
- Introduction
- What is Hashing?
- How Hashing Works
- What is Encryption?
- How Encryption Works
- Key Differences Between Hashing and Encryption
- When to Use Hashing and Encryption
- Conclusion
Hashing and encryption are both cryptographic techniques, but they serve different purposes. Hashing is a one-way process that transforms data into a fixed-size hash, typically used for data integrity and password storage. In contrast, encryption is a reversible process designed to protect data confidentiality, ensuring that only authorized parties can access the original information. This concept is a fundamental topic covered in Cyber Security Training Courses, where students learn how encryption techniques safeguard sensitive data and prevent unauthorized access. Hashing is commonly used for verifying data integrity, while encryption is essential for securing sensitive data during transmission or storage. Understanding these key differences helps in selecting the appropriate technique based on the specific security needs.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Introduction
Hashing and encryption are two fundamental concepts in cybersecurity that play a crucial role in protecting digital information. While both mechanisms are designed to enhance data security, they serve distinct purposes and operate in different ways. Hashing is primarily used to ensure data integrity by converting information into a fixed-length value, making it ideal for storing passwords and verifying data authenticity. On the other hand, encryption focuses on data confidentiality by converting plaintext into ciphertext, ensuring that only authorized parties can access the original information. This is an essential practice in Cyber Hygiene, which emphasizes maintaining secure systems and safeguarding sensitive data through encryption and other protective measures. Understanding the key differences between hashing and encryption is essential for implementing the right security measures in various applications, whether for safeguarding user credentials, securing online transactions, or protecting sensitive data in transit. In this blog, we will explore the concepts of hashing and encryption, their key differences, and the scenarios where each should be used to maximize security.
What is Hashing?
- MD5 (Message Digest Algorithm 5): Widely used, but now insecure and vulnerable.
- SHA-1 (Secure Hash Algorithm 1): Widely used but deprecated for the same reasons as MD5.
- SHA-256: A member of the SHA-2 family of cryptographically secure hash functions; it is constantly being used for security protocols and as a part of blockchain technologies.
- The Encryption Key: That secret key to which both encryption and decryption are done.
- The Algorithm: A mathematical procedure that mixes the data using the encryption key.
- Encryption can be symmetric: (the same key is used for both encryption and decryption) or asymmetric (different keys are used for encryption and decryption, such as in public-key cryptography). Common Encryption Algorithms:
- AES (Advanced Encryption Standard): A symmetric encryption algorithm widely used in various security applications.
- RSA (Rivest-Shamir-Adleman): Asymmetric encryption algorithm, widely used for secure data transmission.
- Blowfish: Symmetric-key block cipher, fast and effective.
- Purpose: Hashing is mainly deployed for data integrity and verification purposes. It essentially produces a distinctive representation of the data (known as the hash) that ensures the data wasn’t changed in any way. Encryption is meant to ensure the secrecy of data; its objective is to make it unreadable and accessible only to authorized users based on the possession of the corresponding decryption key.
- Reversibility: Hashing is one way and cannot be reversed. In other words, data that is hashed cannot ever be reversed and made into original data. Hashing is great for storing passwords. When a password is hashed there is no easy way to extract the original password from the hash. Encryption is two-way and reversible. Encrypted data can be decrypted back into its original form using the correct decryption key. This makes encryption well-suited for scenarios where data needs to be accessed in its original form by authorized users. Use Cases:
- Secure storage of passwords.
- Checking data integrity, such as file checksums.
- Digital signatures in cryptography.
- Encryption is widely used for Protecting sensitive data in transit (for example, over HTTPS or VPN).
- Protecting files and data at rest.
- Secure communication between two parties.
- You need to store sensitive data securely, where the data will never be retrieved in its original form.
- You must be sure that data is valid and not tampered with, without having access to the data itself.
- You work with one-way operations, such as determining whether two pieces of data are the same (for example, verifying files or messages). Apply Encryption when:
- You want to maintain the confidentiality of your data, especially when transporting or storing sensitive information.
- You want to restore data to a previous version once it has been encrypted.
- Your operation is bidirectional, like in the case of secure messaging or file storage.
