
- Cyber Hygiene Definition
- Why is it vital?
- Best Practices for cyber hygiene
- The advantages of hygiene cyber
- Types of Cyber Hygiene
- What occurs if your online hygiene could be better?
- Conclusion
Today, whether personal or organizational hygiene, it is an absolute must to keep strong cyber security for survival in this interconnected world. The closer Cyber Security Training Courses practices bring to the idea of preventing illness, like people’s usual hygiene practices, thereby keeping their digital assets and themselves safe online. This introduction explores the simple principles of cyber security- emphasizing that proactive steps ensure the protection of personal information, system integrity, and a secure digital climate. Through the practice that forms good cybersecurity, it is evident that we all play a role in the giant effort at mitigating cyber risks.
Cyber Hygiene Definition
Cyber is the discipline of maintaining a secure and private digital environment. It entails behaviours and precautions to protect personal data and digital assets from online dangers. Cyber Security Training Courses is crucial for digital well-being, just as personal cleanliness is for physical well-being. The aim of hygiene cyber is to maintain the security and health of your hardware and software while shielding them from threats like viruses and internet intrusions. Regular cyber hygiene practice contributes to the protection of your data and information. By incorporating hygiene cyber into your daily practice, you may prevent hackers from causing issues or stealing your personal information. Moreover, it guarantees that your machine’s programs are constantly updated.
Why is it vital?
- Safeguarding Personal Information: Keeping your personal information safe is one of the main reasons hygiene cyber matters. We save many personal details online, from financial information to social media profiles.
- Preventing Identity Theft: Cybercriminals frequently target people with lax hygiene cyber standards to steal identities. Web Security can thwart such endeavours and safeguard you against theft.
- Preventing Financial Losses: Cyberattacks can cause large financial losses for people and companies. Hygiene cyber practices lower the chance of falling for fraud or scams, which can prevent these losses.
- Safeguarding Reputation: Your internet reputation is important in the current digital era. cyber hygiene helps you keep a solid online reputation by stopping dangerous content from spreading under your name or illegal access to your accounts.
Want to learn more about Cyber Hygiene ? Enroll in our Complete Cyber Security online training .
Best Practices for cyber hygiene
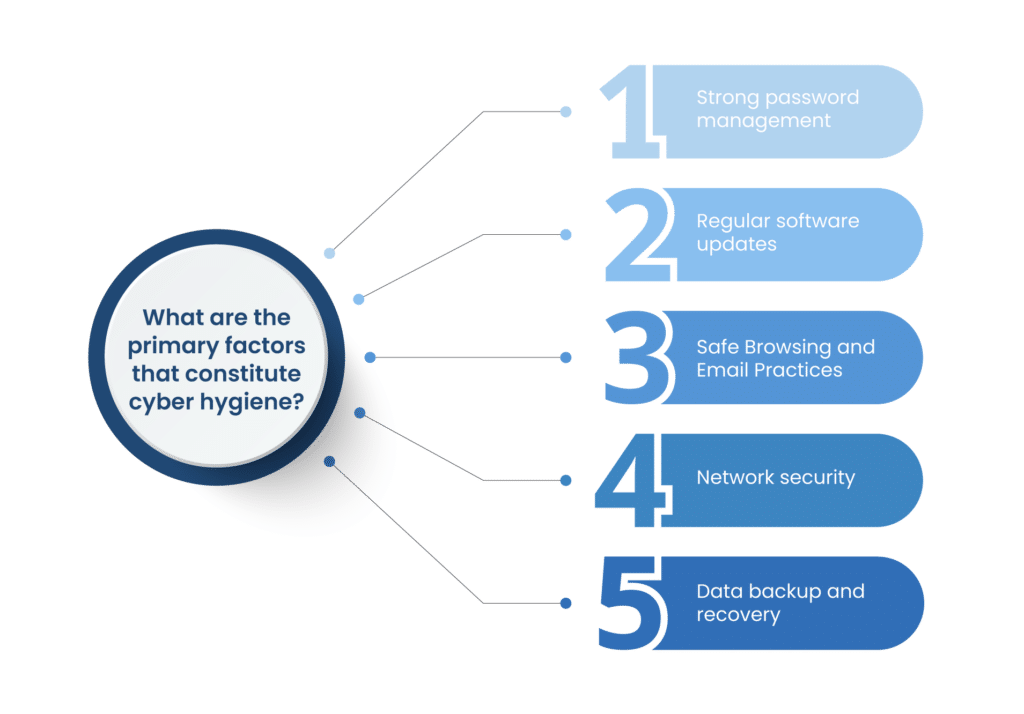
Employ Strong Passwords
- Password Complexity:Create passwords that are difficult to figure out by using a combination of capital and lowercase characters, numbers, and special symbols. Don’t use cliches or readily available personal information.
