
HCL is a worldwide technology firm specializing in IT services and solutions. Renowned for its innovative strategies, HCL enables businesses to transform through digital technologies, software development, and consulting. With an emphasis on client collaboration, the company offers customized solutions that enhance efficiency and foster growth across diverse industries. Committed to sustainability, HCL also focuses on creating a positive impact on society and the environment.
1. Explain the idea of polymorphism in item-orientated programming.
Ans:
Polymorphism in object-oriented programming allows objects to take on multiple forms, providing a single interface for different types. The main types are compile-time polymorphism (method overloading), where multiple methods share the same name but differ in parameters, and runtime polymorphism (method overriding), which enables a subclass to provide a specific implementation of a method already defined in its superclass.
2. How does rubbish series paintings in Java?
Ans:
- Garbage series in Java is an automated reminiscence control manner that identifies and discards gadgets now not in use to loose up reminiscence space. The Java Virtual Machine (JVM) uses algorithms like mark-and-sweep or generational rubbish series to music item references.
- When gadgets emerge as unreachable (i.e., no references factor), the rubbish collector marks them for cleanup. This prevents reminiscence leaks by reclaiming reminiscence from unused gadgets.
- Developers don’t want to explicitly manipulate reminiscence because the JVM handles deallocation, even though wrong reminiscence use can nonetheless result in overall performance problems like common rubbish series cycles.
3. What is enter-output (I/O) in C++?
Ans:
In C++, enter/output (I/O) refers back to the manner of studying statistics from enter devices (just like the keyboard) and writing statistics to output devices (just like the screen). The preferred library presents streams to address I/O operations: cin for enter, court for output, and colour for mistake handling. These streams permit formatted and unformatted statistics switches between this system and the I/O devices. For example, the usage of cin >> reads enter from the user, even as court
4. Explain the principles of OOPS.
Ans:
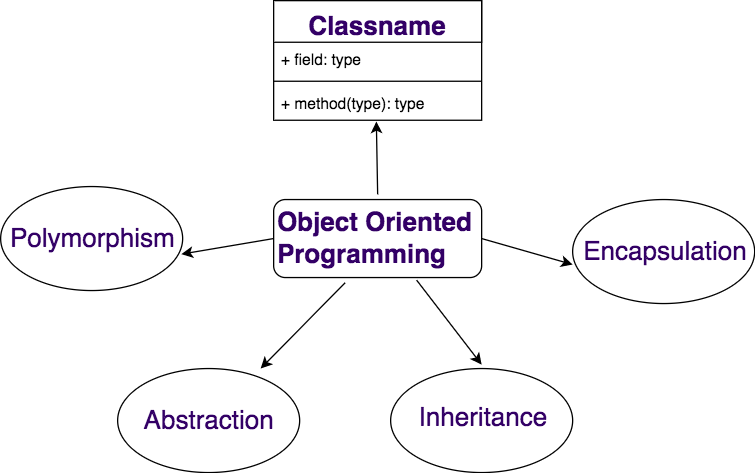
Object-Oriented Programming (OOP) is primarily based totally on 4 major principles: Encapsulation, Inheritance, Polymorphism, and Abstraction. Encapsulation binds information and techniques into an unmarried unit (magnificence) and restricts direct admission to a few components. Inheritance lets in a category to derive houses and conduct from any other magnificence, permitting code reuse. Polymorphism allows one interface to symbolize more than one type, permitting techniques to act otherwise primarily based totally on the item that invokes them.
5. What are the distinctive cloud computing carrier models?
Ans:
- Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
- IaaS provides virtualized computing assets over the Internet, including servers, storage, and networking, permitting customers to install and control their packages.
- PaaS provides a platform consisting of hardware and software program tools, including improvement frameworks, to build, test, and install packages without dealing with the underlying infrastructure.
6. Explain the principles of Static Keyword in Java.
Ans:
- The static keyword in Java is used to outline magnificence-degree variables and techniques that belong to the magnificence itself instead of to times of the magnificence.
- A static variable is shared throughout all times of the magnificence, which means adjustments made to the static variable in a single example are pondered.
- A static approach may not develop an item of magnificence and may involve static variables and different static techniques.
7. What is the cause of the Domain Name System (DNS)?
Ans:
The Domain Name System (DNS) is a hierarchical gadget that interprets human-readable area names (like www.example.com) into IP addresses (like 192.168.1.1), which computer systems can utilize to discover and speak with every different over the Internet. DNS acts as the “phonebook” of the Internet, making it simpler for customers to get admission to websites without considering complicated numerical IP addresses.
8. Explain the difference between a HashSet and a TreeSet.
Ans:
| Feature | HashSet | TreeSet |
|---|---|---|
| Implementation | Based on a hash table | Based on a red-black tree |
| Ordering | No guaranteed order | Maintains sorted order |
| Performance | Faster for add, remove, contains (O(1) average) | Slower (O(log n) for add, remove, contains) |
| Null Values | Allows one null value | Does not allow null values |
| Traversal | Unordered traversal | Ordered traversal (ascending) |
9. What is a number one key? Explain with an example.
Ans:
A number one key is a unique identifier for a file in a relational database desk. It guarantees that every row within the desk may be uniquely recognized through the cost within the number one key column, preventing reproduction entries and maintaining information integrity. A number one key must incorporate specific values and can’t incorporate null ones. For example, in a “Customers” desk, the customer_id column may be the number one key because every consumer has a unique ID.
