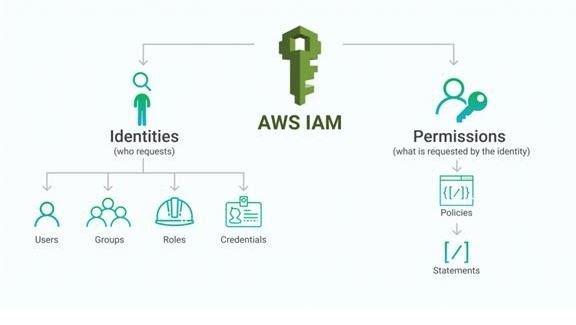
- AWS Identity and Access Management (IAM) is a web service that encourages you to safely control access to AWS resources.
- You use IAM to control who is validated (signed in) and authorized (has permissions) to utilize resources.

- At the point when you initially make an AWS account, you start with a solitary sign-in character that has total access to all AWS services and resources in the record.
- This personality is known as the AWS account root client and is gotten to by marking in with the email address and secret key that you used to make the record.
- We unequivocally suggest that you don’t utilize the root client for your ordinary errands, even the authoritative ones. Rather, stick to the best act of utilizing the root client just to make your first IAM client.
- At that point safely lock away the root client credentials and use them to perform just a couple of accounts and service the management tasks.
Policies
Features
Shared access to your AWS account
You can grant other people permission to administer and use resources in your AWS account without having to share your password or access key.
Granular Permissions
- You can give various consents to various individuals for various resources. For instance, you may permit a few clients complete access to Amazon Elastic Compute Cloud (Amazon EC2), Amazon Simple Storage Service (Amazon S3), Amazon DynamoDB, Amazon Redshift, and different AWS services.
- For different users, you can permit read-only access to simply some S3 buckets, or consent to manage only some EC2 instances, or to get to your charging data yet nothing else.
Secure Access To AWS Resources For Applications That Run On Amazon EC2
You can utilize IAM highlights to safely give accreditations to applications that sudden spike in demand for EC2 instances. These qualifications give authorizations to your application to get to different AWS resources. Models incorporate S3 buckets and DynamoDB tables.
Multi-Factor Authentication (MFA)
You can add two-factor verification to your record and to individual clients for additional security. With MFA you or your clients must give not just a secret word or access key to work with your record, yet additionally a code from a specially configured device.
Identity Federation
You can allow users who already have passwords elsewhere—for example, in your corporate network or with an internet identity provider—to get temporary access to your AWS account.
Identity Information For Assurance
On the off chance that you use AWS CloudTrail, you get log records that incorporate data about the individuals who made solicitations for resources in your record. That data depends on IAM identities.
PCI DSS Compliance
IAM supports the processing, storage, and transmission of credit card data by a merchant or service supplier, and has been approved as being consistent with Payment Card Industry (PCI) Data Security Standard (DSS).
Eventually Consistent
- IAM, in the same way as other AWS services, is eventually consistent. IAM accomplishes high accessibility by repeating data over different servers inside Amazon’s databases on the world.
- On the off chance that a solicitation to change a few data is fruitful, the change is submitted and securely put away. In any case, the change must be reproduced across IAM, which can take some time.
- Such changes include creating or updating users, groups, roles, or policies. We suggest that you do exclude such IAM changes in the basic, high-availability code paths of your application.
- Rather, make IAM changes in a different statement or arrangement schedule that you run less as often as possible. Likewise, make sure to check that the progressions have been propagated before production workflows depend upon them.
Free To Use
AWS Identity and Access Management (IAM) and AWS Security Token Service (AWS STS) are features of your AWS account offered at no additional charge. You are charged only when you access other AWS services using your IAM users or AWS STS temporary security credentials.
Use Cases
Fine-Grained Access Control To AWS Resources
IAM empowers your clients to control access to AWS service APIs and to explicit resources. IAM likewise empowers you to include explicit conditions, for example, time of day to control how a client can utilize AWS, their starting IP address, regardless of whether they are utilizing SSL, or whether they have verified with a multi-factor authentication device.
