
- Introduction to End to End Encryption (E2EE)
- How End to End Encryption Works
- Advantages of End to End Encryption
- Uses of End to End Encryption
- Challenges in Implementing E2EE
- Future of End to End Encryption
- Conclusion
End to End Encryption (E2EE) is one of the most important security measures used in a communication system to encrypt data sent from one party and ensure it remains private from third parties. In Cybersecurity Training Courses interconnected digital world, End to End Encryption has become vital for keeping data private and secure. The blog will explore the concept of End to End Encryption, its working, its application, and why it is important for protecting sensitive data, ensuring data protection, and maintaining data privacy in various domains.
Are you curious to know more about Cybersecurity ? Take advantage of our comprehensive online Cyber Security Online Training .
Introduction to End to End Encryption (E2EE)
E2EE End to End Encryption refers to the encryption method for data transfer. The data is encrypted at the sender’s end, and only the recipient can decrypt it. The encryption technique ensures that no hacker, service providers, or platform administrators can read the data in transit. This provides privacy for users, as the most basic objective of End to End Encryption is to safeguard private information and sensitive data from unwanted access. With increased cyber attacks and data breaches happening in the current world, End to End Encryption is one of the core security protocols for secure communication platforms, online services, and applications handling sensitive data such as messaging services, email platforms, and financial transactions. To achieve this level of security, cryptography algorithms are employed. These algorithms play a critical role in securing data, ensuring that encryption keys are robust, and preventing unauthorized access to private information. Cryptography algorithms underpin the encryption methods used in E2EE, making it a powerful and reliable solution for protecting sensitive data. The choice of cryptography algorithms directly affects the security of the encrypted data. These algorithms ensure that, even if data is intercepted during transmission, it remains unreadable and secure, thus providing a strong foundation for effective cipher encryption provides privacy for users, as the most basic objective of End to End Encryption is to safeguard private information and sensitive data from unwanted access.With increased cyber attacks and data breaches happening in the current world, End to End Encryption is one of the core security protocols for secure communication platforms, online services, and applications handling sensitive data such as messaging services, email platforms, and financial transactions.
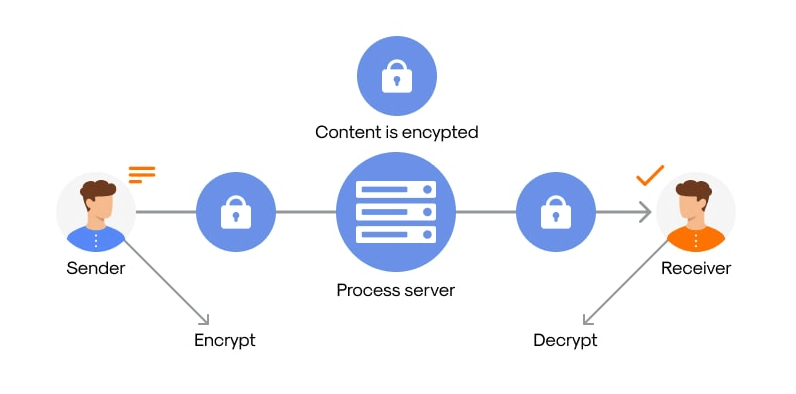
How End to End Encryption Works
- Sender’s Side: The sender writes the message or data they want to send. The message gets encrypted using the recipient’s public encryption key. The encryption key is available to the general public and is used to encrypt the data however, it will never be able to decrypt that data.
- Transmission: The sent, encrypted message is relayed through the network to the recipient. In the process of movement through the network, even if the intercepted message is read, it would never be possible because of being encrypted with strong cryptographic techniques.
- Recipient’s End: The recipient decrypts the message using their private key, which they alone own.Once decrypted, the message is readable to the recipient. The essence of E2EE is that only the recipient, who has the corresponding private key, can decryption in cybersecurity and read the original message. Neither the service provider nor any intermediary in transmitting the message can view its data protection contents.
