
Introduction :-
Linux working framework, which is a clone of UNIX, is created to deal with various clients with performing multiple tasks highlights. This implies than beyond what one client can work in this working simultaneously when the PC is appended to an organization or Internet. The far off clients can associate with the PC that contains the Linux working framework through SSH and work on the framework. It is vital to keep up with security when different clients work in a similar working framework simultaneously.
Many inherent security highlights exist in the Linux working framework that can be utilized when neighborhood or remote access is conceded from various clients. The Linux clients need to comprehend the idea of document authorizations and the responsibility for record to give security at the record framework level. How the Linux clients can see and change the consents, and the responsibility for record and envelopes is displayed in this article.
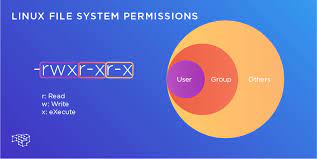
Kinds of Users :-
Three kinds of clients exist in the Linux working framework, which is referenced beneath.
- Proprietor:
The client who makes the record or envelope is the proprietor of that document or organizer, and the proprietor can allow different sorts of clients to get to that record and envelope. It is meant by ‘u’.
Bunch:
Every client can have a place with a specific gathering in Linux. Thus, when a client makes a record or organizer, then, at that point, different individuals from the gathering where the client should be can get to the document or envelope. At the point when numerous clients work on a specific envelope, then, at that point, it is smarter to make a gathering with those clients to get to that organizer appropriately. It is indicated by ‘g’.
Others/All:
It shows any client who isn’t the proprietor of a specific record or organizer and doesn’t have a place with the document or envelope proprietor’s gathering. Assuming the proprietor of the record or organizer allows any admittance to other people, then, at that point, any clients can do that specific access as it were. ‘o’ is utilized to indicate different clients, and ‘a’ is utilized to signify all clients.
Permission Types:
Three consent types exist in the Linux framework, which is referenced underneath.
Peruse:
This consent is utilized to peruse any record or envelope as it were. It is signified by ‘r’ when it is characterized by character, and it is meant by 4 when it is characterized by a number.
Compose:
This authorization is utilized to compose, annex, or supersede any document or organizer. It is meant by ‘w’ when it is characterized by the person, and it is meant by 2 when it is characterized by the number. Assuming the client needs to compose consent to a record, however he/she has not to compose authorization on the envelope where the document is found, then, at that point, the client can change the substance of the document just, yet he/she will not ready to rename, move or erase the document.
Execute:
This authorization is utilized to execute any document as it were. It is indicated by ‘x’ when it is characterized by the person, and it is signified by 1 when it is characterized by the number.
Despite the fact that there are now a ton of good security highlights incorporated into Linux-based frameworks, one vital potential weakness can exist when neighborhood access is allowed – – that is document authorization based issues coming about because of a client not allotting the right consents to records and indexes. So in view of the requirement for appropriate consents, I will go over the ways of allotting authorizations and show you a few models where change might be essential.
Fundamental File Permissions :-
Authorization Groups
Each record and catalog has three client based authorization gatherings:
Proprietor – The Owner authorizations apply just the proprietor of the document or registry, they won’t affect the activities of different clients.
Bunch – The Group authorizations apply just to the gathering that has been appointed to the document or index, they won’t impact the activities of different clients.
All clients – The All Users authorizations apply to any remaining clients on the framework, this is the consent bunch that you need to watch the most.
Authorization Types
Each record or catalog has three fundamental authorization types:
Peruse – The Read authorization alludes to a client’s capacity to peruse the substance of the record.
compose – The Write authorizations allude to a client’s capacity to compose or adjust a record or registry.
execute – The Execute authorization influences a client’s capacity to execute a record or view the substance of an index.
Seeing the Permissions
You can see the consents by checking the record or index authorizations in your cherished GUI File Manager (which I won’t cover here) or by auditing the result of the “ls – l” order while in the terminal and keeping in mind that working in the registry which contains the document or envelope.
The authorization in the order line is shown as: _rwxrwxrwx 1 owner:group
Client freedoms/Permissions
- The main person that I set apart with a highlight is the exceptional authorization banner that can shift.
- The accompanying arrangement of three characters (rwx) is for the proprietor authorizations.
- The second arrangement of three characters (rwx) is for the Group authorizations.
- The third arrangement of three characters (rwx) is for the All Users authorizations.
Following that gathering since the whole number/number shows the quantity of hardlinks to the record.
The last piece is the Owner and Group task organized as Owner:Group.
Adjusting the Permissions
When in the order line, the authorizations are altered by utilizing the order chmod. You can appoint the authorizations unequivocally or by involving a parallel reference as portrayed underneath.
Expressly Defining Permissions
To explicity characterize consents you should reference the Permission Group and Permission Types.
The Permission Groups utilized are:
u – Owner
g – Group
o – Others
a – All clients
The potential Assignment Operators are + (in addition to) and – (short); these are utilized to advise the framework whether to add or eliminate the particular authorizations.
The Permission Types that are utilized are:
r – Read
w – Write
x – Execute
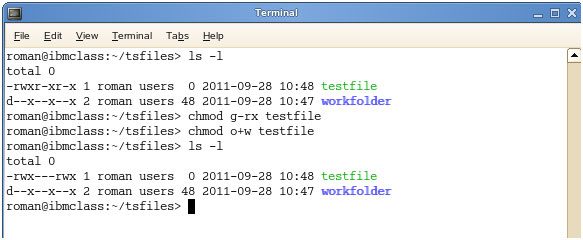
So for a model, lets say I have a document named file1 that right now has the authorizations set to _rw_rw_rw, which implies that the proprietor, gathering and all clients have perused and compose consent. Presently we need to eliminate the read and compose authorizations from the all clients bunch.
