
- Introduction
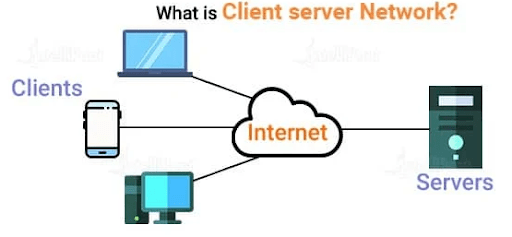
- What is a Client Server Network?
- Client Server Network Example
- Advantages of Client Server Network
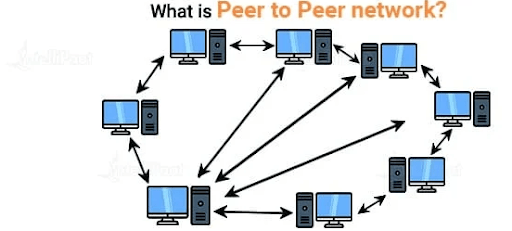
- What is a Peer-to-Peer network?
- Peer-to-Peer Network Example
- Advantages of Peer-to-Peer Network
- Difference Between Peer-to-Peer Network and Client Server Network
- Conclusion
Introduction
Client-server community and peer-to-peer community may be understood as telecommunication networks that switch records from a supply to the destination. One of the full-size motives for the recognition of those networking fashions is they set off minimum loss inside the transmission of statistics over a community. In each network, a course is used for the transmission of statistics or records in this Cybersecurity Training Courses . However, one of the full-size variations between the peer-to-peer community and client-server community is that the previous one no longer has a committed course for shifting statistics, while the latter does have a committed course for shifting statistics.
What is a Client Server Network?
- Web Servers: When you get the right of entry to a website, your net browser (client) sends a request to the net server, which approaches the request and returns the asked net pages or records.
- Email Systems: In structures like Microsoft Outlook or Gmail, the client (e-mail application) communicates with the e-mail server to ship and get hold of messages.
- Database Servers: Applications like consumer dating control (CRM) or corporation aid planning (ERP) structures rely upon database servers to address queries and shop records centrally for more than one user.
- File Servers: In businesses, a record server shops files and documents, and customers get the right of entry to those documents over the community for sharing and collaboration.
- Game Servers: Multiplayer online video games like World of Warcraft use committed recreation servers to host the sports world, with gamers appearing as customers who hook up with the server.
- Centralized Management: Resources, records, and protection regulations are centrally managed, making sure higher manipulation over the community.
- Enhanced Security: Centralized servers permit the implementation of sturdy safety features like firewalls, authentication, and get right of entry to manipulate.
- Scalability: The community may be without problems scaled through including extra customers or upgrading server hardware to address improved demands.
- Efficient Resource Sharing: Servers offer optimized sharing of assets which include documents, applications, and printers throughout the community.
- Reliability: The receiver, who possesses the same secret key as the sender, applies the Decryption in Cybersecurity algorithm to the ciphertext.
- Performance Optimization: High-overall performance servers can take care of massive workloads and make certain clean operations for more than one customer.
- User Management: Centralized manipulation permits for green person account control and monitoring.
- Support for Large Networks: Suitable for groups requiring based and prepared networking for a massive variety of users.
- Ease of Maintenance: Centralized updates and troubleshooting lessen the effort and time required for community maintenance.
- Supports Advanced Applications: Ideal for web website hosting net services, e-mail structures, and database control, which require effective server capabilities.
- File Sharing Applications: Platforms like BitTorrent permit customers to proportion documents without delay with every different without counting on an imperative server.
- Blockchain Networks: Cryptocurrencies like Bitcoin and Ethereum function on decentralized P2P networks for steady transactions and statistics sharing.
- VoIP Services: Skype to start with used a P2P structure for voice and video communique among customers.
- Gaming Networks: Many multiplayer online video games use P2P connections for matchmaking and gameplay among players.
- Collaboration Tools: Tools like Shareaza and LimeWire (now discontinued) enabled customers to proportion documents, music, and different documents without delay.
- Cost-Effective: It calls for no devoted servers, lowering hardware and preservation costs.
- Ease of Setup: P2P networks are easy to configure and do now no longer require specialized technical expertise.
- Decentralized Structure: There isn’t any imperative dependency, lowering the threat of an unmarried factor of failure.
- Direct Resource Sharing: Peers can proportion assets like documents, printers, and bandwidth without delay, improving collaboration.
- Scalability: New gadgets may be introduced to the community without problems and sizeable adjustments to the structure.
- Flexibility: Peers can act as each customer and server, making the community dynamic and adaptable.
- Reduced Traffic Bottlenecks: As responsibilities are disbursed amongst peers, there’s much less risk of congestion as compared to centralized networks.
- Local Performance Optimization: Data Classification and assets are frequently shared inside smaller groups, lowering reliance on outside connections.
