
An Overview of Patch Workflows | Benefits and Special Features [ For Freshers and Experience ]
Last updated on 27th Dec 2021, Blog, General
A patch file represents a single set of changes (i.e., a commit) that can be applied to any branch, in any order. In this sense, the patch workflow is akin to interactive rebasing, except you can easily share patches with other developers.
- Patch management overview
- Supported platforms for patch management
- Supported platforms for storing the patch repositories of patch catalogues
- Offline and online mode
- Patch management workflow
- Configuring global configuration parameters
- Additional Information on installed patches, configuration data, and more
- Why do we need patch management?
- How your organisation benefits from an efficient patch management program
- Patch management best practises
- Conclusion
Patch management overview:
Patch management refers to the acquisition, testing and installation of patches. The patch administrator analyzes individual servers to determine which patches should be received and installed to comply with organisational standards. TrueSight Server Automation automates the process of building and maintaining patch repositories, analysing target servers, and packaging and deploying patches, if necessary.
At the end of the process, TrueSight for Server Automation reports are available to show Smart Reporting compliance. BMC recommends that you set up a small test group of servers and run the patch process on the group. Then, expand the process to all servers in the organisation.
- Microsoft Windows
- Oracle Solaris 10 and 11
- Fujitsu Solaris
- ibm x
- MultiBOS
- Red Hat Enterprise Linux
- SUSE Linux Enterprise
- oracle linux
- Ubuntu
- Debian
Supported platforms for patch management:
The patch management feature in TrueSight Server Automation supports the following operating systems:
For detailed information about supported operating systems and versions, see BMC Solutions and the Product Availability and Compatibility Utility. Patch management is supported for HP-UX and CentOS using an external tool called Vendor Patch Content (VPC). VPC is included as part of TrueSight Server Automation. For more information, see How to perform HP-UX or CentOS patch analysis using vendor patch content. An additional, separate package is provided for patch management on Solaris 11. For more information, see How to do script-based patch analysis for Solaris 11.
- Windows
- Windows or unix
- Axe
- Any AIX server
- If you are downloading patches using the SUMA option, make sure you have the SUMA utility installed on your repository server.
- We recommend using the latest suma download option instead of the fixed get download option.
- Before using the SUMA download option, make sure that the repository server is running an AIX system.
- repository server version
- Mrs Establishment
- SuSE 11 SP3
- SuSE 11 SP4
- Note: SuSE recommends upgrading SuSE 12 to SuSE 12 SP1 to avoid dependency issues.
- Not configured with SMT out of the box. You must manually install and configure SMT (version 11 SP3) on the repository server before creating the SuSE patch catalogue.
- SuSE 12 SP1 or later (recommended) The SMT is shipped out-of-the-box with the operating system.
- WARNING: BMC strongly recommends using Zipper when creating patching jobs for patch catalogues created using the Subscription Management Tool (SMT). For more information, see Zipper Patching Tool.
- SuSE Linux 11 is installed with SuSE Linux createrepo and python-urlgrabber.
- Oracle Enterprise Linux Any supported RPM-based Linux installed with createrepo and python-urlgrabber.
- windows or unix
- note: If you are using Solaris 11 patch, you can only use Solaris
- 11 server to store the patch repository.
- ubuntu unix
- Debian Windows or Unix
- CentOS for CentOS 7 Use the patch repository created on a system running CentOS 7. Similarly, for CentOS 8, use the patch repository created on the system running CentOS 8. Make sure createrepo and python-urlgrabber are installed on CentOS. System.
- HP-UX
- An HP-UX patch repository must be located either directly on the HP-UX (SWA) server or in a directory that the SWA server considers to be a local share.
- Note that if you are using an offline downloader, you can run Offline Downloader on any Windows or Linux machine, but the HP-UX patch repository must still be on the HP-UX (SWA) server.
