
DevSecOps is a methodology that integrates security practices into the DevOps process, aiming to address security concerns early and continuously throughout the software development lifecycle. By embedding security practices and tools into every stage of development, from design to deployment, DevSecOps promotes a culture of shared responsibility and collaboration among development, operations, and security teams. This approach enables organizations to identify and remediate security vulnerabilities more effectively, enhance compliance with regulatory requirements, and deliver secure and resilient software products to market faster.
1. Explain the term “DevSecOps” and its role in modern software development.
Ans:
- DevSecOps emphasizes security throughout the software development lifecycle.
- It ensures security considerations are built into every stage of development and deployment.
- It aims to automate security testing and compliance checks.
2. Explain the deployment pattern in blue and green to us.
Ans:
Software updates are released using the blue/green technique, which reduces risk and downtime.One production environment (blue) is used to serve users, while the other (green) is idle. Both environments must be maintained in the same way.Once verified, traffic is shifted to the updated Devsecops environment from the idle environment where updates are deployed.
3.How is automation testing carried out?
Ans:
In DevSecOps, automation testing refers to using automated tools and scripts to perform security testing at every stage of the software development lifecycle.Automated security testing tools are integrated into the CI/CD pipeline to continuously check for vulnerabilities, misconfigurations, and compliance issues.Early detection of security flaws, quick developer feedback, and smooth integration of security into the software delivery process are all made possible by automation testing.
4. How might DevOps benefit from continuous testing?
Ans:
- Permits quick comments on modifications to the code.
- Enhances the general dependability and quality of software.
- Finds flaws early in the process of development.
- Supports continuous delivery and quicker release cycles.
5. Describe the DAST for DevOps.
Ans:
- It finds weaknesses by simulating actual attacks.
- DAST tools use application interaction to find security flaws.
- It aids in the prioritization and resolution of security issues in production environments by teams.
6. What kind of responsibilities might a DevOps/DevSecOps architect have?
Ans:
- Create and put into action CI/CD pipelines.
- Ensure that development processes incorporate security measures.
- Automate the deployment and provisioning of infrastructure.
- Verify adherence to legal requirements.
7. Explain a DevOps maturity model with examples.
Ans:
- Culture: Places an emphasis on sharing responsibilities and teamwork.
- Automation: This area of study focuses on automating software delivery process repetitive chores.
- Lean: Seek to reduce waste and enhance processes.
- Measurement: Tracks performance and makes process improvements using metrics.
- Sharing: Promotes openness and information exchange amongst teams.
8. What anti-patterns are there in DevOps?
Ans:
Teams that are isolated and communicate less.Manual procedures that impede agility and automation.The development, operations, and security teams’ lack of cooperation.Insufficient attention to feedback loops and monitoring.Failure to give culture and mentality changes a priority.
9. How are hashing and encryption different?
Ans:
| Aspect | Hashing | Encryption | |
| Purpose |
One-way function used for data integrity verification. |
Two-way process used for data confidentiality. | |
| Reversibility | Non-reversible; cannot be decrypted. | Reversible; can be decrypted with the correct key. | |
| Key usage |
No key required. |
Requires a key for encryption and decryption. | |
| Output | Fixed-size hash value. | Variable-length ciphertext. | |
| Usage |
Data integrity checks, password storage. |
Securing sensitive data during transmission or storage. | |
| Example |
SHA-256, MD5 |
AES, RSA |
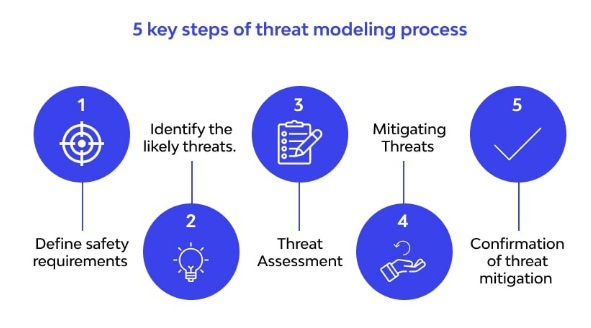
10. What is threat modeling, and how do you proceed?
Ans:
As part of the threat modeling process, a system’s possible threats are identified, their impact and likelihood are evaluated, and mitigating actions are implemented.
- Determine the value of the assets as part of the procedure.
- I am listing all possible dangers and weak points.
- We are evaluating the dangers connected to every hazard.
- We are arranging mitigating actions in order of risk intensity.
- Verify the mitigation techniques’ efficacy, make any necessary adjustments, and record the results to inform future security initiatives and decision-making.
11. How Does SAST Help the DevSecOps Process?
Ans:
- Identification of security flaws in code early on.
- CI/CD pipeline integration for automated security audits.
