web gateway solution from Blue Coat that offers a range of web security and content control features. Its main features include :
- URL Filtering
- SSL Inspection
- Content Analysis
- Bandwidth Management
- Access Control
- Authentication and Authorization
- Logging and Reporting
19. What is caching, and how does ProxySG use it to improve performance?
Ans:
Caching is storing copies of commonly used information temporarily for quick retrieval. ProxySG uses caching to improve performance by :
Accelerating Content Delivery : ProxySG caches frequently requested local web content, such as images and videos. When users request the same content, ProxySG delivers it from the cache, reducing latency and accelerating content delivery.
Reducing Bandwidth Usage : Caching reduces the need to fetch the same content repeatedly from the origin server, conserving bandwidth and optimising network performance. Enhancing User Experience: By delivering cached content quickly, ProxySG improves the user experience by reducing page load times and enhancing the responsiveness of web applications.
20. Discuss the role of ProxySG in controlling user access to web content.
Ans:
ProxySG plays a critical role in controlling user access to web content through various features :
URL Filtering : ProxySG enforces access policies by categorising and controlling website access based on predefined categories, helping organisations enforce acceptable use policies.
Access Control Policies : Organisations can define granular access control policies to specify which users or groups can access specific web content, applications, or services. SSL Inspection: ProxySG decrypts and inspects encrypted SSL/TLS traffic, allowing it to enforce access policies even for encrypted connections.
21. How does ProxySG handle policy enforcement in a network?
Ans:
ProxySG handles policy enforcement in a network through the following mechanisms :
- URL Filtering
- Access Control Policies
- SSL Interception
- Authentication and Authorization
- Content Analysis
22. Can you describe the process of SSL interception in ProxySG?
Ans:
SSL interception, also known as SSL decryption or SSL/TLS interception, is the process of intercepting and decrypting encrypted SSL/TLS traffic for inspection. In ProxySG, the process of SSL interception involves the following steps :
- Initiation of SSL Connection
- Generation of Substitute Certificate
- Establishment of Connections.
- Decryption and Inspection
- Re-encryption
23. What is the purpose of ICAP (Internet Content Adaptation Protocol) in ProxySG?
Ans:
ICAP, or Internet Content Adaptation Protocol, is a standard protocol that enables ProxySG to interact with external content adaptation servers. The purpose of ICAP in ProxySG is to: Integrate Third-Party Services: ProxySG can use ICAP to connect to external servers or services that provide specialised content adaptation or processing. This allows organisations to leverage third-party solutions seamlessly.
Content Modification : ICAP servers can modify or adapt web content based on predefined policies. For example, content may be scanned for malware, modified for compliance reasons, or translated into a different language.
Enhance Security : ICAP can extend security measures by integrating additional security services, such as antivirus scanning or data loss prevention (DLP) solutions.
24. Have you obtained any Blue Coat certifications, and if so, which ones?
Ans:
Symantec Certified Specialist (SCS) : There are various SCS certifications covering different Symantec products and solutions, including web security, data loss prevention, and endpoint protection.
Symantec Certified Professional (SCP) : SCP certifications are designed for more advanced proficiency in specific Symantec solutions.
25. Discuss the benefits of having Blue Coat certifications for a professional in the cybersecurity field?
Ans:
Obtaining Blue Coat (now Symantec) certifications can offer several benefits for professionals in the cybersecurity field:
- Expertise Validation
- Career Advancement
- Industry Recognition
- Access to Resources
- Networking Opportunities
- Employer Confidence
26. What are the common challenges in cybersecurity, and how does Blue Coat address them?
Ans:
Common challenges in cybersecurity include :
Advanced Threats : Blue Coat addresses this challenge through solutions like Advanced Threat Protection (ATP), which provides advanced threat detection and prevention capabilities.
Data Loss : Blue Coat helps protect against data loss through content inspection, SSL interception, and Data Loss Prevention (DLP) policies.
