
- Introduction
- What is DDoS?
- DDoS Mitigation: Definition
- DDoS Mitigation Techniques
- DDoS Mitigation Procedures
- Best Practices for DDoS Mitigation
- Conclusion
Introduction
Cyberattacks, particularly Distributed Denial of Service (DDoS) attacks, are increasingly sophisticated and disruptive. These attacks overwhelm target systems with excessive traffic, making them inaccessible to legitimate users in Cybersecurity Training Courses . The consequences can include website downtime, business loss, and reputational damage. However, effective DDoS mitigation methods like traffic filtering and rate limiting can significantly minimize the impact of such attacks, ensuring that critical services remain available and operational.
What is DDoS?
This cyberattack is where multiple systems often compromised are utilized for sending traffic to one target system; it disrupts the service in that system, and the result will be a distributed denial of service. The hacker’s objective would be to use up the bandwidth or the computer power of a server in that target system making the service not available to legal users. A DDoS attack usually employs a Power of Network Address Translation of compromised computers or devices under the control of the attacker, which is used to send an enormous amount of traffic to the victim’s server or network. This traffic may include simple requests, packets, or even malicious payloads, depending on the attack vector.
Are you curious to know more about Cybersecurity ? Take advantage of our comprehensive online Cyber Security Online Training .
DDoS Mitigation: Definition
DDoS mitigation involves strategies, techniques, and tools designed to detect, prevent, and manage DDoS attacks, minimizing their impact on systems. The process requires identifying malicious traffic and distinguishing it from legitimate traffic. Once detected, it is filtered or redirected to safeguard services from disruption. A successful DDoS mitigation strategy includes proactive prevention measures, tools for Threat Intelligence detection and analysis, and responsive actions such as blocking or limiting the attack to maintain system availability and performance.
DDoS Mitigation Techniques
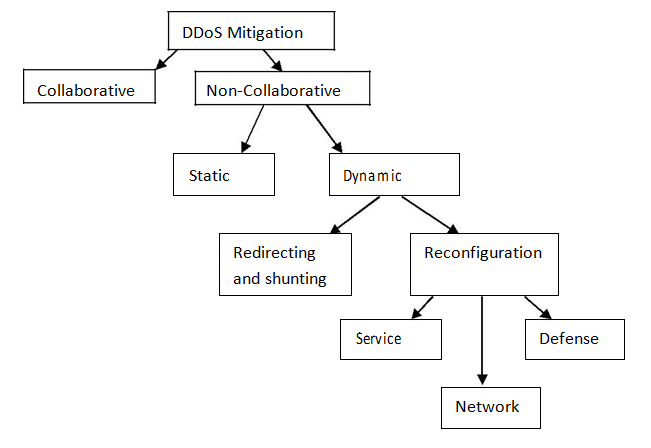
There are various measures taken to prevent DDoS attacks. This depends on the type of DDoS attack, targeted infrastructure, and also the level of protection required by the infrastructure. Some of the most frequently used DDoS mitigation techniques include in Cybersecurity Training Courses ;
-
Rate Limiting
- Rate limiting is essentially a technique designed to limit how many requests from a user or device can occur in a network or server for a given timeframe. It keeps the incoming requests restricted and prevents attacks that flood servers with large quantities of traffic because it makes such an attack process much more complex. For example, a website can accept only 100 requests per minute from a single IP address. If the DDoS attacker tries to send millions of requests that may overwhelm the server, then rate limiting will block or throttle the excess traffic. Traffic Filtering
- Traffic filtering entails the examination of incoming traffic, identifying, and filtering out bad or unwanted traffic while passing valid traffic through. Traffic filtering is done at a variety of levels in a network, either in the network layer or application layer. Tools such as firewalls, IDS, and IPS can be set up to look for known patterns of attacks and drop the malicious packets before they get to the targeted system.
