
Technical support interview questions typically assess a candidate’s problem-solving skills, technical knowledge, and customer service abilities. Interviewers may ask about specific technical issues, troubleshooting processes, and how candidates handle difficult customer interactions. It’s important for candidates to demonstrate their ability to communicate complex information clearly and to show empathy towards users.
1. Which operating systems familiar with?
Ans:
Many operating systems are available Windows, macOS, and Linux, each developed to have specific characteristics and applications. Windows is the most popular and used for enterprise businesses and individuals since it has an interface that suits them and allows them to keep their compatibility up to date. macOS is an Apple O.S. and is also very popular in creative jobs due to its design and also because of how it integrates with Apple hardware. Knowing at least two different O.S. platforms will enhance the skill set for troubleshooting and compatibility.
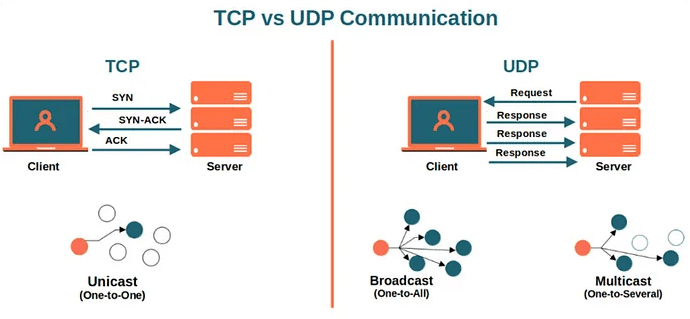
2. What’s the difference between TCP and UDP?
Ans:
TCP and U.D.P. are two of the key transport protocols over the Internet. TCP is a connection-oriented protocol with error checking and data retransmission, making it reliable but slower. On the other hand, U.D.P. is connectionless with minimal error checking; it is faster but less reliable. TCP is used for applications requiring accuracy, such as transferring files, whereas U.D.P. is used where speed is a parameter, such as video streaming. Knowing both protocols is needed in troubleshooting the network.
3. What is the O.S.I. model, and what are the layers?
Ans:
The O.S.I. model represents the view of network communications in seven layers. These have been classified into the categories Physical, Data Link, Network, Transport, Session, Presentation, and Application. Each layer offers specific functions, including data transfer, routing, and application interfacing, and helps standardize communication protocols. Isolating and troubleshooting problems on the network would be easier when required to focus on a specific layer.
4. How is a network connectivity problem diagnosed?
Ans:
- Troubleshooting network connectivity begins with checking the physical connection, be it a cable and/or network adapter.
- A further check of I.P. configurations followed by running commands such as ping or tracert may help to highlight network paths and connectivity to devices.
- A deeper analysis of DNS settings and firewall rules can sometimes indicate what is blocking internet access.
5. What is an I.P. address, and why is it important?
Ans:
- An I.P. address is a unique identifier assigned to each device on a network. It enables data communication between devices.
- I.P. addresses can be either IPv4 or IPv6. The larger the address pool, the more benefits an I.P. address provides.
- They are very important for routing data across the Internet and maintaining connectivity in local networks.
- Static I.P.s never change for fixed connections, while dynamic I.P.s change frequently for easier management.
6. Can DNS be explained, and how does it work?
Ans:
- DNS is short for Domain Name System, an addressing system that converts human-readable domain names such as www.example.com to I.P. addresses that a computer understands to locate a website.
- The way type a domain name first querying the resolver to find the I.P. address from a DNS server. This hierarchical system comprises root servers, TLD servers, and authoritative servers.
- The former ensures that requests are handled efficiently, while the latter solves the problem of repeated requests and maintains records across the Internet. DNS is very important for web accessibility.
7. Describe what a VPN is and its use.
Ans:
A VPN is a network connection that encrypts connection and masks I.P. address. It offers users a way of accessing private networks safely, such as resources that a company might have placed behind a firewall from remote locations. VPNs enhance privacy, intercept data theft, and open a gateway to region-restricted content. In short, VPNs have widely been used in business organizations for safety in communication and by individuals for privacy and overcoming geolocation constraints.