- It lets developers address problems prior to release.
- Enhances the posture of overall software security.
12. How can code compliance help with DevSecOps operations?
Ans:
In DevSecOps operations, code compliance guarantees that the Code conforms to best practices and industry requirements. Automating security checks during development ensures that security flaws are found and fixed quickly. This reduces the likelihood of security breakdowns and synchronizes development with regulatory standards.
13. How effectively has DevSecOps been implemented across the entire organization?
Ans:
Integration of DevSecOps into organizational processes and culture is critical to its efficacy. When used effectively, it encourages cooperation between the teams responsible for development, security, and operations, resulting in deployments that are quicker, more effective, and safer. However, obstacles like siloed teams, lack of training, and opposition to change may prevent its acceptance.
14. Which security tools are commonly used in the integration of DevSecOps?
Ans:
- Several security products that are frequently used in DevSecOps integration include:
- Instruments for Static Application Security Testing (SAST)
- Technologies for Dynamic Application Security Testing (DAST)
- Tools for Software Composition Analysis (SCA)
- Security Vulnerabilities
- Scanners for Container Security
- Security Information and Event Management (SIEM) systems
15. How does incident response fit into the DevSecOps framework?
Ans:
- Automated security incident detection and alerting.
- Using tools and procedures, issues are analyzed and prioritized quickly.
- Cooperation for a solution between the security, operational, and development teams.
- On the basis of incident input, security defenses are strengthened through ongoing learning and development.
16. What is the significance of DevSecOps employing Infrastructure as Code (IaC)?
Ans:
DevSecOps benefits from using Infrastructure as Code (IaC) because it treats infrastructure configurations as version-controlled code, allowing for automation, consistency, and repetition in infrastructure deployment. It also helps organizations ensure that security is ingrained in their infrastructure from the beginning by implementing security controls and best practices in the infrastructure code.
17. In DevSecOps, why is logging crucial?
Ans:
- Devsecops provide visibility into system activities and security events.
- It Facilitates incident response and forensic analysis.
- It Supports compliance requirements by documenting actions and changes.
- It enables proactive monitoring and detection of security threats.
18. What makes you believe the DevSecOps Cycle’s priority should be SCA?
Ans:
Software Composition Analysis (SCA) is a crucial tool in the DevSecOps cycle since it can identify vulnerabilities in open-source components used in the codebase. Because open-source software is used frequently, SCA ensures these components are secure and up-to-date while preventing potential vulnerabilities from external libraries. Prioritizing SCA helps reduce risk early in the development process.
19. What are the primary obstacles to implementing SCA in practice?
Ans:
- Ignorance about open-source components.
- Trouble keeping track of dependencies.
- Problems with license compliance.
- Opposition to implementing new procedures and instruments.
20. What is the significance of machine-readable output from security tools?
Ans:
- It permits integration and automation with the DevSecOps pipeline.
- Speeds up the process of prioritizing and analyzing security discoveries.
- Results in quicker reaction times.
- Enhances the posture of security overall.
21. How are security issues addressed in a cloud environment?
Ans:
In a cloud environment, security problems are addressed by several methods, including:I am putting identity management and strict access constraints into place.Both in-transit and at-rest data encryption.I am keeping an eye out for security problems and questionable activity.We are patching and updating systems regularly.
22. In contrast to other security techniques, what are some disadvantages of DAST?
Ans:
- Minimal knowledge of the code hierarchy.
- High rate of false positives.
- It is challenging to identify logical mistakes or weaknesses in business logic.
- Automated patches for discovered vulnerabilities are lacking.
23. Describe the importance of including security in the DevOps workflow.
Ans:
- Risk Mitigation: By incorporating security into DevOps workflow, vulnerabilities are found and fixed early on, lowering the likelihood of security breaches.
- Constant Compliance: Throughout the development process, integrating security guarantees conformity to industry standards and legal regulations.
- Enhanced Trust: DevOps teams enhance trust with partners, stakeholders, and customers by putting security first, which benefits the company’s reputation.
- Cost savings: By proactively addressing security concerns early in the software lifecycle, costly security incidents and rework are avoided.
24. What does “shift-left” signify in DevSecOps?
Ans:
The term “shift-left” in the context of DevSecOps refers to the incorporation of security practices and considerations at an earlier stage of the software development lifecycle (SDLC), namely during planning, design, development, and testing, as opposed to delaying until post-production or deployment.By including security measures, automated security testing, and security-focused reviews into the development process from the outside, shifting security left can result in the speeder delivery of dependable and safe software.
25. Why is DevSecOps automation important?
Ans:
- Simplifies the procedures for security validation and testing.
- Improves the repeatability and consistency of security measures.
- It makes it easier to respond quickly to security incidents.