Phishing Attacks : Blue Coat contributes to the prevention of phishing attacks through web security solutions, URL filtering, and threat intelligence integration.
User Awareness : Blue Coat emphasises user awareness by providing visibility into web usage, enforcing policies, and supporting user education on security best practices.
27. Explain the concept of a zero-day vulnerability and how Blue Coat deals with such threats.
Ans:
A program security defect unknown to the public is called a zero-day vulnerability: vendor or the public. “Zero-day” indicates that attackers exploit the vulnerability before the vendor has had zero days to release a patch or fix.
Blue Coat addresses zero-day vulnerabilities through various means:
- Threat Intelligence
- Behavioural Analysis
- Sandboxing
- Dynamic Updates
28. How does Blue Coat contribute to the prevention of phishing attacks?
Ans:
Blue Coat contributes to the prevention of phishing attacks through several mechanisms : URL Filtering: Blue Coat’s solutions use URL filtering to block access to known phishing websites, preventing users from visiting malicious URLs.
Threat Intelligence Integration : Blue Coat leverages threat intelligence feeds to identify and block phishing sites in real-time.
Content Analysis : Content Analysis System may analyse email content and attachments for phishing indicators, preventing the delivery of malicious payloads.
SSL Inspection : Blue Coat decrypts and inspects SSL/TLS traffic, allowing it to detect and block phishing attempts even in encrypted communications.
29. Discuss the importance of user awareness training in cybersecurity.
Ans:
User awareness training is crucial in cybersecurity for several reasons: Phishing Prevention: Training users to recognize phishing emails and websites reduces the likelihood of falling victim to phishing attacks.
Password Security : Educating users on creating strong passwords and avoiding password-related pitfalls enhances overall security.
Device Security : Users must be aware of security practices for their devices, including updating software, using antivirus tools, and securing physical access.
Data Handling : Training users on proper data handling practices helps prevent unintentional data breaches and promotes a culture of data security.
Social Engineering : Users should be informed about social engineering tactics to recognize and resist manipulation attempts.
30. How do you troubleshoot performance issues in a Blue Coat deployment?
Ans:
Troubleshooting performance issues in a Blue Coat deployment involves several steps :
- Traffic Analysis
- Log Analysis
- Bandwidth Management
- SSL Inspection
- Policy Review
- Cache Optimization
- Content Analysis System
- Sandboxing
31. Can you outline the steps you would take to investigate a security incident involving Blue Coat products?
Ans:
Initial Triage :
- Gather information on the incident, including affected systems and users.
- Identify the type of incident (e.g., data breach, malware infection).
Isolate and Contain :
- Isolate affected systems to prevent further damage.
- Contain the incident by blocking malicious traffic or isolating compromised devices.
Forensic Analysis :
- Use Blue Coat logs and reporting tools to trace the incident’s origin.
- Analyse network traffic and endpoint logs for indicators of compromise.
Collaborate with Blue Coat Support :
Engage Blue Coat’s support team for assistance in analysing logs and identifying potential vulnerabilities.
32. How does Blue Coat provide support for its customers?
Ans:
Blue Coat provides customer support through various channels, including:
Online Support Portal : Access to knowledge base, documentation, and software updates.
Technical Support Teams : Dedicated teams for assisting with troubleshooting and issue resolution.
Training Programs : Educational resources for customers to enhance product understanding.
33. Explain how Blue Coat integrates with other security solutions.
Ans:
Blue Coat integrates with various security solutions through APIs and partnerships. This includes integration with firewalls, antivirus programs, SIEM systems, and other third-party security tools. Integration enhances security by sharing threat intelligence and facilitating coordinated responses.
34. Discuss the compatibility of Blue Coat products with different network environments?
Ans:
Blue Coat products are designed to be versatile and deployable under various network conditions, including on-premises, cloud, and hybrid setups. They provide flexibility and scalability to accommodate the specific requirements of different network architectures. The compatibility of Blue Coat products with different network environments is crucial to consider when implementing cybersecurity measures.