Supported platforms for storing the patch repositories of patch catalogues:
Using the Red Hat Enterprise Linux (RHEL) CDN Interface
Red Hat Enterprise Linux 6, 7, or 8
SuSE Linux 15 To patch SuSE 15 targets, ensure that the patch repository server runs a SuSE 11 or 12 system and is configured with Subscription Management Tools (SMT). A server running SuSE 15 with RMT is not supported for the patch repository.
Suse linux 12
SUSE Linux with SMT installed.
Note: To patch SuSE 12 targets, ensure that the SuSE patch repository server is configured with SMT.
The following table lists the versions that are installed with SMT out-of-the-box, as well as the versions on which SMT must be installed manually.
Sus 12
Solaris
Fujitsu Solaris Windows or Linux
- Use offline mode if you work in an air-gapped environment where the TrueSight Server Automation application server does not have external Internet access. In offline mode, you use the BMC Offline Patch Downloader utility to download metadata and payload information to a server with Internet access. After downloading, you can transfer metadata and payload information (using removable storage) to the patch repository in an air-gapped environment.
- Patch Downloader utilities run scripts that use XML configuration files (samples are provided) that contain essential information such as repository location, as well as filters used when downloading from the vendor website.
Offline and online modes:
TrueSight Server Automation includes two patch management modes:
Online Mode — Patches are downloaded directly from the appropriate product site.
Offline Mode — Patches are pre-downloaded to the local repository and patches are applied from the repository.
- preparatory work
- Defining role-based permissions
- Configuring global configuration parameters
- (Offline mode only) Creating an offline patch repository
- Downloading Patch Downloader Utilities from BMC
- Preparing XML Configuration Files for Downloading Patch Content
- Downloading patches to an offline patch repository
- patching work
- Creating and updating patch catalogues
- Creating and running patching jobs and remediation jobs
- Task
- Description
- preparatory work
- Defining role-based permissions
- To create or update a catalogue, you must be assigned a role that includes the required permissions. To facilitate the division of responsibilities, you can assign permissions to a role or split them between multiple roles.
- For a list of required permissions, see Minimum permissions for patching.
- For details about assigning roles and permissions, see Managing Authorizations.
- For a list of permissions required to create a patching job and to apply a patch, see Minimum permissions for patching.
- Creating an offline patch repository
- (offline mode only)
- Getting Patch Downloader Features from BMC
- From the BMC EPD site, download the appropriate utilities for building your offline repository.
- Utilities are platform-specific. You should know which platform you plan to use to download your patches.
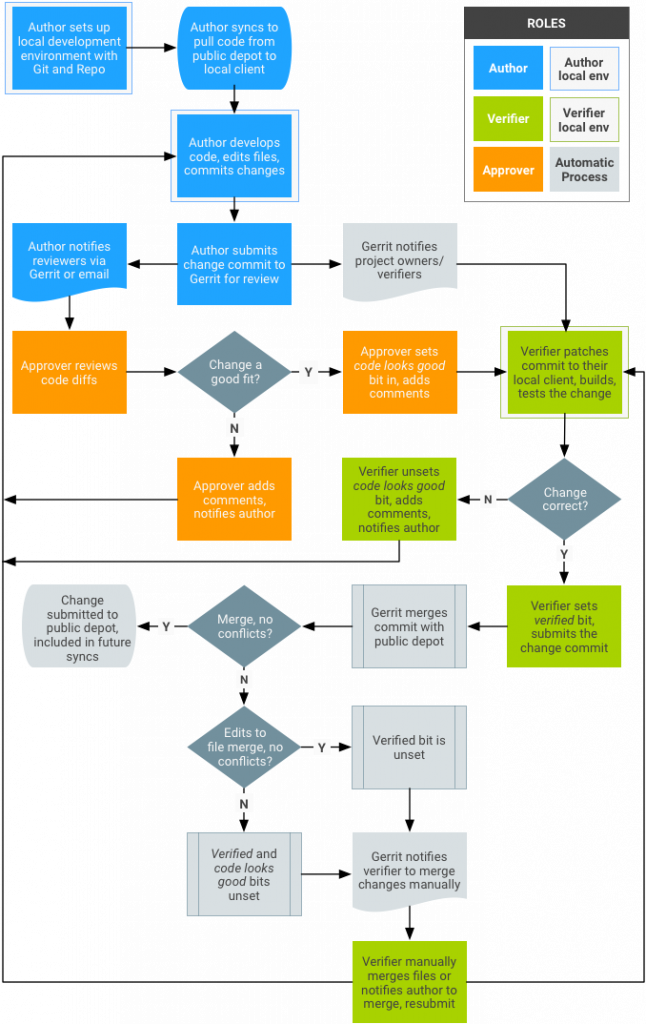
Patch management workflow:
Patch management consists of the following functions:
These functions are described in more detail in the following table:
Configuring global configuration parameters:
Global configuration parameters provide basic information used for patch catalogue creation and update, as well as patch and remedial jobs. The following parameter groups are available:
All operating systems — Configuration parameter options for proxy servers.