- Permits ongoing security posture monitoring and enhancement.
26. In what ways might DevSecOps techniques mitigate typical security issues in software development?
Ans:
Connecting automated security testing to CI/CD operations.Integrating security examinations and evaluations with code reviews.Implementing policies and guidelines for safe coding. Dependable and secure deployments are made possible by containerization and infrastructure as code (IaC).
27. How can an application be containerized and made more secure?
Ans:
- Make use of container orchestration tools for security management.
- Use trustworthy base pictures in your containers.
- Implement secure coding strategies.
- For sensitive data kept in containers, provide access controls and encryption.
28. What impact does security have when utilizing a microservices architecture?
Ans:
Security is paramount in microservices architecture due to the system’s distributed nature. Each microservice may communicate over a network, making it vulnerable to attacks such as unauthorized access, data breaches, and service disruptions. Strong authentication, encryption, and continuous monitoring are essential to protect each service and the data exchanged.
29. How do you handle sensitive and confidential data in a DevSecOps environment?
Ans:
- Use access-controlled, safe storage solutions.
- Make use of dependable methods for authorization and authentication.
- Encrypt data and employ secure coding strategies to reduce the amount of personal information disclosed.
30. Which best practices are relevant to cloud-based infrastructure security?
Ans:
- Put in place robust identification and access management procedures.
- As you routinely audit and check for security compliance, encrypt data both in transit and at rest.
- Use firewalls and network segmentation.
- Patch and update infrastructure components on a regular basis.
31. How is threat modeling done for a software application?
Ans:
In a DevSecOps context, threat modeling involves locating possible risks to a system or application, estimating their impact and likelihood, and implementing controls and mitigation. It involves cooperation between the development, operations, and security teams to guarantee that security considerations are integrated early in the software development lifecycle.
32. Describe the significance of security code review in DevSecOps.
Ans:
- Early Detection: Early in the development phase, security code review assists in identifying vulnerabilities.
- Risk mitigation: Fixing vulnerabilities before deployment lowers the possibility of security breaches.
- Educational Opportunity: Increases developers’ understanding of security by providing them with insights into secure coding practices.
- Compliance assurance supports overall compliance activities by guaranteeing adherence to security standards and regulatory regulations.
33. How does the CI/CD pipeline incorporate security testing?
Ans:
- Integration Points: Security testing is incorporated into several CI/CD pipeline stages, including the build, test, and deployment phases.
- Automated Scans: Code vulnerability analysis is done automatically as part of the automated build process using automated security scanning technologies.
- Constant Monitoring: Security tests are carried out regularly to provide constant input on the application’s security posture.
- Gatekeeping Mechanism: The findings of security testing serve as gatekeepers, keeping unsafe code from moving farther along the pipeline and guaranteeing that only secure code is implemented.
34. What common security problems occur in multi-cloud environments?
Ans:
Common security problems in multi-cloud setups include inconsistent rules from various cloud providers, misconfigured data breaches, insufficient visibility and monitoring, and difficulties with identity and access control management. These issues may result in vulnerabilities that attackers may exploit if they need to be sufficiently resolved.
35. How can the PCI DSS requirements of an e-commerce application be ensured?
Ans:
Encrypt critical data, including credit card numbers and personal details.When sending financial information over networks, make use of secure communication protocols like TLS/SSL.To limit access to cardholder data, implement permissions and access controls.Conducted routine audits and monitored e-commerce application operations to ensure adherence to PCI DSS regulations.
36. Which tools are available for use in the security testing of static applications (SAST)?
Ans:
- The Fortify Static Code Analyzer (SCA) offers extensive scanning features for locating security flaws in source code.
- Checkmarx Provides static application security testing (SAST) to identify compliance problems and vulnerabilities in code.
- Veracode Static Analysis Makes use of static analysis techniques to find security holes and give developers useful information.
- SonarQube integrates static code analysis technologies to find security flaws, code odors, and technical debt in apps.
37. How can safe authorization and verification be guaranteed inside a DevSecOps framework?
Ans:
- Authentication and permission can be ensured securely in a DevSecOps environment through the following:
- Making use of multi-factor authentication (MFA)
- Making use of strong encryption techniques (such as TLS/SSL)
- Perform regular audits of access controls to identify and stop unauthorized access. Authorize using OpenID Connect or OAuth.
38. How can protection against DDoS attacks be ensured, and what defenses are in place?
Ans:
Protection against DDoS attacks can be guaranteed using techniques like rate limitation, Content Delivery Networks (CDNs) for traffic distribution, and Web Application Firewalls (WAFs). DDoS mitigation services, which can identify and redirect malicious traffic, also help ensure that legitimate users are not impacted by the assault.