Multi-Factor Authentication For Highly Privileged Users
Protect your AWS environment by using AWS MFA, a security feature available at no extra cost that augments user name and password credentials. MFA requires users to prove physical possession of a hardware MFA token or MFA-enabled mobile device by providing a valid MFA code.
Analyze Access
IAM encourages you to analyze access over your AWS condition. Your security groups and chairmen can rapidly approve that your strategies just give the planned open and cross-account access to your resources. You can likewise effectively recognize and refine your arrangements to permit access to just the services being utilized. This causes you to all the more likely cling to the guideline of least privilege.
Integrate With Your Corporate Directory
IAM can be used to grant your employees and applications federated access to the AWS Management Console and AWS service APIs, using your existing identity systems such as Microsoft Active Directory. You can use any identity management solution that supports SAML 2.0, or feel free to use one of their federation samples (AWS Console SSO or API federation).
Working Of IAM
Identity Access and Management offers the best infrastructure that is required to control all the authorization and authentication for your AWS account. Here are some of the elements of IAM infrastructure:
Principle
The principle in the AWS IAM is used to take an action on the AWS resource. The administrative IAM user is the first principle, which can allow the user for the particular services in order to assume a role. You can support the federated users to allow the application access your current AWS account.
Request
While using the AWS management console, the API or CLI will automatically send the request to AWS. It will specify the following informations:
- Actions are considered as the principles to perform
- The actions are performed based on the resources
- The principle information includes the environment where the request has made previously
Authentication
It is one of the most commonly used principles which is used to sign in for AWS while sending the request to it. However, it also consists of the alternate services like Amazon S3 which will allow requests from the unknown users. In order to authenticate from the console, you need to sign in with your login credentials like username and password. But to authenticate you need to provide the secret and access key to them along with the required additional security information.
Authorization
While authorizing the IAM values that are raised from the request will context to check all the matching policies and evaluate whether it is allowed or denied the respective request. All the policies are stored in IAM as JSON documents and offer the specified permission for the other resources. AWS IAM automatically checks all the policies which particularly match the context of all your requests. If the single action is denied then the IAM denies the entire request and regret to evaluate the remaining ones, which is called as an explicit deny. The following are some of the evaluation logic rules for IAM:
- All the requests are denied by default
- The explicit can allow the overrides by default
- An explicit may also deny the override by allowing them
Actions
After processing your request authorization or unauthenticated automatically, AWS approves your action in the form of request. Here all the actions are defined by services and things can be done by resources such as creating, editing, deleting and viewing. In order to allow the principle of action, we need to include all the required actions into policy without affecting the existing resource.
Resources
After getting the AWS approvals all the actions in your request can be done based on the related resources that contain in your account. Generally, a resource is called an entity which exists particularly within the services. These resource services can be defined as a set of activities which is performed particularly on each and every resource. If you want to create one request, first you need to perform the unrelated action that cannot be denied.
