
- What is Whitelisting
- How Whitelisting Works
- Benefits of Whitelisting
- Challenges and Limitations
- Whitelisting vs Blacklisting
- Types of Whitelisting
- Best Practices in Implementing Whitelisting
- Conclusion
Protecting Systems Against Nefarious Attacks The best and most effective way to mitigate risks in cybersecurity is to allow listing. Allowlisting is a proactive security measure that can prevent unauthorised access and even minimise cyber awareness. This blog will explain what allow listing is, how it works, its types, benefits, and limitations, and why it is an important tool in modern cybersecurity strategies.
What is Whitelisting
Whitelisting in cybersecurity is listing a list of accepted entities, such as applications, whitelist ip address, or email addresses, that are granted permission to enter a specific network, system, or resource. It differs from blocklisting because it assumes a more conservative approach: only items on the approved list are allowed, and everything else is denied by default. Compared to reactive measures for known threats, Cybersecurity Training Courses is considered a proactive security measure since it provides permission based on trust. Organisations can highly minimise their exposure to security risks, such as malware, ransomware, and other cyberattacks, by avoiding the execution of only those verified and trusted applications or communications from trusted sources.
Enroll in ACTE’S Cyber Security Online Training if you want to become an expert in cyber security field and have a prosperous career.
Whitelisting ‘s proactive nature makes it an effective tool for preventing known malware, zero-day attacks, and emerging threats that have yet to be identified or catalogued by traditional blocklisting systems. By allowing only pre-approved, trusted applications and communications to interact with the network, organisations can significantly reduce their vulnerability to new and unknown exploits. This approach is particularly valuable in environments where high levels of security are required, such as financial institutions, healthcare providers, or critical infrastructure sectors, where even a single breach could lead to significant economic loss or reputational damage. Despite its benefits,cyber incident response, whitelist antivirus careful management and frequent updates to remain effective, as new applications or legitimate users may need to be added to the approved list.
How Whitelisting Works
- First, an organisation will define and create a list of entities deemed “safe” or “trusted.” Such a list can include approved software, trusted whitelist ip address, verified email senders, etc.
- Whenever the system accepts an access request, be it an app trying to run, an email trying to enter the inbox, or an external IP trying to connect to a network, it checks against the allowlist. Access is allowed if the entity is on the list, if not, it is blocked.
- The allowlist is constantly updated with the new set of applications, users, or whitelist ip address trusted. Organisations continually look for emerging threats and update the allowlists based on their new threats or software versions.
- This model reduces a system’s attack surface since only approved entities will be granted access to the system, and malicious actors’ chances of exploiting vulnerabilities are minimised.
- Whitelisting enables greater control over system access, as organisations can specifically define who or what is allowed to interact with their critical systems and data. This control is essential in highly regulated industries, where compliance with strict security standards is necessary.
- By implementing whitelist antivirus, organisations can demonstrate a more stringent approach to cyber protection. Packet Filtering Firewall proactively limit the scope of who can access sensitive information and resources. This also helps mitigate the risk of insider threats, as only authorised users and applications can perform actions on the system.