39. When it comes to DevSecOps, describe the least privilege and defense-in-depth.
Ans:
To defend against many types of assaults, the “defense-in-depth” strategy entails establishing multiple security control levels. The notion of least privilege is to grant users the bare minimum of access that they require to fulfill their obligations. Ensuring that access privileges are restricted in line with the least privilege principle and incorporating security controls into the development and deployment process at every stage are two ways that DevSecOps puts these ideas into practice.
40. What is the difference between a vulnerability and an exploit?
Ans:
A vulnerability is an opening or flaw that hackers use to gain access to software, networks, operating systems, online applications, websites, and other IT systems. A specific piece of code or attack technique known as an exploit takes advantage of a vulnerability to initiate an attack or gain unauthorized access. An exploit uses a weakness to launch an assault.
41. How are security issues addressed when relying on external parties?
Ans:
By carrying out extensive security evaluations and due diligence before choosing suppliers, organizations can reduce the security risks connected with their reliance on third parties. They also have to create explicit contracts that spell out their obligations and security requirements, audit and regularly monitor the actions of third parties, and have backup plans ready to reduce security lapses or occurrences.
42. Describe the steps needed to release software safely in a DevSecOps context.
Ans:
- The following procedures are involved in software deployment in a DevSecOps environment:
- I am combining security needs with the development process.
- Security testing (SAST, DAST, etc.) is automated in the CI/CD process.
- We are assessing security and weaknesses before putting anything into practice.
- It makes use of secure configuration management and infrastructure as code (IaC).
- Monitoring should continue, and incident response protocols should be implemented to recognize and handle security concerns.
43. How can data security be ensured in transit and at rest?
Ans:
Data sparsity in transit can be guaranteed by safeguarding data using encryption methods like TLS (Transport Layer Security) while it travels across networks. Advanced Encryption Standard (AES) and other encryption techniques should be used to protect data held at rest. In both states, regular audits and access controls are essential for preserving data security.
44. What security vulnerabilities are commonly associated with serverless computing?
Ans:
- Typical serverless computing security vulnerabilities include
- Data exposure from insecure API endpoints
- Unstable dependencies
- Inadequate authorization and authentication systems
- Inadequate capability for monitoring and logging.
45. Describe the function of threat intelligence in DevSecOps.
Ans:
Threat intelligence is the process of obtaining, analyzing, and sharing information on potential security risks, including existing vulnerabilities, attacker tactics, techniques, and procedures (TTPs), and emerging dangers. Threat intelligence in DevSecOps assists businesses in proactively identifying and mitigating security threats by offering insights into potential risks and guiding security decision-making processes.
46. How is encryption used to secure data in a DevSecOps environment?
Ans:
Data encryption protects information in transit and at rest in a DevSecOps environment. It guarantees the protection of sensitive data across the whole development and deployment lifecycle. Encryption is incorporated into automatic procedures to ensure constant security, and keys are safely stored to thwart unwanted access.
47. What best practices exist for secure configuration management?
Ans:
- Software and system updates and patches on a regular basis are examples of secure configuration management best practices.
- I am Using access controls with the least privilege.
- Reduce exposure by configuring firewalls and segmenting the network.
- Implementation of multi-factor authentication and strong password policies.
- System configurations are being watched over and audited to ensure security standard compliance.
48. Explain what DevSecOps is all about and the concept of security by design.
Ans:
The DevSecOps process is one way to integrate security protocols with DevOps, ensuring that security is considered at every stage of the software development lifecycle. Security by design refers to the idea that security is integrated into the system architecture from the start rather than being an afterthought. By taking a proactive stance, vulnerabilities are avoided, and security standard compliance is guaranteed.
49. How can orchestration platforms like Kubernetes for containers be made secure?
Ans:
- Install security updates frequently to harden the Kubernetes infrastructure.
- Limit access according to roles by implementing role-based access control, or RBAC.
- For traffic control between pods, use network policies.
- To find security holes in container images, use tools to scan containers.
50. Describe how to do security testing for mobile applications.
Ans:
Analyzing source code to find vulnerabilities is known as static analysis.Executing the program to find runtime vulnerabilities is known as dynamic analysis.Simulating assaults to find gaps in the app’s protections is known as penetration testing.Evaluating the security of servers and APIs that are connected to the application is known as backend security testing.
51. How can data backup and disaster recovery systems be secured?
Ans:
Backup data should be encrypted to guarantee security even if the backup is corrupted. Put authentication procedures and access controls in place to prevent unwanted users from accessing backup systems. Test the backup and disaster recovery systems on a regular basis to find and fix any flaws or vulnerabilities. Maintain offsite backup data security to guard against physical dangers like theft and natural catastrophes.