- Privacy Protection: End to End Encryption ensures that sensitive data exchanged between two parties cannot be accessed by other people or organizations. This is especially important for data privacy involving financial transactions, medical records, and business communication.
- Data Interception Prevention: Since End to End Encryption encrypts the data, it is impossible to intercept it during its transmission because it will appear unreadable to anyone but the recipient. Thus, hackers or malicious actors cannot steal or tamper with the information.
- Secure Communication: By ensuring only the intended recipient can read the data, End to End Encryption establishes trust between the communicating parties. This is particularly important for messaging services, email platforms, and online banking applications that handle sensitive data and financial transactions.
- Protects Data Integrity: End to End Encryption also prevents tampering with sensitive data. No matter how many times they intercept the message, they cannot alter Cybersecurity Training Courses content because they cannot get the encryption key that will be used to decrypt it.
- Regulatory Compliance: Many industries, such as healthcare and finance, have legal requirements to safeguard sensitive data. End to End Encryption assists organizations in compliance with data protection regulations such as HIPAA, GDPR, and CCPA, which insist that encryption and cryptographic techniques be used for secure communication and End to End Encryption.
- Key Management: The problem of encryption key management plagues End to End Encryption. The encryption key pair needs to be stored and transmitted securely. Sensitive data can become inaccessible if the private encryption key is lost or compromised.
- Performance Impact: Overheads come in with encryption and decryption processes, which slows the system, especially with large data volumes and real-time communications. Hence, this can be a pain with high-speed data applications requiring secure communication.
- Complexity: End to End Encryption is complex and difficult to deploy among developers and organizations. That entails getting to know the right cryptographic techniques, which often go wrong with improper configuration, Network Topology resulting in mishaps.
- Regulatory Pressure: Governments have forced backdoors in encrypted communication systems in some countries to assist law enforcement. Including backdoors can undermine the security of End to End Encryption, making it a contentious issue for End to End Encryption developers and digital privacy advocates.
- Complexity: End to End Encryption is complex and difficult to deploy among developers and organizations. That entails getting to know the right cryptographic techniques, which often go wrong with improper configuration, resulting in mishaps.
- User Education: Users must be made aware of the significance of End to End Encryption and how it works. If users do not understand the encryption process or follow best security practices, the efficacy of End to End Encryption may be compromised.
Want to learn more about Cybersecurity ? Enroll in our Complete Cyber Security Online Training.
Advantages of End to End Encryption
Uses of End to End Encryption
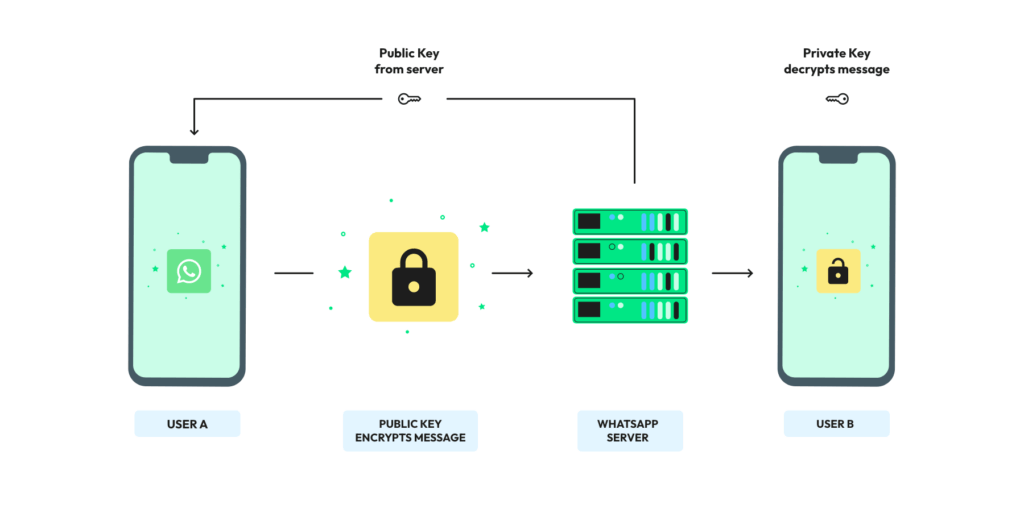
Messaging services such as WhatsApp, Signal, and Telegram rely on End to End Encryption to safeguard users privacy by ensuring that only the sender and recipient can access the contents of their messages. This encryption prevents even the platform providers from reading the messages. Similarly, email services like ProtonMail and Tutanota implement End to End Encryption to guarantee that emails remain confidential and only the intended recipient can read them. Cloud storage and file-sharing platforms, such as Tresorit and Sync.com, also use End to End Encryption to protect files during upload, storage, and download, ensuring that only authorized users can access the files.
In the financial sector, End to End Encryption is crucial for securing financial transactions on platforms like PayPal and credit card companies, protecting transaction details from potential interception or alteration. The healthcare industry also benefits from End to End Encryption, as it helps protect sensitive data, including medical records and personal health information (PHI), ensuring compliance with data privacy regulations like HIPAA. Additionally, video conferencing tools such as Zoom and Microsoft Teams utilize End to End Encryption to secure communication, encryption in network security ensuring only authorized participants can access the video and audio feeds during meetings.
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Today!
Challenges in Implementing E2EE
Preparing for Cyber Security job interviews? Check out our Cyber Security Interview Questions and Answers now!
Future of End to End Encryption
The importance of End to End Encryption is only set to grow as more services and platforms move toward digital-first models. With growing concerns over data privacy and security, especially after high-profile breaches, the demand for End to End Encryption solutions is expected to increase. As businesses and consumers become more aware of cybersecurity and digital privacy, End to End Encryption will continue to be a critical component in protecting sensitive data, building trust, and ensuring secure communication in the digital world. Looking ahead, Quantum Encryption is poised to become a key development in the field of cybersecurity. This advanced encryption technique is being developed as a response to the rise of quantum computing, which threatens to undermine traditional Cryptographic Techniques . The arrival of quantum computers could potentially break current encryption standards, which rely on mathematical problems that would be solvable by quantum processors. In this context, Quantum Encryption will play a crucial role in ensuring that data remains secure, even in a future where quantum computing becomes more widespread. The next step in Quantum Encryption involves creating algorithms that can withstand the power of quantum computers. These Quantum Encryption methods will provide the next generation of secure communication, addressing the vulnerabilities of today’s encryption systems. As such, quantum-safe cryptographic techniques are already in development to ensure that encryption solutions remain robust in the quantum era. At the same time, regulatory frameworks will continue to be further developed and challenged for platforms adopting End to End Encryption, as they struggle with the balance between data privacy and national security concerns. Governments and law enforcement agencies face the challenge of adapting to evolving encryption standards while ensuring they can still access necessary information for security purposes. As these frameworks evolve, the need for secure, quantum-resistant encryption will be more critical than ever.
Conclusion
End to End Encryption is an essential tool in modern cybersecurity that ensures sensitive data remains secure, private, and tamper-proof during transmission. With the number of cyber threats and privacy breaches increasing daily, End to End Encryption is more critical than ever. Whether for personal communication, online financial transactions, or business operations, End to End Encryption plays an important role in maintaining data privacy and security.The future of End to End Encryption seems bright, with constant innovations in encryption key management, cryptography algorithms, and a growing adoption rate across all sectors of Cybersecurity Training . Cryptography algorithms are fundamental in ensuring the effectiveness of encryption methods, providing the necessary security to protect sensitive information from unauthorized access.As privacy concerns and cybersecurity threats continue to escalate, the demand for robust encryption solutions will only continue to rise, reinforcing its importance in securing digital communications.