- To make this adjustment you would summon the order: chmod a-rw file1
- To add the authorizations above you would summon the order: chmod a+rw file1
As may be obvious, to allow those authorizations you would change the less person to an or more to add those consents.
Utilizing Binary References To Set Permissions
- Since you comprehend the consents gatherings and types this one should feel normal. To set the consent utilizing paired references you should initially comprehend that the info is finished by entering three whole numbers/numbers.
- An example authorization string would be chmod 640 file1, which implies that the proprietor has perused and compose consents, the gathering has understood authorizations, and any remaining client reserve no options to the document.
- The main number addresses the Owner authorization; the second addresses the Group consents; and the last number addresses the authorizations for any remaining clients. The numbers are a parallel portrayal of the rwx string.
- r = 4
- w = 2
- x = 1
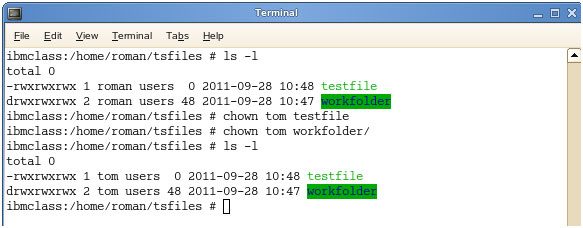
- I have made a few references to Owners and Groups above, however have not yet let you know how to relegate or change the Owner and Group doled out to a record or catalog.
- You utilize the chown order to change proprietor and gathering tasks, the grammar is simplechown owner:group filename, so to change the proprietor of file1 to user1 and the gathering to family you would enter chown user1:family file1.
- _ – no extraordinary authorizations
- d – registry
- l–The record or catalog is an emblematic connection
- s – This showed the setuid/setgid consents. This isn’t set shown in the exceptional consent a piece of the authorizations show, yet is addressed as a s in the read part of the proprietor or gathering consents
- t – This shows the tacky piece authorizations. This isn’t set shown in the extraordinary authorization a piece of the consents show, however is addressed as a t in the executable part of the all clients consents
- The setuid/setguid authorizations are utilized to advise the framework to run an executable as the proprietor with the proprietor’s consents.
- Be cautious utilizing setuid/setgid bits in authorizations. Assuming that you inaccurately allot consents to a document possessed by root with the setuid/setgid bit set, then, at that point, you can open your framework to interruption.
- You can allot the setuid/setgid bit by expressly characterizing authorizations. The person for the setuid/setguid bit is s.
- So set the setuid/setguid bit on file2.sh you would give the order chmod g+s file2.sh.
- The tacky piece can be extremely helpful in shared climate since when it has been relegated to the authorizations on an index it sets it so just record proprietor can rename or erase the said document.
- You can appoint the tacky piece by expressly characterizing authorizations. The person for the tacky piece is t.
- To set the tacky piece on a catalog named dir1 you would give the order chmod +t dir1.
- Bootloader arrangement documents If you choose to carry out secret phrase to boot explicit working frameworks then you will need to eliminate read and compose consents from the setup record from all clients however root. To do you can change the authorizations of the record to 700.
- Framework and daemon design documents It is vital to limit privileges to framework and daemon setup records to confine clients from altering the substance, it may not be fitting to confine read authorizations, yet confining compose consents is an unquestionable requirement. In these cases it could be ideal to change the freedoms to 644.
- Firewall scripts – It may not forever be important to impede all clients from perusing the firewall record, however it is fitting to limit the clients from keeping in touch with the document. For this situation the firewall script is controlled by the root client naturally on boot, so any remaining clients need no privileges, so you can allocate the 700 consents.
You add the numbers to get the number/number addressing the authorizations you wish to set. You should incorporate the double consents for every one of the three authorization gatherings.
So to set a record to consents on file1 to peruse _rwxr_____, you would enter chmod 740 file1.
Proprietors and Groups
Progressed Permissions
The extraordinary authorizations banner can be set apart with any of the accompanying:
Setuid/Setgid Special Permissions
Tacky Bit Special Permissions –
At the point when Permissions Are Important :
To certain clients of Mac-or Windows-based PCs you don’t contemplate authorizations, however those conditions don’t zero in so forcefully on client put together privileges with respect to records except if you are in a professional workplace. Be that as it may, presently you are running a Linux-based framework and authorization based security is streamlined and can be handily used to confine access however you see fit.
So I will show you a few archives and envelopes that you need to zero in on and show you how the ideal consents ought to be set.
home registries The clients’ home indexes are significant in light of the fact that you don’t need different clients to have the option to see and change the records in one more client’s archives of work area. To cure this you will need the index to have the drwx______ (700) consents, so lets say we need to authorize the right authorizations on the client user1’s home catalog that should be possible by giving the order chmod 700/home/user1.
Features :-
Conclusion :-
Every file, directory, and other system objects in Linux are assigned an owner and a group.This is generally referred to as file permissions in Linux. To set permissions and manage ownership, we will use the following commands: chmod : change file permissions. chown : change file owner. Thus we conclude the article with all the Linux File Permissions Files , Data Structures and includes more.





