
Top Cryptography Interview Questions & Answers [SCENARIO-BASED ]
Last updated on 04th Jul 2020, Blog, Interview Questions
1. What is the primary purpose of using a hash function in cryptography?
Ans:
- Hash functions play a pivotal role in cryptography by providing a one-way mathematical transformation of data. The primary purpose is to ensure data integrity and authenticity through the creation of a unique hash value for each input. Hash functions are crucial in password storage, digital signatures, and message authentication codes, enhancing security by preventing unauthorized alterations and aiding in quick data retrieval. Hash functions are used to transform data into a fixed-size code, ensuring data integrity.
2. Explain the role of a digital certificate in simple terms.
Ans:
A digital certificate is like a virtual ID card that verifies the identity of a user, system, or website. This mechanism forms the basis for secure online activities like e-commerce, online banking, and secure communication, fostering a safer digital environment by preventing unauthorized access, data tampering, and man-in-the-middle attacks.
3. In basic terms, what’s the difference between symmetric and asymmetric cryptography?
Ans:
| Feature | Symmetric Cryptography | Asymmetric Cryptography |
|---|---|---|
| Key Usage | Single key for both encryption and decryption (shared secret key) | Pair of keys – public key for encryption, private key for decryption |
| Key Distribution | Requires secure distribution of the shared key | Public keys can be openly distributed; private keys must be kept secret |
| Computational Complexity | Generally faster and more efficient | Slower compared to symmetric cryptography |
| Examples | DES, 3DES, AES, Blowfish | RSA, ECC, DSA |
4. How does a nonce enhance security in cryptographic protocols?
Ans:
A nonce, or special code used only once, adds extra security by preventing replay attacks. A nonce, or “number used once,” enhances security in cryptographic protocols by introducing a unique value for each session or transaction. Nonces are commonly used in protocols like TLS and IPsec to protect against both replay and certain types of cryptanalysis, contributing significantly to the overall security and integrity of communication over networks.
5. Briefly describe the purpose of the Diffie-Hellman key exchange.
Ans:
- Diffie-Hellman lets two parties securely create a shared secret over an insecure channel. The key idea behind Diffie-Hellman is the use of modular arithmetic and the difficulty of solving the discrete logarithm problem.
- Each party generates a public-private key pair, and they exchange their public keys openly. Through a series of mathematical operations, both parties can independently compute the same shared secret using their private keys and the received public key.
6. What does it mean when we talk about “forward secrecy” in cryptography?
Ans:
Forward secrecy ensures that compromising a key doesn’t expose past communication, making systems more secure over time. Forward secrecy, also known as perfect forward secrecy (PFS), is a property in cryptography that ensures the confidentiality of past communications even if the long-term secret keys are compromised in the future. This is achieved by generating unique, ephemeral session keys for each session or communication instance.
7. Why is randomness important when generating cryptographic keys?
Ans:
Random keys are harder for attackers to predict, making our codes more secure. The importance of randomness in generating cryptographic keys lies in the fundamental principle of unpredictability. Cryptographic keys serve as the foundation for securing communication, data, and systems. If the process of generating keys lacks true randomness, it introduces vulnerabilities that adversaries could exploit.
8. Explain the concept of zero-knowledge proofs in simple terms.
Ans:
- Zero-knowledge proofs allow someone to prove they know a secret without revealing the actual secret. Imagine you want to prove to a friend that you have a magic word that opens a hidden door.
- Instead of telling them the magic word, you demonstrate its power by opening the door. Your friend sees that you have access, but they still don’t know the actual magic word.
9. What is quantum cryptography, and how does it differ from traditional cryptography?
Ans:
Traditional Cryptography: In classical systems, key distribution is a critical challenge. Keys need to be securely exchanged between parties, and the security often relies on the difficulty of problems like factoring large numbers (used in RSA) or solving discrete logarithms (used in Diffie-Hellman).