10. What is a neighbourhood and worldwide variable in Python?
Ans:
In Python, a neighbourhood variable is declared interior a characteristic and is available handiest inside that characteristic’s scope. Once the characteristic exits, the neighbourhood variable’s cost is lost. On the other hand, a worldwidotherle is described out of doors of any characteristic and may be accessed through any characteristic withinsidegram. If we need to alter a worldwide variable interior a characteristic, we have to claim it using the worldwide keyword explicitly; otherwise, Python treats it as a neighbourhood variable.
11. What is cloud computing? How is it beneficial nowadays?
Ans:
- Cloud computing is the transport of computing services, storage, processing power, and software over the Internet, or “the cloud.”
- Instead of proudly owning and coping with bodily servers or facts centres, companies and people can access scalable assets on call from cloud carriers like AWS, Microsoft Azure, or Google Cloud.
- Cloud computing is beneficial nowadays as it permits flexibility, price savings, scalability, and far-off entry. Companies can speedily scale their IT infrastructure primarily based on a call for and pay most effectively for what they use.
12. Explain the idea of approach overriding in Java.
Ans:
- Method overriding in Java happens when a subclass presents a particular implementation of a technique already described in its superclass.
- The overridden approach inside the subclass ought to have an identical name, go-back type, and parameters because the approach withinside the figure class.
- Method overriding is a crucial part of runtime polymorphism. It permits a subclass to inherit a technique from a superclass but alters its behaviour.
- For example, if a superclass has a technique draw(), one-of-a-kind subclasses like Circle or Rectangle can override this approach to put their unique drawing model in force.
13. What is the position of the ‘very last’ keyword in Java?
Ans:
The last keyword in Java may be used to outline constants, save approach overriding, and inheritance. A previous variable can not be changed after initialization, making it a constant. An earlier approach can not be overridden by using any subclass, ensuring its implementation stays constant throughout subclasses. Additionally, affirming a category as last prevents it from being subclassed, which is beneficial whilst growing immutable or safety-touchy instructions, including String in Java.
14. What are the differences between shallow and deep cloning in object cloning?
Ans:
In item cloning, a shallow reproduction creates a brand new item; however, it most effectively copies the references of nested items, now no longer the items themselves. This way, adjustments to the nested items within the reproduction may affect the unique item. In contrast, a deep reproduction creates a brand-new item and recursively copies all nested items, ensuring that adjustments to the reproduction no longer affect the unique item.
15. What are the constraints in SQL?
Ans:
- Constraints in SQL are policies enforced on information in a database to ensure information integrity, accuracy, and reliability.
- Common constraints encompass PRIMARY KEY, which guarantees a column has particular values and no nulls; FOREIGN KEY, which guarantees referential integrity among tables; and UNIQUE, which prevents reproduction of values in a column.
- The NOT NULL constraint guarantees that a column can not have null values, while CHECK permits outlining situations at the information that ought to be met.
16. What is the number of variations between C and C++?
Ans:
- C is a procedural programming language, while C++ is an object-orientated language. C++ extends C by introducing standards like instructions and objects.
- C makes a speciality of capabilities and step-via way of means of-step procedures. At the same time, C++ emphasizes information encapsulation, inheritance, and polymorphism, making it extra appropriate for large, complicated software program systems.
- C++ supports both procedural and object-orientated paradigms, presenting extra flexibility. It additionally gives capabilities like characteristic overloading, operator overloading, and templates, which might be absent in C.
17. What are threads, and explain their types?
Ans:
Threads are the smallest execution unit inside the process, permitting much more than one responsibility to be finished simultaneously inside an identical method. There are fundamental varieties of threads: User-degree threads are controlled via way of means of person-area libraries and are scheduled via way of means of the person without kernel intervention, making them speedy, however confined in having access to gadget resources.
18. What are distinct varieties of joins?
Ans:
- Joins in SQL are used to mix rows from or extra tables primarily based totally on an associated column. The not unusual place varieties of joins are INNER JOIN, which returns facts with matching values in each tabletable.
- LEFT JOIN (or LEFT OUTER JOIN) returns all facts from the left desk and matches facts from the proper desk, filling in NULLs for non-matching rows. RIGHT JOIN does the identical, however, in reverse, focusing on the proper desk.
- CROSS JOIN produces a Cartesian product, pairing each row from the primary desk with each from the second.
19. Describe the distinction between a stack and a queue.
Ans:
- A stack is a record shape that follows the Last In, First Out (LIFO) principle, which means the final detail brought is the primary one removed. Operations like push (add) and pop (remove) are carried out on the pinnacle of the stack.
- On the other hand, a queue follows the First In, First Out (FIFO) principle, which means the primary detail brought is the primary one removed. Operations like enqueue (add) and dequeue (remove) are carried out at contrary ends. Queues are generally utilized in scheduling algorithms, mission management, and breadth-first search.
20. What are ACID Properties in DBMS?
Ans:
A Database Management System’s (DBMS) ACID homes ensure reliable transaction processing. Atomicity guarantees that every operation inside a transaction is completed; if one operation fails, the whole transaction is rolled back. Database integrity is maintained through consistency, which ensures that a transaction moves the database from one valid kingdom to another. Isolation guarantees that simultaneously executing transactions no longer intrude with each other.
