Introduction to Quantum:
Quantum computing holds great promise in many fields, such as medical research, artificial intelligence, weather forecasting, etc. But it also poses a significant threat to cyber security, which requires changes in the way we encrypt our data. Even though quantum computers don’t technically have the power to break most forms of encryption we currently have, we still need to stay ahead of the danger and come up with quantum-proof solutions. If we wait until those powerful quantum computers start breaking our encryption, it will be too late.
Another reason to take action now: Scraping Threat:
Even if quantum computers are commercially available, yet another reason quantum-proof data is now at risk of scraping the data by nefarious actors. They are already stealing data and holding it until they can get their hands on a quantum computer to decrypt it. At that point, the data would have already been compromised. The only way to ensure the security of information, especially information that needs to be protected well into the future, is to protect it now with a quantum-proof solution.
- Quantum computers will be able to solve problems that are too complex for classical computers. This involves solving the algorithms behind the encryption keys that protect our data and the infrastructure of the Internet. Much of today’s encryption is based on mathematical formulas that would take today’s computers an impractically long time to decode. To simplify this, for example, think of two large numbers and multiply them together. Coming up with a product is easy, but starting with a large number and dividing it into its two prime numbers is much harder. However, a quantum computer can easily factor those numbers and break the code. Peter Shor has developed a quantum algorithm (named Shor’s algorithm) that easily factors large numbers far faster than a classical computer can. Since then, scientists have been working on developing quantum computers that can factor rapidly into large numbers.
- Today’s RSA encryption, a widely used form of encryption, especially for sending sensitive data over the Internet, is based on 2048-bit numbers. Experts estimate that a quantum computer would need to be as large as 70 million qubits to break that encryption. Considering the largest quantum computer today is IBM’s 53-qubit quantum computer, it could take us a long time to break that encryption.
- As the pace of quantum research continues to accelerate, however, the development of such computers in the next 3-5 years cannot be discounted. As an example, earlier this year, Google and the KTH Royal Institute of Technology in Sweden reportedly “found a more efficient way for quantum computers to perform code-breaking calculations, reducing the resources they need to use”. is required in the order of magnitude.” Their work, highlighted in the MIT Technology Review, demonstrated that a 20-million-qubit computer could crack a 2048-bit number in just 8 hours. That performance means that such continued successes will continue to move up the timeline.
- It is worth noting that sensitive data being corrupted is not the main concern when it comes to quantum encryption threats. More risk is the vulnerability of information that needs to maintain its privacy well in the future, such as national security-level data, banking data, Privacy Act data, etc. Those are the secrets that really need to be protected with quantum-proof encryption now, especially in the face of bad actors stealing it while they wait for a quantum computer that can break the encryption.
The Quantum Threat to Cybersecurity:
- Researchers have been working hard for the past several years to develop “quantum-secure” encryption. American Scientist reports that the US National Institute of Standards and Technology (NIST) is already evaluating 69 potential new methods of what it calls “post-quantum cryptography (PQC)”.
- Another promising method is quantum key distribution (QKD), which uses properties from quantum physics to securely transfer a “quantum key” between two endpoints. Initially, this method was only possible over fibre optic cable, but quantum exchange has now developed a way to transfer it over the Internet as well. Through the company’s Phio TX, businesses can choose the level of quantum readiness they desire and add in QKD or PQC as needed to protect their communications.
- There are so many questions surrounding quantum computing, and scientists continue to work diligently to answer them. When it comes to the impact of quantum computing on cyber security, one thing is certain: it will pose a threat to our current forms of cyber security and encryption. To reduce that threat, we need to change how we protect our data and start doing it now. We need to approach a quantum threat as we do other security vulnerabilities: by deploying a defence-intensive approach, a quantum-secure one characterised by multiple layers of security. Security-forward organisations understand this need for crypto agility and are seeking to make their encryption quantum-secure and quantum-ready for the threats of tomorrow, like the solutions offered by Quantum Exchange.
Adapting Cybersecurity to Address the Threat:
Cybersecurity Implications:
Quantum computing, and prosaic quantum technology, promise to transform cybersecurity in four areas:
1. Quantum random number generation is fundamental to cryptography. Traditional random number generators typically rely on algorithms known as pseudorandom number generators, which are not truly random and are thus potentially open to compromise. Companies such as Quantum Dice and idQuantic are developing quantum random number generators that use quantum optics to generate sources of true randomness. These products are already seeing commercial deployment.
2. Quantum-secure communications, especially quantum key distribution (QKD). The sharing of cryptographic keys between two or more parties allowing them to exchange information privately is at the heart of secure communication. QKD encryption uses aspects of quantum mechanics to enable a completely secret exchange of keys and can even alert the presence of an eavesdropper. QKD is currently limited to fibre transmission of more than 10 kilometres, with proof of concept via satellite over several thousand kilometres. KETS Quantum Security and Toshiba are two leaders in this area.