Quantum Cryptography: Quantum key distribution (QKD) allows two parties to generate a shared secret key with the help of quantum properties, such as the uncertainty principle and the no-cloning theorem. Any attempt to intercept the quantum states during key generation can be detected, providing a higher level of security.
10. Can you give a basic explanation of the birthday paradox in relation to cryptography?
Ans:
The birthday paradox warns us that collisions (two different inputs producing the same hash) can happen more easily than we might expect due to the limited space of possible hash values. The birthday paradox refers to the counterintuitive probability that in a surprisingly small group of people, there is a relatively high likelihood that two individuals share the same birthday. This phenomenon arises from the fact that there are many possible pairs of people in a group, and the probability of a shared birthday increases faster than one might expect.
11. What is cryptography, and why do we use it?
Ans:
Cryptography is a way to secure information by turning it into a secret code, preventing unauthorized access or changes.The primary goals of cryptography are confidentiality, integrity, authenticity, and non-repudiation
- Confidentiality: Cryptography helps in keeping information confidential by encrypting it. Encryption involves the use of algorithms to convert plain text into ciphertext, making it unreadable without the appropriate key.
- Integrity: Cryptographic techniques are used to ensure the integrity of data, meaning that any unauthorized changes or alterations to the data can be detected. This is often achieved through the use of hash functions and digital signatures.
- Authenticity: Cryptography enables the verification of the origin or source of a message or piece of data. Digital signatures and message authentication codes (MACs) are common tools for ensuring the authenticity of information.
12. What’s the difference between a secret key and a public key?
Ans:
Secret Key (Symmetric Key):
- Usage: A secret key, also known as a symmetric key, is used for both encryption and decryption of data. The same key is used for both processes.
- Key Distribution: The challenge with secret keys is secure key distribution. Since the same key is used for both encryption and decryption, both parties involved in communication must possess the key and keep it secret from others.
Public Key (Asymmetric Key):
- Usage: Public key cryptography uses a pair of keys: a public key and a private key. The public key is used for encryption, while the private key is used for decryption. Data encrypted with the public key can only be decrypted with the corresponding private key.
- Key Distribution: The public key can be freely distributed to anyone, while the private key must be kept secret. This eliminates the need for secure key exchange between parties.
13. What does a hash function do?
Ans:
It takes information and turns it into a fixed-size code to check if the data remains intact. Here are the key properties and functions of hash functions:
- Deterministic: A hash function is deterministic, meaning that the same input will always produce the same hash output.
- Fixed Output Size: Regardless of the size or length of the input data, a hash function produces a fixed-size output. For example, the SHA-256 (Secure Hash Algorithm 256-bit) hash function always produces a 256-bit hash value.
- Efficient Computation: Hash functions are designed to be computationally efficient, allowing for quick computation of the hash value.
14. Why do we need digital signatures in cryptography?
Ans:
Digital signatures ensure that messages or files are genuine and haven’t been tampered with.
- Authentication: Digital signatures provide a means to verify the origin or identity of the sender of a message or document. By using a private key to create a digital signature, the sender provides proof that they are the legitimate owner of the private key associated with a public key used for verification.
- Integrity: Digital signatures ensure the integrity of the signed content. If the signed data is modified or tampered with in any way, the digital signature will no longer be valid, providing a clear indication that the data has been altered.
15. What are the key principles of the Agile software development methodology?
Ans:
The Agile methodology emphasizes iterative and incremental development, collaboration between cross-functional teams, customer feedback, and the ability to respond to change. It values individuals and interactions over processes and tools, working software over comprehensive documentation, and customer collaboration over contract negotiation.
16. Can you explain a man-in-the-middle attack in simple terms?
Ans:
- It’s like someone secretly listening to and possibly changing your messages without you knowing. The two communicating parties might believe they are talking directly to each other, but the attacker is in the middle, secretly controlling or monitoring the conversation.