8. What is the difference between HTTP and HTTPS?
Ans:
| Feature | HTTP | HTTPS |
|---|---|---|
| Full Form | HyperText Transfer Protocol | HyperText Transfer Protocol Secure |
| Security | Not secure, data transmitted in plaintext | Secure, data encrypted using SSL/TLS |
| Port Number | 80 | 443 |
| Data Integrity | No data integrity checks | Ensures data integrity |
| Authentication | No authentication mechanisms | Provides authentication of the server |
9. What is involved in the diagnosis of a slow computer?
Ans:
Slow computer diagnosis begins with looking for high CPU or memory utilization in Task Manager for Windows or Activity Monitor on a Mac. One of the surest ways to fix a slow computer is to remove unnecessary start-up programs, clear temporary files, and scan for malware. Updating the O.S. and drivers can also help. In most cases, hardware upgrades, such as adding extra RAM, may also be required. This step-by-step guide can determine whether a problem is software-related or hardware-related.
10. What are network monitoring tools?
Ans:
Track network traffic, troubleshoot problems, and ensure the best network performance using different network-monitoring tools: Wireshark, Nagios, and SolarWinds. Wireshark captures and analyses all packet data; it is very helpful for deep troubleshooting. Nagios means real-time server, switches, and application monitoring and sends alerts if something goes wrong. SolarWinds provides with a full suite for performance and traffic analysis. This makes it easy to manage the health of the network proactively.
11. How to check if a computer’s hardware is working?
Ans:
- Computer hardware functionality is checked on the components, including CPU, RAM, hard drive, and graphics.
- Diagnostic software programs like CPU-Z, MemTest86, and CrystalDiskInfo are used to monitor the health status of the hardware and diagnose some complex problems.
- BIOS or UEFI normally possesses diagnostic tools to self-test memory and check storage/other devices.
12. Can the purpose of RAM in a computer be explained?
Ans:
- RAM is the short term memory of a computer-it is where data and instructions are stored temporarily for the central processing unit.
- It allows a CPU to run on current applications and processes quickly, greatly influencing the system’s speed and multitasking capabilities.
- In general, more RAM means better performance in task areas relying on lots of data-storage activity since the data in these files stream to RAM.
- It may seem similar similar age, but in RAM, the data is volatile, and that sandt every time turn off computer.
13. What are the common symptoms of a failing hard drive?
Ans:
- Files may be corrupted or take an inordinate amount of time to open, and the operating system will not boot.
- Error messages associated with S.M.A.R.T. are common early warning signs, which can be inspected using diagnostic tools.
- Prudent Recommendation: Systematic data backup is recommended if symptoms appear as failure leads to complete data loss.
14. What must be done to replace a power supply unit in a desktop computer?
Ans:
P.S.U. replacement starts with disconnecting the computer from the power source and opening the case. Old P.S.U. Cables are removed from the motherboard, CPU, and GPU components. The old P.S.U. is removed after unscrewing from its place, and a new unit is installed. After reconnecting all the cables, the P.S.U. is secured to its place, and the computer is turned on to test every component. Special care needs to be taken so as not to damage it.
15. How does one resolve printer issues?
Ans:
Printer troubleshooting starts with seeing its power, connection, and paper jam status, to name a few. Software problems can be easily solved by installing the correct printer driver or updating it if needed. Networked printers should try to verify network settings, and for hardware problems, check the paper and ink levels. Running the printer’s troubleshooting utility provides particular guidance. These steps are followed in printer troubleshooting for hardware and software-related issues.
16. How does one measure computer overheating?
Ans:
Computers are bound to overheat if they continuously shut down, start responding slowly, or produce abnormally noisy fans. The temperature in real-time can be known through either HWMonitor or Core Temp through the monitoring software. A look inside the case can be taken, and any dusty cooling system parts can be checked. Maintaining good ventilation around the computer avoids overheating. If it is done in time, one can avoid breaking any of the other components kept within.
17. What is a motherboard, and what do motherboards typically consist of?
Ans:
- A motherboard is the brain and the main printed circuit board of a computer. Chipsets on a motherboard help regulate data flow between the CPU and other parts.
- It contains critical components: the central processing unit, random access memory, and expansion slots for graphics processors or other cards.
- Connectors for peripherals, power, and storage devices are also found here, and they play a significant role in ensuring component-to-component communication.
18. Explain how a video card functions.
Ans:
- A GPU is short for a graphics processing unit. It refers to the hardware of a computer with the responsibility of processing and rendering visual data to deliver images on a computer’s display.
- Dedicated Graphics have their memory known as VRAM, offloading most of the visual processing from the CPU, enhancing the latter’s performance.
- Integrated Graphics have a central processing unit and can manage the basic graphics but lack power in demanding applications. A GPU significantly boosts graphical capabilities.
19. What is the purpose of a U.P.S. (Uninterruptible Power Supply)?
Ans:
- When there is power out, it prevents the loss of data and damage caused by hardware.