35. How does Blue Coat support integrating its solutions with SIEM?
Ans:
Blue Coat supports integration with SIEM systems by providing connectors and APIs. This allows organisations to feed Blue Coat’s logs and event data into their SIEM solutions for centralised monitoring, analysis, and correlation of security events. It’s essential for organisations planning to integrate Blue Coat solutions with their SIEM systems to refer to the latest product documentation.
36. What recent trends in cybersecurity do you find most interesting?
Ans:
Zero Trust, AI-driven cybersecurity, and increased focus on cloud security could impact Blue Coat’s product development. Blue Coat may enhance its solutions to align with these trends, incorporating advanced threat detection, cloud-native security features, and improved user authentication mechanisms. It’s crucial to note that industry trends, customer feedback, and emerging threat landscapes will influence the evolution of Blue Coat’s products.
37. How does Blue Coat adapt to the evolving threat landscape?
Ans:
Blue Coat adapts to the evolving threat landscape by regularly updating its threat intelligence feeds, releasing security patches, and enhancing its products to address emerging threats. Regularly reviewing product documentation, participating in training programs, and engaging with vendor support can contribute to a more effective response to the evolving threat landscape.
38. How do you stay updated on the latest developments in cybersecurity and Blue Coat technologies?
Ans:
Stay updated through :
- Regularly reviewing security publications, blogs, and industry reports.
- Participating in webinars, conferences, and training sessions.
- Engaging with the Blue Coat community and monitoring official communications.
39. Can you discuss a situation where you had to quickly learn?
Ans:
In a professional setting, I quickly learned and adapted to new technology by :
- Leveraging online resources and documentation.
- Participating in training programs and seeking mentorship.
- Collaborating with colleagues and sharing knowledge within the team.
40. Describe a challenging situation you encountered while working with Blue Coat products.
Ans:
In a challenging situation, I faced an issue with a Blue Coat deployment affecting network performance. The resolution involved :
- Collaborating with Blue Coat support to analyse logs and diagnose the problem.
- Implementing recommended configuration changes to optimise performance.
- Conducting post-implementation testing and monitoring to ensure sustained improvement.
41. How do you prioritise security measures in a limited resource environment?
Ans:
Risk Assessment :
- Identify and assess potential risks and vulnerabilities.
- Prioritise based on the impact and likelihood of each threat.
Focus on Fundamentals :
- Ensure fundamental security measures (e.g., patching, access controls) are in place.
- Address critical vulnerabilities first.
Cost-Effective Solutions :
- Look for cost-effective security solutions.
- Leverage open-source tools and community resources.
Continuous Monitoring :
- Implement continuous monitoring for early threat detection.
- Use threat intelligence to focus on current risks.
42. Discuss a time when you had to collaborate with a team to implement a security solution.
Ans:
Collaborating with a team to implement a security solution involved :
- Conducting a comprehensive risk assessment.
- Engaging stakeholders to understand business requirements.
- Collaborating with IT, development, and operations teams to ensure a holistic approach
43. How does Blue Coat assist organisations in meeting regulatory compliance requirements?
Ans:
Blue Coat helps organisations meet regulatory compliance by :
- Providing granular control over web traffic, ensuring compliance with data protection regulations.
- Offering detailed reporting and logging features for audit purposes.
- Facilitating the implementation of policies that align with specific regulatory requirements.
44. What role does Blue Coat play in ensuring data privacy and protection?
Ans:
Blue Coat ensures data privacy and protection through :
- Robust encryption capabilities for secure data transmission.
- Content inspection to prevent data leakage.
- Access controls and authentication mechanisms to restrict unauthorised access.
45. How can Blue Coat help optimise network performance while ensuring security?
Ans:
Blue Coat optimises network performance by :
- Caching frequently accessed content locally for faster delivery.
- Prioritising and managing bandwidth usage based on policies.
- Utilising optimization techniques like compression to reduce data transfer.