- To protect against man-in-the-middle attacks, secure communication protocols, encryption, and authentication mechanisms are commonly used. These measures help ensure that even if someone intercepts the communication, they can’t understand or modify the information being exchanged.
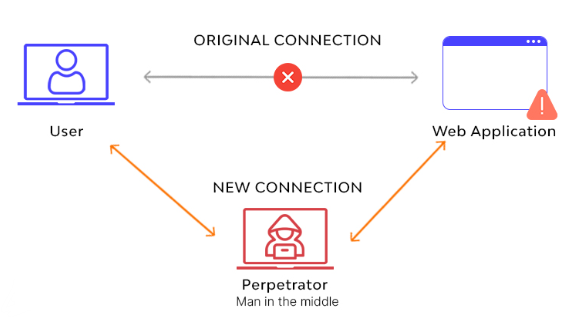
17. What do we mean by confidentiality and integrity in simple words?
Ans:
- Confidentiality: This means keeping information private and ensuring that only authorized people have access to it. Imagine you have a secret, and confidentiality is like making sure only the people you trust know about it.
- Integrity: This refers to the accuracy and trustworthiness of information. It’s like making sure that your message doesn’t get changed or tampered with when you send it.
18. Why is randomness important in cryptography?
Ans:
Randomness helps make sure our secret codes are really hard to guess or crack. Randomness plays a crucial role in cryptography for several reasons
- Key Generation: Cryptographic algorithms often rely on the generation of secret keys. If these keys are predictable, an attacker might be able to guess or deduce them.
- Initialization Vectors (IVs): In certain encryption algorithms, such as those using block ciphers in modes like CBC (Cipher Block Chaining), an initialization vector is used to introduce an element of randomness into the encryption process.
- Nonces: Nonces (number used once) are unique values that are often used to ensure the freshness of cryptographic operations. For example, in preventing replay attacks, a unique nonce is used for each session or transaction.
19. What’s a rainbow table, and why should we be cautious about it?
Ans:
A rainbow table is a cheat sheet used by hackers to guess passwords. We use tricks to make their cheat sheet less effective. A rainbow table is a precomputed table of hash values for every possible combination of input values (such as passwords) for a given hash function. The purpose of a rainbow table is to accelerate the process of reverse engineering hashed passwords. Instead of computing the hash values on-the-fly during a password attack
20. What’s the purpose of a nonce, and why is it useful?
Ans:
A nonce, which stands for “number used once,” is a random or unique value that is used only once in a cryptographic communication or protocol. The purpose of a nonce is to add an element of randomness and uniqueness to various cryptographic operations, and its usefulness stems from several key security considerations:
- Preventing Replay Attacks
- Enhancing Cryptographic Security Protocols
- Unique Initialization Vectors (IVs)
- Mitigating Deterministic Behavior
21. What is the primary goal of cryptography?
Ans:
The primary goal of cryptography is to secure communication and protect data from unauthorized access or manipulation. Cryptography encompasses a set of techniques and methods that enable secure communication in the presence of adversaries or potential threats. The main objectives of cryptography include:
- Confidentiality
- Integrity
- Authentication
- Non-repudiation
- Key Management
22. Differentiate between public key and privat
Ans:
Nature:
- Public Key: This key is shared openly and can be distributed to anyone. It is used for encryption and verifying digital signatures.
- Private Key: This key is kept secret and should only be known to the owner. It is used for decryption and generating digital signatures.
Function:
- Public Key: Used for encrypting data or verifying digital signatures. It cannot be used to decrypt data or generate digital signatures.
- Private Key: Used for decrypting data that was encrypted with the corresponding public key and for generating digital signatures. It should be kept confidential.
23. Define a hash function.
Ans:
A hash function transforms input data into a fixed-size string of characters, creating a hash value. A hash function is a mathematical function that takes an input (or “message”) and produces a fixed-size string of characters, which is typically a hexadecimal number. The output, often called the hash value or hash code, is unique to the input data.
