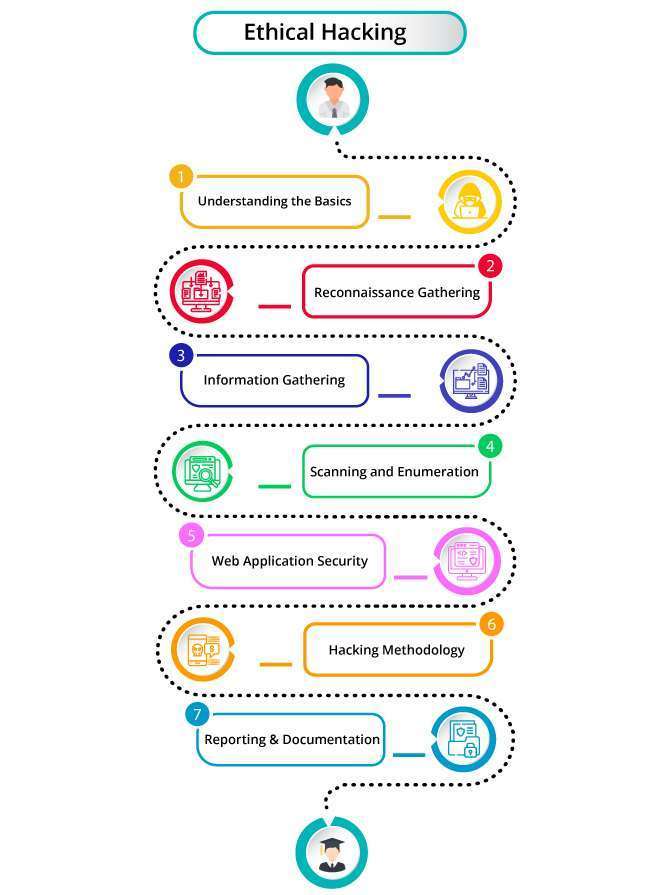
As the world becomes more reliant on technology, the subject of cybersecurity is becoming increasingly vital. Ethical hacking is one aspect of cybersecurity that has received a lot of attention. Ethical hacking is detecting weaknesses in computer systems and networks in order to improve their security. A course in ethical hacking equips students with the information and tools they need to become ethical hackers. An ethical hacking course often covers a wide variety of cybersecurity and network security issues. Penetration testing, social engineering, and vulnerability assessment are among the hacking techniques taught to students. They also learn about several sorts of cyber-attacks, such as malware, phishing, and denial of service assaults. Students also learn about the legal and ethical elements of hacking, such as the significance of acquiring formal authorization before doing any security testing.
Additional Info
Benefits of taking Ethical hacking Training:
Ethical hacking, also known as penetration testing, involves authorized individuals attempting to exploit vulnerabilities in a computer system to identify weakznesses and provide recommendations for strengthening security. Undertaking an ethical hacking course can offer numerous benefits:
Cybersecurity Knowledge: Ethical hacking courses provide a deep understanding of cybersecurity concepts, techniques, and tools. You will learn about various vulnerabilities, attack vectors, and security controls, enabling you to assess and enhance the security of computer systems and networks.
Hands-on Experience: Ethical hacking courses often include practical exercises and labs where you can apply your knowledge in a controlled environment. This hands-on experience helps you develop skills in identifying vulnerabilities, exploiting them, and implementing security measures.
Career Opportunities: With the increasing reliance on technology, there is a high demand for skilled cybersecurity professionals. Completing an ethical hacking course can open up career opportunities in fields such as penetration testing, vulnerability assessment, security auditing, and cybersecurity consulting.
Defensive Skills: By learning how to ethically hack into systems, you gain valuable insights into potential attack vectors. This knowledge can be used to strengthen the security of systems, networks, and applications by implementing appropriate countermeasures and defenses.
Protection against Cyber Threats: Understanding the mindset and techniques of hackers allows you to proactively identify and mitigate vulnerabilities in your own systems. By taking preventive measures, you can reduce the risk of falling victim to malicious attacks and protect your sensitive data.
Legal and Ethical Awareness: Ethical hacking courses emphasize the importance of legal and ethical considerations. You will learn about the boundaries and legal frameworks governing cybersecurity practices, ensuring that you operate within the law and adhere to ethical standards while assessing system security.
Continuous Learning: The field of cybersecurity is constantly evolving, with new threats and vulnerabilities emerging regularly. Ethical hacking courses foster a mindset of continuous learning, equipping you with the skills to stay updated on the latest security trends, technologies, and best practices.
Current trends and techniques used in Ethical hacking:
As technology continues to advance, new trends and techniques have emerged in the field of ethical hacking. These trends and techniques are aimed at staying ahead of evolving cyber threats and ensuring the security of sensitive information. Here are some of the current trends and techniques used in ethical hacking:
Cloud Security:
As organizations increasingly adopt cloud computing, ethical hackers focus on identifying vulnerabilities and misconfigurations specific to cloud environments. This includes assessing the security of cloud infrastructure, platforms, and services, as well as understanding the shared responsibility model between cloud providers and customers.
