
Get OKTA Interview Questions and Answers [ TO GET HIRED ]
Last updated on 14th Nov 2021, Blog, Interview Questions
OKTA is a publicly traded identity and access management software system. This provides cloud software that helps companies to manage and secure user authentications into modern applications, for developers to build identity controls into the applications, website web services and devices. The main purpose of the OKTA system is to provide secured and authorized assessment with any software devices. We have designed frequently asked industry level OKTA interview questions with answers to help those who want to pursue their desire in this field. With the help of this, you can crack any type of complex interview in an easier way.
1. What is OKTA?
Ans:
OKTA stands as a prominent cloud-based identity and access management (IAM) platform, offering organizations a secure means to connect and manage user identities. This platform is equipped with a variety of features, including Single Sign-On (SSO), Multi-Factor Authentication (MFA), and other identity management capabilities.
2. Explain Single Sign-On (SSO) and how does OKTA implement it?
Ans:
Single Sign-On (SSO) is a crucial aspect of identity and access management, allowing users to access multiple applications with a single set of login credentials. In the case of OKTA, it serves as an identity provider, authenticating users and furnishing tokens that authorise access to various applications without necessitating separate login processes.
3. What is Multi-Factor Authentication (MFA), and why is it important in identity management?
Ans:
Multi-Factor Authentication (MFA) is a security mechanism that requires users to provide multiple forms of identification before gaining access to an account or application. OKTA places a strong emphasis on MFA, offering various methods such as SMS codes, push notifications, and hardware tokens to bolster overall security by adding an extra layer of authentication.
4. How does OKTA integrate with Active Directory?
Ans:
OKTA integrates seamlessly with Active Directory (AD) through the deployment of the OKTA Active Directory agent. This agent facilitates the synchronisation of user accounts and groups between the AD and OKTA platforms, enabling centralised management of user access across the organisation.
5. Explain the concept of Federation in OKTA.
Ans:
Federation within the OKTA framework involves establishing trust relationships between different identity providers, facilitating Single Sign-On (SSO) across various organisations. OKTA supports standard federation protocols such as SAML (Security Assertion Markup Language), OAuth, and OpenID Connect, ensuring secure authentication and authorization processes between disparate systems.
6. What is the purpose of the OKTA Universal Directory?
Ans:
The OKTA Universal Directory serves as a central cloud-based repository for user profiles, attributes, and group memberships. It plays a pivotal role in managing and storing user identity information, offering a unified and scalable solution that seamlessly integrates with diverse applications and services.
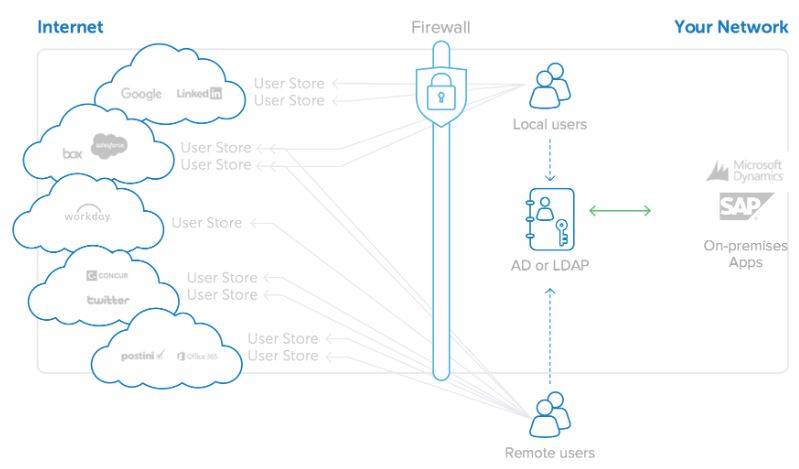
7. How does OKTA handle user provisioning and de-provisioning?
Ans:
OKTA streamlines the process of user provisioning and de-provisioning by automating these tasks. Through integration with Human Resources (HR) systems or directories, OKTA ensures that when a new employee joins, access to necessary applications is provisioned automatically. Conversely, when an employee leaves, OKTA promptly revokes access, enhancing security and compliance.
8. Explain the difference between OKTA and other identity management solutions.
Ans:
OKTA distinguishes itself from traditional identity management solutions by being a cloud-first platform that prioritizes simplicity, scalability, and seamless integration. With a broad array of features such as adaptive Multi-Factor Authentication (MFA), lifecycle management, and API access management, OKTA offers a modern and comprehensive approach to identity and access management.
9. How does OKTA ensure security and compliance in its platform?
Ans:
Security is paramount in OKTA’s platform, encompassing robust measures such as encryption, secure protocols, and regular security assessments. In addition to this, OKTA aligns with industry compliance standards like SOC 2, ISO 27001, and GDPR, ensuring a secure and compliant environment for organizations utilizing its services.