21. What is the distinction between abstraction and encapsulation in Java?
Ans:
Abstraction specializes in hiding the complexity by displaying most effective the vital capabilities of an object, leaving out the implementation information. It enables defining a clean interface for objects, like using summary training or interfaces. Encapsulation, on the other hand, binds the records (attributes) and the methods (functions) right into an unmarried unit (class) and restricts direct get entry to the records with the aid of making variables non-public and offering public methods.
22. Explain the benefits of a Relational Database Management System (RDBMS).
Ans:
- Relational Database Management Systems (RDBMS) prepare information into tables (relations), permitting customers to store, control, and retrieve information without problems using SQL (Structured Query Language).
- Key benefits encompass information integrity via regulations like number one and overseas keys, ensuring information accuracy and consistency.
- RDBMS additionally helps ACID (Atomicity, Consistency, Isolation, Durability) properties, presenting dependable transaction management. Normalization minimizes information redundancy, optimizing garage efficiency.
23. What is the distinction among compiler, interpreter, and assembler?
Ans:
- A compiler interprets the complete high-level programming code (like C or Java) into system code (binary) at once, producing an executable report before running the program.
- An interpreter interprets and executes code line by line without developing an intermediate system code report, making debugging simpler but execution slower (e.g., Python).
- An assembler converts meeting language code, which is a low-stage language, into system code immediately into system code.
24. Discuss the idea of software programs trying out and exceptional styles of trying out techniques.
Ans:
Software compares a machine or its additives to discover errors, gaps, or lacking necessities. There are numerous styles of trying out techniques, which include unit trying out, which examines character additives or modules in isolation; integration trying out, which examines how exceptional modules paintings together; machine trying out, which evaluates the entire and included machine; and consumer recognition trying out (UAT), in which real customers take a look at the software program to affirm if it meets their needs.
25. What distinguishes soft, corporation, and difficult real-time structures?
Ans:
- In a difficult real-time machine, lacking a cut-off date results in catastrophic failure, and the machine should meet all closing dates to feature correctly (e.g., plane control).
- A corporation’s real-time machine can tolerate occasional ignored closing dates; however, such misses degrade the machine’s overall performance, even though they no longer lead to finish failure (e.g., banking structures).
- Soft real-time structures can manage common cut-off date misses, and while this influences overall performance, the machine maintains its normal features (e.g., multimedia streaming).
26. What is an interface in OOP, and the way is it exceptional from a category?
Ans:
An interface is a settlement that defines strategies that a category should enforce. However, it no longer offers any implementation itself. It represents a blueprint for classes dealing with implementations and data manipulation. Unlike a couple of inheritances with classes, a category can enforce a couple of interfaces, taking into account extra flexibility in item design.
27. What is a constructor in OOP?
Ans:
In a category, a constructor is a special approach frequently used when creating anything elegant. It initializes the item, regularly placing the preliminary values of attributes or acting on setup tasks. Constructors may be parameterized or default, depending on whether arguments are surpassed at some stage in item creation. In languages like Java or C++, constructors are described with equal calls because of their elegance and can not have a go-back type.
28. What is the distinction between a summary elegance and an interface?
Ans:
- A summary elegance is a category that can not be instantiated independently and may comprise each summary strategy (strat without mentation). It permits shared conduct for subclasses even as leaving a few methods to be described via way of means of them.
- On the other hand, another cons technique is declarations (in maximum languages) and no longer offmplementatoffersWhile a category can amplify the summary elegance, it can put in force more than one interface.
- This difference permits interfaces to offer greater flexibility in layout by helping more than one inheritance of conduct.
29. What is the ‘this’ keyword in OOP?
Ans:
- This keyword refers back to the cutting-edge example of a category. It is used inside a category’s technique to differentiate among elegance attributes and technique parameters once they have the same call.
- For example, in a constructor, this. Call refers to the elegance’s attribute, while the call should talk to the technique’s argument.
- This keyword is likewise used to name different constructors inside equal elegance or by skipping the cutting-edge item as an argument.
30. What is the difference between composition and inheritance in OOP?
Ans:
Inheritance establishes an “is-a” courting among an infant and a discerning elegance, permitting the kid elegance to inherit conduct from the discerning. Composition, on the other hand, represents a “has-a” courting, wherein a category consists of references to different gadgets, and those gadgets cope with unique functionalities. Composition is regularly desired over inheritance as it ends in greater flexible, loosely coupled designs.
31. What is the position of get right of entry to modifiers in OOP?
Ans:
Access modifiers (e.g., public, non-public, protected) outline the visibility and accessibility of classes, strategies, and attributes. Public contributors are reachable from any part of the program, non-public contributors are restrained to the defining magnificence, and guarded contributors may be accessed via the magnificence and its subclasses. These modifiers put in force encapsulation, assisting in managing how the inner kingdom of an item is uncovered or hidden.
32. What distinguishes early and past due binding in OOP?
Ans:
- Early binding, additionally referred to as static binding, takes place at compile time. The approach to be used is decided primarily based on the magnificence of the item reference.
- In contrast, past-due binding (dynamic binding) occurs at runtime, wherein the approach to be accomplished is decided primarily based totally on the real item, which is no longer the reference type.
- Early binding is quicker but much less bendy because the approach is locked in for compilation.
- Late binding, frequently related to polymorphism, permits greater dynamic and bendy behaviour because it defers the choice of which approach to name until runtime.
33. What is a singleton magnificence, and why is it used?
Ans:
- A singleton magnificence restricts the instantiation of a category to an unmarried item, ensuring that the simplest example exists during the program.