46. Discuss the impact of Blue Coat on user experience in a corporate network.
Ans:
Blue Coat aims to have a minimal impact on user experience by :
- Balancing security measures with performance optimization.
- Providing transparent background security without disrupting normal operations.
- Optimising content delivery to enhance speed and responsiveness.
47. How does Blue Coat address security challenges in cloud-based environments?
Ans:
Blue Coat addresses cloud security challenges by :
- Extending its security solutions to cover cloud-based traffic.
- Integrating with cloud security platforms and services.
- Offering consistent policies across on-premises and cloud environments.
48. Explain the role of Blue Coat in securing cloud applications and services.
Ans:
The role of Blue Coat in securing cloud applications and services involves implementing measures to protect data, users, and networks as organisations adopt and utilise cloud-based resources. Blue Coat solutions typically include monitoring and reporting features that provide visibility into cloud-related security events.
49. What features does Blue Coat offer for securing web applications?
Ans:
Blue Coat offers features for securing web applications, including :
- Web application firewall (WAF) for protecting against application-layer attacks.
- I am filtering material to remove objectionable or harmful stuff.
- SSL inspection to identify and prevent threats within encrypted traffic.
50. How does Blue Coat protect against common web application vulnerabilities?
Ans:
Blue Coat protects against common web application vulnerabilities by :
- Implementing a WAF to detect and block SQL injection, cross-site scripting (XSS), and other attacks.
- Conducting thorough content inspection to identify and block malicious payloads.
- Providing regular updates and patches to address emerging threats and vulnerabilities.
51. Discuss the role of Blue Coat in incident response and threat mitigation.
Ans:
Blue Coat plays a critical role in incident response and threat mitigation by :
- Providing real-time visibility into network activities.
- Offering tools for incident detection and analysis.
- Enabling rapid response through automated actions and policy enforcement.
- Facilitating the containment and eradication of threats.
52. How can Blue Coat assist in identifying and responding to security incidents in real time?
Ans:
Blue Coat assists in real-time incident response by :
- Continuously monitoring network traffic for anomalies.
- Utilising advanced threat detection mechanisms.
- Providing automated response capabilities, such as blocking malicious traffic.
- Offering real-time reporting and alerting features.
53. Explain the importance of threat intelligence in Blue Coat’s security approach.
Ans:
Threat intelligence is crucial in Blue Coat’s security approach because :
- It helps identify and understand emerging threats.
- Enhances the accuracy of threat detection mechanisms.
- Informs proactive security measures, allowing organisations to stay ahead of evolving threats.
54. How does Blue Coat leverage threat intelligence to enhance its security solutions?
Ans:
Blue Coat leverages threat intelligence by :
- Integrating feeds from reputable sources to update its databases.
- Correlating threat data with network activities for accurate detection.
- Enhancing its security solutions with real-time information to improve threat prevention and response.
55. How does Blue Coat address security challenges associated with remote work?
Ans:
Blue Coat addresses remote work security challenges by :
- Extending security controls to cover remote users through VPNs or cloud-based solutions.
- Implementing secure web gateways to protect users accessing the internet from various locations.
- Providing visibility into remote user activities to detect and respond to potential threats.
56. Can you discuss the role of Blue Coat in mobile device security?
Ans:
While traditionally focused on web security, Blue Coat has adapted to mobile device security by :
- Integrating with mobile device management (MDM) solutions.
- Offering secure web gateways that extend protection to mobile users.
- Ensuring consistent security policies for both traditional and mobile endpoints.
57. How do you evaluate and manage third-party vendors for security solutions?
Ans:
Evaluating and managing third-party vendors involves :
- Evaluating the standing and performance history of the vendor.
- Ensuring compliance with industry standards and regulations.
- Evaluating the effectiveness and scalability of the security solution.
- Regularly monitor and audit the vendor’s performance.