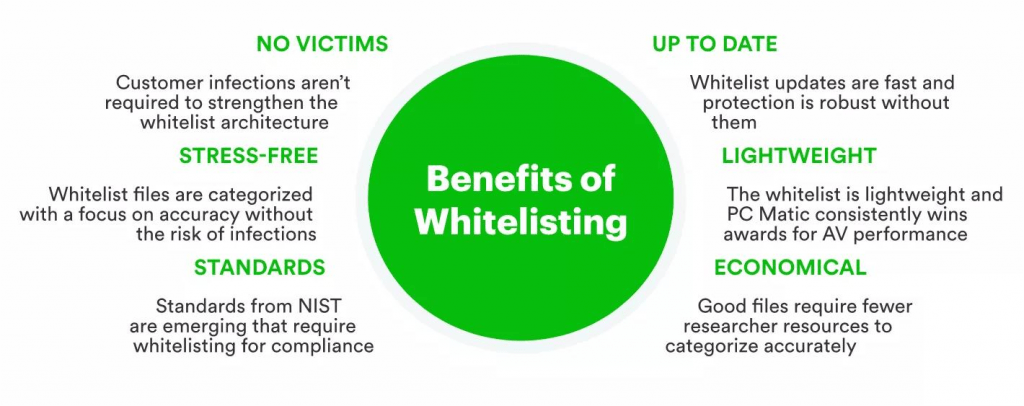
Benefits of Whitelisting
Whitelisting reduces probable entry points for cyber awareness since only approved entities are allowed to interact with a system, reducing the chances of a successful attack. Whitelisting may prevent zero-day exploits because only applications or IP addresses that have been verified can execute. Whitelisting gives gives organizations full control over what should run on the systems and who can access them; thus, only trusted sources are allowed. Malware often disguises itself as trusted applications cyber incident response or programs; whitelist antivirus ensures that only validated and authorised software operates; hence, malicious applications can access the system. In some industries, Whitelisting can help organisations ensure their systems meet regulatory requirements for data security and access control.
Whitelisting is a highly effective security strategy that minimises attack vectors by allowing only approved entities to interact with a system, reducing the likelihood of successful cyber awareness. It helps prevent zero-day exploits by ensuring that only verified applications or IP addresses can execute and protect against malware that may disguise itself as trusted software. By providing organisations full control over which applications and users can access sensitive data, whitelist antivirus enhances data cyber protection and supports regulatory compliance in Firewall And Antivirus Software Article . This proactive approach ensures that only validated and authorised entities are permitted, establishing due diligence in safeguarding critical systems and information.
Sign up for ACTE Cyber Security Online Training and get a head start in your career cyber security.
Challenges and Limitations
- Maintaining a whitelist requires extensive administrative overhead and constant monitoring. The whitelists need to be updated with every addition or removal of applications, whitelist ip address, or users, Vulnerability Scanning which could create a massive administrative workload.
- Sometimes, legitimate applications or users are denied access because they are not found in the whitelist. This may affect business operations and require manual intervention to correct the situation.
- It reduces flexibility, as allow listing will probably not be capable of responding rapidly to new or unexpected situations, especially when an application or resource needs immediate access but is not on the list.
- In organisations where the end-users should often interact with many applications or websites, allowing listing would induce friction since sometimes applications or services require approval from the IT or security teams.
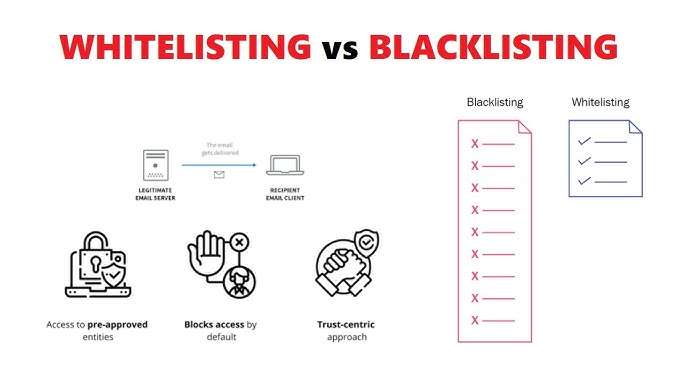
Whitelisting vs Blacklisting
- The fundamental difference between whitelisting and blocklisting is based on how access control is enforced.
- Access is granted only to those trusted entities; everything else is denied unless explicitly permitted. firewall whitelist is an active ot security measure that, among other things, reduces risk to a minimum.
- The blocklisting permission system grants access to all entities by default but denies access to those known to be bad. This is a reactive approach, most often less secure because it waits to identify the threat after it has been detected.
- While both techniques have Ethical Hacking roles and places in cyber incident response, whitelisting tends to offer robust protection through a “trust first” approach, permitting only known-good entities.
Leverage Cyber Security to Unlock the Future! Enroll in the Cybersecurity Expert Masters Program Training Course Program at ACTE Right Away.
