Blog
-
AWS Certified Cloud Practitioner – Essential Cloud Knowledge
Introduction to AWS Certified Cloud Practitioner Importance of AWS Certification Roles and Responsibilities of AWS Cloud Practitioners Industry Demand for AWS Practitioners Freelancing vs Full-Time Salary Comparison Job Opportunities for AWS Certified Professionals Salary Trends in Different Regions Factors Affecting AWS Practitioner...
-
The Ultimate Guide to Git and Version Control
Introduction to Git and Version Control History and Evolution of Git Key Features of Git Basic Git Commands and Their Uses Git Branching and Merging Working with Remote Repositories Git Workflow: Centralized vs Distributed Best Practices for Using Git Git vs. Other Version Control Systems Advanced Git Features and...
-
What is Azure DevOps?
Introduction to Azure DevOps Features and Components of Azure DevOps Azure Repos: Source Code Management Azure Pipelines: CI/CD Implementation Azure Artifacts: Package Management Azure Test Plans: Testing Capabilities Benefits of Azure DevOps for Development Teams Integration with Third-Party Tools Security Features in Azure DevOps Getting...
-
The Future Scope of IoT: Trends, Opportunities, and Innovations
Introduction to IoT Evolution and Growth of IoT Key Industries Benefiting from IoT Emerging Technologies in IoT AI and Machine Learning Integration in IoT Security Challenges in IoT Smart Cities and IoT Adoption IoT in Healthcare, Agriculture, and Manufacturing IoT and 5G: Future Trends Job Opportunities in IoT Key IoT Certifications for...
-
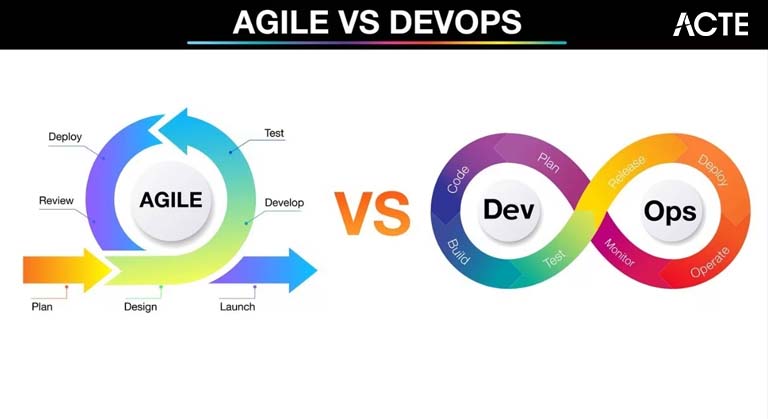
DevOps vs Agile: Difference
Introduction to DevOps and Agile Key Principles of Agile Key Principles of DevOps Agile Development Life Cycle DevOps Deployment Pipeline Comparison Based on Methodology Tools Used in DevOps and Agile Benefits and Challenges of Agile Benefits and Challenges of DevOps When to Choose Agile vs DevOps? Case Studies of Agile and DevOps...
-
Robotic Process Automation : RPA Developer Salary Overview
Introduction to RPA Development Role and Responsibilities of an RPA Developer Skills Required for an RPA Developer Industry Demand for RPA Developers Entry-Level vs Experienced RPA Developer Salary Salary Trends Across Different Countries Certifications That Boost Salary Potential Job Roles Related to RPA Development Freelance vs Full-Time RPA...
-
How to Become an AWS Solution Architect Associate
Introduction to AWS Solution Architect Role Key Responsibilities of an AWS Solution Architect Skills Required for AWS Solution Architects Learning AWS Fundamentals Hands-on AWS Practice and Labs Preparing for the AWS Certified Solutions Architect Associate Exam Best Study Materials and Resources Real-World Projects and Case Studies Getting Your...
-
AWS Command Line Interface (CLI): A Complete Guide
Introduction to AWS CLI Benefits of Using AWS CLI Installing AWS CLI on Different Platforms Configuring AWS CLI for Your Environment Basic AWS CLI Commands Managing AWS Resources with AWS CLI Scripting and Automation Using AWS CLISecurity Best Practices for AWS CLI Troubleshooting Common AWS CLI Issues Advanced Features of AWS CLI Real-World Use...
-
Amazon Web Services List and Products
Introduction to AWS Services Compute Services Storage Services Database Services Networking and Content Delivery Services Security and Compliance Services Analytics and Big Data Services Machine Learning and AI Services DevOps and Developer Tools on AWS AWS Cost Management and Optimization Tools Future AWS Service...
-
Google Cloud Computing: Learn the Basics and Advanced Concepts
Introduction to Cloud Computing History and Evolution of Cloud Computing Types of Cloud Computing Services (IaaS, PaaS, SaaS) Key Cloud Service Providers (AWS, Azure, GCP) Benefits of Cloud Computing Security Challenges in Cloud Computing Cloud Computing Use Cases Getting Started with Cloud Platforms Cloud Certifications and Career...
- Telephone Interview Questions and Answers
- Genpact Interview Questions and Answers
- 50+ [REAL-TIME] Personal Interview Questions and Answers
- Behavioural Interview Questions and Answers
- 45+ [REAL-TIME] Team Leader Interview Questions and Answers
- Embedded System Interview Questions and Answers
- UX Designer Interview Questions and Answers
- 50+ [REAL-TIME] Nutanix Interview Questions and Answers
- 50+ [REAL-TIME] SAP PS Interview Questions and Answers
- 50+Wipro Interview Questions and Answers
Interview Questions and Answers
- Data Science Masters Program Training Course
- Python Master Program Training Course
- Software Testing Master Program Training course
- Data Analyst Masters Program Training Course
- Full Stack Developer Masters Program Training Course
- Digital Marketing Masters Program Training Course
- Java Full Stack Developer Master Training
- Cloud Computing Master Program Training Course