- This is beneficial in situations where a single, centralized item is wanted to coordinate actions with a configuration supervisor or logging system.
- A singleton is normally carried out by making the constructor non-public and imparting a static approach to getting the example.
34. What is more than one inheritance, and does it exist in all OOP languages?
Ans:
Multiple inheritance allows a class to inherit from multiple classes, enabling greater code reuse but potentially causing ambiguity when methods or attributes with the same name are inherited from different sources. Languages like C++ support multiple inheritance directly, while others like Java do not, instead offering interfaces to achieve similar behavior. A key issue in multiple inheritance is the “diamond problem,” where a class inherits the same method from multiple paths.
35. What is the Open/Closed Principle in OOP?
Ans:
The Open/Closed Principle (OCP) is one of the SOLID ideas in OOP that states software program entities (like lessons, modules, or functions) have to be “open for extension, however closed for modification. This ensures balance while allowing for future improvements by requiring a category’s behaviour to be expandable (via inheritance or interfaces) without changing its current code. By adhering to OCP, code will become easier to preserve and adapt by introducing insects or requiring the most important rewrites, which is vital in evolving software program systems.
36. What is an affiliation, aggregation, and composition in OOP?
Ans:
- These are unique relationships among items. The association is a widespread dating wherein lessons are linked, but every elegance can exist independently (e.g., a “Teacher” and a “Student”).
- Aggregation is a specialized shape of affiliation wherein one elegance is part of any other; however can nevertheless exist independently (e.g., a “Department” containing “Teachers”).
- Composition is a sturdy shape of aggregation wherein the contained items can’t exist independently of the container (e.g., a “House” and its “Rooms”). Composition implies ownership, even as aggregation does now no longer.
37. What is the Liskov Substitution Principle (LSP)?
Ans:
- The Liskov Substitution Principle, part of the SOLID ideas, states that items of a superclass must be replaceable with items of a subclass without affecting the program’s correctness.
- In other words, if elegance B is a subclass of sophistication A, then items of kind A must be capable of being replaced by items of kind B without changing the program’s conduct.
- This guarantees that a subclass complements the figure elegance’s conduct without breaking the contract, offering dependable inheritance and polymorphism.
38. What is the Dependency Inversion Principle (DIP)?
Ans:
- The Dependency Inversion Principle, like any other SOLID precept, states that high-degree modules can no longer rely on low-degree modules. Instead, they must each rely on abstractions (interfaces or summary lessons).
- This precept enables less coupling among a device’s unique components, making it easier to preserve and extend.
- By relying on abstractions as opposed to concrete implementations, modifications in lower-degree additives no longer ripple via higher-degree modules, offering flexibility and modularity in device design.
39. What are the recommendations and references in C++?
Ans:
Pointers and references are each used to consult reminiscence locations; however, they behave differently. A pointer holds the reminiscence dealing with a variable and may be reassigned to factor to distinct variables throughout the runtime. It additionally helps pointer arithmetic. Alternatively, a reference is an alias for a variable and must be initialized while declared; it can not be reassigned. References provide a more secure opportunity for recommendations as they can not be null, lowering the probabilities of reminiscence-associated errors.
40. What is feature overloading in C++?
Ans:
Function overloading permits a couple of capabilities inside the equal scope to have the equal call, however, distinct parameters (through number, type, or each). This is an instance of compile-time polymorphism. It permits the equal feature call to carry out particular duties relying on the arguments surpassed to it. Overloading improves code clarity and reusability by logically grouping associated operations below an unmarried feature call.
41. What is the distinction between stack and heap reminiscence in C++?
Ans:
Stack reminiscence is used for static reminiscence allocation, in which variables are saved in a Last In, First Out (LIFO) structure, and reminiscence is mechanically controlled. At the same time, a feature is known as an exit. On the other hand, heap reminiscence is used for dynamic reminiscence allocation, in which reminiscence is allotted and deallocated manually through the programmer using new and delete. Stack reminiscence is quicker and mechanically controlled; however, restrained in size.
42. What are digital capabilities in C++?
Ans:
- Virtual capabilities allow polymorphism in C++ by permitting derived lessons to override a base elegance technique.
- When a way is marked as digital inside the base elegance, and a pointer or connection with the bottom elegance calls the technique, the derived elegance’s technique model may be executed (if overridden).
- This conduct is called runtime (or dynamic) polymorphism. Virtual capabilities permit flexible and extensible designs, but they include a mild overall performance fee because digital tables (vtables) are used to define the feature at runtime.
43. What is the distinction between structure and sophistication in C++?
Ans:
- In C++, the number one distinction between struct and sophistication is the default get right of entry to control. In a structure, individuals are public through default; at the same time, in elegance, individuals are personal through default.
- Both structure and sophistication may have member capabilities, constructors, and destructors and might guide inheritance and polymorphism.
- While struct is historically used for undeniable facts structures (much like C), elegance is normally used for completely encapsulated object-orientated designs.
44. What is the RAII (Resource Acquisition Is Initialization) idea in C++?
Ans:
RAII is a programming idiom in C++ wherein assets (like reminiscence, document handles, or community connections) are tied to the life of items. When an item is created, it acquires essential assets; whilst it’s far destroyed, it releases them. This is generally performed through constructors and destructors. RAII guarantees that assets are well controlled and freed, even in the presence of exceptions, making aid control more secure and more predictable. This idea is crucial to clever hints, which routinely control reminiscence.