52. In modern software development, which secure coding best practices are applicable?
Ans:
- Validate and sanitize all input to thwart injection attacks like cross-site scripting and SQL injection (XSS).
- Effective error management Put in place reliable error handling procedures to shield private data and stop possible exploitation.
- The least privilege concept states that users and components should have only a minimal number of permissions to reduce the possible harm from a security breach.
- Frequent audits of code and security reviews To find and fix security flaws early in the development process, do routine code reviews and security audits.
53. What is the process of implementing network segmentation to enhance security?
Ans:
- Describe the areas under security: Segment the network into discrete security zones based on the degree of trust in the systems and the sensitivity of the information.
- Establish access controls: You can restrict communication between different network components using routers, firewalls, and access control lists (ACLs).
- Watch and note what happens on the network: Spot and handle any illicit or dubious activity by utilizing intrusion detection systems (IDS) and network monitoring technologies.
54. Describe the use of multi-factor authentication (MFA) in a DevSecOps environment.
Ans:
Make it necessary for developers to employ MFA in order to access development environments. For safe access to DevOps technologies, incorporate MFA into the CI/CD pipeline. For extra security during deployment procedures, use biometric authentication or MFA tokens.
55. What are some common security flaws with Internet of Things (IoT) gadgets?
Ans:
- Hardcoded or default credentials represent weak authentication.
- Transmitting data without encryption is known as a lack of encryption.
- Vulnerabilities in device firmware are referred to as insecure firmware.
- Unauthorized data acquisition and improper use of user data are privacy concerns.
56. How can GDPR compliance be maintained while ensuring user data protection?
Ans:
Automated GDPR compliance tests ought to be included in DevSecOps pipelines to ensure adherence to data protection rules.Use tokenization and encryption techniques while creating software to safeguard sensitive user data.Implement access controls and permissions management into DevSecOps technologies to prevent unauthorized access to user data. Find and address any compliance issues by routinely assessing and auditing DevSecOps processes for security vulnerabilities.
57. Which tactics can be used to defend against insider threats?
Ans:
In the DevSecOps environment, access to vital resources is restricted by using the least privileged access criteria.Use tools for user behavior analytics to look for unusual conduct that might indicate insider threats.To guarantee that every member of the DevSecOps team is aware of the dangers posed by insider threats, do extensive background checks and staff training.Use ongoing auditing and monitoring of DevSecOps processes to promptly detect and address any occurrences involving insider risks.
58. Explain the logging and continuous monitoring procedure used for security analysis.
Ans:
- Logging: Keep track of and document system actions and events.
- Constant Monitoring: Look for anomalies and security events by continuously analyzing network traffic and data.
- Alerting: Create alerts in times of possible security breaches or questionable activity.
- Reaction: Take the necessary steps to reduce vulnerabilities and security concerns.
59. How can the security of private data kept in databases be guaranteed?
Ans:
- When sensitive data is in transit or at rest, encrypt it.
- Put authentication and access controls in place.
- Audit and regularly keep an eye out for questionable activity in databases.
- Updates and patches should be applied to fix known vulnerabilities.
60. Describe threat modeling and the role it plays in risk assessment.
Ans:
Determine which applications or systems have vulnerabilities and possible threats. To decide which security measures to prioritize, evaluate the possibility and impact of these risks. Create mitigation plans to successfully handle identified threats. Threat models should be reviewed and updated frequently as new threats materialize or the system changes.
61. In what ways are vulnerability scans and penetration tests different from one another?
Ans:
Vulnerability scans use automated tools to look for known vulnerabilities and misconfigurations in systems, producing an extensive list of possible security problems.Conversely, penetration tests imitate attacks carried out by knowledgeable security experts seeking to exploit weaknesses in a safe setting. This approach offers a more accurate evaluation of an organization’s security posture and the possible consequences of successful attacks.
62. In hybrid cloud setups, what are some common security concerns?
Ans:
- Security configuration errors result in data breaches.
- Absence of visibility between various cloud platforms.
- Insufficient access controls resulting in unapproved entry.
- Data transmission between on-premises and cloud systems raises issues with data integrity and privacy.
63. Outline the procedures used in security testing web applications.
Ans:
- Investigation and reconnaissance
- Vulnerability scanning and evaluation
- Manual testing for prevalent security flaws such as SQL injection, XSS, CSRF, etc.
- Security configuration review
- penetration testing
- security code review.
64. In what ways can data stored in cloud-based storage services be secured?
Ans:
Strong encryption algorithms protect data in the cloud storage service while it is in transit and at rest.To ensure that only those with authority may access the data being stored, strict permissions and access controls should be implemented.Employ techniques such as data masking and anonymization to conceal sensitive information and reduce the likelihood of being detected.Pay close attention to data access and audit activities and review logs for odd activity to promptly detect and handle security incidents.