- No Need for Central Administration: Eliminates the want for a imperative administrator, simplifying control in small networks.
- Ideal for Specific Applications: Suitable for environments like report sharing, collaborative projects, or small office/domestic networks.
It is likewise called the networking computing version or client-server community as all requests and offerings are added over a community. The client-server structure or version has another(other) gadget(s) related to a community wherein assets are shared by a few of the one-of-a-kind computers. Customers provoke requests, along with retrieving statistics, getting access to packages, or the usage of shared hardware like printers, even as the server responds by offering the asked offerings. This structure is broadly utilized in businesses, websites, and packages that require sturdy security, scalability, and Supply Chain Management . However, client-server networks generally call for greater assets and protection in comparison to less difficult community fashions. Recognized as one of the maximum weirdly used networking fashions, the client-server community version, generally, consists of many customers or workstations interconnected in a community with a vital server. While the server acts as an effective gadget that shops all of the statistics on it, the client features as a device that requests particular records from the server.
Are You Interested in Learning More About Cybersecurity? Sign Up For Our Cyber Security Online Training Today!
Client Server Network Example
Advantages of Client Server Network
To learn about different Cybersecurity techniques, sign up for our Cyber Security Online Training right now!/i>
What is a Peer-to-Peer network?
Peer-to-peer community entails or greater computer systems that pool numerous peripheral assets inclusive of printers and DVD players. Such shared assets are to be had on each laptop inside the community. In a peer-to-peer community, every laptop behaves because the purchaser in addition to the server, communicates with the opposite computer systems immediately. This sort of community is ideally utilized by SMBs that paint without the want of a vital server. All linked computer systems of the device paint as nodes and permit seamless document sharing. Such a community is simple to install and requires a Wi-Fi connection or an Ethernet cable for its setup. A peer-to-peer (P2P) community is a decentralized community version wherein all linked devices, or “peers,” have identical roles and responsibilities. In this setup, every peer can act as a purchaser and a server, permitting them to percentage assets, files, or offerings immediately without counting on a vital server. P2P networks are easy to install and cost-effective, making them appropriate for obligations like document sharing, collaborative paintings, or small-scale packages. However, they could face demanding situations with Encryption in Network Security, scalability, and performance, as there may be no centralized management to manipulate visitors or make certain facts integrity. This version is normally utilized in packages like document-sharing platforms, blockchain systems, and a few gaming networks.
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Today!
Peer-to-Peer Network Example:
Torrent is one of the maximum famous examples of peer-to-peer networks. In this kind of community, all computer systems are related to the net wherein assets shared with the aid of using any person’s laptop may be downloaded with the aid of using others in Cybersecurity Training Courses. Another extensively used instance of peer-to-peer community is the neighborhood region community (LAN,) which is commonly desired with the aid of using small workplaces for the motive of useful resource sharing.
Advantages of Peer-to-Peer Network
Preparing for a job Interview? Check out our blog on Cybersecurity Interview Questions and Answers !
Difference Between Peer-to-Peer Network and Client Server Network
A peer-to-peer (P2P) community and a purchaser-server community range on the whole in shape and functionality. In a P2P community, all gadgets, or “peers,” proportion identical duties and may each request and offer services, making it decentralized. Conversely, a purchaser-server community has a centralized architecture, in which servers offer assets or services, and customers request them. P2P networks are less complicated and cost-powerful however may also warfare with scalability and safety. Client-server Network Security Keys provide centralized manipulation, higher performance, and more advantageous safety however require greater assets and maintenance. P2P is usually used for record sharing, at the same time as purchaser-server setups are perfect for enterprise packages and websites. The preference relies upon particular needs, inclusive of scale, safety, and functionality.
Conclusion
In conclusion, purchaser-server and peer-to-peer (P2P) networks constitute wonderful procedures for community design, every with its strengths and limitations. Client-server networks provide a centralized shape that guarantees higher manipulation, safety, and scalability, making them appropriate for organizations and large-scale packages. In contrast, P2P networks offer a decentralized and cost-powerful model, permitting gadgets to proportion assets directly, which is right for small-scale setups or particular duties like record sharing. While purchaser-server networks call for better assets and maintenance, Cybersecurity Training excel in reliability and performance. On the opposite hand, P2P networks are less complicated to put in force however may also face demanding situations in safety and efficiency. The preference among the 2 relies upon the use case, scale, and favored degree of manipulation and complexity. Given the differentiating parameters of each sort of network, it can be inferred that each network has its very own benefits and disadvantages. While the purchaser server community is essentially desired with the aid of using enterprises, the peer-to-peer community is satisfactorily healthy for SMBs. Individuals and corporations can pick out any kind of community relying on their plans to scale, implementation cost, and numerous different factors. Hope this weblog helped you recognize the distinction between peer-to-peer community and purchaser server community.