45. What is a clever pointer in C++?
Ans:
Smart hints in C++ are template instructions inside the Standard Template Library (STL) that control dynamic reminiscence. They assist in making sure the right deallocation of reminiscence whilst it’s far now not needed, addressing reminiscence leaks. Std::unique_ptr, std::shared_ptr, and std::weak_ptr are the most often utilized clever hints._ptr guarantees different possession of an aid, shared_ptr permits a couple of items to percentage possession, and weak_ptr is a non-proudly owning connection with an item controlled through shared_ptr.
46. What is a digital destructor, and why is it needed?
Ans:
- A digital destructor guarantees that the destructors of derived instructions are also known, whilst an item is deleted through a pointer to the bottom.
- Without a digital destructor, the bottom elegance destructor is invoked, which could cause incomplete aid cleanup in derived instructions, inflicting memory leaks or undefined behaviour.
- In polymorphic elegance hierarchies, wherein items are accessed through base elegance hints, marking the destructor as digital guarantees that the whole item’s destruction chain (along with derived instructions) is completed correctly.
47. What is an inline characteristic in C++?
Ans:
- An inline characteristic is a characteristic that the compiler tries to extend in place, changing the characteristic name with the real characteristic code to lessen overhead.
- This can cause quicker execution as it removes the overhead of a characteristic name, mainly for small, regularly known functions. To claim an inline characteristic, operate the inline keyword.
- However, inlining is best a suggestion to the compiler, and it can choose to disregard it if the characteristic is too complex. Excessive inlining can increase code size (code bloat), so it must be used judiciously.
48. What is a natural digital feature in C++?
Ans:
A natural digital feature is declared in a base magnificence that has no implementation and needs to be overridden with the aid of using any derived magnificence. It is said with the help of assigning zero wa ithininsidere declaration (e.g., digital void draw() = zero;). A magnificence containing, as a minimum, one natural digital feature is referred to as a summary magnificencea and can not be instantiated directly. Pure digital capabilities outline a not unusual interface for derived instructions, imposing that derived instructions offer particular behaviour.
49. What are buddy capabilities in C++?
Ans:
A buddy feature in C++ is a feature that isn’t always a member of a category but has been admittedits personal and guarded members. It is said with the aid of using the buddy keyword in the magnificence. Friend capabilities may be beneficial for operations that require admission to a couple of instructions’ records; however, they do need to be a member of any particular magnificence now no longer. However, they spoil the precept of encapsulation, as they disclose inner magnificence details.
50. What is the const keyword in C++, and how is it used?
Ans:
- The const keyword in C++ is used to claim constants, making the price of variables or the end result of a feature immutable. When applied to a variable, it prevents change after initialization.
- When used with a member feature, it guarantees that it doesn’t adjust any member variables. The keyword can also be used with pointers, making sure that either the pointer or the records it factors to stay constant.
- Using const well complements code reliability by stopping unintentional changes and permitting optimizations through the compiler.
51. What are templates in C++?
Ans:
- Templates in C++ permit capabilities and instructions to function with customary sorts, allowing code reuse for one-of-a-kind record sorts.
- A template defines a blueprint for developing capabilities or instructions with placeholders for record sorts, which can be exact at the time of usage.
- For example, a template feature can carry out identical operations on integers, floats, or custom sorts without overloading it for every kind.
- Templates are effective for developing kind-safe, customary libraries, including the Standard Template Library (STL). However, they could result in large code sizes because code is instantiated for every record type used.
52. What is a namespace in C++?
Ans:
A namespace is a declarative location that provides variables, capabilities, and instructions with scope. It prevents naming conflicts by permitting identical names for use in one-of-a-kind contexts without ambiguity. For example, libraries can outline a feature called print(); however, putting them in one-of-a-kind namespaces avoids collisions. The std namespace, for example, incorporates all the same old C++ library capabilities. The use of namespace directives may be used to simplify code.
53. What distinguishes new and malloc() in C++?
Ans:
The new operator in C++ is used for dynamic reminiscence allocation, much like malloc() in C, however, with a few key differences. new calls the constructor of a category to initialize an item and returns a pointer of an appropriate type, whilst malloc() best allocates uncooked reminiscence and calls for casting to the proper type. Memory allotted with new needs to be launched with delete, whilst reminiscence allotted with malloc() needs to be freed with unfastened(). New is greater type-secure and helps item initialization, making it premier in C++ for item creation.
54. What is the distinction between delete and delete[] in C++?
Ans:
- The delete operator is used to unfastened reminiscence allotted for an unmarried item, whilst delete[] is used to unfastened reminiscence allotted for an array of gadgets.
- Please apply the proper shape of delete to avoid undefined behaviour. For instance, the use of delete on an array best calls the destructor of the primary element, which can also reason for reminiscence leaks or flawed useful resource deallocation.
- New with delete and new with delete are always compatible using an appropriate shape guarantees the right cleanup and stops reminiscence-associated bugs.
55. What is a digital desk (v-desk) in C++?
Ans:
- A digital desk (v-desk) is a mechanism utilized by the compiler to implement dynamic (runtime) polymorphism in C++. When a category has digital features, the compiler creates a desk containing suggestions for the digital features of elegance.
- Each item of elegance carries a pointer to the v-desk. While a digital feature is known, an appropriate feature is selected at runtime by searching the v-desk.