10. Discuss OKTA’s role in providing secure access to APIs
Ans:
| Authentication | Authorization | Integration Capabilities | |
| OKTA uses OAuth for robust authentication, issuing secure access tokens. |
Fine-grained authorization controls ensure precise application permissions.. |
Seamless integration with various API management solutions for unified management. | |
| Access tokens serve as credentials, verifying applications securely. | Authorization mechanisms prevent unauthorized access and enhance security. | OKTA’s Identity Engine allows tailored access policies for specific business and compliance needs. | |
| Authentication processes prioritize trust, ensuring only authorized apps receive tokens. |
Comprehensive approach mitigates potential security risks and enforces the principle of least privilege. |
Integration capability extends to the entire API landscape, accommodating diverse business requirements. |
11. Can you explain the concept of OAuth and how it is utilised in OKTA?
Ans:
- OAuth, which stands for Open Authorization, is a widely adopted framework used for authentication and authorization.
- In the context of OKTA, OAuth plays a pivotal role in enabling secure access to resources by allowing applications to obtain limited access tokens on behalf of users.
- This mechanism facilitates delegated access without exposing sensitive user credentials. OKTA’s implementation of OAuth ensures a robust and standardized approach to authentication and authorization within its identity and access management ecosystem.
12. What role does OKTA play in securing APIs, and how does it handle API access management?
Ans:
OKTA takes a comprehensive approach to securing APIs by employing OAuth and OpenID Connect protocols. API access management in OKTA ensures that only authorized users or applications can access protected resources. This level of control enhances security by preventing unauthorised access to critical data and functionalities. Through OKTA’s API access management, organisations can govern and regulate the interactions with their APIs, reinforcing the overall security posture of their systems.
13. Explain the significance of Adaptive Multi-Factor Authentication (AMFA) in OKTA.
Ans:
Adaptive Multi-Factor Authentication (AMFA) is a sophisticated approach to MFA within the OKTA platform. It goes beyond traditional MFA methods by dynamically assessing various factors, including user behaviour and geographical location, to determine the appropriate level of authentication required. The adaptive nature of OKTA’s AMFA enhances security by tailoring the authentication process to the specific context, thereby striking a balance between heightened security measures and user convenience.
14. How does OKTA support user self-service capabilities, and why is it important?
Ans:
OKTA recognizes the importance of empowering users to manage their own identities and accounts through robust self-service capabilities. The platform provides users with the tools to perform tasks such as profile management, password resets, and other account-related activities independently. This not only enhances user experience by reducing dependence on IT support but also contributes to organisational efficiency and agility. OKTA’s emphasis on user self-service aligns with contemporary trends in identity management, where user empowerment is a key aspect of a streamlined and user-friendly authentication experience.
15. Discuss OKTA’s role in the context of Zero Trust Security.
Ans:
OKTA aligns itself with the principles of Zero Trust Security, a modern security paradigm that assumes no inherent trust for users or systems, even those within the organisation’s network. OKTA achieves this by continuously verifying the identity of users and devices before granting access to resources. This proactive and risk-based approach ensures that access is granted based on the current context and risk factors, contributing to a more robust and adaptive security posture in line with the evolving threat landscape.
16. How does OKTA handle identity lifecycle management, and what benefits does it offer to organisations?
Ans:
OKTA’s approach to identity lifecycle management involves automating processes related to user onboarding, changes, and offboarding. This automation ensures that user access permissions align seamlessly with their roles and responsibilities within the organisation. The benefits of OKTA’s identity lifecycle management include increased operational efficiency, compliance adherence, and a reduced risk of unauthorised access. By automating these critical processes, OKTA helps organisations maintain accurate and up-to-date user access, contributing to a more secure and well-governed identity landscape.
17. Can you explain the concept of OKTA Workflows and how it enhances automation in identity management?
Ans:
OKTA Workflows serves as a powerful tool within the OKTA platform, enabling organisations to create and implement automated processes and integrations across various systems. This capability enhances automation in identity management by allowing organisations to streamline complex workflows. OKTA Workflows can be customised to automate routine tasks, such as user provisioning, de-provisioning, and other identity-related processes. This not only reduces manual intervention and the likelihood of errors but also contributes to operational efficiency and agility in adapting to evolving business needs.
18. What is OKTA Advanced Server Access (ASA), and how does it contribute to overall security?
Ans:
OKTA Advanced Server Access (ASA) is a specialised solution designed to enhance security in server access. By centralising authentication and authorization for server access, OKTA ASA ensures that only authorised users can interact with servers. This approach significantly reduces the risk of unauthorised access to critical infrastructure components, contributing to the overall security and integrity of an organisation’s IT environment.
19. How does OKTA handle single sign-on for mobile applications, and what considerations are involved?
Ans:
OKTA extends its support for Single Sign-On (SSO) to mobile applications through the provision of Software Development Kits (SDKs) and APIs. Developers can integrate these tools into mobile applications, allowing users to experience seamless and secure authentication across various devices.
Considerations in this context include the need for a consistent user experience, adherence to mobile application security best practices, and ensuring that OKTA’s mobile SDKs are effectively utilized to provide robust and secure authentication mechanisms.
20. Discuss OKTA’s role in enabling secure access to remote applications and resources.
Ans:
OKTA plays a crucial role in enabling secure access to applications and resources, particularly in the context of remote work. Leveraging its cloud-based identity and access management platform, OKTA ensures that users can securely access the resources they need from anywhere.