- It has inbuilt activated batteries to ensure the devices stay on for a while and act as a backup.
- The U.P.S. systems protect against power surges, voltage drops, and spikes.
- The appliances are used with computers and networking equipment to make operations run without interruptions.
20. How to safely clean the internal components of a computer?
Ans:
Cleaning the inner parts involves using compressed air to remove dust particles from fans, heat sinks as well as vents without touching sensitive parts. Liquids as cleaners are a big no-no because they can damage, it is highly recommended to use antistatic tools due to static discharge. Overheating is caused by dust, constant cleaning is advisable to keep the flow of air or performance proper. Dismantling it for cleaning requires that the power source be disconnected, plus components have to be gently handled not to damage them.
21. What are some ways to troubleshoot a software installation failure?
Ans:
Troubleshooting software installation failure involves steps such as checking the system’s compatibility, ensuring that there’s enough disk space available, checking for proper permissions, looking at error log reports, and updating the system software. All these help eliminate conflicts, missing dependencies, or corrupt installation files, making the installation successful.
22. How might the differences between viruses, worms, and malware be characterized?
Ans:
A virus is a malicious program that attaches itself to files; it moves its copies from file to file and system to system as it runs. A worm is distinct from a virus in that it doesn’t need to latch onto a file and can replicate over networks with little user action. Malware is a catch-all term describing all forms of malicious programs, including viruses, worms, and spyware.
23.How to remove a virus from a computer?
Ans:
- To remove a virus, first of all disconnect the infected computer from the network to avoid spreading further.
- If the virus is still not removed after an initial clean-up, may have to perform a system restore or a full reinstallation of the operating system.
- It is also important to update antivirus software later to ward off future infections.
- For severe cases, professional support may be needed to completely get rid of the virus.
24.Describe how updates of software are managed within a system.
Ans:
- A managed process of software update looks after the availability of a soft patch, application of which together with scheduling of installations decreases time spent on downtime.
- Enhances security and system operation of improvements, and usually applies improvements in security and a slight increase in system function or performance.
- Most the systems allow administrators to allow auto-processing of these upgrade functions, which ensures updating regularly without manual intervention can improve safety.
25. What is a firewall, and how does it work?
Ans:
- A firewall is a security mechanism that acts as a gatekeeper, monitoring and regulating network traffic according to defined security rules.
- Depending on the source, destination, and type of traffic, it can block or allow traffic, thereby restricting unauthorized access to the system.
- Firewalls are necessary in safeguarding sensitive data against threats such as viruses, malware, and hacking attempts.
26. How does a computer recover to an earlier point in time?
Ans:
The system restore can be used to restore a computer back to its original state by making use of the “System Restore” feature that comes along with the system. After selecting a restore point prior to when the problem first arose, the system automatically runs the process according to choice. It reverts the settings, drivers, and files of the system to a previously set state and thus solves most software-related problems without altering personal data. This is one of the fastest means of solving compatibility problems and undoing changes that were unintentionally made to the system.
27. What is System Restore?
Ans:
System Restore is a feature in Windows that allows users to revert their system settings and files to a previous state, usually to correct problems that occur following the installation of new software, drivers, or updates. It does not touch personal files but can solve stability problems by rolling back the system configurations to a working state. Users start the System Restore process by selecting a specific restore point, which is automatically or manually created before any major changes.
28. How to clear the cache and cookies of a web browser?
Ans:
Under “Privacy” or “History” in the browser settings, clear cache and cookies by selecting the options for deletion. It will delete stored data like login credentials and history of browsing. This cleans the cache and cookies to have a faster experience on browsing and free storage space and sometimes removes problems due to out-of-date or conflicting session data. Periodical clearing of cache and cookies is a good habit, especially after troubleshooting performance problems on websites.
29. What is a virtual machine?
Ans:
- A virtual machine, or VM, is the software imitation of a physical computer that runs its own OS and applications independent of a host system.
- Vms are very useful to create multiple environments on one machine, usually for development, testing, or consolidation servers.
- That added security allows the flexibility of being able to test or deploy an application without jeopardizing system stability.
30. How to configure a user account in Windows?
Ans:
- In order to open a user account in Windows, go to “User Accounts” in Control Panel.
- There, can create a new account, assign logon details, and adjust permissions, if necessary.
- Might also need to assign them to certain groups, which determine their access rights.
- Group policies might be in place to enforce limitations for example, a policy on file access or software installs.
31. How to deal with an angry customer?
Ans:
- The full understanding of the problem requires managing an irate customer with active listening, acknowledgement of frustration, and responses with empathy.