- This permits C++ to assist feature overriding and guarantees that the maximum derived elegance’s approach is known while using base elegance references or suggestions.
56. What is the mutable keyword in C++?
Ans:
The mutable keyword in C++ permits a member variable of a category to be changed even though it’s far part of an item declared as const. Normally, const gadgets save any amendment in their member variables. Nonetheless, the inner characteristics of a mutable member can be altered. This is beneficial when wanting to extrude a particular variable, like a cache or counter, without violating the const correctness of the elegance. Mutable is generally used sparingly, as overusing it may undermine the const idea in C++.
57. What are flow semantics in C++11, and why are they important?
Ans:
Move semantics, delivered in C++11, optimize overall performance through moving sources (like reminiscence) from one item to another instead of copying them. This is executed using rvalue references (&&), which permit sources from transient gadgets to be “moved” in place of a copy. A flow constructor and flow undertaking operator are used to take possession of those sources, making the authentic item’s sources unusable.
58. What distinguishes throw, strive, and trap in C++?
Ans:
- In C++, the strive, throw, and trap blocks are used for exception management. A strive block includes code that would throw an exception, and a throw assertion is used to signify the incidence of a top-notch condition (like runtime mistakes).
- When an exception is thrown, the manipulation is transferred to the matching trap block, which handles the exception. The trap block needs to be shaped according to the kind of exception thrown.
- This mechanism allows for smooth mistake management without cluttering the code with more than one test and permits separating regular code from mistake logic.
59. What is the Rule of Three in C++?
Ans:
- The Rule of Three states that if a category desires to outline a destructor, a replica constructor, or a replica project operator, it probably desires to outline all 3.
- This is because the training that controls sources like dynamic memory, report handles, or community connections needs a proper cleanup to prevent troubles like memory leaks or double deletions.
- If any of those 3 capabilities are user-described, the alternative’s default behaviours might not be as expected. The Rule of Three guarantees the right to aid control while copying or assigning objects.
60. What are lambda expressions in C++11, and how are they used?
Ans:
Lambda expressions, added in C++11, are nameless capabilities that may be described in an area without claiming a separate function. They are beneficial for passing brief code snippets as parameters, mainly in algorithms or callbacks. The syntax is [capture](parameters) -> return_type. Captures permit admission to variables outside the lambda scope, both via means of cost and means of reference. Lambdas are broadly utilized in present-day C++ for practical programming tasks, including iterating over boxes or managing occasions concisely and readably.
61. What is the distinction among std::vector and std::array in C++?
Ans:
std::vector is a dynamic array that could develop or reduce in length throughout the runtime, whilst std::array is a fixed-length array whose length is thought to bring together time. Vectors offer dynamic resizing abilities through computerized reminiscence reallocation as needed, making them extra flexible. Arrays, conversely, are quicker to access factors, considering that their length is fixed and no reminiscence control is required. std::vector is a part of the Standard Template Library (STL), and its length may be changed with strategies like push_back().
62. What is a hanging pointer in C, and how can it be avoided?
Ans:
- A dangling pointer arises whilst a pointer nonetheless references a reminiscence region that has already been freed or deallocated. Using a hanging pointer can result in undefined behaviour, including crashes or statistics corruption.
- This can appear if reminiscence is freed using free(); however, the pointer isn’t always nullified or reassigned.
- To keep away from dangling pointers, constantly set a pointer to NULL after releasing reminiscence and avoid getting access to freed reminiscence locations.
63. Explain the distinction between an array and a related list.
Ans:
An array is a contiguous block of reminiscence wherein factors are saved in adjoining reminiscence places and accessed using indices. Arrays permit for regular time admissionto to factors; however, resizing them is steeply-priced given that they require reminiscence reallocation. Linked lists, however, are collections of nodes wherein every node incorporates facts and a pointer to the following node.
64. What is an impasse in working systems, and how can it be prevented?
Ans:
- An impasse is a scenario in a working gadget wherein a series of hard and fast approaches become stuck, each looking ahead to sources held through others, ensuing in an indefinite wait.
- Deadlock prevention strategies ensure that at least one of the important situations for impasse (mutual exclusion, maintain and wait, no preemption, round wait) is no longer maintained.
- For example, the “Banker’s Algorithm” prevents impasse by ensuring that gadget sources are allotted safely.
65. What is a binary search, and when can it be applied?
Ans:
Binary seek is an effective set of rules used to discover the location of a goal price inside taken care of array or list. It works repeatedly, dividing the quest area in half, and evaluating the center detail to the goal. If the goal is smaller than the centre detail, the quest is maintained inside the left half; otherwise, it proceeds to the proper half. Binary seek has a time complexity of O(log n), making it much quicker than linear look for huge datasets. It is simplest relevant whilst the dataset is taken care of and calls for logarithmic time for seek operations.
66. What is normalization in databases, and why is it important?
Ans:
Normalization is a database layout that organizes tables to reduce redundancy and dependency by dividing a database into extra tables and defining relationships among them. The major intention of normalization is to make certain that every piece of fact is saved in a single vicinity, which reduces fact anomalies and improves facts’ integrity. The normalization manner includes attaining numerous regular forms (1NF, 2NF, 3NF, and BCNF), every addressing unique forms of redundancy.
67. What is the distinction between TCP and UDP in networking?
Ans:
- TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are each shipping layer protocol; however, their functionality fluctuates.