24. Why is a digital signature essential in cryptography?
Ans:
A digital signature is essential in cryptography for several reasons, primarily related to ensuring the authenticity, integrity, and non-repudiation of digital messages or transactions. Here are key reasons why digital signatures play a crucial role.
- Authentication
- Integrity
- Non-Repudiation
- Data Integrity Across Networks
- Legal and Regulatory Compliance
- Secure Transactions
25. How is Cryptography used in various applications?
Ans:
Cryptography is used in various applications and systems, including:
- Secure Communication: Cryptography ensures that communication over insecure channels (such as the internet) remains confidential and secure.
- Data Protection: It is used to secure sensitive data, such as personal information, financial transactions, and corporate data.
- Authentication: Cryptographic methods help in verifying the identity of users and entities in online transactions and systems.
26. Describe a man-in-the-middle attack briefly.
Ans:
A man-in-the-middle (MitM) attack is a type of cyberattack where an unauthorized third party intercepts and potentially alters the communication between two parties without their knowledge. In a man-in-the-middle attack, the attacker secretly relays and may manipulate the communication between two parties who believe they are directly communicating with each other.
27. Differentiate confidentiality and integrity in cryptography.
Ans:
Confidentiality: Ensures information is not disclosed to unauthorized individuals.
Integrity: Ensures information is not tampered with by unauthorized parties.
28. What role does randomness play in cryptography?
Ans:
Randomness plays a crucial role in cryptography, contributing to the security and effectiveness of cryptographic systems. Here are several key roles that randomness plays in various cryptographic applications:
- Initialization Vectors (IVs)
- Nonce Generation
- Salting in Hash Functions
- Randomized Algorithms
- Key Exchange Protocols
- Random Number Generators (RNGs):
- Digital Signatures
29. Define a rainbow table.
Ans:
A rainbow table is a precomputed table of hash values for every possible plaintext input for a given hash function. The purpose of a rainbow table is to accelerate the process of reverse engineering hashed passwords. Instead of computing the hash values on-the-fly during a password attack, an attacker can consult the precomputed table to quickly look up the hash and find the corresponding original input
30. Briefly explain the purpose of a nonce.
Ans:
A nonce is a unique value used once in cryptographic protocols to prevent replay attacks.
31. What is the difference between a block cipher and a stream cipher?
Ans:
- Block Cipher: Operates on fixed-size blocks of data. Encrypts and decrypts data in blocks.
- Stream Cipher: Operates on a continuous stream of data. Encrypts and decrypts data one bit or byte at a time.
32. Explain the concept of a nonce in cryptographic protocols?
Ans:
A nonce (number used once) is a random or unique value used only for a specific transaction or session to prevent replay attacks.
33. What is the role of a salt in password hashing?
Ans:
A salt is a random value added to each password before hashing, enhancing security by preventing attackers from using precomputed tables (like rainbow tables) for multiple passwords.
34. Describe the difference between a digital certificate and a digital signature.
Ans:
- Digital Certificate: A digital certificate is an electronic document used to verify the identity of a user, system, or website.
- Digital Signature: A digital signature is a cryptographic technique that verifies the authenticity and integrity of a message or document.
35. What is the purpose of the Diffie-Hellman key exchange algorithm?
Ans:
Diffie-Hellman allows two parties to generate a shared secret over an insecure channel, facilitating secure communication without the need to exchange secret keys.
36. How does a brute-force attack differ from a dictionary attack in password cracking?
Ans:
- Brute-Force Attack: Tries all possible combinations systematically. Resource-intensive but effective against weak passwords.
- Dictionary Attack: Uses a predefined list of potential passwords. Faster but relies on users choosing common passwords.
37. Explain the concept of forward secrecy in cryptographic systems.
Ans:
Forward secrecy ensures that compromising a long-term secret key doesn’t compromise past session keys, enhancing security over time.