- Answers should be short and solution-focused. Calm and professional, that can help de-escalate the situation.
- Can provide them with practical steps to solve their concerns or an alternative solution to convert a negative experience into a positive one by addressing their concerns promptly and respectfully.
32. How to approach to solve a difficult technical problem.
Ans:
Most complex technical problems require patience and sometimes detailed troubleshooting. For example, if a user is having software crashes that keep recurring, the technician might have to check whether there could be software conflicts, update, or check for hardware compatibility issues among others. This can be done effectively and will give the user confidence without overwhelming him/her with technical details.
33. How to prioritize multiple requests for help?
Ans:
It considers requests by urgency, customer impact, time sensitivity, and complexity. The highest priority issues involve core functionality problems such as system outages. Other problems are scheduled depending on resources available, and the least important matters may be done at later times. In this regard, critical operations will always be supported first to make sure that there is proper distribution of resources in terms of maximum impact and customer satisfaction.
34. What does an effective customer communication process include?
Ans:
An effective process of communication includes active listening, ensuring that understood what they said, and providing clear explanations. In any case, no solution may be available immediately. Keep them updated and ask for feedback after the resolution of the issue. Follow-up with simple language ensures trust building, which reflects an important value: the worth and knowledge of customers concerning the support process. The support experience is thus improved.
35. How to explain a technical problem to a non-technical user?
Ans:
- Technical issues should also be explained in simple technical terms by breaking down complex procedures and using minimal jargon.
- Analogies can be helpful-such as network traffic for road traffic. Should feel aided and guided to move the process along confidently.
- The procedure should concentrate on what information the user needs to move forward to execute the operation, but without overwhelming her with all the steps leading to that end.
36. What is the most important skill of a technical support representative?
Ans:
- A technical support representative should possess problem-solving skills because these enable easy identification and swift resolution of the issue at hand.
- The communication skill also forms an important part of the set because this enables the representative to express the solution properly.
- Other important attributes include patience, technical expertise, and empathy enable a technical support representative to give timely.
37. What to do if users cannot answer a customer question?
Ans:
- When users do not know, tell the customer that users do not know and request any further information they might be able to provide users to better answer their question.
- Inform them users will get back to them and research the problem or verify it with other colleagues to make sure users are giving them correct information.
- This approach not only builds trust but also fosters a positive relationship with customers by demonstrating a commitment to their needs and concerns.
38. Describe an instance of receiving negative feedback.
Ans:
When receiving negative feedback, remain calm and attentive. Thank the customer for feedback; apologize if appropriate; seek to understand the cause of the customer’s dissatisfaction; show a commitment to taking corrective action immediately to restore the customer’s satisfaction. Show a commitment to continuous improvement by following up with the customer after the situation is corrected.
39. How to keep customers informed about their problems?
Ans:
Keeping the customers updated regularly via email or phone about the status of the problem informs the customers that something is being done on their problem. Develop realistic timelines, and whenever changes take place, let them know quickly. It is only through transparency that customers can be trusted with this type of communication, and follow-ups are less likely to occur because they feel heard and valued throughout the entire support process.
40. How to manage customer expectations?
Ans:
This means managing expectations by setting realistic timelines and indicating the potential challenges. Always outline the steps that one is taking to solve this problem and keep it totally transparent. This reduces frustration amongst customers because they know exactly what to expect, making for a more positive outcome. This proactive communication fosters trust and reinforces the customer’s confidence in the support process, leading to stronger relationships.
41. When a user reports their computer won’t turn on, what steps are taken?
Ans:
- First, check if the power cable is properly connected to both the computer and power outlet.
- Look for any LED indicators on the power button or computer to see if it receives power.
- Next, disconnect all peripherals like USBs or external devices and try turning it on again.
- If there’s still no power, inspect the power supply and internal components for signs of damage.
42. When a customer is unable to access the internet, how is troubleshooting conducted?
Ans:
- Begin by checking if other devices on the same network can connect to isolate the issue.
- Verify the device’s Wi-Fi settings, ensuring it’s connected to the correct network and that airplane mode is off.
- Check network cables and confirm the IP settings if connected via Ethernet. If issues persist, investigate potential outages with the ISP.
43. What steps assist a user who cannot print from their computer?
Ans:
- Ensure the printer is connected to the computer or network and is powered on.
- Check the print queue to see if there are stuck or pending jobs, then clear it if necessary.
- Verify that the correct printer is selected as the default in the printer settings.
- Update or reinstall printer drivers, especially if the issue arose after a system update.