Functions Of AWS IAM
Following are important Amazon IAM Functions, let’s discuss them one by one:
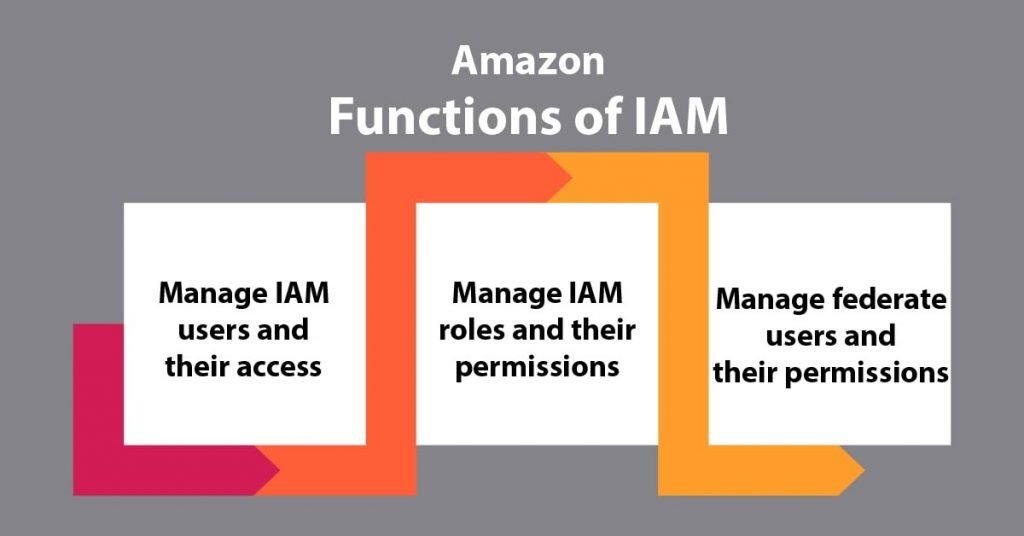
Amazon Identity and Access Management – Functions
a. To Manage AWS IAM Users And Their Access
The user will be able to produce users in Amazon IAM, assign them individual security. The user can also demand the temporary security credentials to produce users access to AWS services and resources. Here, user will be able to manage permissions so as to manage those operations a user can perform.
b. To Manage Amazon IAM Roles And Their Permissions
The user will be able to produce roles in AWS Identity and access management and manage permissions to manage that operations are performed by the entity, or AWS service, that assumes the role. The user will be able to conjointly outline the entity is allowed to assume the role. Additionally, the user will be able to use service-linked roles to delegate permissions to AWS services that make and manage AWS resources on The user are behalf.
c. To Manage To Federate Users And Their Permissions
The user will be able to alter identity federation to permit existing identities (users, groups, and roles) in The user are an enterprise to access the AWS Management Console, decision AWS APIs, and access resources, while not the necessity to make an IAM user for every identity. Use any identity management resolution that supports SAML 2.0, or use one in all our federation samples (AWS Console SSO or API federation).
4. Amazon IAM Uses
Here, we will clear the Applications of AWS IAM in detail:
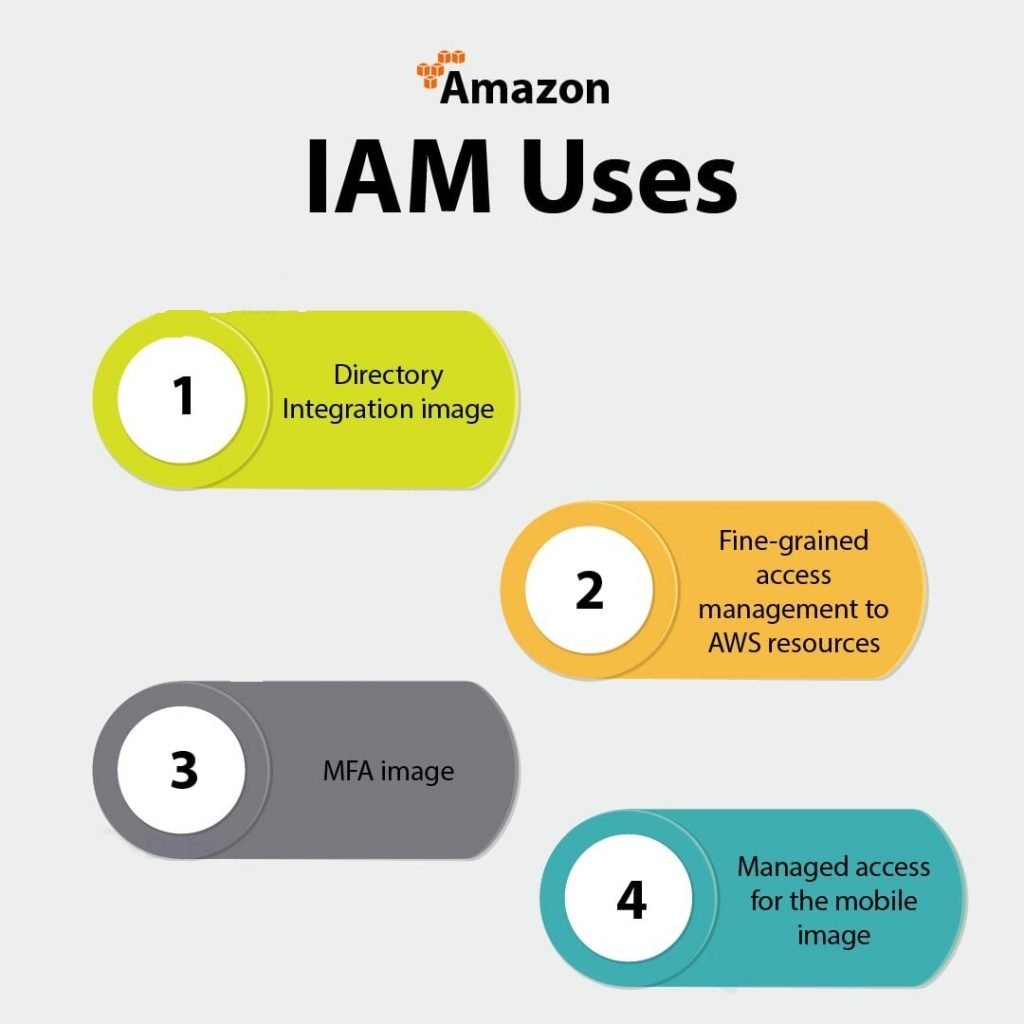
Amazon Identity and Access Management – Uses
a. Directory Integration Image