This involves robust authentication mechanisms, secure communication protocols, and a comprehensive approach to identity verification. OKTA’s role in facilitating secure remote access is instrumental in supporting the evolving work landscape, where remote and distributed teams require reliable and secure access to organizational resources.
21. How does OKTA manage the synchronization of user attributes?
Ans:
OKTA ensures the synchronization of user attributes through its Universal Directory, maintaining consistency in user profiles across integrated systems. This plays a crucial role in identity management, ensuring that user information remains accurate and up-to-date, thereby supporting seamless access and personalization across different applications.
22. Can you delve into OKTA’s strategy for enforcing access policies?
Ans:
OKTA employs access policies to establish rules for user access based on factors such as user attributes, device status, and location. These policies are consistently enforced across applications, guaranteeing that access is granted or denied based on predefined criteria, ultimately enhancing security and compliance.
23. Elaborate on OKTA’s standpoint on passwordless authentication?
Ans:
OKTA embraces passwordless authentication, eliminating reliance on conventional passwords. This enhances security by mitigating the risks associated with password vulnerabilities. OKTA offers alternative authentication methods such as biometrics, smart cards, or push notifications, delivering a more secure and user-friendly authentication experience.
24. Can you provide insights into how OKTA secures privileged access?
Ans:
OKTA addresses privileged access security through features like Adaptive Multi-Factor Authentication (AMFA) and role-based access controls. By implementing stringent authentication measures and restricting access to privileged accounts based on roles, OKTA effectively mitigates the risks linked to unauthorised access to critical systems and data.
25. Discuss OKTA’s capabilities in supporting fine-grained access control?
Ans:
OKTA empowers organisations with fine-grained access control by allowing them to define specific permissions and policies for individual users or groups. This flexibility is essential in diverse organisational environments, enabling administrators to tailor access levels to specific job roles and responsibilities, ultimately enhancing security and compliance.
26. How does OKTA assist organisations in managing?
Ans:
OKTA offers comprehensive Customer Identity and Access Management (CIAM) solutions, equipping organisations with tools to manage and secure customer identities. This is particularly crucial for customer-facing applications, where OKTA ensures secure authentication, registration, and personalised experiences while upholding robust security measures.
27. Explain OKTA ThreatInsight’s role in enhancing security?
Ans:
OKTA ThreatInsight is a security feature that utilizes contextual data to assess the risk level of authentication attempts. By scrutinizing factors such as device health, location, and user behavior, OKTA dynamically adjusts authentication requirements, providing risk-based authentication to counter potential threats and unauthorized access.
28. How does OKTA handle identity federation with third-party identity providers?
Ans:
OKTA facilitates identity federation with third-party providers through standard protocols like SAML and OAuth. This allows users to use credentials from external identity providers to access applications integrated with OKTA. The advantages include streamlined user experiences, reduced password fatigue, and simplified identity management across different platforms.
29. Discuss OKTA’s approach to managing consent?
Ans:
OKTA enables organizations to manage user consent and privacy by providing tools to define and enforce consent policies. This is crucial, particularly in applications dealing with sensitive data, ensuring compliance with privacy regulations and granting users control over how their information is accessed and utilized.
30. How does OKTA address the challenges of securing API access in a microservices architecture,
Ans:
OKTA tackles API security challenges in a microservices architecture through features like OAuth, OpenID Connect, and API Access Management. These tools guarantee secure authentication, authorization, and management of API access, safeguarding the integrity of microservices-based applications.
31. Elaborate on OKTA’s support for password management
Ans:
OKTA supports password management through features like self-service password reset, enabling users to regain access to their accounts independently. Additionally, OKTA empowers organisations to define password policies, ensuring compliance with security standards and minimising the risk of compromised credentials.
32. How does OKTA handle identity proofing and verification?
Ans:
OKTA supports identity proofing through various methods such as document verification, biometrics, and knowledge-based authentication. In scenarios requiring stringent identity verification, OKTA provides the flexibility to implement multiple layers of authentication to ensure a high level of confidence in user identities.
33. Discuss the integration capabilities of OKTA?
Ans:
OKTA boasts robust integration capabilities through pre-built connectors and APIs. This allows organisations to easily connect OKTA with a diverse range of enterprise applications, streamlining workflows, and enhancing overall efficiency.
34. How does OKTA handle user authentication in scenarios where users have multiple devices?
Ans:
OKTA employs adaptive authentication to handle scenarios where users have multiple devices. By analyzing contextual factors such as device trustworthiness and user behavior, OKTA dynamically adapts the authentication process, ensuring a consistent and secure experience across various devices while maintaining a high level of security.
35. Discuss OKTA’s support for cross-platform identity
Ans:
OKTA excels in providing cross-platform identity and access management solutions, bridging the gap between on-premises and cloud-based applications. Through its adaptable architecture, OKTA ensures a unified identity experience, allowing organisations to manage access seamlessly across diverse application environments.