44. When a user complains their application is crashing frequently, what is checked?
Ans:
First, check if the system meets the minimum requirements for the application. Ensure that both the application and operating system are fully updated, as updates often fix bugs and compatibility issues. Monitor system resources to see if high CPU, memory, or storage usage could be causing crashes. Review error logs, which might indicate specific causes for the crashes. Finally, consider reinstalling the application if issues persist.
45. What actions are taken if a user reports a blue screen error?
Ans:
Ask the user to note any error codes or messages displayed on the blue screen, as they can help identify the cause. Check for any recent software or driver changes that could have triggered the issue. Run a memory diagnostic to rule out RAM problems and a disk check for potential storage errors. Ensure all hardware drivers are up-to-date, as outdated drivers often lead to blue screens. If the problem recurs, consult the Event Viewer for specific logs.
46. How are Wi-Fi connectivity issues troubleshot?
Ans:
Check that the device is within the Wi-Fi range and that the network signal strength is adequate. Verify the Wi-Fi settings to ensure it’s connected to the correct network and password is correct. Restart the router and device to reset network connections and clear any temporary glitches. Ensure the device is set to obtain an IP address automatically, avoiding static IP conflicts. If multiple devices are affected, consider channel interference or ISP issues.
47. When a user says their keyboard is not responding, what is checked?
Ans:
- First, check that the keyboard is securely connected to the computer if it’s wired, or ensure it has enough battery power if wireless.
- Test it with a different USB port or use a different keyboard to isolate the issue.
- Restart the computer, as minor system glitches can sometimes prevent keyboard detection.
- Check Device Manager for any driver issues and update or reinstall the keyboard driver if necessary.
48. How is audio playback troubleshooting handled when a user experiences issues?
Ans:
- Verify that the system’s audio isn’t muted and that volume levels are set correctly for the output device.
- Check that the correct playback device is selected, especially if multiple devices are connected.
- Update or reinstall audio drivers, especially after a recent OS update.
- If external speakers, test them on another device to confirm functionality.
49. What approach is taken when a customer reports slow performance on their computer?
Ans:
- Open Task Manager to identify processes using excessive CPU, memory, or disk resources, which could slow down the system.
- Check for malware or viruses using a reliable antivirus scanner, as malicious software often impacts performance.
- Ensure that the operating system and software are updated, as patches can improve efficiency.
50. What actions are taken when a customer reports missing data?
Ans:
Check the Recycle Bin to see if the files were accidentally deleted but still recoverable. If not found, ask the user about any recent backup methods or cloud storage they may have used. Consider using a data recovery tool to retrieve lost files if no backup exists. Document the file names and paths, and search the system for any hidden or moved files. Review recent activities or installed programs that could have affected the files.
51. What remote support tools are familiar?
Ans:
Experience may include remote support tools like TeamViewer, AnyDesk, LogMeIn, and Microsoft Remote Desktop, which provide secure remote control of client systems. These tools allow technicians to view and control a user’s computer to diagnose and resolve issues directly. They also offer file transfer, remote reboot, and multi-session support. Familiarity with setting up and managing permissions for secure access is essential. Tools with cross-platform compatibility and session logging are often preferred.
52. Can experience with ticketing systems be described?
Ans:
Experience with ticketing systems such as Jira, ServiceNow, or Zendesk helps track issues, prioritize tasks, and manage support cases efficiently. These systems record detailed information about support requests, enabling organized handling and resolution tracking. Ticketing systems also assist in SLA management, ensuring timely responses according to priority. Reporting and analytics tools in these systems help identify recurring issues and support trends.
53. What diagnostic tools are used to troubleshoot issues?
Ans:
- Diagnostic tools include Windows Task Manager, Resource Monitor, Event Viewer, HWMonitor.
- Task Manager and Resource Monitor help identify system resource bottlenecks like CPU or memory usage.
- Event Viewer logs provide insights into system events and errors for in-depth analysis.
- HWMonitor and CrystalDiskInfo give valuable hardware temperature and health statistics.
54. How are support tickets and resolutions documented?
Ans:
- Each support ticket should detail the user’s issue, troubleshooting steps taken, and final resolution for clear documentation.
- Ticketing systems like Zendesk or ServiceNow streamline this by organizing information in structured formats.
- Accurate documentation improves support quality, aiding future troubleshooting and consistency.
55. Are any monitoring software experienced?
Ans:
Experience with monitoring software like Nagios, SolarWinds, or Zabbix enables network performance tracking, hardware health, and resource usage. These tools help monitor infrastructure uptime and send alerts for unusual activity, such as high CPU or bandwidth usage. Monitoring software can also display real-time dashboards with system metrics, providing a clear view of network health. Alerts and reporting features assist in proactive troubleshooting.