AWS IAM is accustomed grant the user staff and applications united access to the AWS Management Console and AWS service APIs, using the user existing identity systems like Microsoft Active Directory. The user will use any identity management answer that supports SAML 2.0, or be at liberty to use one in every of our federation samples (AWS Console SSO or API federation).
Directory Integration Image
b. Fine-Grained Access Management To AWS Resources
Amazon IAM permits the users to regulate access to AWS service Apis and to specific resources. IAM also permits The user to feature specific conditions like time of day to regulate however a user will use AWS, their originating science address, whether or not they are using SSL, or whether or not they have genuine with a multi-factor authentication device.
Fine-Grained Access
c. MFA Image
Multi-factor authentication for extremely valuable as it protects The user are AWS surroundings by using AWS MFA, a security feature out there at no further value that augments username and countersigns credentials. Amazon MFA needs users to prove physical possession of a hardware MFA token or MFA-enabled mobile device by providing a legitimate MFA code.
MFA Image
d. Managed Access To The Mobile Image
Manage access control for mobile applications with net Identity suppliers. The user can modify the mobile and browser-based applications to firmly access AWS resources by requesting temporary security credentials that grant access solely to specific AWS resources for a configurable amount of the user’s time.
Mobile Image
Creating An IAM User
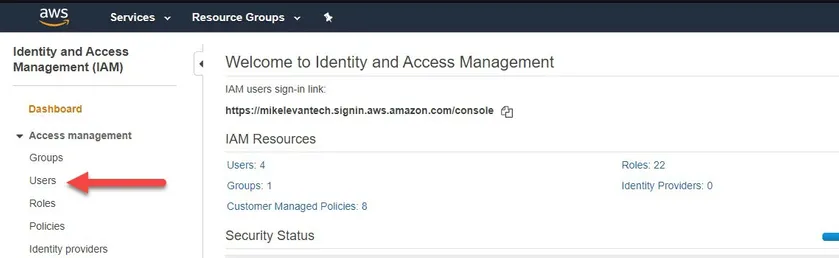
Your first task will be to create an IAM user. An IAM user allows you to authenticate across many different AWS services. To create the IAM user, first navigate to IAM in the management console. You will see a welcome page with IAM Resources as shown in the screenshot below.
Click on Users on the left-hand side of the screen.