58. Discuss how Blue Coat adapts to virtualized and containerized environments.
Ans:
Blue Coat adapts to virtualized and containerized environments by :
- Offering virtual appliances that can be deployed in virtualized infrastructure.
- Integrating with container orchestration platforms to secure containerized applications.
- Ensuring compatibility with various virtualization technologies.
59. How does Blue Coat contribute to the security of virtual networks?
Ans:
Blue Coat contributes to virtual network security by :
- Providing virtualized security solutions for virtual networks.
- Enforcing security policies for virtualized workloads.
- Offering visibility and control over traffic within virtualized environments.
60. Explain the role of Blue Coat in Data Loss Prevention (DLP).
Ans:
Blue Coat plays a role in DLP by :
- Monitoring and controlling sensitive data as it traverses the network.
- Implementing content inspection and policy enforcement to prevent data leaks.
- Integrating with DLP solutions to enhance overall data protection measures.
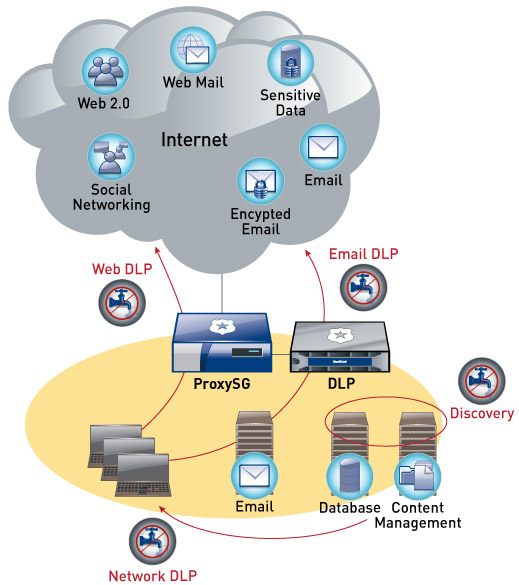
61. How does Blue Coat help organisations prevent unauthorised data exfiltration?
Ans:
Blue Coat helps prevent unauthorised data exfiltration by :
- Implementing Data Loss Prevention (DLP) policies to monitor and control sensitive data.
- Inspecting outgoing traffic for potential data leaks.
- Applying encryption and access controls to safeguard data from unauthorised access.
62. Discuss Blue Coat’s approach to cryptographic security.
Ans:
Blue Coat emphasises cryptographic security by :
- Supporting robust encryption protocols for secure communication.
- Providing SSL inspection capabilities to detect threats within encrypted traffic.
- Ensuring compliance with cryptographic standards to protect sensitive information.
63. How does Blue Coat handle encryption and decryption of network traffic?
Ans:
Blue Coat handles encryption and decryption by :
- Offering SSL/TLS interception to decrypt and inspect encrypted traffic.
- Ensuring visibility into encrypted content to detect and prevent malicious activities.
- Implementing secure and transparent methods for managing encryption keys.
63. How does Blue Coat handle encryption and decryption of network traffic?
Ans:
In a typical enterprise network architecture, Blue Coat can be positioned as: A secure web gateway at the network perimeter.
- Integrated with firewalls, VPNs, and other security components.
- Deployed in a distributed manner to cover various network segments.
- Connected to central management for unified policy enforcement.
64. How does Blue Coat fit into a typical enterprise network architecture?
Ans:
Blue Coat solutions are designed for scalability in large network environments by :
- Offering appliances and virtualized solutions that can handle high traffic volumes.
- Providing centralised management for streamlined policy enforcement.
- Supporting load balancing and distributed deployment for efficient resource utilisation.
65. Discuss the scalability of Blue Coat solutions in large network environments.
Ans:
Blue Coat assists in monitoring and analysing network performance through :
- Real-time visibility into network traffic and user activities.
- Features for performance enhancement like compression and caching.
- Reporting tools that provide insights into bandwidth usage and application performance.
66. How does Blue Coat assist in monitoring and analysing network performance?
Ans:
Blue Coat assists in monitoring and analysing network performance through :
- Real-time visibility into network traffic and user activities.