56. What is the experience with Active Directory?
Ans:
Experience with Active Directory (AD) includes managing user accounts, configuring group policies, and setting permissions for secure access. Active Directory allows centralized management of organizational resources, users, and security settings. Using AD, accounts can be set up with access controls to protect sensitive information. Managing OUs (Organizational Units) and GPOs (Group Policy Objects) is also essential. This knowledge ensures smooth management of large-scale user and device environments.
57. Can the purpose of an asset management tool be explained?
Ans:
Asset management tools track hardware and software inventories, enabling better resource allocation and planning. They help organizations monitor the lifecycle of assets, from acquisition to disposal, and streamline asset tracking. Tools like ServiceNow Asset Management also support compliance by tracking software licenses and expiration dates. By documenting all assets, organizations can quickly identify and resolve asset-related issues. Asset data aids budgeting, maintenance scheduling, and performance management.
58. Have any chat support tools been used?
Ans:
- Chat support tools like Slack, Microsoft Teams, and Intercom facilitate real-time communication and provide prompt assistance to users.
- These platforms allow instant message notifications, enabling quicker responses to issues.
- Using channels, support teams can categorize issues and discuss solutions collaboratively.
- Integrating chat tools with ticketing systems can streamline ticket creation and updates.
59. What methods are used to manage passwords securely?
Ans:
- Secure password management often includes using password managers, enforcing strong passwords, and multi-factor authentication.
- Password managers store credentials in encrypted formats, enhancing security and accessibility.
- Strong password policies should prevent using common or weak passwords, reducing account vulnerability.
60. What version control systems have been worked with?
Ans:
- Experience with version control systems like Git, GitHub, GitLab, or Bitbucket supports collaborative development.
- These tools help track changes, allowing multiple contributors to work on the same codebase.
- They allow for branching, which enables isolated development of new features or fixes before merging with the main code.
61. What are the current trends in the technical support industry?
Ans:
The maturing of the technical support industry relates to trends like automation, remote support, and AI-powered chatbots, which ensure support processes are streamlined with faster customer responses. Other pivotal trends include cloud computing and digital transformation, in which support teams can access data and tools from anywhere in the world. There is an added focus on data security, self-service options, and personalized customer experiences that reshape the way technical support is provided to meet evolving customer expectations.
62. How is today’s technological knowledge kept up-to-date?
Ans:
Keeping abreast of technology changes requires continuous training via industry publications, online courses, and certifications. Of course, attending webinars, conferences, and tech meetups keeps one abreast of what is happening. Contributing to tech forums, reading relevant blogs, and keeping up with industry leaders on social media update one’s knowledge base. Practical experience and experimentation with new tools and technologies give insights that are applied directly to technical support roles.
63. Can one explain the significance of data security in technical support?
Ans:
Data security in technical support is critical as technical teams, in the course of attending to different types of technical issues of customers, will often come across data that contains sensitive information related to their customers. Data security creates this trust and gives the satisfaction of keeping data secure and preventing a data breach. With the increasing cyber threats, the safe management of data in technical support matters more than ever.
64. What general compliance requirements must technical support comply with?
Ans:
- These regulations have unique data privacy and security requirements for handling customer data and necessitate tight standards.
- Without adherence to such regulations, heavy fines and a bad reputation are the consequences. This support staff training on such regulations will ensure compliance and proper handling of customer information.
- Knowledge about such regulations is also important in forming and implementing internal policies aligned with the best legal standards.
65. How is sensitive customer information managed?
Ans:
- Sensitive customer information is treated confidentially and safely and secured through controls on access, encryption.
- Only authorized personnel can access the sensitive data, and in most cases, multi-factor authentication is applied for an added layer of security.
- All staff undergo periodic training on data protection practices to understand the need to keep the information confidential.
- Storage is kept only on customer information when necessary; otherwise, the data is deleted or anonymized.
66. What is the understanding of cloud computing?
Ans:
- Cloud computing allows access to services over the internet rather than from a personal on-premises server.
- To support this, it scales resources based on demand, provides access to services remotely, and saves organizations money on IT infrastructure.
- For technical support, cloud computing makes it possible to troubleshoot remotely, access data quickly, and collaborate easily.