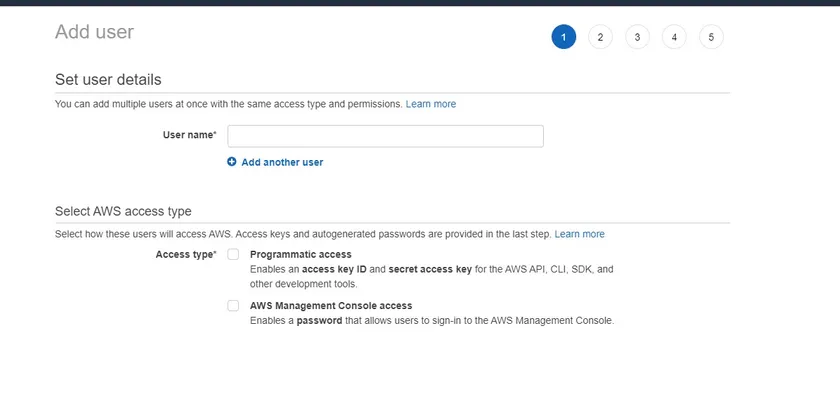
Once you are on the Add user page, click the Add User button. You will see a two options: User name which can be anything you’d like and Access type. Access type indicates how the IAM user will be used.
If you plan to connect to AWS via tool like the AWS CLI IAM, SDK or other, choose Programmatic access. If you’re setting up a user to access the management console only, choose AWS Management Console access. For this demonstration, check the box next to Programmatic access.
Click on Next: Permissions to get started assigning permissions.
Assigning IAM User Permissions
- Once you’ve defined the username, it’s time to start assigning permissions to this user. Permissions give the IAM user the ability to interact with various AWS services through policies.
- Before assigning permissions, always track down what permissions the user will need. Do not assign overly lax permissions!
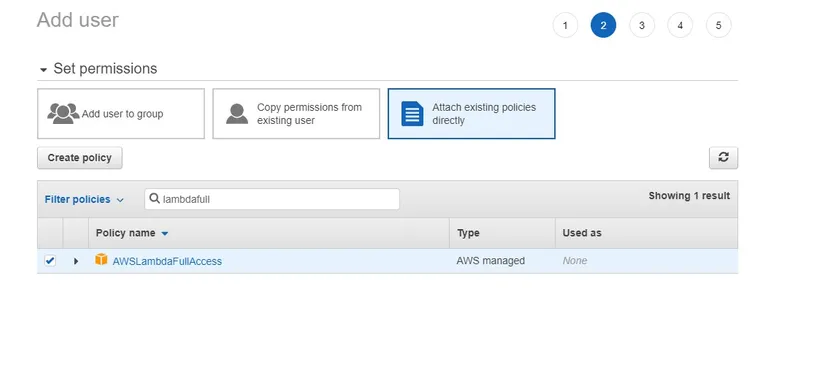
- For this article, no specific permissions are necessary. Let’s find a few existing policies to attach to this IAM user. Click on Attach existing policies directly and search for an example policy called AWSLambdaFullAccess. This policy is used for an AWS Lambda function.
Assigning Tags
Once the permissions are attached to the user, click the Next: Tags button. Tags are a great way to organization resources in AWS. For this tutorial though, they aren’t necessary.
Completing IAM User Setup
At this point, the IAM user set up is complete. Click the Create user button as seen below to create the IAM user.