36. How does OKTA contribute to compliance initiatives?
Ans:
OKTA aids compliance initiatives by offering features such as comprehensive audit logs, policy enforcement, and support for various compliance standards like GDPR, HIPAA, and others. These features assist organisations in meeting regulatory requirements by providing the necessary tools for monitoring, reporting, and ensuring adherence to compliance standards.
37. Explain the role of OKTA Identity Engine in customization?
Ans:
OKTA Identity Engine is a powerful tool for customization and policy orchestration. It enables organisations to define and tailor identity policies based on their unique requirements. This flexibility ensures that OKTA can adapt to the specific needs of different organisations, providing a customizable and extensible identity management solution.
38. How does OKTA handle the secure integration of applications that are not natively supported through connectors or APIs?
Ans:
OKTA provides a Universal Directory that serves as a central identity hub, allowing organisations to extend the integration of applications not natively supported. Through custom integrations and standards like LDAP, organisations can securely connect and manage access to a wide array of applications, ensuring a comprehensive identity management solution.
39. Discuss OKTA’s role in managing access for external partners ?
Ans:
OKTA supports secure collaboration by extending access management to external partners or contractors. Through features like external identity providers and guest access, OKTA enables organisations to manage access for external entities securely, ensuring a collaborative yet controlled environment.
40. How does OKTA contribute to user education?
Ans:
OKTA contributes to user education through features like multi-factor authentication and security policies. By promoting best practices and implementing security awareness campaigns, OKTA helps users recognize and respond to potential phishing and social engineering threats, fostering a culture of cybersecurity within organisations.
41. How does OKTA handle user provisioning in a dynamic organisational environment?
Ans:
In a dynamic organisational environment, OKTA streamlines user provisioning by implementing an automated process that integrates seamlessly with Human Resources (HR) systems or directories. This automation ensures that new employees gain timely and automatic access to the applications and resources they need. By eliminating the need for manual intervention, OKTA facilitates a more efficient onboarding process, reducing administrative burdens and enhancing organisational agility.
42. Explain the concept of OKTA Universal Directory and its advantages.
Ans:
The OKTA Universal Directory serves as a centralised repository for managing user profiles and attributes within an organisation. This cloud-based solution offers scalability and flexibility, allowing for the storage and efficient management of user identity information. The advantages of the Universal Directory include its role in providing a unified access point for user identity across various applications. By centralising user data, OKTA ensures consistency, accuracy, and seamless integration with a diverse range of applications, contributing to a more cohesive and streamlined identity management process.
43. What role does Adaptive Multi-Factor Authentication (AMFA) play in enhancing security, and how does it work in OKTA?
Ans:
- Adaptive Multi-Factor Authentication (AMFA) plays a pivotal role in enhancing security within the OKTA ecosystem. Unlike traditional Multi-Factor Authentication (MFA), AMFA dynamically assesses user behaviour and contextual factors to adapt the authentication requirements.
- By continuously evaluating risk factors, such as the user’s location and device health, OKTA’s AMFA ensures that the level of authentication aligns with the perceived risk.
- This adaptive approach provides a higher level of security while minimising user friction, offering a balance between robust security measures and a seamless user experience.
44. How does OKTA contribute to Zero Trust Security, and what principles does it follow?
Ans:
OKTA aligns with the principles of Zero Trust Security, a modern security paradigm that challenges the traditional notion of implicit trust within a network. OKTA follows Zero Trust principles by assuming zero inherent trust, regardless of whether a user or system is internal or external. The core tenet involves continuous verification of user and device identities before granting access to resources. This proactive and risk-based approach ensures that access is granted based on real-time contextual factors, enhancing security in the face of evolving cyber threats.
45. Explain OKTA’s approach to API access management and securing interactions in a microservices architecture.
Ans:
In the context of API access management, OKTA adopts a robust approach to secure interactions within a microservices architecture. Leveraging protocols such as OAuth, OpenID Connect, and API Access Management, OKTA ensures the authentication, authorization, and management of API access are conducted securely. This multifaceted approach safeguards APIs from unauthorised access and potential vulnerabilities, providing a comprehensive solution for organisations adopting microservices-based applications.
46. How does OKTA support Single Sign-On (SSO) for mobile applications?
Ans:
OKTA extends its support for Single Sign-On (SSO) to mobile applications through the provision of Software Development Kits (SDKs) and APIs. Developers can seamlessly integrate OKTA’s mobile SDKs into their applications, enabling users to experience a secure and consistent authentication process across various mobile devices. This support for SSO in the mobile realm not only enhances security but also contributes to a unified and user-friendly experience, aligning with the expectations of modern mobile app users.
47. Discuss OKTA’s role in securing server access with Advanced Server Access (ASA).
Ans:
OKTA’s Advanced Server Access (ASA) is instrumental in enhancing security by centralising authentication and authorization for server access. By leveraging ASA, organisations can ensure that only authorised users have the privilege to interact with servers. This centralised control over server access significantly reduces the risk of unauthorised entry and potential security breaches, contributing to the overall fortification of an organisation’s IT infrastructure.