3. The most controversial application of QC is its ability to break public-key cryptography, particularly the RSA algorithm, which is at the heart of the nearly $4 trillion ecommerce industry. RSA relies on the fact that the product of two primes is computationally challenging to factor. Classical computers would take trillions of years to break RSA encryption. A quantum computer with about 4,000 error-free qubits can beat RSA in seconds. However, this would require close to 1 million of today’s noisy ones. The world’s largest quantum computer is currently less than 100 qubits; However, IBM and Google have road maps to achieve 1 million by 2030. A million-qubit quantum computer may still be a decade away, but that time frame may well be narrowed. Additionally, highly sensitive financial and national security data today is prone to theft – it can only be decrypted once a sufficiently powerful quantum computer is available. The potential danger of public-key cryptography has led to the development of algorithms that are vulnerable to quantum computers. Companies like PQShield are pushing this post-quantum cryptography.
4. Machine learning has revolutionised cyber security, allowing new attacks to be detected and blocked. As the amount and complexity of data increases, the cost of training deep models increases exponentially. Open AI’s GPT-3 used as much carbon as a typical American would do in 17 years. The emerging field of quantum machine learning may enable increasingly faster, more time- and energy-efficient machine learning algorithms. This, in turn, could generate more effective algorithms to identify and defeat new cyberattack methods.
- Quantum computing promises to transform cyber security, but there are substantial challenges to be addressed and fundamental breakthroughs still needed. The most immediate challenge is to obtain a sufficient number of fault-tolerant qubits to fulfil the computational promise of quantum computing. Companies like IBM, Google, Honeywell and Amazon are investing in this problem.
- Quantum computers are currently programmed with different quantum logic gates, which may be acceptable for small quantum computers, but once we reach thousands of qubits it is impractical. Companies such as IBM and Classiq are developing more abstract layers in the programming stack, enabling developers to build powerful quantum applications to solve real-world problems.
- Arguably, the major obstacle in the quantum computing industry would be a lack of talent. While universities churn out computer science graduates at an accelerated pace, little is still being done to train the next generation of quantum computing professionals.
- The United States’ National Quantum Initiative Act is a step in the right direction and includes funding for educational initiatives. There are also some tremendous open-source communities that have developed around quantum computing – perhaps the most exciting and active is the IBM Kiskit community. It will take efforts from governments, universities, industry and the wider technology ecosystem to enable the level of talent development needed to truly capitalise on quantum computing.
Quantum Computing Challenge:
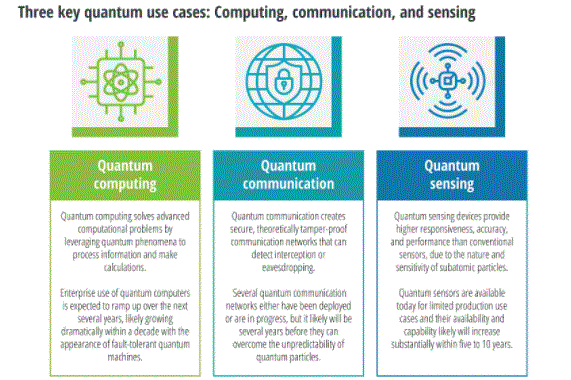
- The quantum revolution is upon us. Although the profound impact of large-scale fault-tolerant quantum computers may be a decade away, near-term quantum computers will still reap tremendous benefits. We are seeing substantial investment in scaling qubit count, error correction and solving core problems surrounding algorithms.
- From a cybersecurity perspective, while quantum computing may render some existing encryption protocols obsolete, it holds promise for increasing communication security and substantial levels of privacy. Organisations must think strategically about the long-term risks and benefits of quantum computing and technology and engage critically today to prepare for the quantum revolution of tomorrow.
Preparing For The Quantum Future:
- Quantum mechanics is a branch of physics that explores how the physical world works at a fundamental level. At the quantum level, particles can occupy more than one state at the same time, and they can correlate their states even when separated by large distances. Quantum computing uses these quantum phenomena to process information in profoundly new ways. The worldwide market for quantum computing is projected to exceed USD 10 billion by 2024.
- In symmetric encryption, the same key is used to encrypt and decrypt a given piece of data. The Advanced Encryption Standard (AES) is an example of a symmetric algorithm. Adopted by the US government, the AES algorithm supports three key sizes: 128 bits, 192 bits, and 256 bits. Symmetric algorithms are commonly used for bulk encryption tasks, such as encoding major databases, file systems, and object storage.
- In asymmetric encryption, data is encrypted using one key (commonly referred to as the public key) and decrypted using another key (commonly referred to as the private key). Although the private key and the public key are different, they are mathematically related. The widely employed Rivest, Shamir, Edelman (RSA) algorithm is an example of an asymmetric algorithm. Even though it is slower than symmetric encryption, asymmetric algorithms solve the problem of key distribution, which is an important issue in encryption.
Quantum cybersecurity: The positives and negatives:
Large-scale quantum computers will expand computing power, creating new opportunities for improving cyber security. Quantum-era cyber security will give quantum-age cyber attacks the power to detect and deter them before they do harm. But it could turn out to be a double-edged sword, as quantum computing could also pose new risks, such as the ability to quickly solve the difficult maths problems that are the basis of some forms of encryption. While post-quantum cryptography standards are still being finalised, businesses and other organisations can start preparing today.
Here comes quantum computing:
- Encryption methods will change with the advent of quantum computing. Currently, the most widely used asymmetric algorithms are based on difficult mathematical problems, such as factoring large numbers, that can take thousands of years on today’s most powerful supercomputers.
- However, research by Peter Shor at MIT more than 20 years ago showed that the same problem could theoretically be solved in days or hours on a large-scale quantum computer. Future quantum computers may be able to break asymmetric encryption solutions that base their security on an integer factorization or a discrete logarithm
- Although symmetric algorithms are not affected by Shor’s algorithm, the power of quantum computing requires multiplication in prime sizes. For example, large quantum computers running Grover’s algorithm, which uses quantum concepts to search databases very quickly, can provide a quadratic improvement in brute-force attacks on symmetric encryption algorithms such as AES.
- To help withstand brute-force attacks, key sizes must be doubled to support the same level of security. For AES, this meant using 256-bit keys to maintain today’s 128-bit security power.
- Even though large-scale quantum computers are not yet commercially available, there are now significant advantages to introducing quantum cyber security solutions. For example, a malicious entity today could capture secure communications of interest. Then, when quantum computers are available on a large scale, that enormous computing power can be used to break encryption and learn about those communications.
- Considering its potential risks, quantum cyber security may provide a more robust and compelling opportunity to protect critical and personal data than is currently possible. It is particularly useful in quantum machine learning and quantum random number generation.
Quantum risks to cybersecurit:
- According to a 2018 report from the National Academies of Sciences, Engineering and Medicine, “a quantum computer uses unusual features of quantum mechanics—the non-spontaneous behaviour of very small particles—to perform calculations, unlike current computers.” This feature of the new technology enables a quantum computer, which encodes data into qubits (quantum bits), to extend the possible states of a classical computer.
- A traditional computer bit is either 0 or 1, and cannot represent 0 and 1 simultaneously. In contrast, an orbit can represent both 0 and 1 at any given time, a phenomenon known as superposition. As a result of this feature, a quantum computer can process large-scale calculations, effectively increasing the power and capability of the new technology.
- A fully robust quantum computer is likely more than a decade away. However, the major tech giants, such as Google, Intel, IBM and Microsoft, already have smaller quantum computers, which pack more quantum bits to increase their performance. Other vendors leading the way in this technology include Toshiba, NTT, Honeywell, D-Wave Solutions and Alibaba Quantum Computing. Reviews of these companies indicate a race toward developing systems that can resolve complex transactions using multiple variables. Some of the application areas include predicting stock market volatility, designing AI, weather forecasting, and cracking complex cryptography methods.
- Quantum computers rely on probabilistic algorithms that give results within a certain number of probabilities rather than exact answers. This feature makes the technology ideal for a set of specialised problems in areas such as risk management, finance, and a range of possibilities. With this in mind, it is important to identify significant cyber security challenges that predate the advent of general-purpose and easily accessible quantum computers.
What is a Quantum Computer:
- The biggest concern of cyber security analysts is that new tools based on quantum physics, which are believed to be superior to standard computers, will enable cyber attackers to break secure cryptography methods. This prediction, in turn, provides reliable encrypted communication and unsecured data storage.
- Classical digital ciphers rely on complex mathematical formulas to convert data into encrypted messages for storage and transmission. A digital key is used to encrypt and decrypt the data. As a result, an attacker attempts to break the encryption method used to steal or modify the protected information. The obvious way to do this is to try all possible keys to identify the key that decrypts the data back into a readable form. The process can be controlled using a conventional computer, but it requires a lot of effort and time to complete. “The world’s fastest supercomputer will take trillions of years to find the right key,” says an American scientist. In contrast, Grover’s algorithm, a quantum computing method, simplifies and accelerates the cracking process.
- Certainly, the transition phase from conventional to quantum computers will take a long time. This prediction suggests that some computing areas will involve the use of both technologies rather than replacing one with the other. As quantum computers complement and accelerate the power of traditional systems, modern cryptographic methods will remain in use throughout the period. Ultimately, quantum computing developers will have implications for national security because of their ability to break today’s cryptography to reveal encrypted information and stored data.
- As an article on Scientific American states, the issue of quantum computing breaking modern cryptography remains hypothetical because the power of existing quantum computers is incapable of cracking commonly used encryption approaches. Furthermore, according to the National Academies, current quantum computers ***** are too error-prone for current codes. Significant advances in new technology are still needed for manufacturers and developers to effectively break the widely used code on the Internet. Good luck to cyber security enthusiasts?
Conclusion:
Quantum Computing Power Malware Attack:
Today hackers can adopt advanced techniques such as machine learning techniques to develop and distribute lethal forms of malware. What can a quantum computer offer to criminals running massive data sets for machine learning? Threat actors can leverage the power of quantum computing to create a new approach to breaching cyber security. On classical computers such activities can be very computationally expensive, but with quantum computers, the hacker can quickly analyse datasets and proceed to launch a sophisticated attack on a large population of networks and devices.