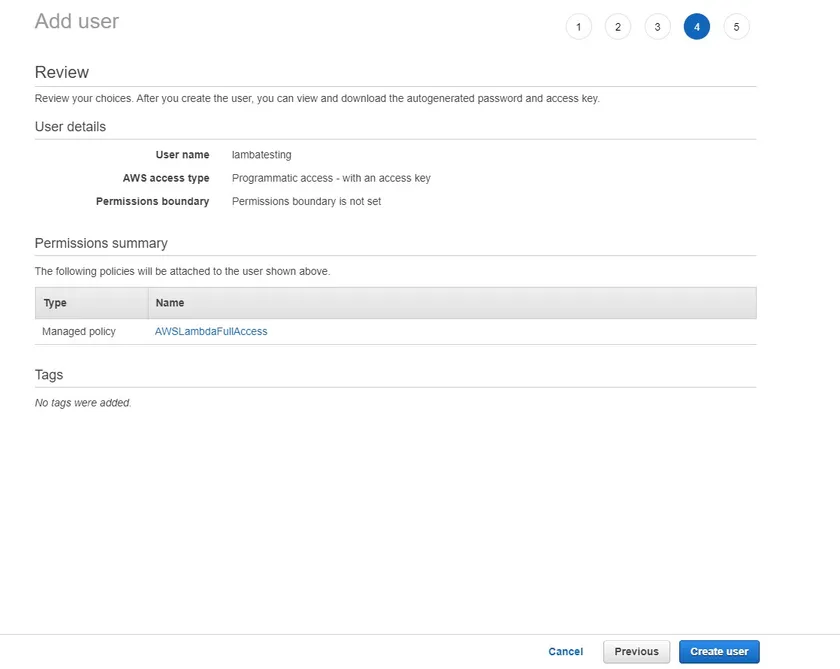
Now that the user is created, you’ll be presented with two critical pieces of information – the Access Key ID and the Secret access key. You will need to provide these two items to the AWS CLI and other tools to successfully authenticate to AWS.
The secret access key is only displayed once. Be sure to copy and store it in a safe place like a password manager.
Once you’ve copied the access key ID and the secret access key, it’s time to create the IAM role.
Creating An IAM Role
- In the last section, you created an IAM user and assigned permissions directly to it. But what if you have a more complex setup that needs that set of permissions available to multiple users? One way to do that is with IAM roles.
- IAM roles are essentially “groups” of permissions that various users can attach to inherit those permissions. In this section, you’re going to create a role for the AWS Lambda service.
- To get started, navigate to IAM and instead of clicking on Users, click on Roles this time. Once the page comes up, click on the Create role button as you can see below.
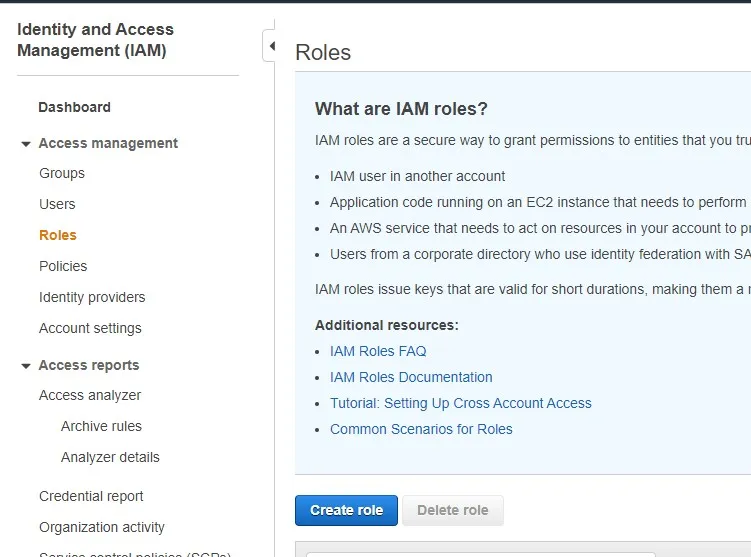
Assigning A Type Of Role
The next step is to tell IAM what you’re going to use this role for. For this tutorial, choose AWS service. Since the role to create will be used by Lambda, choose Lambda or whatever service you intend this role to access.
When you’re done, click on the Next: Permissions button as shown below.