65. Describe zero-trust security and how DevSecOps procedures relate to it.
Ans:
Zero-trust security is an approach that assumes no trust between people, devices, or systems, regardless of where the devices or systems are located or the network environment in which they operate. Least privilege access, continuous verification, and strict access controls are highly valued. DevSecOps uses zero-trust principles across the development lifecycle to ensure that security is incorporated at each stage of the procedure, from code creation to deployment and operation.
66. Which security procedures work well for the toolchains that DevOps uses?
Ans:
- One of the best security procedures for DevOps toolchains is to include security testing tools such as container scanning, software composition analysis (SCA), dynamic application security testing (DAST), and static code analysis.
- It’s also critical to use infrastructure, employ tools for managing secrets, and enforce safe coding standards as code security measures.
67. Explain how serverless architecture security controls are put into place.
Ans:
- RBAC: Use role-based access control (RBAC) to limit access to resources to just permitted functions by limiting permissions based on roles.
- API Security: Secure APIs using authentication methods like OAuth or JWT to prevent unwanted access and guarantee data integrity.
- Secure Code Practices: To reduce typical vulnerabilities like injection attacks and unsecured setups, follow secure code practices.
- Constant Monitoring: Make use of monitoring technologies to spot irregularities, unlawful access, or strange activity in the serverless environment.
68. How can microservices in a distributed system securely communicate with one another?
Ans:
Before allowing communication, strict authentication protocols should be implemented to verify the authenticity of microservices. Encryption is used to protect data transit across microservices and ensure confidentiality and integrity. Use API gateways to control authentication, enforce security policies, and encrypt microservices’ connections. Establish encrypted communications using secure communication protocols, like HTTPS or TLS, to prevent manipulation or eavesdropping.
69. How may unauthorized access to CI/CD pipelines be prevented best?
Ans:
- Update pipeline components frequently to fix vulnerabilities that are known to exist.
- To stop unwanted use, restrict pipeline access based on roles and responsibilities.
- Use programs designed to handle and store private data, including tokens, passwords, and API keys, in an encrypted manner.
- Install monitoring tools to identify odd or suspicious activity in CI/CD pipelines, indicating possible security lapses.
70. Describe how encryption is put into practice to protect data while it is being transferred.
Ans:
- Transport Layer Security (TLS): Encrypt data as it travels over networks by using TLS protocols.
- HTTPS Protocol: Use HTTPS to provide safe online communication between clients and servers.
- Public Key Infrastructure (PKI): Use PKI to enable safe key exchange and confirm the legitimacy of communication endpoints.
Use end-to-end encryption techniques to make sure that data is encrypted as it travels from the originator to the destination, avoiding eavesdropping or interception.
71. In what ways can a DevSecOps environment safeguard the security of container registries?
Ans:
- Put access controls in place: Use roles and permissions and limit access to container registries.
- Constant scanning: To find vulnerabilities in images, incorporate container security scanning into CI/CD pipelines.
- Image signing: To confirm the legitimacy and integrity of container images, use cryptographic signatures.
- Patching vulnerabilities: Update and patch container images on a regular basis to fix known security flaws.
72. In containerized environments, what are some typical security challenges?
Ans:
Making sure container images are routinely checked and patched is known as vulnerability management. Isolating containers guarding against unapproved access and breakout attacks. Container orchestration technologies, such as Kubernetes, should be protected against abuse or hacking through orchestration security. Restricting lateral movement and network-based attacks on containerized applications is known as network security.
73. In what ways are serverless functions that run in the cloud secure?
Ans:
- Isolation: By operating in segregated settings, serverless functions lower their attack surface.
- Managed Security: Cloud providers handle patching and updates for the underlying infrastructure.
- Authorization: To limit access to serverless operations and resources, apply fine-grained access controls.
- Runtime Protection: Use runtime security technologies to monitor and defend against abnormalities and threats at runtime.
74. Which security procedures are the best for cloud-based storage services?
Ans:
- Encryption: To safeguard data both in transit and at rest, use robust encryption techniques.
- Access Control: To prevent unwanted access to data that has been stored, strictly limit access and permissions.
- Monitoring and Auditing: Monitor data access, check logs for unusual activity, and audit activities.
- Management of Compliance: Assure adherence to pertinent laws and industry norms pertaining to privacy and data security.
75. Describe how to put secure monitoring and logging into a DevSecOps environment:
Ans:
Implement centralized logging solutions to aggregate logs from various components within the DevSecOps environment.Utilize security information and event management (SIEM) systems to analyze logs for security incidents and anomalies.Implement real-time monitoring and alerting mechanisms and ensure logs are encrypted during transmission and storage to prevent unauthorized access.Regularly review and analyze logs to identify security issues and improve the overall security posture of the environment.