- Longer Passwords: Stronger passwords are generally longer. To make it more difficult for attackers to decipher them, try to use at least 12 characters.
- Steer clear of dictionary words:Avoid employing dictionary terms or phrases, as attackers frequently use dictionary-based password-guessing techniques.
Update Often
- Operating SystemsEnable automatic updates to ensure that your operating system receives the most recent security fixes as soon as they become available.
- Software:Update all of your software regularly. This includes office suites, web browsers, and security software. Cyber Awareness often target outdated software.
- Third-Party Plugins: Keep your browser and other apps’ third-party plugins and extensions up to date. These plugins may contain exploitable vulnerabilities.
- Patch ManagementTo automate the upgrading and patching process, enterprises can utilize patch management technologies.
Watch Out for Phishing
- Email Verification: Before opening any emails, especially those with links or attachments, ensure the sender is legitimate. Check the email addresses of the senders for inconsistencies.
- Training on Phishing Awareness Inform yourself and your staff on typical phishing techniques and offer advice on how to spot dubious emails.
- Hover over Links To see a link’s exact URL, move your mouse cursor over it rather than clicking on it. Don’t click on anything if it seems fishy or doesn’t match the email’s associated source.
- Never Exchange Sensitive Personal This is especially true when responding to unsolicited requests.
- Report Suspected Phishing Encourage your company to set up a system for reporting any suspected phishing efforts. Reporting enables prompt identification of possible risks.
Backup Data
- Automated backup: Use automated backup solutions to store backup copies of your data regularly on a safe cloud service or an external device.
- Backup routine:To guarantee that your data is constantly safeguarded, set up a regular backup routine. Regular backups are especially crucial for sensitive data.
- Data Encryption: To provide additional security, consider encrypting your backup data. This guarantees that the data is protected even if the backups are hacked.
Activate the two-factor authentication (2FA) system
- Enable 2FA on All Related Accounts: If feasible, set up 2FA for all your online accounts, such as social media, email, and banking. By demanding a second verification step, it provides an additional degree of security.
- Authentication Apps: For extra security, consider utilizing authentication apps like Authy or Google Authenticator in addition to SMS-based 2FA. These programs generate time-based codes.
- Replica Codes: If you misplace your primary 2FA device, store the backup codes that your 2FA service has supplied. Could you keep them in a safe place?
The advantages of Hygiene cyber
Minimize Vulnerabilities The primary goal of Hygiene Cyber is to lessen the vulnerabilities that online criminals might exploit. Potential security issues can be prevented when individuals and companies regularly update the software on their devices and computers, install security updates, and use up-to-date antivirus and anti-malware programs. Common Cyber Media Prevention Hygiene cyber is essential for thwarting and minimizing common internet threats. Phishing, login information theft, and other scams by cybercriminals can be prevented by using strong passwords, enabling two-factor authentication, and exercising caution when surfing. Encouraging Security Awareness: Educating individuals about online safety and what to do is crucial to cyber Hygiene. Hygiene cyber helps people make wise decisions and take action to keep themselves and their organizations secure by educating people about being safe online. Adaptability to Emerging Threats New threats are constantly emerging in cybersecurity, which is always changing. Practising cyber hygiene makes it easier to combat these emerging threats. People and organizations may stay ahead of these emerging threats by reading about cybersecurity news and staying current on the latest security developments.
Are you curious to know more about Cyber Hygiene ? Take advantage of our comprehensive Cyber Security online training
Types of Cyber Hygiene
- Password Hygiene: Complex, unique passwords applied to each service or application may reduce the chances of getting credential stuffed or password-related attacks. A password manager securely stores and generates strong passwords so that there is no chance of using the same password more than once, forgetting it, or mishandling it. If MFA is available, it adds another layer of protection to the account in case the password is compromised.