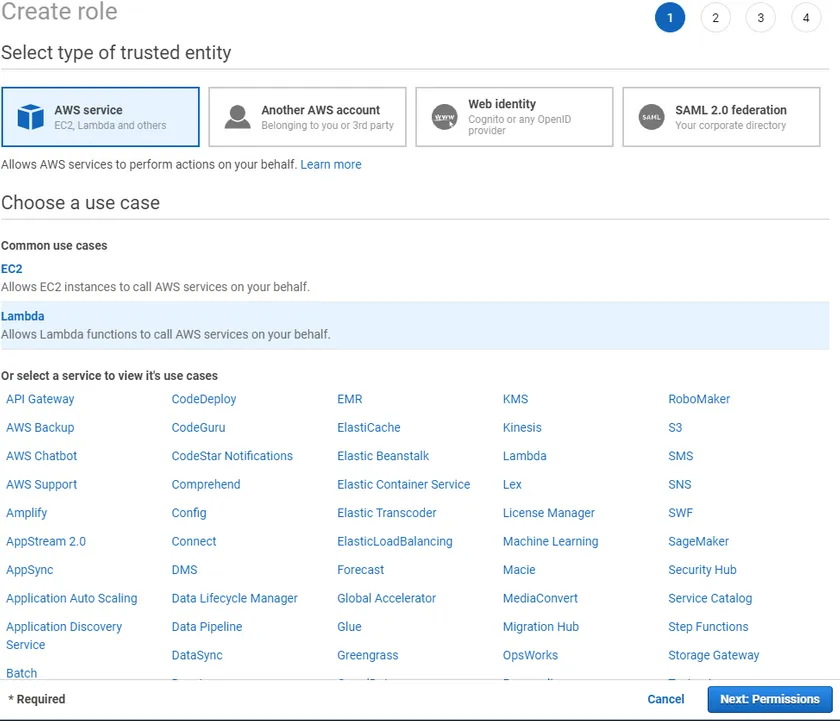
Attaching IAM Role Permission Policies
The next step is to assign a policy or policies to the role. For this example, we’d like the role to have full control over all EC2 instances in the account. Filter the policies by typing AmazonEC2Full in the Filter policies box and the policy should come up.
When the policy shows up, select the checkbox by the policy and click on Next: Tags to continue to the tags screen.
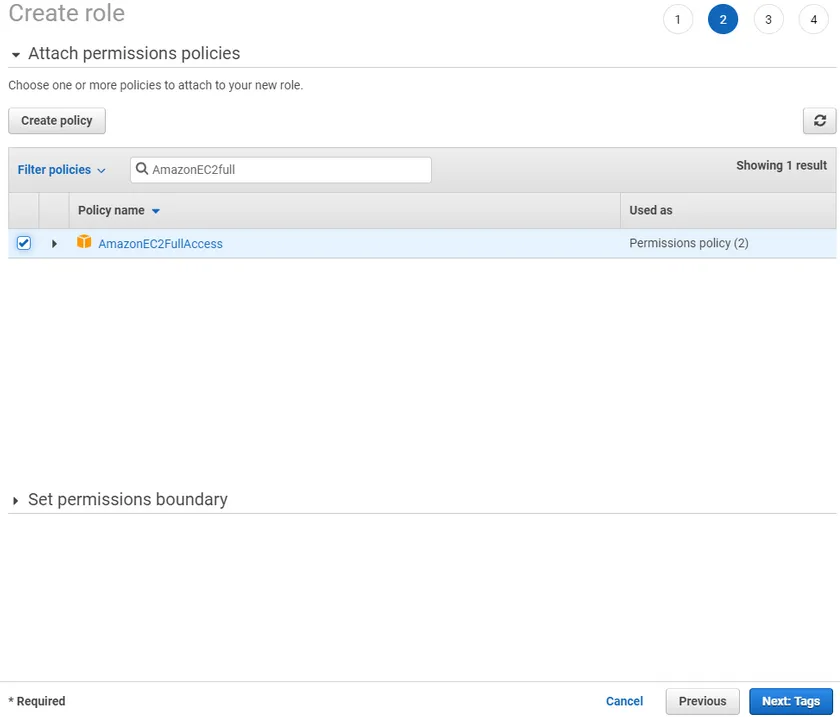
Assigning Tags
Since we don’t need to assign any tags to this role, click the Next: Review button.