- TCP is a connection-orientated protocol that guarantees reliable, ordered, and error-checked data transport among packages, making it appropriate for use in packages like Internet surfing and email.
- On the other hand, UDP is a connectionless protocol that sends facts without organizing a connection, leading to quicker transmission. However, it does not ensure transport, order, or integrity.
68. What is dynamic programming, and the way is it special from recursion?
Ans:
- Dynamic programming is an optimization method used to remedy complicated troubles by breaking them down into less difficult subproblems, fixing every subproblem most effectively once, and storing the end result for future reference (memoization).
- It is particularly beneficial for troubles with overlapping subproblems and excellent substructure properties, such as the Fibonacci sequence, knapsack problem, or shortest route in a graph.
- On the other hand, recursion is a method in which a characteristic calls itself to remedy smaller times of the identical problem.
69. What is a system vs. a thread in working systems?
Ans:
A system is an impartial software in execution with its personal reminiscence space, code, facts, and device resources. It is remoted from different approaches, which means adjustments in a single system no longer affect others. A thread, in contrast, is the smallest unit of execution inside a system and stocks the system’s resources, which include reminiscence. Multithreading permits more than one thread to run simultaneously inside an unmarried system, mainly advancing overall performance for parallel tasks.
70. What is the reason for indexing in databases?
Ans:
Indexing is a database optimization method that improves the velocity of facts retrieval operations by developing a facts structure (index) that permits quicker searching, sorting, and filtering of records. An index is largely a research desk offering a shortcut for accessing rows in a database without scanning the whole desk. Indexes may be created on one or extra columns and are beneficial for queries regarding SELECT, WHERE, or JOIN clauses.
71. Explain the idea of paging in reminiscence control.
Ans:
- Paging is a reminiscence control scheme that removes the want for contiguous allocation of bodily reminiscence by dividing reminiscence into fixed-length pages (inside the digital deal with area) and corresponding frames (inside the bodily reminiscence).
- When an application wishes to get the right of entry to a web page that isn’t always presently in bodily reminiscence, a web page fault occurs, and the working machine masses the specified web page into reminiscence, probably swapping out different pages.
72. What is a hash desk, and the way does it work?
Ans:
A hash desk is the shape of a record that maps keys to values with the use of a hash function, which transforms the important thing into an index that corresponds to a bucket in which the price is stored, searches, inserts, and deletions, hash tables provide average-case constant time complexity (O(1)). However, collisions can arise whilst multiple keys hash to the identical index, and special techniques like chaining (related lists) or open addressing (probing) are used to solve them.
73. What is a kernel, and what are its functions?
Ans:
- The kernel is the middle element of a working machine, answerable for handling machine sources consisting of CPU, reminiscence, and devices.
- It operates in a privileged mode with complete access to the hardware and affords critical offerings like system control, memory control, and tool control.
- The kernel handles machine calls, which can be requests from user-area applications for hardware sources or offerings. There are forms of kernels: monolithic (in which the whole thing runs in an unmarried deal with a
74. What is the distinction between a system and a thread?
Ans:
A system is an unbiased unit of execution with its own reminiscence area, sources, and code; at the same time, a thread is a smaller unit inside a system that stocks identical reminiscence and sources. Processes are remoted and require greater overhead to create and manage, while threads are lighter and faster, as they percentage records with different threads within the identical system. While methods offer greater safety and stability (one system crashing no longer affects others), threads permit higher concurrency and are perfect for parallel tasks.
75. What is an impasse, and how can it be prevented in a running gadget?
Ans:
Deadlock occurs when two or more processes are stuck waiting for resources held by each other, leading to indefinite waiting. Four conditions must be met for deadlock to happen: mutual exclusion, hold and wait, no preemption, and circular wait. To prevent deadlock, at least one of these conditions must be broken, such as avoiding circular wait by enforcing a strict resource allocation order or using strategies like the Banker’s Algorithm for safe resource allocation.
76. What is digital reminiscence, and the way does it work?
Ans:
- Virtual reminiscence is a reminiscence control method that offers the phantasm of a large, non-stop reminiscence area to methods by using each bodily RAM and disk area.
- The running gadget divides packages into smaller chunks known as pages and loads only the essential pages into RAM, while the rest are saved on disk.
- This allows the gadget to run larger or greater packages simultaneously than the bodily memory might otherwise allow. Virtual reminiscence is carried out via strategies like paging and segmentation.
77. What is context switching in a running gadget?
Ans:
- Context switching allows multitasking in running structures by loading the country of each thread or system while saving the country of the one that is now jogging.
- During a context switch, the CPU switches from one system to another by saving the modern system’s registers, software counter, and other country information and restoring the country of the following system.
- Context switching is crucial for time-sharing structures; however, it incurs an overhead because the CPU spends time switching instead of executing real tasks.
78. What are gadget calls, and how are they utilized in running structures?
Ans:
- The interface between consumer-area packages and the running gadget kernel.
- Permitting packages to request offerings from the kernel, which include record operations.
- System management.
- Community communication.
When a gadget name is made, this system switches from consumer to kernel mode, allowing the running gadget to execute the request safely. Common gadget calls encompass open, read, write, fork, and exec.
79. What is paging, and the way does it vary from segmentation?
Ans:
Paging is a reminiscence control scheme in which the working machine divides reminiscence into fixed-length blocks referred to as pages and the bodily reminiscence into frames of equal length. This lets in non-contiguous reminiscence allocation and avoids fragmentation issues. The working machine continues a web page desk to map logical addresses to bodily addresses. Segmentation, conversely, divides reminiscence into variable-sized segments primarily based totally on logical divisions in software, like code, data, or stack segments.