48. How does OKTA contribute to compliance with industry standards and regulations?
Ans:
OKTA plays a vital role in supporting organisations’ compliance initiatives by aligning with industry standards and regulations. OKTA’s adherence to standards such as SOC 2, ISO 27001, GDPR, HIPAA, and others demonstrates its commitment to security and data protection. Additionally, OKTA offers features like comprehensive audit logs and policy enforcement, assisting organisations in meeting regulatory requirements, conducting audits, and ensuring adherence to established compliance standards.
49. Explain OKTA’s role in identity proofing and the methods it employs for user verification.
Ans:
OKTA places a strong emphasis on identity proofing by offering various methods for user verification. These methods include document verification, biometrics, and knowledge-based authentication. The flexibility provided by OKTA allows organisations to implement multi-layered approaches to user identity verification. This ensures a high level of confidence in authenticating user identities, especially in scenarios where stringent verification is required for secure access to sensitive information and resources.
50. How does OKTA address user education and awareness in the context of cybersecurity threats?
Ans:
OKTA actively contributes to user education and awareness regarding cybersecurity threats by incorporating features such as multi-factor authentication and implementing security awareness campaigns. By promoting best practices and offering tools to enhance users’ understanding of potential threats, OKTA assists in creating a cybersecurity-conscious culture within organisations. This proactive approach empowers users to recognize and respond effectively to phishing and social engineering threats, fostering a heightened level of cybersecurity awareness across the organisation.
51. How does OKTA handle identity lifecycle management, and what benefits does it provide to organisations?
Ans:
OKTA’s approach to identity lifecycle management involves the automation of key processes related to user identities within an organisation. This encompasses the entire lifecycle, including user onboarding, changes, and offboarding. By integrating seamlessly with Human Resources (HR) systems or directories, OKTA ensures that new employees gain automatic access to the applications and resources they require. During changes or offboarding, OKTA automates the revocation of access, reducing the risk of unauthorised access to sensitive information.
52. Discuss OKTA’s role in enabling secure access to remote applications and resources.
Ans:
- OKTA plays a pivotal role in facilitating secure access to remote applications and resources, particularly in today’s increasingly remote and distributed work environments.
- Leveraging its cloud-based identity and access management platform, OKTA ensures that users can securely authenticate and access the applications they need from any location.
- This involves the implementation of robust authentication mechanisms, secure communication protocols, and a comprehensive approach to identity verification.
- By providing a secure remote access solution, OKTA enables organisations to maintain productivity while prioritising the security of their digital assets and sensitive data.
53. Can you explain the concept of OKTA Workflows and how it enhances automation in identity management?
Ans:
- OKTA Workflows is a sophisticated tool designed to empower organisations with the ability to create and implement automated processes and integrations within their identity management framework.
- In the context of identity management, Workflows streamline and automate various tasks, including user provisioning and de-provisioning, group management, and access policy enforcement.
- By providing a visual interface for defining workflows, organisations can customise and automate processes to suit their specific needs.
- This enhances automation in identity management by reducing manual interventions, improving operational efficiency, and ensuring that identity-related processes are executed consistently and in compliance with organisational policies.
54. What is OKTA Advanced Server Access (ASA), and how does it contribute to overall security?
Ans:
OKTA Advanced Server Access (ASA) is a specialised solution designed to enhance the security of server access within an organisation. ASA centralises the authentication and authorization processes for accessing servers, introducing a heightened level of control and security.
By consolidating server access management, OKTA ASA significantly reduces the risk of unauthorised access to critical infrastructure components. This centralised approach ensures that only authenticated and authorised users can interact with servers, minimising the potential vulnerabilities associated with decentralised or less secure server access mechanisms.
55. How does OKTA support user self-service capabilities, and why is it important?
Ans:
- OKTA places a strong emphasis on empowering users through self-service capabilities, allowing them to manage various aspects of their user profiles and accounts independently.
- Users can perform tasks such as resetting passwords, updating personal information, and managing access permissions without requiring direct assistance from IT support.
- This emphasis on user self-service is crucial for several reasons. Firstly, it enhances the overall user experience by providing a convenient and efficient way for users to address their account-related needs.
- Secondly, it reduces the workload on IT support teams, allowing them to focus on more complex issues. Lastly, by empowering users, OKTA contributes to increased organisational efficiency and agility.
56. Explain OKTA’s approach to access policies and how it enforces them across applications.
Ans:
OKTA’s approach to access policies revolves around the definition of rules and conditions that govern user access to applications. These policies take into account various factors such as user attributes, device status, and contextual information.
Access policies are not only defined but are consistently enforced across all integrated applications within the OKTA ecosystem. This ensures a standardised and secure access environment where users are granted or denied access based on predefined criteria.
The enforcement of access policies across applications contributes to a cohesive and compliant access management framework, supporting organisations in maintaining a robust security posture.
57. How does OKTA handle user authentication in scenarios where users have multiple devices?
Ans:
OKTA addresses the challenge of user authentication across multiple devices through the implementation of adaptive authentication. In scenarios where users utilise various devices, OKTA dynamically adapts the authentication process based on contextual factors. These factors may include the trustworthiness of the device and the user’s behaviour patterns. By analysing these contextual cues, OKTA ensures that the authentication experience remains both consistent and secure across different devices. This adaptive approach strikes a balance between security and user convenience, providing a seamless yet robust authentication experience.