38. What is the birthday paradox, and how does it relate to cryptographic hashing?
Ans:
The birthday paradox states that in a set of 23 people, there is a 50% chance that two share the same birthday. In cryptography, it emphasizes the potential for collision (two different inputs producing the same hash) in hash functions due to the finite size of output space.
39. How does the concept of zero-knowledge proofs enhance security in cryptographic protocols?
Ans:
Zero-knowledge proofs allow one party to prove knowledge of a secret without revealing the secret itself, ensuring security without unnecessary disclosure.
40. What is quantum cryptography, and how does it differ from classical cryptography?
Ans:
Quantum cryptography leverages principles of quantum mechanics to secure communication, offering potentially unbreakable encryption through quantum key distribution.
41. Differentiate between black-box testing and white-box testing.
Ans:
Black-box testing: It involves testing a system without knowledge of its internal workings, focusing on inputs and outputs.
White-box testing: On the other hand, examines the internal structure and logic of a system, including code paths and branches.
42. Explain the concept of quantum key distribution (QKD) and its application in secure communication.
Ans:
QKD uses quantum mechanics to secure key exchange between parties.It provides a way to detect eavesdropping attempts.
43. What is the role of a firewall in network security, and how does it differ from an Intrusion Detection System (IDS)?
Ans:
A firewall is a network security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules. An IDS, on the other hand, detects and responds to suspicious activities or potential security threats. Firewalls focus on traffic control, while IDS focuses on monitoring and analysis.
44. Describe the concept of cryptanalysis resistance in the context of cryptographic algorithms.
Ans:
- Cryptanalysis resistance means the algorithm should resist attempts to break it, even with significant computational resources.
- It emphasizes the importance of algorithm strength against various attacks
45. Explain the concept of quantum superposition and how it can impact certain cryptographic algorithms.
Ans:
- Quantum superposition allows quantum bits (qubits) to exist in multiple states simultaneously.
- Algorithms like Shor’s can exploit superposition to efficiently factor large numbers, threatening some cryptographic systems.
46. What is the role of a commitment scheme in cryptographic protocols?
Ans:
A commitment scheme is integral in cryptographic protocols as it enables a party to commit to a specific value without disclosing it prematurely. This is essential in scenarios where the order of information disclosure is critical. By using commitment schemes, parties can ensure the integrity of their interactions and prevent cheating by binding themselves to a particular value before revealing it.
47. How does the concept of indistinguishability obfuscation contribute to cryptographic security?
Ans:
- Indistinguishability obfuscation plays a crucial role in cryptographic security by ensuring that two functionally equivalent programs are indistinguishable.
- This concept adds an additional layer of security by obscuring the internal workings of cryptographic schemes.
- It prevents attackers from gaining insights into the underlying algorithms, contributing to the robustness of cryptographic protocols.
48. Describe the purpose of a zero-knowledge succinct non-interactive argument of knowledge (zk-SNARK) in blockchain technology.
Ans:
zk-SNARKs allow for the verification of certain computations without revealing the details.They contribute to privacy and efficiency in blockchain transactions.
49. What is the significance of the birthday problem in hash function analysis?
Ans:
The birthday problem highlights the likelihood of collisions in hash functions.It emphasizes the importance of choosing hash functions with a large output space.
50. Explain the concept of quantum-resistant cryptography and its importance in the post-quantum era.
Ans:
- Quantum-resistant cryptography aims to provide security even in the presence of quantum computers.
- It is essential for maintaining confidentiality and integrity in the post-quantum era.
51. How does the concept of key whitening enhance the security of block ciphers?
Ans:
- Key whitening involves combining the secret key with additional randomness before encryption.
- It adds an extra layer of security against certain attacks, including related-key attacks.
52. Describe the purpose of the padding scheme in RSA encryption.
Ans:
The padding scheme in RSA ensures that plaintext has a specific format before encryption. This safeguards against certain cryptographic attacks and plays a crucial role in maintaining the security of the RSA algorithm.