80. What are interrupts, and how are they treated through the working machine?
Ans:
- Interrupts are indicators despatched to the processor through hardware or software that indicate an occasion, like a key press or a timer expiration, wishes to be instantaneously interested.
- When an interrupt occurs, the processor quickly stops its modern task, saves its country, and jumps to a unique habitual called the interrupt carrier habitual (ISR) to address the occasion.
- After an ISR completes, the CPU resumes the previous task. The operating system manages interrupts by prioritizing high-priority tasks and handling multiple interrupts systematically.
81. What is a scheduler in a working machine?
Ans:
A scheduler is a part of the working machine responsible for figuring out which procedure or thread needs to be carried out through the CPU. There are 3 varieties of scheduling: long-term (which selects tactics from the activity pool and hundreds them into reminiscence), short-term (which selects tactics from the geared-up queue for CPU execution), and medium-term (which handles tactics inside the suspended country).
82. What is beating in working systems, and in the way can it be averted?
Ans:
- Thrashing occurs when a working machine spends most of its time swapping pages inside and outside of memory rather than executing tactics, which leads to critically degraded performance.
- It usually occurs while the machine is overloaded with tactics that exceed the available bodily memory, inflicting excessive paging.
- Thrashing may be averted through higher web page substitute algorithms, growing bodily reminiscence, or decreasing the diploma of multiprogramming (the wide variety of tactics jogging concurrently).
83. What is the distinction between a Monolithic and a Microkernel structure?
Ans:
In a monolithic kernel, all essential OS services like file management and device drivers operate in kernel space, leading to higher performance but greater crash risk, as a failure can affect the entire OS. In contrast, a microkernel keeps only core services (such as inter-process communication and scheduling) in kernel space, while other services run in user space.
84. Explain the idea of a Real-Time Operating System (RTOS) and how it differs from a standard-reason OS.
Ans:
A Real-Time Operating System (RTOS) is designed to deal with real-time programs that require predictable and time-confined execution of obligations. RTOS ensures that vital commitments can be achieved within a deadline, making it best for structures like clinical devices, car controls, and commercial automation. In contrast, a standard-reason OS (like Linux or Windows) specializes in maximizing useful resource usage and throughput without strict ensures on execution time.
85. What is the distinction between symmetric and uneven multiprocessing (SMP vs AMP)?
Ans:
- Symmetric multiprocessing (SMP) is a structure in which all processors percentage the identical reminiscence and I/O resources, and every processor runs an example of the working device.
- In SMP, any processor can execute any task, supplying higher load balancing and scalability for standard-reason workloads.
- On the other hand, asymmetric multiprocessing (AMP) dedicates precise processors to certain obligations, with one processor normally performing as a grasp and others as slaves.
- AMP is utilized in structures with specialized workloads, where certain processors handle time-vital obligations while others handle standard commitments.
86. What is the scheduler’s role in multiprocessor devices compared to single-processor devices?
Ans:
In a multiprocessor device, the scheduler’s position is to assign obligations or threads to more than one processor simultaneously, optimizing for load balancing, minimizing rivalry for shared resources, and enhancing throughput. The complexity will increase because the scheduler must ensureneeds that threads jogging on exclusive processors get admission to shared reminiscence without inflicting race conditions.
87. What is NUMA (Non-Uniform Memory Access), and how does it affect running machine design?
Ans:
- NUMA is a reminiscence structure in multiprocessor structures in which every processor has its nearby reminiscence, and gaining access to nearby reminiscence is quicker than gaining access to reminiscence connected to different processors.
- NUMA contrasts with uniform reminiscence to enter (UMA), in which all reminiscence accesses take equal time.
- The OS ought to be NUMA-conscious to successfully manipulate memory and responsibilities, assigning techniques to processors that might be in the direction of the specified memory to lessen latency.
88. What is precedence inversion, and the way is it treated in real-time structures?
Ans:
Priority inversion happens in real-time structures while a lower-precedence venture holds an aid required with the help of using a higher-precedence venture, main to the higher-precedence venture being not directly blocked. This can result in ignored cut-off dates in essential real-time structures. A not unusual place to address precedence inversion is through inheritance, in which the lower-precedence venture quickly inherits the higher-precedence venture’s precedence until it releases the wished aid.
89. Explain the distinction between tough and tender real-time structures.
Ans:
In a tough real-time machine, lacking a cut-off date is considered catastrophic, as it can result in machine failure or risky consequences (e.g., aerospace manipulation or pacemaker structures). Every venture ought to be entirely inside a strict cut-off date, and the machine is designed to ensure this even below most load. In contrast, a tender real-time machine permits occasional cut-off date misses. While those misses degrade overall performance, they no longer motivate catastrophic failures (e.g., video streaming or online gaming).
90. What is the distinction between preemptive and cooperative multitasking?
Ans:
Preemptive multitasking permits the running machine to forcibly interrupt and transfer responsibilities to ensure every responsibility getter, whether or not a venture is prepared to yield. The OS scheduler determines when a venture needs to be interrupted, primarily based totally on priorities or time slices, making preemptive multitasking greater responsive in structures with a couple of applications. On the other hand, cooperative mothering is based on the responsibility to yield manipulation gain to the OS voluntarily.