Platform-specific groups for each platform (such as Windows and Solaris) — parameters that apply only to that specific platform type
Shavlik URL Configuration — Configuration to connect to Shavlik Technologies to download patch-related metadata to patch Windows software.
For details about global configuration parameters, see Global configuration parameter list.
Additional Information on installed patches, configuration data, and more:
The following methods can be used to obtain additional information:
Live Browse – Use Live Browse to view patches installed on a server, one server at a time. For more information about live browse, see Server browse options.
Live Browse on the server does not list non-security patches.
Snapshot Jobs – Snapshot can record the configuration of patches on the target server at a specific time. To take a snapshot, you must run the snapshot job. For more information, see Creating and modifying snapshot jobs.
Reports — For information about the patch management report, see the online technical documentation for TrueSight Smart Reporting for Server Automation.
Why do we need patch management?
Patch management is important for the following major reasons:
Security: Patch management fixes vulnerabilities on your software and applications that are susceptible to cyber attacks, helping your organisation reduce its security risks.
System uptime: Patch management ensures that your software and applications stay up-to-date and run smoothly while supporting system uptime.
Compliance: With the continuous increase in cyber attacks, organisations are often required by regulatory bodies to maintain a certain level of compliance. Patch management is a necessary part of adhering to compliance standards.
Feature Improvements: Patch management software may extend beyond bug fixes to include feature/functionality updates. Patches can be key to making sure you have the latest and greatest of what a product has to offer.
How your organisation benefits from an efficient patch management program:
Your company can benefit from patch management in several ways:
A more secure environment: When you are regularly fixing vulnerabilities, you are helping to manage and reduce the risk that exists in your environment. It helps protect your organisation from potential security breaches.
Happy Customers: If your organisation sells a product or service that requires customers to use your technology, you know how important technology really is. Patch management is the process of fixing software bugs, which helps keep your system running.
No unnecessary fines: If your organisation is not patching and, therefore, not meeting the compliance standards, you may be subjected to some monetary penalty from regulatory bodies. Successful patch management ensures you are in compliance.
Continuous Product Innovation: You can apply patches to update your technology with better features and functionality. This can provide your organisation with a way to deploy your latest innovations in your software at scale.
- Set clear expectations and hold teams accountable: Leveraging organisational agreements, such as service-level agreements, can keep teams in check, and ensure that risk mitigation is actually done.
- Work closely with technical teams to ensure a common language: Security teams often refer to software errors as “risks”, while IT/DevOps teams may use the term “patches”. Making sure everyone is on the same page and recognizes the importance of patching is key to a successful patch management process.
- Establish a disaster recovery process: It is always a good idea to have a backup plan in case your patch management process fails and problems arise. patch management process
- A poor strategy would be to install new patches only after they are available for all assets in your organisation’s inventory without considering the impact. Instead, a more strategic approach should be adopted. Patch management should be implemented with a detailed, organisational process that is both cost-effective and security-focused.