Internet of Things (IoT) Security:
The proliferation of IoT devices has introduced new security challenges. Ethical hackers are exploring vulnerabilities in smart devices, including cameras, home automation systems, wearables, and industrial IoT devices. They analyze device communication protocols, firmware, and the overall ecosystem to identify potential attack vectors.
Practical Application:
Many Digital Marketing certifications include practical exercises, case studies, and real-world projects that allow individuals to apply their knowledge in practical scenarios. This hands-on experience enhances their skills by providing opportunities to implement digital marketing strategies, analyze results, and make data-driven decisions.
Mobile Application Security:
With the widespread use of mobile apps, securing them against unauthorized access, data leaks, and other vulnerabilities is crucial. Ethical hackers employ techniques like reverse engineering, static and dynamic analysis, and code review to identify vulnerabilities in mobile applications on various platforms (Android, iOS).
Social Engineering:
Social engineering remains a prevalent technique used by hackers. Ethical hackers study and employ tactics such as phishing, pretexting, and baiting to assess an organization's susceptibility to human-based attacks. This includes conducting simulated phishing campaigns and educating employees about the risks and countermeasures.
Bug Bounty Programs:
Many organizations have implemented bug bounty programs, inviting ethical hackers to discover and responsibly disclose vulnerabilities in their systems. These programs incentivize security researchers to find vulnerabilities and report them for a monetary reward, fostering a collaborative approach to security testing.
Red Teaming:
Red teaming involves simulating real-world attack scenarios to evaluate an organization's overall security posture. Ethical hackers work as part of a red team to conduct comprehensive assessments, including social engineering, physical security tests, and technical attacks, with the goal of identifying weaknesses and improving defenses.
Machine Learning and Artificial Intelligence (AI) in Security:
Ethical hackers leverage machine learning and AI techniques to enhance security testing. This includes developing models to identify patterns, anomalies, and potential vulnerabilities in large datasets, as well as using automated tools for vulnerability scanning and analysis.
DevSecOps:
The integration of security practices into the software development lifecycle is gaining momentum. Ethical hackers assist organizations in implementing security controls and conducting continuous security testing throughout the development process. This ensures that security vulnerabilities are identified early and addressed proactively.
Roles and Responsibilities of Ethical Hacker:
- In today's technological world, the duties and obligations of an ethical hacker are not just interesting but essential. These experts have the ability to safeguard our digital assets and prevent unauthorized access to our data. Ethical hackers are essential to the security of businesses and people because of the knowledge and experience they bring to the table.
- Ethical hackers are professionals whose job it is to find security flaws in software and hardware. They put their hacking talents to good use by testing the limits of security systems in an effort to find vulnerabilities that may be exploited by malicious hackers. By doing so, they aid businesses in identifying their weak points and implementing countermeasures. Data breaches and other forms of cyber-attack may be avoided if businesses take this preventative measure.
- Ethical hackers also do vulnerability testing, which is like modelling a cyberattack to see how well a company's security measures work. They look at systems, networks, and apps very carefully to see if there are any holes or weak spots that could be used. By doing these tests, ethical hackers give organizations useful information about their security and help them set up strong security rules to reduce risks.
Skills needed to be an Ethical Hacker:
Becoming an ethical hacker requires a combination of technical skills, problem-solving abilities, and a strong understanding of cybersecurity principles. Here are some essential skills needed to excel in this field:
Networking Knowledge:
A solid understanding of networking protocols, architectures, and how different components interact is crucial. This includes TCP/IP, DNS, routing, switching, firewalls, and VPNs. Knowledge of network scanning and enumeration techniques is also important.
Operating Systems Knowledge:
Proficiency in various operating systems such as Windows, Linux, and macOS is necessary. Understanding the inner workings, file systems, and security mechanisms of these platforms enables ethical hackers to identify vulnerabilities and weaknesses.
Programming Skills:
Proficiency in programming languages like Python, C/C++, Java, or scripting languages like Bash or PowerShell is beneficial. Programming skills help in developing custom tools, automating tasks, and understanding vulnerabilities at a deeper level.
Pay scale of Ethical Hacker:
The salary of an ethical hacker in India can vary depending on factors such as experience, skills, location, industry, and the organization they work for. Ethical hacking is a specialized field within the broader cybersecurity domain, and professionals with the right skills and expertise are often in high demand.
Junior Ethical Hacker: Entry-level positions or those with a few years of experience can expect a salary range of approximately INR 4 lakh to INR 8 lakh per year.
Mid-Level Ethical Hacker: With a few years of experience and additional certifications, mid-level ethical hackers can earn between INR 8 lakh and INR 15 lakh annually.
Senior Ethical Hacker/Consultant: Ethical hackers with significant experience, advanced certifications, and a proven track record may earn salaries ranging from INR 15 lakh to INR 30 lakh or more per year. Senior positions often involve leadership roles and responsibilities.