58. What role does OKTA ThreatInsight play in enhancing security, and how does it leverage contextual data for risk-based authentication?
Ans:
OKTA ThreatInsight is a security feature that significantly enhances the overall security posture by dynamically assessing the risk level of authentication attempts. This assessment is based on a range of contextual data, including the health of the user’s device, their location, and behavioural patterns. By leveraging this contextual data, OKTA ThreatInsight dynamically adjusts the authentication requirements. In essence, it introduces risk-based authentication, where the level of authentication adapts to the perceived risk. This proactive approach strengthens security measures, providing an additional layer of defence against potential threats and unauthorised access.
59. Discuss OKTA’s support for cross-platform identity.
Ans:
- OKTA excels in providing comprehensive solutions for cross-platform identity and access management, addressing the challenges posed by diverse application environments.
- In organisations with a mix of on-premises and cloud-based applications, OKTA acts as a unifying force.
- It bridges the gap between different application environments, ensuring a seamless and consistent identity management experience.
- Regardless of the application’s deployment model, OKTA’s adaptable architecture facilitates the integration and management of access across diverse platforms.
- This cross-platform support is crucial for organisations seeking a unified approach to identity and access management.
60. How does OKTA contribute to user education?
Ans:
OKTA actively contributes to user education and awareness by incorporating features that promote security best practices. For instance, the implementation of multi-factor authentication serves not only as a security measure but also as an educational tool. Additionally, OKTA conducts security awareness campaigns to educate users on potential threats such as phishing and social engineering. These campaigns aim to raise awareness, equip users with the knowledge to identify and respond to threats effectively, and foster a culture of cybersecurity within the organisation. By integrating education with security features, OKTA contributes to a more vigilant and informed user base.
61. Can you elaborate on OKTA’s role in securing APIs, and how it handles API access management?
Ans:
OKTA plays a crucial role in securing APIs, recognizing the significance of API security in modern application architectures. It achieves this through the implementation of robust protocols such as OAuth and OpenID Connect. These protocols facilitate secure authentication, authorization, and management of API access. OKTA’s API access management capabilities ensure that only authorised users or applications can interact with protected resources. By safeguarding APIs from unauthorised access and potential vulnerabilities, OKTA contributes to the overall security of applications relying on API interactions.
62. Discuss OKTA’s capabilities in supporting fine-grained access control and its importance in diverse organisational environments.
Ans:
OKTA stands out in its support for fine-grained access control, allowing organisations to define specific permissions and policies at a granular level. This level of granularity is crucial in diverse organisational environments where different roles and responsibilities necessitate distinct access levels.
OKTA empowers administrators to tailor access permissions based on individual user roles or groups. This not only enhances security but also ensures compliance with organisational policies and regulatory requirements. The flexibility of fine-grained access control provided by OKTA addresses the unique needs of diverse organisational structures.
63. How does OKTA handle the secure integration of applications that are not natively supported through connectors or APIs?
Ans:
OKTA provides a robust solution for the secure integration of applications that may not be natively supported through connectors or APIs. Central to this capability is the OKTA Universal Directory, serving as a central identity hub. Through custom integrations and standards such as LDAP (Lightweight Directory Access Protocol), organisations can securely connect and manage access to a wide array of applications. OKTA’s approach ensures that even applications without native support can be seamlessly integrated into the identity management framework, offering a comprehensive solution for organisations with diverse application landscapes.
64. Explain OKTA’s support for password management, including features like self-service password reset and password policies.
Ans:
- OKTA provides robust support for password management, recognizing the critical role that passwords play in ensuring account security.
- Features such as self-service password reset empower users to independently regain access to their accounts, reducing reliance on IT support for password-related issues.
- Additionally, OKTA allows organisations to define and enforce password policies. These policies serve to ensure compliance with security standards, specifying criteria such as password complexity and expiration.
- By combining self-service capabilities with robust password policies, OKTA contributes to a more secure and user-friendly password management experience.
65. Discuss OKTA’s approach to managing consent and user privacy, especially in applications dealing with sensitive data.
Ans:
OKTA prioritises the management of consent and user privacy, particularly in scenarios involving sensitive data. The platform provides organisations with tools to define and enforce consent policies, giving users control over how their information is accessed and utilised. This is crucial in applications dealing with sensitive data, where privacy considerations are paramount. OKTA’s approach aligns with privacy regulations and standards, ensuring that organisations can adhere to compliance requirements while offering users transparency and control over their data.
66. How does OKTA contribute to compliance initiatives?
Ans:
OKTA actively contributes to compliance initiatives by offering features that align with various regulatory requirements. Notably, the platform provides comprehensive audit logs, allowing organisations to track and monitor user access and activities. Additionally, OKTA supports policy enforcement, ensuring that access policies align with regulatory standards. The platform adheres to multiple compliance standards, including GDPR, HIPAA, and others, demonstrating its commitment to security and data protection. OKTA’s features assist organisations in meeting regulatory requirements, conducting audits, and maintaining a robust compliance posture.