67. How is technical support changing because of artificial intelligence?
Ans:
This changes technical support by allowing automation: automated responses, predictive maintenance, and even AI-driven chatbots to handle routine questions. Most importantly, AI improves self-service options, identifies patterns around customer issues, and supports troubleshooting so that the support agents can focus on more complex work. Machine learning algorithms can predict possible problems, thereby making support proactive. Efficiency and customer experience are enhanced with AI tools shortened response time and increased support quality.
68. Can any experience with CRM systems be described?
Ans:
Many of the experiences a person could have regarding CRM systems relate to managing customer information, tracking interactions, and, thus, streamlining customer service processes. Therefore, CRMs such as Salesforce, HubSpot, or Zoho make all data centralized access, letting support teams see customer histories and personalize their support. Familiarity with CRM software helps in effectively resolving customer issues and remembering how to streamline follow-up processes.
69. What is the meaning of ITIL?
Ans:
ITIL is a service management framework that aligns IT processes with business needs. ITIL is short for Information Technology Infrastructure Library, and this generates the best practice for service lifecycle management, cutting across all dimensions of incident management, problem management, and change management. Technical support guides efficient and standardized practices regarding service requests, issue resolution, and the delivery of quality services.
70. What are the mechanisms available for enforcing compliance with software licenses?
Ans:
- Asset management ensures that there is always compliance with the agreed terms of the software licensing agreements by keeping tabs on usage to avoid any licensing violation.
- Regular audits and observation of policies related to licensing ensure the minimal penalty resulting from non-compliance.
- Support staff training on licensing agreements is meant to enlighten them on the importance of compliance in the day-to-day operations and, therefore, with customer support interactions.
71. Can an example of going above and beyond for a customer be given?
Ans:
- This could be through assisting a customer who may have needed additional time or collaborating with departments to ensure the right solution was met.
- Proactive contact with the customer, staying on top of updates, and keeping them informed at every step resulted in a resolution that surpassed their expectations.
- Of greater importance is providing more resources or tips on how the problem could be prevented or fixed in the future as a show of commitment to the customer’s success.
72. What motivates work in technical support?
Ans:
- Technical support is often driven by the desire to solve problems, make customers successful, and learn new skills.
- This role also takes satisfaction in solving problems and offering solutions that will directly impact the end-users.
- A personal focus on growth and teamwork motivates technical support roles which creates a fulfilling reward for their efforts.
73. Stress Management in a Fast-Paced Environment.
Ans:
Necessary elements to manage stress in such fast-paced environments include an arrangement of priorities, organization, and time management. Managing short breaks, focusing on one issue at a time, and clear communication with colleagues can reduce pressure. Handling stress is accompanied by regular exercise, mindfulness techniques, and maintaining an appropriate work-life balance. Calmness and composure in instances involving pressure are crucial, ensuring that problems are better solved and decision-making.
74. Describe an experience in which users had to learn something new quickly.
Ans:
Learning a new tool or software for solving a customer problem or helping the team with a specific project can be one instance. In such situations, quick research, testing of the tool, and support from colleagues with experience helped bring the skills on board. Proactive and flexible capabilities are shown through the rapid adaptation and application of knowledge to ensure success at the task – exactly what is needed to adapt to rapidly changing technical environments.
75. How to work with colleagues on complex problems?
Ans:
Collaborating on complex issues requires appropriate communication skills, active listening, and respect for the team members skill sets. Effective collaboration requires breaking the problem into pieces, assigning roles for cooperation. Updating and brainstorming sessions and shared documentation will also ensure everyone is informed about the steps taken. Maintaining a positive attitude and supporting each other creates a collaborative environment and enhances the ability to solve problems and bring results.
76. Is it possible to share an example of a project worked on and its role?
Ans:
- An example might be participation in a migration project aimed to assist users during the transition.
- My specific tasks included troubleshooting problems, creating user manuals, and giving training sessions.
- This involved coordination with the project team, administering user inquiries and ensuring it went through very smoothly.
- This role showed problem-solving skills, customer service, and teamwork, therefore completing the project.
77. How to Approach Constructive Criticism?
Ans:
- Approach constructive criticism with an open mind to highlight areas needing improvement rather than personal attacks.
- Listen actively and fully understand the criticism so that there are good opportunities to take action.
- Ask questions to clarify points made and make necessary changes to prove that want to learn and grow.
- Accepting constructive criticism will improve performance, change, and professional relationships.
78. How is continuous improvement of skills ensured?
Ans:
- Continual skill improvement is maintained through learning objectives, attendance at workshops, and myriad on-demand online courses.
- Industry trends are followed read articles that are available technically, to attain new skills.
- Knowledge sharing in teams and feedback received from colleagues provide additional growth.