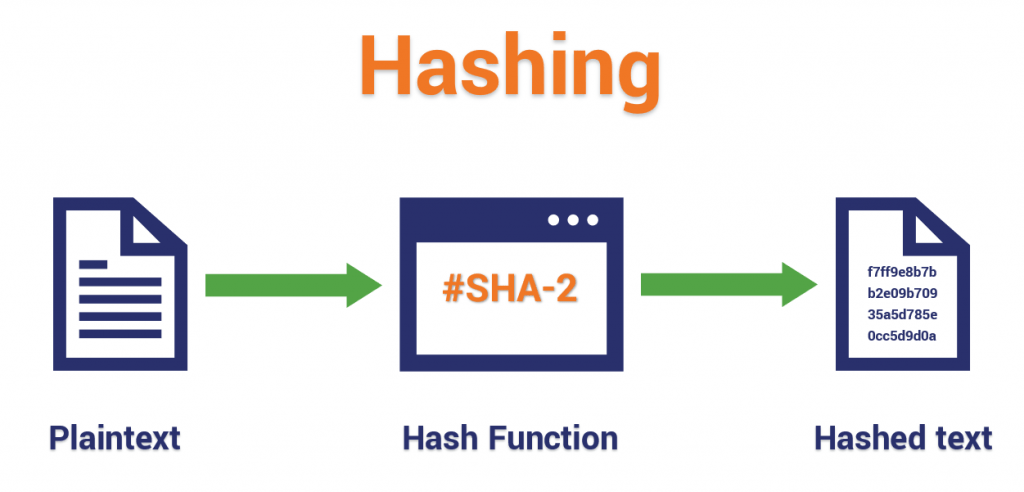
Hashing is a cryptographic data transformation process whereby data of any size is converted into a fixed-length string of characters, commonly referred to as a hash code or digest. This hash serves as a unique representation of the original data, making it useful for various security applications. Unlike encryption, which allows data to be decrypted back to its original form, hashing is a one-way function, meaning that once data is hashed, it cannot be reversed to reveal the original input. Understanding this difference is crucial in fields like Network Topology, where both encryption and hashing play vital roles in securing data and ensuring the integrity of communication across networks. Hashing is widely used in secure password storage, ensuring data integrity, and maintaining consistency in databases. It helps protect sensitive information by preventing direct access to the original data.
In password storage, for example, instead of saving actual passwords, systems store their hash values. When a user logs in, the entered password is hashed and compared with the stored hash to verify authenticity. This approach enhances security, as even if a database is compromised, attackers cannot easily retrieve the actual passwords.
Are You Interested in Learning More About Cybersecurity? Sign Up For Our Cyber Security Online Training Today!
How Hashing Works
A hashing algorithm processes an input (such as a password, file, or message) and produces a fixed-size hash value. This hash is unique to the specific input data, ensuring that even the smallest change in the input results in a completely different hash output. For example, modifying a single character in a document will produce an entirely different hash value, making it easy to detect unauthorized alterations. One of the key properties of hashing is that it is deterministic meaning the same input will always produce the same output. This property is essential when using Container Security Tools, where hashes are often used to verify the integrity of containers and ensure that their contents have not been tampered with. Additionally, hashing functions are designed to be collision-resistant, ensuring that different inputs do not produce the same hash. This makes hashing an essential tool for data verification, digital signatures, and cryptographic applications. Since hashing is a one-way process, it is particularly useful in scenarios where storing or verifying data is required without the need to retrieve the original input. It is extensively used in cybersecurity for protecting sensitive information, verifying file integrity, and securing blockchain transactions.
Some Common Hashing Algorithms:What is Encryption?