67. Explain the role of OKTA Identity Engine in customization.
Ans:
OKTA Identity Engine serves as a powerful tool for customization and policy orchestration within the identity management landscape. This engine enables organisations to define and tailor identity policies based on their unique requirements and business processes. The flexibility offered by OKTA Identity Engine ensures that the platform can adapt to the specific needs of different organisations. Whether addressing industry-specific regulations or internal policies, OKTA Identity Engine provides a customizable and extensible framework for identity management, allowing organisations to achieve a nuanced and tailored approach to their identity and access requirements.
68. How does OKTA handle identity federation with third-party identity providers?
Ans:
- OKTA facilitates identity federation with third-party providers through widely adopted protocols such as SAML (Security Assertion Markup Language) and OAuth.
- This allows users to leverage credentials from external identity providers to access applications integrated with OKTA.
- The advantages of these federated relationships are manifold. Users benefit from streamlined experiences, as they can use familiar credentials across multiple platforms.
- Password fatigue is reduced, and the overall identity management process becomes more seamless.
- Federated identity relationships simplify the user experience while providing organisations with the flexibility to integrate with a diverse array of external identity providers.
69. How does OKTA contribute to incident response and remediation in case of a security breach or suspicious activity?
Ans:
OKTA contributes to incident response and remediation by providing features such as real-time alerts, audit logs, and automated response actions. In the occurrence of a security breach or suspicious activity, organisations can promptly identify and respond to incidents through OKTA’s monitoring and reporting capabilities. This proactive approach assists in minimising the impact of security incidents and ensures a swift remediation process.
70. How does OKTA strike a balance between user convenience and robust security measures?
Ans:
- OKTA achieves a balance between user convenience and robust security measures by prioritising features like Single Sign-On (SSO).
- Offering a seamless authentication experience enhances user convenience, reducing the need for multiple credentials.
- Simultaneously, OKTA ensures security through adaptive access controls, risk-based authentication, and continuous monitoring, maintaining a secure environment without compromising user experience.
71. How does OKTA ensure secure authentication for users accessing applications globally?
Ans:
OKTA guarantees secure authentication on a global scale by considering factors such as regional compliance, data residency, and network latency. Employing a distributed architecture, OKTA optimises performance and compliance while delivering a consistent and secure authentication experience for users worldwide.
72. Describe OKTA’s support for privileged access management (PAM).
Ans:
OKTA addresses challenges in privileged access management through features like Adaptive Multi-Factor Authentication (AMFA) and role-based access controls. By implementing robust controls and monitoring privileged access, OKTA enhances security, ensuring that only authorised individuals can interact with sensitive systems and data.
73. How does OKTA contribute to the authentication?
Ans:
OKTA excels in managing authentication and authorization in a hybrid cloud environment by seamlessly integrating with on-premises and cloud-based applications. Its adaptive architecture ensures a unified approach, allowing organisations to maintain consistent security measures across diverse application environments.
74. Can you elaborate on OKTA’s support for multi-cloud environments?
Ans:
OKTA provides robust support for multi-cloud environments through standardised protocols and integrations. Offering a unified identity management solution, OKTA enables organisations to seamlessly oversee identity and access across different cloud providers, promoting interoperability and a cohesive user experience.
75. Explain OKTA’s role in securing the authentication process for Internet of Things (IoT) devices.
Ans:
OKTA addresses IoT security challenges by incorporating secure authentication mechanisms for IoT devices. It ensures that only authenticated and authorised devices can access relevant resources. Challenges such as device heterogeneity and scalability are considered, and OKTA provides solutions to mitigate these challenges in the context of IoT security.
76. Discuss OKTA’s approach to user authentication .
Ans:
OKTA adapts to BYOD policies by implementing adaptive authentication. It considers factors such as device trustworthiness and user behaviour to dynamically adjust access controls. This ensures a secure and consistent experience for users, regardless of the devices they bring into the organisational environment.
77. How does OKTA support organisations in managing access for external contractors or vendors without compromising security?
Ans:
OKTA facilitates secure access for external contractors or vendors through features like external identity providers and guest access. By extending access management capabilities to external entities, OKTA enables organizations to collaborate securely while maintaining control over access permissions and ensuring a secure external collaboration environment.
78. Elaborate on OKTA’s role in securing the authentication process for mobile applications, considering the unique challenges posed by mobile platforms.
Ans:
OKTA secures mobile application authentication through Software Development Kits (SDKs) and APIs tailored for mobile platforms. It addresses challenges such as diverse device types and operating systems by providing a consistent and secure Single Sign-On (SSO) experience across various mobile devices.
79. How does OKTA contribute to the Zero Trust security model, and what steps does it take to continuously verify user identities and devices?
Ans:
OKTA aligns with the Zero Trust security model by assuming zero inherent trust and continuously verifying user identities and devices. It employs continuous authentication and adaptive access policies, ensuring that access is granted based on real-time risk factors, and user trust is continuously verified throughout their interaction with applications and resources.