76. In what ways can data security during microservices transfers be guaranteed?
Ans:
Utilize encryption mechanisms such as TLS/SSL to encrypt data during transit between microservices. Implement mutual TLS (mTLS) for authentication and encryption of communication between microservices. Utilize secure communication protocols and standards to ensure data integrity and confidentiality during transfers.
77. Describe the steps involved in putting infrastructure as code through automated security testing:
Ans:
Define security policies and standards for infrastructure as code (IaC) implementations. Integrate security testing tools into the CI/CD pipeline to automatically scan IaC templates for security vulnerabilities and implement static code analysis to identify security issues in IaC scripts. Utilize dynamic infrastructure scanning tools to assess the security posture of deployed infrastructure. Implement automated security checks and validations as part of the deployment process to enforce security policies.
78. Which typical security issues do distributed systems face?
Ans:
- Data breaches, unauthorized access, and distributed denial-of-service (DDoS) attacks.
- Insecure communication between distributed components.
- Lack of centralized security management and monitoring.
- Vulnerabilities in distributed system components and dependencies.
79. In what ways can sensitive data stored in distributed databases be secured?
Ans:
- Implement encryption for data at rest and in transit.
- Utilize access controls and permissions to restrict who can access sensitive data.
- Implement auditing and logging mechanisms to track access to sensitive data.
- Regularly audit and monitor distributed database activity for any suspicious activity or unauthorized access.
80. Describe immutable infrastructure and its function in DevSecOps.
Ans:
Immutable infrastructure refers to infrastructure that is created once and never modified in place.In DevSecOps, immutable infrastructure ensures consistency and reliability by preventing unauthorized changes and reducing the attack surface.Security patches and updates are applied by deploying new instances of immutable infrastructure rather than modifying existing instances, minimizing security risks and vulnerabilities.
81. What are the recommended practices for securing publicly accessible APIs?
Ans:
Encrypting data while it’s in transit with HTTPS, implementing robust authentication and permission procedures, and implementing rate limitations to prevent misuse are just a few of the procedures involved in securing publicly available APIs. To further defend against injection attacks, input validation and output encoding should be used, and Frequent security audits must be carried out to find and fix vulnerabilities.
82. What steps are involved in secure configuration management for cloud-based infrastructure?
Ans:
- Define security configuration baselines for cloud-based infrastructure components.
- Utilize configuration management tools to automate the deployment and enforcement of security configurations.
- Regularly audit and validate configurations against security standards and best practices and implement change management processes to track and review configuration changes.
- Utilize infrastructure as code (IaC) practices to ensure consistency and repeatability in configuration deployments.
83. In a multi-tenant environment, how can serverless applications be made secure?
Ans:
- Implement strong authentication and authorization mechanisms to ensure isolation between tenants.
- Utilize encryption algorithms such as AES to encrypt sensitive data before storing it in databases or storage systems.
- Store encryption keys securely and separately from the encrypted data to prevent unauthorized access.
- Implement access controls and permissions to restrict who can decrypt and access encrypted data.
- Regularly rotate encryption keys and audit encryption configurations for compliance with security policies and standards.
84. Which best practices exist for protecting servers used for continuous integration?
Ans:
Implement strong authentication mechanisms and access controls to restrict access to CI servers. Regularly update and patch CI server software to address security vulnerabilities. Utilize network segmentation and firewalls to isolate CI servers from other internal networks. Implement logging and monitoring mechanisms to detect and respond to security incidents on CI servers.
85. How can the security of data kept in NoSQL databases be guaranteed?
Ans:
- Implement encryption for data at rest and in transit.
- Utilize access controls and permissions to restrict who can access and modify database records.
- Regularly audit and monitor database activity for any unauthorized access or suspicious activity.
- Implement database-level encryption features provided by NoSQL database vendors.
86. What are a few typical security issues in environments using edge computing?
Ans:
- Lack of physical security: Edge devices may be deployed in uncontrolled environments, making them susceptible to physical tampering or theft.
- Network vulnerabilities: Edge devices often connect to the internet or other networks, increasing the attack surface and potential for network-based attacks.
- Data privacy concerns: Edge computing involves processing and storing sensitive data closer to the source, raising concerns about data privacy and compliance with regulations.
- Limited security controls: Edge devices may have limited processing power and memory, making it challenging to implement robust security controls and encryption mechanisms.
87. Explain how to put safe authentication methods for APIs into place.
Ans:
Implement OAuth 2.0 or API keys for authentication to ensure secure access to APIs. Utilize HTTPS/TLS for encrypted communication between clients and APIs to prevent eavesdropping and data interception. Implement rate limiting and throttling to prevent abuse and denial-of-service attacks on APIs. Utilize strong password policies and multi-factor authentication (MFA) to enhance authentication security. Regularly audit and monitor API access logs for any unauthorized access or suspicious activity.