- Patch Management: Upgrades the operating systems, software, applications, or firmware. This is also to seal off the weak points that can be exploited. Put on the automatic updates feature of your main software so the patching is timely without having to make manual adjustments.
- Endpoint Protection: Antivirus/Anti-malware From installing the antivirus software combined with the periodic updates is the detection of unwanted programmes such as viruses, spyware, or ransomware. Firewalls Install firewalls on endpoints and networks to detect and prevent suspicious or unauthorized traffic.
- Network Security:Use strong encryption, such as WPA3, for wireless networks and change your Wi-Fi passwords regularly to prevent unauthorized access to your network.Virtual Private Networks (VPNs): VPNs must be used when accessing sensitive data remotely, especially over untrusted networks such as public Wi-Fi, to protect communications and avoid man-in-the-middle attacks.
- Data Backup and Recovery: The regular backup and safe storage of the created backups, either in the cloud or offline, are the first step in data recovery in case the data is lost by ransomware or similar disasters. Testing backups and recovery procedures for integrity and knowing how to execute them without hassle when required.
- User Education and Awareness: Raise awareness of phishing emails, scams, or social engineering techniques. Educating the user so that they know whether the email or link belongs to a legitimate party is very important as one of the best weapons against human error-based attacks.Regular cybersecurity training of all employees so that they remain aware of Resolution Protocol and understand why these security norms are so important or what may happen if they are not followed.
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cybersecurity Expert Masters Program Training Course Today!
What occurs if your online Hygiene could be better?
- Increased Vulnerability:Phishing, malware, and ransomware attacks are likely.
- Financial Impacts: Recovery costs resulting from cyber events include fines and legal fees. Possible lost businesses are incurred. Reputation Damage
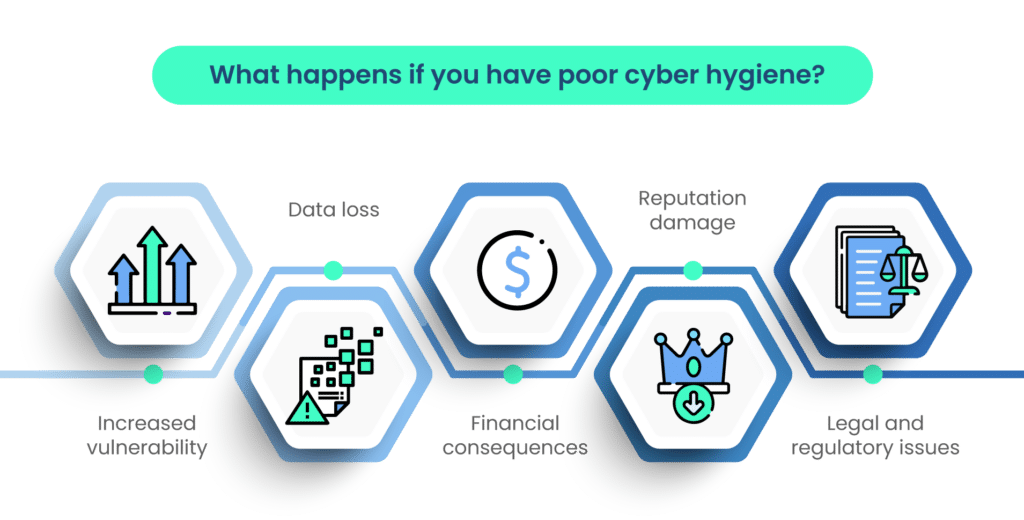
- Data Exposure: The sensitivity of personal or organizational information will be exposed and likely cause identity theft or loss of finances due to the Vulnerability Management of the information.
- Exposure of Confidential Information: Business and personal information held in one’s business and private affairs will be stolen, compromised, or destroyed. The exposure will have a detrimental effect on business operations and privacy.
Preparing for a job Interview? Check out our blog on Cyber Security Interview Question And Answers
Conclusion
In the current digital era, practising Cyber Security Training Courses is essential rather than optional. It’s a preemptive strategy for safeguarding your information, identity, and reputation online. By implementing best practices, individuals and companies can benefit from improved security, reduce the dangers associated with cyberattacks, and remain ahead of the always-changing cyber hygiene. Adopting cyber is essential to a safer digital future in this linked world.