80. Discuss OKTA’s role in mitigating the risks associated with identity-based attacks, such as account takeover.
Ans:
OKTA employs advanced security measures like multi-factor authentication, risk-based authentication, and anomaly detection to mitigate risks associated with identity-based attacks. By proactively monitoring user behaviour and applying adaptive access controls, OKTA enhances security and prevents unauthorised access, safeguarding against threats like account takeover and credential stuffing.
81. How does OKTA manage user consent, particularly in instances where applications require explicit user consent for accessing specific data or features?
Ans:
OKTA provides tools for effective user consent management. In cases where applications mandate explicit user consent, OKTA ensures users have control over their data, allowing them to grant or revoke consent based on their preferences. This functionality is crucial for complying with privacy regulations and upholding user data rights.
82. Discuss OKTA’s backing for federated identity management.
Ans:
OKTA supports federated identity management through protocols like SAML and OAuth. This enables users to seamlessly access resources across trusted domains without the need for separate credentials. Federated identity management enhances user experience and simplifies access across interconnected systems.
83. How does OKTA assist organisations in managing access for temporary or seasonal workers?
Ans:
OKTA facilitates access management for temporary or seasonal workers by streamlining onboarding and offboarding processes. Integrating with HR systems, OKTA ensures rapid access provisioning for seasonal workers and automates the de-provisioning process at the end of their tenure. This agility contributes to operational efficiency.
84. Elaborate on OKTA’s role in identity proofing and the methods it uses to verify user identities in high-security environments.
Ans:
OKTA supports identity proofing through methods such as document verification, biometrics, and knowledge-based authentication. In high-security environments, OKTA enables a multi-layered approach to identity verification, ensuring a robust and reliable process for authenticating user identities with a high level of confidence.
85. Discuss OKTA’s integration capabilities with Human Capital Management (HCM) systems.
Ans:
OKTA seamlessly integrates with Human Capital Management (HCM) systems to enhance employee lifecycle management. This integration ensures that changes in employee status, such as role changes or departures, trigger automatic adjustments in access permissions. OKTA’s integration with HCM systems contributes to a more synchronised and efficient identity and access management process.
86. How does OKTA address scenarios where organisations have diverse application landscapes?
Ans:
OKTA tackles the challenge of diverse application landscapes, including legacy systems, by providing a Universal Directory as a central identity hub. This allows organisations to extend integration to applications not natively supported through custom integrations, LDAP, or other standards, ensuring a cohesive and secure identity management experience.
87. Can you elaborate on OKTA’s approach to risk-based authentication?
Ans:
OKTA employs risk-based authentication by dynamically assessing contextual risk factors such as device health and user behavior. The system adapts authentication requirements in real-time, allowing for a flexible approach that aligns with the perceived risk, enhancing security without compromising user experience.
88. Discuss OKTA’s role in helping organisations enforce password policies.
Ans:
OKTA supports organisations in enforcing robust password policies and best practices. This includes features like self-service password reset and the ability to define and implement strong password policies. By empowering organisations to establish and enforce secure password practices, OKTA contributes to preventing unauthorised access due to weak or compromised passwords.
89. How does OKTA contribute to continuous compliance?
Ans:
OKTA contributes to continuous compliance by aligning with industry standards and regulations. It offers features such as audit logs and policy enforcement, assisting organisations in maintaining compliance with evolving regulatory standards. OKTA’s commitment to staying abreast of compliance requirements enhances its role as a reliable partner in the dynamic regulatory landscape.
90. Explain OKTA’s role in the Single Sign-On (SSO) experience.
Ans:
OKTA plays a central role in providing a seamless Single Sign-On (SSO) experience. By offering Software Development Kits (SDKs) and APIs, OKTA allows developers to integrate SSO capabilities into applications, ensuring users can access multiple applications with a single set of credentials. This enhances user convenience while maintaining a high level of security across the organisation’s application landscape.
91. How does OKTA assist organisations in overseeing identity?
Ans:
OKTA offers specialised support for managing identity and access for non-human entities such as service accounts and bots. It ensures their secure authentication and authorization through mechanisms like API tokens, OAuth, and service account-specific access controls. By implementing these measures, OKTA helps organisations maintain a robust security posture in the domain of automated processes.
92. Discuss OKTA’s capabilities in furnishing insights and analytics related to user authentication .
Ans:
OKTA provides robust capabilities in delivering insights and analytics concerning user authentication and access. Organisations can harness this data for security and compliance purposes by gaining visibility into user behaviour, identifying potential threats, and ensuring adherence to access policies. OKTA’s analytics tools contribute to a proactive approach in managing security and compliance risks.
93. How does OKTA manage scenarios where organisations require integration with industry-specific standards for identity and access management?
Ans:
OKTA accommodates industry-specific standards for identity and access management by providing customization through the OKTA Identity Engine. This enables organizations to tailor identity policies to meet unique industry requirements. Whether adhering to healthcare regulations, financial standards, or other industry-specific mandates, OKTA’s customization capabilities offer the flexibility needed to align with diverse standards.