- A Content Delivery Network (CDN) refers to a network of servers that will distribute copies of the web contents across different data centers and are likely to be retrieved from the server closest to each requestor’s site. Making use of the CDN can absorb traffic through DDoS because the server loads are dissipated across servers and not kept at one. Since CDNs are distributed geographically, they also can provide redundancy and resilience and keep services alive during high traffic periods caused by DDoS attacks. Anycast Network
- Anycast is a routing that routes Data Classification toward the nearest or best destination out of a set of possible destinations that share the same IP address. Using an Anycast network means a DDoS attack can be spread across multiple data centers, dispersing the traffic and lowering overall loads from one server. This technique is particularly effective for combating large-scale DDoS attacks because such a distributed nature of traffic makes the attacker’s target in a specific location difficult. WAF-Web Application Firewalls
- A Web Application Firewall (WAF) is a security tool specifically designed to protect web applications by filtering and monitoring HTTP requests. WAFs can prevent attacks such as SQL injection, cross-site scripting (XSS), and DDoS by blocking malicious requests or traffic. WAF can detect unusual traffic patterns, such as an unusual spike in requests from a given IP, and cause a block or challenge to the request. This can be particularly helpful in countering application layer DDoS attacks. DDoS Protection Services
- Most organizations opt to outsource DDoS protection to third-party services, which have experience in countering massive attacks. Such services, for example, Cloudflare, Akamai, and AWS Shield, have solutions that detect and mitigate real-time DDoS attacks. They use filtering, rate limiting, and traffic diversion techniques that help keep websites and services up and running during an attack. These services often operate at the edge of the internet and can scale automatically to handle large volumes of malicious traffic, thus keeping your services protected.
Want to learn more about Cybersecurity ? Enroll in our Complete Cyber Security Online Training .
Content Delivery Networks (CDN)DDoS Mitigation Procedures
Mitigating a DDoS attack requires a well-thought-out plan and the implementation of several procedures. Below are the main phases involved in DDoS mitigation:
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Today!
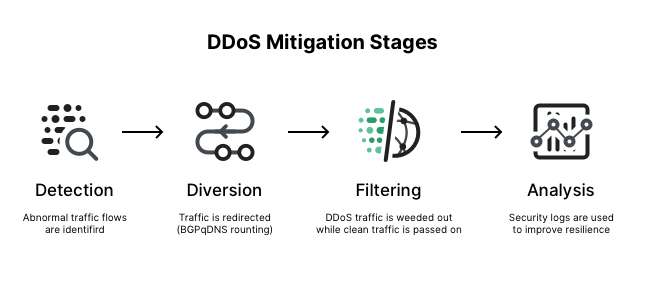
- Prevention
- The first step in mitigating DDoS attacks is to implement preventive measures. This involves setting up security configurations, deploying tools like firewalls and WAFs, and implementing DDoS protection services. Network hardening and security best practices should be part of your strategy to reduce the risk of an attack in the first place. Detection
- DDoS attacks need to be detected early to take corrective action. This can be done through continuous monitoring of traffic patterns and looking for unusual spikes or patterns indicative of an ongoing Malware Attack. Many DDoS protection services provide real-time monitoring and alerts when attack traffic is detected. Response
- Once an ongoing DDoS attack is identified, the subsequent action is a rapid response. This can be a response of turning on rate limiting, implementing traffic filters, or redirecting traffic through Any cast networks or CDNs. In case of an application-layer attack, WAF can be used for the rejection of malicious requests. Rapid response minimizes the time spent during downtime and allows good users to utilize the services. Post-Attack Recovery
- After a DDoS attack, the recovery phase involves analyzing the attack, reviewing logs, and identifying any weaknesses in your infrastructure. This phase is essential for improving future DDoS mitigation strategies. Lessons learned should be used to update security measures and implement stronger defenses for the future.
Get interview-ready with our collection of Cybersecurity Interview Questions and Answers Questions.
Best Practices for DDoS Mitigation
To strengthen your defenses against DDoS attacks, consider the following best practices:
- Regularly update your security infrastructure: Ensure that firewalls, WAFs, and other protective measures are up-to-date.
- Use redundant systems: Deploy multiple servers, data centers, or cloud solutions to ensure redundancy and distribute traffic effectively.
- Conduct DDoS drills: Regularly test your DDoS mitigation plan with simulated attacks to ensure your team is prepared for real incidents. Use specialized services for massive attacks and have a response plan in place for third-party DDoS protection providers.
- Continuous monitoring of traffic: It would help detect anomalies in traffic and allow quick responses to abnormal spikes.
Conclusion
DDoS attacks are increasingly prevalent threats in the online world, but organizations can reduce risks and downtime with effective mitigation techniques. Methods such as rate limiting, traffic filtering, Content Delivery Networks (CDNs), and Any cast networks, combined with a solid DDoS mitigation plan, help ensure services remain accessible to legitimate users. To protect against these attacks, organizations should adopt a proactive approach by continuously monitoring traffic and collaborating with DDoS protection services. Cybersecurity Training allows businesses to develop a robust defense system, ensuring their services stay online during disruptions. Layered security and preparation are essential to mitigate the potential impact of DDoS attacks.