53. What is the importance of the Goldwasser-Micali cryptosystem in the context of probabilistic encryption?
Ans:
- The Goldwasser-Micali cryptosystem is pivotal in probabilistic encryption, offering semantic security.
- Its design conceals information about the encrypted message, even in the presence of an adversary, enhancing the robustness of encrypted communication.
54. Explain the concept of multiparty computation and its applications in secure computation.
Ans:
- Multiparty computation enables multiple parties to jointly compute a function over their inputs while keeping those inputs private.
- It is applied in scenarios where secure collaboration on computations is needed without compromising the confidentiality of individual input data.
55. How does the concept of trapdoor functions contribute to the security of public-key cryptography?
Ans:
Trapdoor functions allow easy computation in one direction but are hard in the reverse direction without additional information. They form the basis of many public-key cryptographic systems.
56. Describe the purpose of a commitment trapdoor in commitment schemes
Ans:
- A commitment trap door allows the party making the commitment to reveal the committed value later.
- It adds flexibility to commitment schemes in certain cryptographic protocols.
57. What role does the Fiat-Shamir heuristic play in turning certain interactive proofs into non-interactive ones?
Ans:
The Fiat-Shamir heuristic serves the purpose of transforming certain interactive zero-knowledge proofs into non-interactive forms. By doing so, it simplifies the implementation of zero-knowledge proofs in cryptographic protocols, allowing for more practical and efficient verification processes.
58. Explain the concept of chosen key attacks and their implications for cryptographic security.
Ans:
- Chosen key attacks involve attackers deliberately selecting cryptographic keys, posing a significant threat to system security.
- These attacks can lead to the compromise of systems, underscoring the critical importance of robust key management practices in cryptographic protocols.
59. What is the role of a commitment ceremony in cryptographic key generation processes?
Ans:
In cryptographic key generation processes, a commitment ceremony involves multiple parties contributing to the creation of cryptographic keys. This collaborative approach adds an additional layer of security, ensuring that the keys are generated with the collective trust and verification of involved parties.
60. Describe the role of quantum entanglement in quantum key distribution (QKD) protocols.
Ans:
- Quantum entanglement plays a pivotal role in Quantum Key Distribution (QKD) protocols. It enables the establishment of a shared secret key with a high level of security.
- Quantum entanglement ensures that any attempts at eavesdropping during the key exchange process are detectable, preserving the integrity of the communication.
61. What is the concept of a side-channel attack in cryptography?
Ans:
Side-channel attacks exploit information leakage during cryptographic processes, such as power consumption or timing, to unveil the secret key. These attacks operate on unintended information channels, emphasizing the need for comprehensive security measures that go beyond algorithmic robustness to safeguard cryptographic systems.
62. Explain the concept of homomorphic encryption.
Ans:
Homomorphic encryption is a cryptographic technique that allows computations to be performed on encrypted data without decrypting it first. In other words, it enables operations to be performed on encrypted data, and the result of those operations is an encrypted value that, when decrypted, corresponds to the result of the operations on the original plaintext data.
- Partially Homomorphic Encryption
- Somewhat Homomorphic Encryption
- Fully Homomorphic Encryption (FHE)
63. What is the significance of the “chosen plaintext attack” in cryptanalysis?
Ans:
In a chosen plaintext attack, the attacker can choose and encrypt specific messages, aiming to analyze patterns and discover the encryption key.
64. Describe the purpose of a cryptographic salt in password storage.
Ans:
A cryptographic salt adds random data to passwords before hashing, preventing attackers from using precomputed tables like rainbow tables.