Types of Whitelisting
Application Whitelisting
Allowing application Whitelistingis a list of approved software applications permitted to run on a system. Any application not on the list, by default, will not be allowed to run. One of the most widely used types of firewall whitelist prevents malware and ransomware from executing, ensuring it is strictly an enterprise product and only trusted applications are allowed to run. Whitelistingis generally considered as Whitelisting software or ot security tools that automatically generate and enforce an application allowlist. Such a solution is very efficient as cyber protection against unauthorised software running on the system, including most zero-day attacks and other advanced threats.
IP Whitelisting
IP Whitelisting involves blocking or allowing access to a system based on IP addresses assigned to trusted sources. In this model, organisations list approved IP addresses or ranges that may use their networks, servers, or applications. The access will be blocked if any attempt to access the system has been made from an IP address, not on the allowlist. IP Whitelisting is mainly implemented with remote access or VPN connections, and the practice is a great last line of defence in system resources with limited access. For instance, a company may limit the remote connection to certain office locations or restrict access to certain cloud-based applications from specific geographic locations.
Email Whitelisting
Email Whitelisting is the process through which a trusted message from a particular sender is approved so that such messages are not flagged as spam or phishing. In essence, a spam filter lets through emails from specific senders to ensure that legitimate communications are carried to the inbox without any hindrance.
Domain Whitelisting
Allow listing of domains allows users or applications to connect to some websites or online resources according to their domain names. That allows the listing to ensure the user or application can interact with only trusted web resources. It’s most commonly used to block unauthorised or potentially harmful websites and stop users from visiting a malicious site by mistake. Allow listing of domains can be one component of the content filtering solution so that employees or systems would have access only to tested, safe Websites or resources. Cybersecurity Training Courses may, therefore, prevent phishing sites and malcode, improper content and general undesirable Web sites from reaching the employees.
Best Practices in Implementing Whitelisting
Organisations should strive to follow best practices to get the maximum mileage out of Whitelisting . Ensure regularly reviewing and updating the Whitelisting list to add newer applications, new users, or IP addresses. Develop a centralised management system that manages and updates allowlists so that allowlists update automatically and simultaneously reduce the administrative burden. Tests allow listing policies in controlled environment tests before implementing them in an organisation to identify and correct issues. On an ongoing basis, monitor the access to the system to ensure interaction only from authorised entities and audit changes made to the allowlist for an opportunity to catch potential misconfigurations Threat Intelligence . Implementing a clear process for adding or removing entities from the allowlist is important, ensuring that only trusted sources are included while minimising the risk of errors. Organisations should also conduct regular audits to verify the integrity and effectiveness of the allowed listing policies,cyber incident response ensuring they align with evolving ot security requirements. User education is also crucial, as employees should be trained on the potential risks of unauthorised software or applications and how to report suspicious activity.
Get interview-ready with our collection of Cybersecurity Interview Questions and Answers Questions. Equip yourself with the knowledge to impress potential employers!
Conclusion
Whitelisting is a very effective ot security method that can significantly enhance protection against many threats from the cyber domain. In allow listing, the attack surface is reduced, malware and unauthorised access are prohibited, and control over system interaction can be increased by focusing on trusted entities, which deny everything else by default. Proper management and constant updating are needed for the effective usage offirewall whitelist. In a correct implementation of Whitelisting , well-placed-fending organisations are at the heart of proactive cyber awareness defence against an ever-evolving landscape of cyber threats. However, while Cybersecurity Training offers strong cyber protection, it is not without its challenges. It requires ongoing maintenance and monitoring to ensure that the list of approved entities remains up-to-date and accurate. As new applications, users, and IP addresses emerge, organisations must adapt their Whitelisting policies to maintain ot security without hindering productivity. Despite these challenges, when implemented alongside other security measures, firewall whitelist can form a critical layer of defence that significantly reduces the risk of attacks, offering organisations a proactive strategy for securing their digital infrastructure and sensitive data.