79. Describe one problem encountered in a previous role and the solution applied.
Ans:
Handling large volumes of customer queries arising from a system outage was challenging. However, the fallout was reduced, and service was restored within the shortest time possible by sorting urgent matters with the technical team to implement quick resolutions. Customers were continuously updated on the progress to make them comfortable, and after restorations were made, they were followed up to ensure satisfaction with services. This is applying problem-solving skills, effective communication, and putting the customer at the centre.
80. Long-Term Career Goals of Technical Support.
Ans:
Long-term goals in technical support are to become a specialist or a management position have certifications in relevant technologies, or even career changes into system administration or network support. A good foundation in technical expertise and customer service skills can provide many opportunities in technical fields. Continued skill development and experience aid one to hope that soon one can contribute towards larger projects.
81. What is DNS spoofing, and how can it be prevented?
Ans:
This is a type of hacking where the DNS record is modified to point users to malicious sites. It can be prevented using DNSSEC (Domain Name System Security Extensions) that validate DNS responses. Regular software updates and network monitoring are also recommended. Strong network security measures include firewalls and intrusion detection. Educating users about recognizing phishing attempts can further enhance overall security and reduce the risk of falling victim to such attacks.
82. Explain the Subnet Mask Function.
Ans:
- The subnet mask splits the IP into network and host parts. This is crucial when on large networks, in case a waste of IPs is utilized.
- It makes handling IPs much easier by specifying the networks, which results in more suitable routing of the traffic flow.
- Subnetting enables better segmentation of a network and controls the broadcasting considerably.
83. How does DHCP work, and what is its purpose?
Ans:
- DHCP dynamically assigns IP addresses to a device, thereby simplifying network management.
- A device requests an IP address from the DHCP server, which then sends an available IP address from its pool along with other network details.
- This minimizes errors due to manual IP address entry and makes device connections to the network smooth.
84. How does Symmetric Encryption differ from Asymmetric Encryption?
Ans:
- Asymmetric encryption uses one key for encryption and decryption, which is faster but less secure in exchanging keys.
- Asymmetric encryption uses two keys, public and private, for encryption and decryption, enhancing security.
- Asymmetric encryption is suitable for internal use, but symmetric is better for exchanging data securely.
85. Can the function of a load balancer be described?
Ans:
A load balancer distributes incoming network traffic across multiple servers to ensure no single server is overloaded. This helps improve application availability, responsiveness, and fault tolerance. Load balancers can work at both the network and application layers. They support redundancy, improving uptime in case of server failure. By optimizing resource use and managing traffic efficiently, load balancers enhance overall system performance and user experience.
86. Why is patch management important?
Ans:
This helps in maintaining systems, as patches help fix security vulnerability issues and enhance system stability. It also prevents attacks based on the fact that the attacked person hasn’t patched that particular software. Patching is also maintained regularly according to industry standards. Automatic patch management tools update in batches. A well-defined patch management strategy can significantly reduce downtime and ensure compliance with regulatory requirements.
87. How is a Wi-Fi network secured?
Ans:
- Wi-Fi network security would involve strong passwords.
- WPA3 encryption, which provide better protection.
- WPS (Wi-Fi Protected Setup) is disabled to prevent unauthorized access.
- Firmware updates on the routers help protect against new vulnerabilities.
- Network segmentation further reduces the amount of access.
88. What is data backup, and what strategies are recommended?
Ans:
Data backup is crucial for preventing data loss from accidental deletions, hardware failures, or cyberattacks. Recommended strategies include following the 3-2-1 rule, which entails maintaining three copies of data on two different types of storage media, with one copy stored off-site. Incremental and differential backups are effective methods that conserve both storage space and time. Implementing automated backup processes ensures that backups occur regularly and consistently.
89. Can the purpose of an SSL certificate be explained?
Ans:
An SSL certificate serves to encrypt data transmitted between a user’s browser and a website, protecting sensitive information from unauthorized access. It also plays a vital role in authenticating the identity of the website, thereby fostering trust among users. By encrypting critical data such as login credentials and payment information, SSL helps secure online transactions. This encryption is essential for safeguarding personal information during digital interactions.
90. How are compliance and security issues addressed?
Ans:
Compliance and security challenges are managed through regular audits and strict adherence to established standards, such as ISO and NIST. Ongoing security training for staff is vital to ensure everyone is aware of current regulations and best practices. Staying informed about evolving legal requirements is equally important for effective compliance management. Employing best practices like encryption and access controls can significantly mitigate security risks.