65. What is the role of a digital timestamp in cryptographic applications?
Ans:
A digital timestamp provides proof that data existed at a specific point in time, enhancing non-repudiation. This timestamp is typically generated and signed by a trusted third party known as a timestamping authority. The primary roles and significance of digital timestamps in cryptographic applications include:
- Proof of Existence
- Data Integrity
- Non-Repudiation:
- Authentication and Authorization:
- Secure Communications
66. Explain the concept of post-quantum cryptography.
Ans:
- Post-quantum cryptography involves the design and implementation of cryptographic algorithms that can withstand attacks from quantum computers.
- Given the potential threat quantum computers pose to traditional cryptographic systems, post-quantum cryptography aims to develop algorithms that remain secure even in the era of quantum computing.
67. What is a chosen ciphertext attack, and how does it differ from a chosen plaintext attack?
Ans:
- In a chosen ciphertext attack, the adversary can select and decrypt specific ciphertexts, intending to gain insights into the decryption process.
- This is different from a chosen plaintext attack where the attacker can choose specific plaintexts and observe the corresponding ciphertexts.
- Chosen ciphertext attacks are particularly potent in scenarios where the adversary can manipulate and analyze decrypted messages.
68. What is the role of a Hardware Security Module (HSM) in cryptography?
Ans:
Hardware Security Modules (HSMs) play a crucial role in cryptography by providing secure storage and management of cryptographic keys. They act as dedicated, tamper-resistant hardware devices, safeguarding keys from unauthorized access and ensuring their secure use in cryptographic operations.
69. Explain the concept of perfect forward secrecy.
Ans:
Hardware Security Modules (HSMs) play a crucial role in cryptography by providing secure storage and management of cryptographic keys. They act as dedicated, tamper-resistant hardware devices, safeguarding keys from unauthorized access and ensuring their secure use in cryptographic operations.
70. What are quantum-resistant algorithms, and why are they important in cryptography?
Ans:
- Quantum-resistant algorithms are cryptographic algorithms specifically designed to resist attacks from quantum computers.
- As quantum computers have the potential to break current cryptographic systems using algorithms like Shor’s algorithm, the development and adoption of quantum-resistant algorithms are crucial to maintaining the security of digital communication in the face of quantum advancements.
71. Define the concept of steganography in the context of information security.
Ans:
- Steganography involves concealing information within non-secret data, making it challenging to detect.
- This technique focuses on hiding the existence of the information itself, contrasting with cryptography that primarily focuses on protecting the content through encryption.
72. What is the role of elliptic curve cryptography (ECC) in modern cryptographic systems?
Ans:
Elliptic Curve Cryptography (ECC) plays a vital role in modern cryptographic systems by providing strong security for key exchange and digital signatures. ECC achieves this security with shorter key lengths compared to other algorithms, contributing to more efficient and resource-friendly cryptographic operations.
73. Explain the term “cryptographic agility” in the context of security protocols.
Ans:
Cryptographic agility refers to a system’s capability to adapt and switch cryptographic algorithms dynamically. This adaptability is crucial for maintaining security in the face of evolving threats, allowing systems to update cryptographic mechanisms without compromising overall security.
74. What is the significance of the meet-in-the-middle attack in cryptanalysis?
Ans:
- The meet-in-the-middle attack is significant in cryptanalysis as it involves calculating an intermediate result and working backward, increasing efficiency in certain attack scenarios.
- Understanding and defending against this type of attack is essential for designing secure cryptographic systems.
75. What role does the Fiat-Shamir heuristic play in the field of cryptographic protocols?
Ans:
The Fiat-Shamir heuristic is instrumental in cryptographic protocols as it transforms certain interactive proof systems into non-interactive ones. This transformation enhances the efficiency of authentication protocols by eliminating the need for direct interaction during the proof process.
76. Explain the concept of key stretching in password-based key derivation.
Ans:
Key stretching involves intentionally slowing down the process of deriving cryptographic keys from passwords. This deliberate slowing mitigates the risk of brute-force attacks, where an attacker systematically tests all possible password combinations.