88. In a distributed system, how can data transferred between services be secured?
Ans:
Utilize encryption protocols such as TLS/SSL to encrypt data in transit between services. Implement mutual TLS (mTLS) for authentication and encryption of communication between services. Utilize service meshes or API gateways to enforce security policies and monitor communication between services. Implement access controls and permissions to restrict access to sensitive data during transfers between services.
89. What are some recommended procedures for protecting serverless databases hosted in the cloud?
Ans:
- Implement encryption for data at rest and in transit to protect sensitive data stored in serverless databases.
- Utilize access controls and permissions to restrict who can access and modify database records.
- Regularly audit and monitor database activity for any unauthorized access or suspicious activity.
- Implement database-level encryption features provided by cloud providers to enhance data security.
90. What does serverless security mean, and how does it relate to DevSecOps?
Ans:
Serverless security refers to ensuring the protection of data, applications, and infrastructure within serverless computing environments. It involves implementing security measures to address risks associated with serverless architectures, such as data breaches, unauthorized access, and runtime vulnerabilities. With DevSecOps, serverless security entails integrating security practices early in the development lifecycle, automating security testing and compliance checks, and continuously monitoring and securing serverless deployments to maintain a strong security posture throughout the development and operations processes.
91. How can secure communication be implemented between serverless functions?
Ans:
- Utilize HTTPS/TLS for encrypted communication between serverless functions.
- Implement mutual TLS (mTLS) for authentication and encryption of communication between functions.
- Utilize secure communication protocols and standards to ensure data integrity and confidentiality during transfers between functions.
92. How can the data handled by serverless applications be made secure?
Ans:
- Implement encryption for data at rest and in transit.
- Utilize access controls and permissions to restrict who can access and modify sensitive data handled by serverless applications.
- Regularly audit and monitor application activity for any unauthorized access or suspicious activity.
93. What are a few secure serverless API best practices?
Ans:
- Utilize rate limiting and throttling to prevent abuse and denial-of-service attacks on serverless APIs.
- Implement encryption for data transmitted over APIs using secure communication protocols such as TLS/SSL.
- Implement access controls and permissions to restrict access to sensitive APIs and resources.
94. Explain how serverless applications can benefit from secure logging and monitoring.
Ans:
Secure logging and monitoring provide visibility into serverless application activity, helping to detect and respond to security incidents.It enables organizations to monitor for unauthorized access, suspicious behavior, and potential security threats.Secure logging ensures that logs are encrypted and stored securely to prevent tampering or unauthorized access.Monitoring allows organizations to proactively identify security vulnerabilities and compliance issues in serverless applications.
95. Explain how encryption is put into practice in a serverless environment to protect data.
Ans:
Encryption is applied to sensitive data before storage or transmission within serverless applications. Data at rest is encrypted using encryption algorithms such as AES, and encryption keys are securely managed and stored. Data in transit is encrypted using secure communication protocols such as TLS/SSL to prevent eavesdropping and interception.
96. Among serverless deployment models, what are some typical security issues?
Ans:
- Insecure configuration: Misconfigured serverless functions or resources may lead to security vulnerabilities.
- Function event data exposure: Exposing sensitive information in function event data can lead to data breaches.
- Injection attacks: Inadequate input validation may lead to injection attacks such as SQL injection or code injection.
- Third-party dependencies: Vulnerabilities in third-party dependencies or libraries used in serverless functions can pose security risks.
97. In a healthcare application, how can HIPAA compliance be guaranteed?
Ans:
- Encrypt patient data both in transit and at rest to prevent unauthorized access.
- Conduct regular risk assessments and audits to identify and address security vulnerabilities.
- Train employees on HIPAA regulations and security best practices to ensure compliance.
98. Give an explanation of the security policy implementation process in code.
Ans:
The security policy implementation process in code involves:
- We are defining security policies and requirements based on regulatory standards and organizational needs.
- I am translating these policies into code by implementing access controls, encryption mechanisms, input validation, and error handling.
- We are conducting code reviews and testing to ensure compliance with security policies.
- I am documenting and maintaining security policies and controls to support ongoing compliance efforts.
99. Which are the best ways to secure API gateways?
Ans:
Implement strong authentication mechanisms such as OAuth 2.0 or API keys to control access to APIs. Enforce strict authorization policies to limit the actions users can perform through the API gateway. Utilize encryption techniques like TLS/SSL to secure data transmission between clients and the API gateway. Regularly update and patch the API gateway software to address known security vulnerabilities and ensure a robust security posture.