Patch management best practises:
Some best practises to keep in mind when implementing patch management include:
Key steps in the patch management process include:
Develop an up-to-date inventory of all your production systems: Whether on a quarterly or monthly basis, this is the only way to really monitor what assets exist in your ecosystem. Through diligent asset management, you will have an informed view of their geographic locations and organisational “owners” as well as the operating system, version type and IP address present. As a general rule, the more often you maintain your property listing, the more information you will have.
Develop a plan to standardise systems and operating systems for the same version type: Although this is difficult to execute, standardising your asset list makes patching faster and more efficient. You will want to standardise your assets to a manageable number so that you can speed up your healing process as new patches are released. This will help save both you and the technical teams the time it takes to do the treatment.
Make a list of all the security controls in your organisation: Keep track of your firewall, antivirus, and vulnerability management tools. You will want to know where they are sitting, what they are protecting and what assets are attached to them.
Compare reported vulnerabilities against your inventory: Use your vulnerability management tools to assess which vulnerabilities exist, which assets in your ecosystem help you understand your security risk as an organisation. is going to help.
Categorise risk: Through vulnerability management tools, you can easily manage which assets you consider important to your organisation and, therefore, prioritise what needs to be improved accordingly. Testing! Apply the patch to a representative sample of the assets in your laboratory environment. Stress test the machines to make sure the patches won’t cause problems in your production environment.
Apply the patch: Once you’ve prioritised what needs to be treated first, start patching to really reduce the risk in your environment. More advanced vulnerability management tools also provide the ability to automate the time-consuming parts of the patching process. Consider rolling out the patch in batches of assets; Although you’ve already tested in your lab environment (you did it right!?) there can still be unexpected results in production. Dip a few toes in before jumping so that there aren’t any sweeping problems.
Track your progress: Reevaluate your assets to make sure patching was successful.
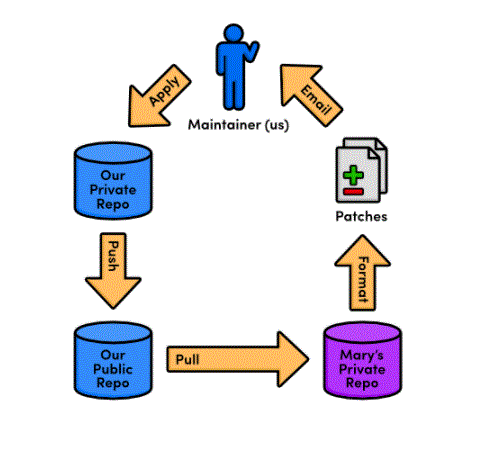
- Whereas remote repositories are a way to share entire branches, patches are a way to send individual commits to another developer. Keep in mind that patches are usually only sent to a project maintainer, who then integrates them into the “official” project for everyone to see. It would be impossible for everyone to communicate using only patches, as no one would apply them in the same order. Eventually, everyone’s project history will look completely different.
- In many ways, patches are an easier way to accept contributions from previous modules than integrator workflows. Only the project maintainer needs a public repository, and will never need to see anyone else’s repository. From the maintainer’s point of view, patches also provide the same security as the integrator workflow: he still doesn’t have to give anyone access to his “official” repositories. But, now he doesn’t even have to keep track of everyone’s remote repositories.
- As a programmer, you are most likely to use patches when you want to fix a bug in someone else’s project. After you fix this, you can send them a patch of the resulting commit. For this kind of one-time-fix, it is more convenient for you to generate a patch than to install a public repository.
- This module concludes our discussion of the standard *** workflow. Hopefully, you now have a good idea of how can better manage your personal and business software projects using a centralised, integrator, or patched workflow. In the next module, we’ll switch gears and introduce a variety of practical commands.
Conclusion:
