Rated #1 Recoginized as the No.1 Institute for Ethical Hacking Training in Hyderabad
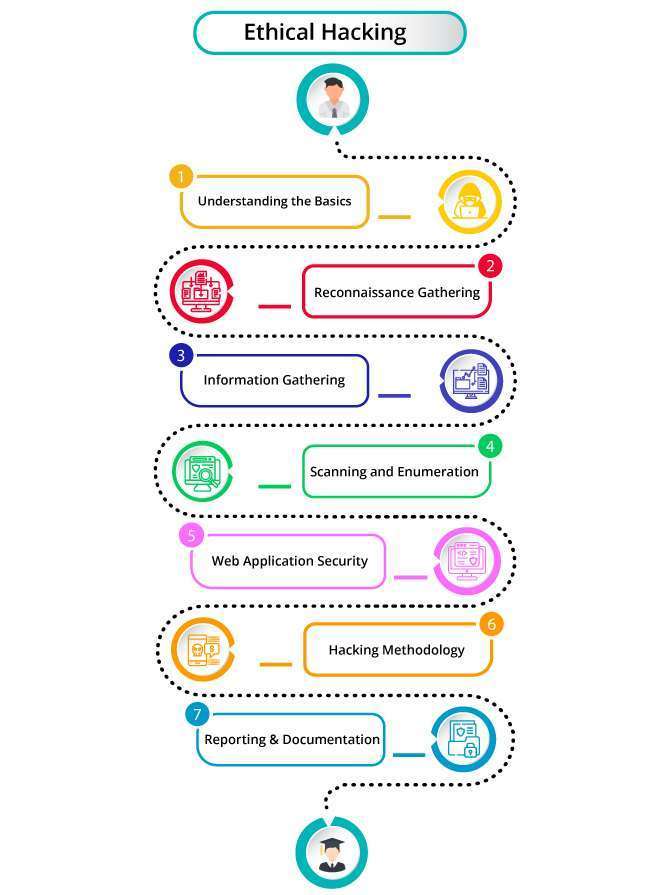
Students will gain a Complete understanding of ethical hacking certification training strategies by enrolling in ACTE Institute Ethical Hacking Course. Network scanning, and system hacking will all be covered in the top ethical hacking course in Hyderabad.
Students Receive Complete Ethical Hacking Training in Hyderabad from the Ground up to the Expert Level of the Course. We Provide a Perfect Setting for Skill Development with Flexible Scheduling, Advice from Specialists in the Field, and a Cooperative Learning Environment. Get a Desired Ethical Hacking Certification Online to Advance Your Career in the Quickly Changing Cybersecurity Industry.
- The Best Curriculum at a Fair Price with 100% Placement.
- The Best Program for Ethical Hacking Training in Hyderabad.
- Over 350+ Employing Clients and over 11462+ Trained Learners.
- Benefits from Countless Opportunities to Interview with Top Global Companies.
- Learn from Certified Ethical Hacking Experts with More than 12+ Years of Experience.
- Take Part in Interactive Sessions That Will Accelerate up the Development of Your Ethical Hacking Course.