77. What is the importance of non-repudiation in cryptographic applications?
Ans:
- Non-repudiation is crucial in cryptographic applications as it ensures that a party cannot deny their involvement in a communication or transaction.
- This property adds accountability and trust, especially in legal or contractual contexts.
78. Describe the purpose of a digital envelope in secure communication.
Ans:
A digital envelope serves the purpose of securing both the message and its key during transmission. It ensures confidentiality by encapsulating the message and key, protecting the content from unauthorized access.
79. What is the difference between substitution-permutation networks (SPN) and Feistel networks in block cipher design?
Ans:
Substitution-Permutation Networks (SPN) and Feistel networks are structures in block cipher design. SPN employs substitutions and permutations in parallel, while Feistel networks use a series of rounds with substitutions and permutations, providing different approaches to achieving block cipher functionality.
80. Explain the concept of Shamir’s Secret Sharing and its application.
Ans:
- Shamir’s Secret Sharing divides a secret into shares distributed among participants. To reconstruct the original secret, a threshold of shares is required.
- This method is applied in multi-party scenarios to enhance security by preventing a single point of failure in secret management.
81. What are the primary goals of cryptography?
Ans:
- Confidentiality: Ensuring that the information is only accessible to those who have the authorized access.
- Integrity: Verifying that the information has not been altered during transmission or storage.
- Authentication: Confirming the identity of the parties involved in communication.
- Non-repudiation: Ensuring that a party cannot deny the authenticity of a message.
82. What is the difference between homomorphic encryption and fully homomorphic encryption?
Ans:
Homomorphic encryption allows computations to be performed on encrypted data without decrypting it. Fully homomorphic encryption extends this concept to support both addition and multiplication operations on encrypted data.
83. Explain the concept of side-channel attacks. Provide an example.
Ans:
Side-channel attacks exploit information leaked during the execution of cryptographic algorithms, such as timing, power consumption, or electromagnetic radiation. An example is a timing attack where an attacker analyzes the time taken by a cryptographic operation to gain insights into the key being used.
84. What is the role of a salt in password hashing?
Ans:
A salt is a random value unique to each password. It is concatenated with the password before hashing, adding randomness and preventing attackers from using precomputed tables (rainbow tables) to crack passwords.
85. Can you explain the concept of a “commitment scheme”?
Ans:
- A commitment scheme is a cryptographic protocol that allows a party to commit to a chosen value while keeping it hidden from others.
- The committed value can later be revealed, and the commitment should be binding, meaning the party cannot change the committed value.
86. What is the difference between elliptic curve cryptography and RSA?
Ans:
Elliptic curve cryptography (ECC) and RSA are both asymmetric cryptographic algorithms, but ECC provides the same level of security with shorter key lengths compared to RSA, making it more efficient in terms of computation and bandwidth.
87. What is the significance of the “one-time pad” in cryptography?
Ans:
The one-time pad is a theoretically unbreakable symmetric encryption scheme where a random key, as long as the message, is used only once. If implemented correctly, it provides perfect secrecy, as the ciphertext reveals no information about the plaintext.
88. What is the concept of “commit-and-prove” in zero-knowledge proofs?
Ans:
- Commit-and-prove is a technique in zero-knowledge proofs where a prover commits to a certain value without revealing it, then later proves knowledge of the committed value.
- This allows the prover to demonstrate knowledge without disclosing the actual information during the commitment phase.
89. What is the difference between authentication and authorization?
Ans:
Authentication is the process of verifying the identity of a user, system, or entity, while authorization is the process of determining what actions or resources a user, system, or entity is allowed to access or perform.
90. Explain the concept of a Turing machine and its relevance to theoretical computer science.
Ans:
A Turing machine is an abstract mathematical model of computation that defines the fundamental limits of what can be computed algorithmically. It consists of an infinite tape, a tape head, and a set of rules for transitioning between states. It helps in understanding the concept of computability and decidability.