- Features for performance enhancement like compression and caching.
- Reporting tools that provide insights into bandwidth usage and application performance.
67. Explain the role of reporting and analytics in Blue Coat’s solutions.
Ans:
Reporting and analytics in Blue Coat’s solutions play a vital role by :
- Providing visibility into security events and policy violations.
- Offering detailed reports on web usage, threat incidents, and overall network health.
- Facilitating informed decision-making and continuous improvement of security measures.
68. Can you discuss the level of customization that Blue Coat allows for its security policies?
Ans:
Blue Coat allows a high level of customization for security policies by :
- Enabling organisations to define granular policies based on user roles, applications, and content.
- Supporting the creation of custom rule sets for specific security requirements.
- Offering flexibility in configuring policies to align with unique organisational needs.
69. How does Blue Coat cater to the unique security needs of different industries?
Ans:
Blue Coat caters to different industries by :
- Offering industry-specific threat intelligence feeds.
- Tailoring security solutions to address regulatory requirements.
- Providing flexibility in policy configuration to accommodate sector-specific security demands.
70. Discuss the methods and protocols Blue Coat supports for user authentication.
Ans:
Blue Coat supports various methods and protocols for user authentication, including :
- Integration with LDAP and Active Directory for user directory services.
- Support for multi-factor authentication to enhance access controls.
- Integration with identity and access management systems for centralised authentication and authorization.
71. How does Blue Coat enhance security through user identity verification?
Ans:
Blue Coat enhances security through user identity verification by :
- Integrating with identity providers for user authentication.
- Enforcing access controls based on user roles and permissions.
- Supporting multi-factor authentication to strengthen user identity verification.
72. How does Blue Coat analyse the current threat landscape?
Ans:
Blue Coat analyses the current threat landscape by :
- Aggregating threat intelligence from various sources.
- Employing advanced analytics to identify patterns and trends.
- Monitoring emerging threats and vulnerabilities to stay proactive in security measures.
73. Discuss a situation where Blue Coat’s threat analysis was crucial in preventing a security incident.
Ans:
In a situation, Blue Coat’s threat analysis was crucial when :
- The system detected a new and sophisticated malware strain.
- The threat intelligence revealed potential targets and attack methods.
- Blue Coat’s proactive response, including signature updates, prevented the malware from compromising systems.
74. Can you outline best practices for deploying Blue Coat solutions in an enterprise?
Ans:
- Conduct a thorough risk assessment and define security policies.
- Implement a phased deployment strategy to minimise disruptions.
- Integrate with existing security infrastructure for a unified defence.
- Regularly update signatures, policies, and software for the latest protections.
75. How does Blue Coat assist in seamlessly integrating its products into existing network infrastructures?
Ans:
The seamless integration of cybersecurity products into existing network infrastructures is crucial for organisations to maintain operational continuity and efficiently enhance their security posture. Blue Coat typically offers professional services and support to assist organisations in integrating.
76. Explain how Blue Coat provides load balancing and redundancy in its solutions.
Ans:
Blue Coat, now part of Broadcom, offers various cybersecurity solutions, including web and network security. Organisations utilising Blue Coat cybersecurity solutions are encouraged to refer to the product documentation and support resources and engage with Blue Coat (now Broadcom) representatives for the latest and most accurate information regarding these features.
77. What measures does Blue Coat take to ensure high availability and reliability?
Ans:
Blue Coat, now part of Broadcom, provides various cybersecurity solutions, including web and network security. Organisations using Blue Coat cybersecurity solutions are encouraged to refer to the product documentation and support resources and engage with Blue Coat (now Broadcom) representatives for the latest and most accurate information regarding high availability and reliability features.
78. Discuss the role of Blue Coat in disaster recovery planning for cybersecurity incidents.
Ans:
Blue Coat contributes to disaster recovery planning by :
- Providing insights into the impact of security incidents on the network.