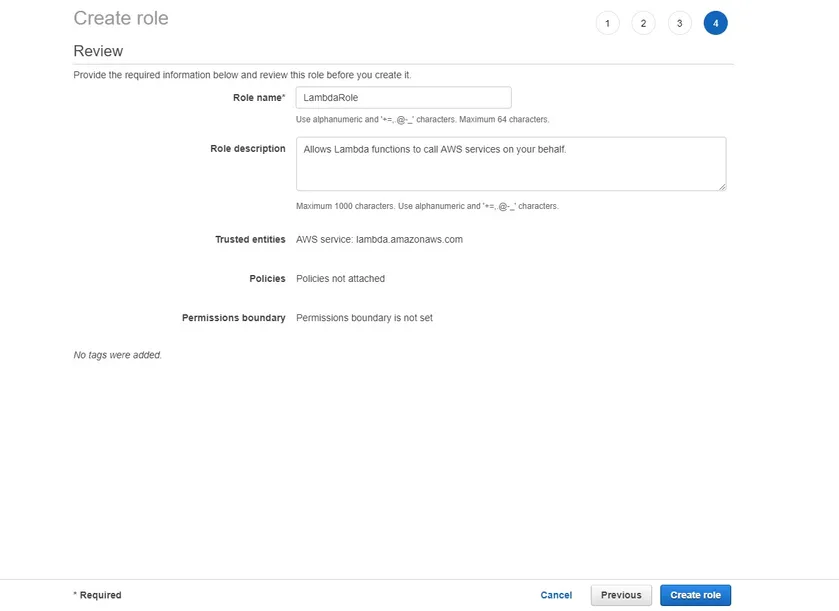
Completing IAM Role Setup
The final screen allows you to review all settings before actually creating the role. You will see five fields – Role name, Role description, Trusted entities, Policies and Permissions boundary.
- Role description – this is generated by default but you can change it to your liking
- Trusted entities – IAM users are associated with a specific person. IAM roles are different. An IAM role is instead a trusted entity which assumes a task to achieve. In this tutorial, that task is to create an EC2 instance.
Provide a Role name and click Create role as shown below.
You have now successfully created an IAM role!
Setting up a password policy for your AWS Account using IAM
In this section, we’ll help you set up your AWS account password policy.
- Navigate to the AWS IAM console and click on Account settings as shown here:
2. Next, click on the Set password policy button
3. You can now set up your password policy by defining a set of rules and selecting the complexity requirements for the password an IAM user can set. The example below meets the standards recommended by the Center for Internet Security (CIS):
Setting up Multi-Factor Authentication (MFA) using AWS IAM
Multi-Factor Authentication (MFA) protocols offer a great way to improve the overall security posture of your AWS cloud services and resources. This simple step could even prove instrumental in preventing costly breaches for your organization. In this tutorial, we will show you how to set up MFA using a mobile device.
- Go to the AWS console, and select your username in the top right corner
- In the dropdown menu, select the My Security Credentials button
3. Scroll down the page until you reach the section titled Multi-factor authentication (MFA), then select the Assign MFA Device button
4. Select virtual or hardware MFA device as appropriate
4a. If a virtual MFA device was selected, scan the QR code with your MFA app (such as Duo Mobile, Google Authenticator, Microsoft Authenticator, etc.) and input two subsequent codes. Select the Assign MFA button and you’re all set!
4b. If instead, you wish to use a hardware MFA device (such as yubikey) for additional security, you will be prompted to insert the MFA device and tap the button. Your web browser may inform you that aws.amazon.com is requesting information about your hardware device. If so, grant it. Now your hardware MFA device is ready to go.
CONCLUSION:
In thisTutorial, you took a hands-on approach to create IAM users and roles. While working with IAM users and roles, you created permissions. You ensured while creating permissions that the IAM user and IAM role had permissions attached so they could access AWS resources. Once an IAM user and role is created, you can attach various policies. Using the AWS console you created the necessary IAM user, role, and attached the needed policies.