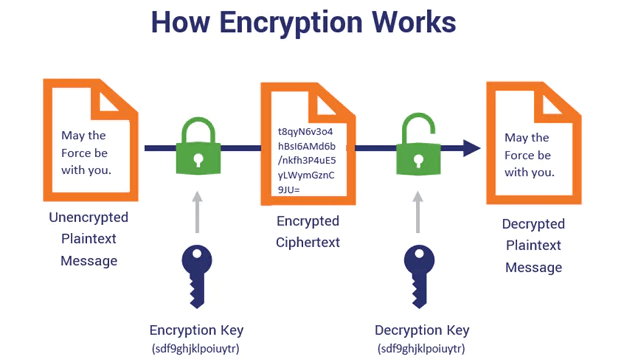
Encryption is the process of transforming plaintext data, such as a message, document, or file, into a scrambled, unreadable format called ciphertext using an encryption algorithm and a secret encryption key. This transformation ensures that unauthorized parties cannot access or understand the original data without the appropriate decryption key. Encryption is a fundamental component of modern cybersecurity, playing a crucial role in protecting sensitive information from cyber threats, unauthorized access, and data breaches. It is widely used in various applications, including secure communication, online transactions, digital file storage, and protecting confidential business or personal data. Cyber Security Training Courses provide in-depth knowledge of these applications, teaching students how encryption plays a key role in securing data and maintaining privacy in today’s digital world.The primary purpose of encryption is to ensure data confidentiality, whether the data is in transit (being transmitted over networks) or at rest (stored on devices or cloud servers). Unlike hashing, which is a one-way function designed for data integrity verification, encryption is a two-way process. This means that once the data is encrypted into ciphertext, it can be decrypted back into its original readable form using the appropriate decryption key.
Are You Considering Pursuing a Cybersecurity Master’s Degree? Enroll For Cyber Security Expert Masters Program Training Course Today!
How Encryption Works
During the encryption process, an encryption algorithm takes the original plaintext data and transforms it into ciphertext using a specific encryption key. The strength and complexity of encryption depend on the algorithm used, such as AES (Advanced Encryption Standard), RSA (Rivest-Shamir-Adleman), or DES (Data Encryption Standard). These algorithms use mathematical computations to scramble the data in a way that makes it nearly impossible to decipher without the corresponding decryption key. To decrypt the data, the system or authorized user must possess the correct decryption key, which reverses the encryption process and converts the ciphertext back into its original plaintext form. This mechanism ensures that even if encrypted data is intercepted during transmission or stored in an unsecured location, it remains inaccessible and unreadable to unauthorized parties.
Key Differences Between Hashing and Encryption
Hashing and encryption are two important concepts in the field of cybersecurity that are often confused with each other. Although both are used to secure data, they are used for different purposes and have different characteristics. Hashing is typically used for verifying data integrity, while encryption focuses on protecting the confidentiality of data during transmission or storage. Both techniques are critical in a Zero Trust Security model, where every request and data exchange is treated as untrusted until verified, ensuring that only authorized entities can access or alter sensitive information. The key differences between these two methods lie in their functionality and application. Understanding when and how to use each is crucial for proper data protection and security. Here are the key differences between them:
When to Use Hashing and Encryption
Knowing when to use hashing and encryption is crucial for implementing the correct security measure based on the specific needs of the data or system. Both techniques are essential in cybersecurity, but each serves a distinct purpose depending on the use case. For example, Firewall and Antivirus Software often work alongside encryption and hashing to protect networks and systems, ensuring that data is not only secure but also that malicious activity is detected and prevented. Understanding their differences and when to apply them ensures that data is protected effectively and appropriately.
Use Hashing when:Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Conclusion
Hashing and encryption both play vital roles in cybersecurity, each serving a distinct yet equally important function in protecting data. Hashing is primarily used to maintain data integrity and security by generating a fixed-length, one-way representation of information that cannot be reversed or decrypted. This makes it ideal for securely storing passwords, verifying file integrity, and ensuring data authenticity.On the other hand, encryption is designed to protect data confidentiality by transforming plaintext into ciphertext using cryptographic algorithms. This critical concept is explored in Cyber Security Training Courses, where learners gain hands-on experience with various encryption methods to understand how they secure sensitive information in different contexts. Unlike hashing, encryption is a reversible process, meaning that the original data can be retrieved if one possesses the correct decryption key. Understanding the differences between these two techniques is essential for implementing proper security measures, especially when dealing with sensitive data such as passwords, financial transactions, personal records, and confidential communications.