- Offering backup and restoration features for configuration and policy settings.
- Supporting organisations in developing incident response and recovery strategies.
79. How does Blue Coat help organisations protect against social engineering attacks?
Ans:
Blue Coat helps protect against social engineering attacks by :
- Implementing web filtering to block access to malicious sites.
- Employing email filtering to identify and quarantine phishing attempts.
- Educating users on social engineering risks and best practices.
80. Discuss user education’s role in mitigating social engineering risks.
Ans:
User education is crucial, and Blue Coat supports this by :
- Providing resources and training materials on recognizing social engineering tactics.
- Encouraging organisations to conduct regular awareness programs.
- Promoting a security culture where users are vigilant and report suspicious activities promptly.
81. Can you speculate on the future developments and innovations in Blue Coat’s technology?
Ans:
While I can’t provide real-time updates, future developments in Blue Coat’s technology might include :
- Integration of advanced AI and machine learning for more robust threat detection.
- Enhanced support for cloud-native security solutions./li>
- Continued focus on user-centric security, including improved identity management.
82. How do you collaborate with other IT teams to ensure a holistic approach to cybersecurity?
Ans:
Cybersecurity is a multidimensional challenge that involves various aspects of technology, processes, and people. Organisations can accomplish a more thorough and efficient cybersecurity method by fostering collaboration across IT teams. This collaborative effort helps break down silos, leverage diverse expertise, and create a unified defence against evolving cyber threats.
83. Discuss a situation where cross-functional collaboration was essential for success of a security project.
Ans:
- The security team collaborated with the IT operations and development teams.
- Cross-functional expertise was crucial in identifying and patching vulnerabilities.
- Regular meetings and shared resources ensured the success of a critical security project.
84. How does Blue Coat contribute to proactive threat hunting in a network?
Ans:
Blue Coat, now part of Broadcom, offers various cybersecurity solutions, including web security and threat intelligence services. Organizations considering Blue Coat for proactive threat hunting should consult the latest documentation and product specifications. They should contact Blue Coat (now Broadcom) representatives for the most up-to-date information on how their solutions contribute to network security and threat detection.
85. Discuss the tools and methodologies Blue Coat employs for threat hunting.
Ans:
- Utilising behavioural analysis to identify abnormal patterns.
- Incorporating threat intelligence feeds to stay ahead of emerging threats.
- Conducting forensic analysis using advanced logging and reporting features.
86. Explain the concept of Zero Trust Security and how Blue Coat aligns with this approach.
Ans:
Zero Trust Security assumes no entity, whether inside or outside the network, should be trusted by default. Blue Coat aligns with this approach by :
- Implementing strict access controls and continuous monitoring.
- Emphasising the need for verification at every stage of communication.
- Providing visibility and inspection of all network traffic.
87. How does Blue Coat enhance security in a perimeter-less environment?
Ans:
Blue Coat enhances security in a perimeter-less environment by :
- Shifting the focus to identity-centric security.
- Implementing secure web gateways and advanced threat detection.
- Offering consistent security policies regardless of the user’s location.
88. Blue Coat’s Contribution to Employee Training and Awareness Programs:
Ans:
Blue Coat supports employee training and awareness programs by :
- Providing educational resources on cybersecurity best practices.
- Integrating security awareness modules into its solutions.
- Encouraging organisations to conduct regular training sessions.
89. Discuss the role of continuous training in maintaining a solid security posture.
Ans:
Continuous training is essential for :
- Keeping employees informed about evolving cyber threats.
- Instilling a security-conscious culture within the organisation.
- Giving people the ability to detect and react to security incidents effectively.
90. How does Blue Coat support implementing and enforcing cybersecurity policies?
Ans:
Blue Coat supports the implementation and enforcement of cybersecurity policies by :
- Providing a flexible policy framework that aligns with organisational requirements.
- Offering regular updates and patches to address policy-related vulnerabilities.
- Enabling centralised management for consistent policy enforcement across the network.

