What is CCNA?
CCNA is a popular certification among computer network engineers. Full Form of CCNA is Cisco Certified Network Associate. It is a certification program valid for all type of engineers. It includes entry-level network engineers, Network Administrators, Network Support Engineers and Network Specialists.
It is estimated that more than 1 million CCNA certificates have been awarded since it was first launched in 1998.
The CCNA certificate covers a broad range of networking concepts. It helps candidates to prepare for the latest network technologies they are likely to work on.
Some of the common topics covered under CCNA certification include:
- OSI models
- IP addressing
- WLAN and VLAN
- Network security and management (ACL included)
- Routers / routing protocols ( EIGRP, OSPF, and RIP)
- IP Routing
- Network Device Security
- Troubleshooting
Why CCNA?
- CCNA validates the ability to understand, operate, configure, and troubleshoot routed and switched network.
- It helps to resolve a customer’s problem more efficiently.
- Once you are CCNA certified, you can get a higher salary.
- It teaches the candidate how to create a point-point connection.
- It explains how to construct network addresses.
Why to acquire a CCNA certification?
- The certificate validates a professional’s ability to understand, operate, configure and troubleshoot medium-level switched and routed networks. It also includes the verification and implementation of connections via remote sites using WAN.
- It teaches the candidate how to create point-to-point network
- It teaches about how to meet users requirement by determining the network topology
- It imparts on how to route protocols in order to connect networks
- It explains about how to construct network addresses
- It explains on how to establish a connection with remote networks.
- The certificate holder can install, configure and operate LAN and WAN services for small networks
- CCNA certificate is a pre-requisite for many other Cisco certification like CCNA Security, CCNA Wireless, CCNA Voice, etc.
- Easy to follow study material available.
Types of CCNA Certification
There are different types of CCNA Certification given below:
- CCNA Routing & Switching (R&S)
- CCNA Wireless
- CCNA Data Center
- CCNA Security
- CCNA Service Provider
- CCNA Voice
Network Connecting Devices
Network connecting devices are used to connect two or more devices to share data or resources from one network to another network.
Some important network connecting devices are given below:
HUB
- The general meaning of the word hub is any connecting device.
- It works on the physical layer of OSI Model.
- A hub is designed to connect computers in a private network.
- It is used to connect peer to peer small networks.
- Hub is slow and insecure.
Switch
- A switch also connects computers like a hub.
- It works on the Data link layer of OSI Model.
- It determines what computer or device the packet is intended for and sends it to that computer only.
- A switch is fast and secure.
Router
It is designed to receive, analyze, and move incoming packets to another network.
A router has more capabilities than other devices, such as a hub or a switch.

End Devices
The network devices that people are most familiar with are called end devices. It is a source to a destination device in a networked system.
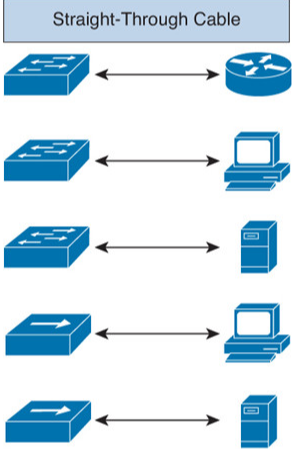
Straight-through Cable
It is used when we want to
- Connect Switch to Router
- Connect Switch to PC
- Connect Switch to Server
- Connect Hub to PC
- Connect Hub to Server
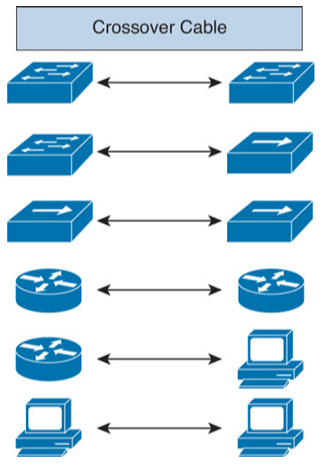
Crossover Cable
It used when we want to
- Connect Switch to Switch
- Connect Switch to Hub
- Connect Hub to Hub
- Connect Router to Router
- Connect Router to PC
- Connect PC to PC
What is a Network?
A network is a group of two or more devices connected by some transmission media, i.e., cables.
The purpose of designing a network is to enable the sharing of files and information between multiple devices.
Types of Network
There are following types of Network –
- Local Area Network (LAN)
- Metropolitan Area Network (MAN)
- Wide Area Network (WAN)
- Storage Area Network (SAN)
- Campus Area Network (CAN)
- Personal Area Network (PAN)
Local Area Network (LAN)
It is a computer network that interconnects computers within a limited area such as a residence, school, or office building.
It can achieve a high data transfer rate at a low cost.
Metropolitan Area Network (MAN)
It is a computer network that interconnects computers within a city or limited geographical area.
MAN is larger than a LAN but smaller than a WAN.
Wide Area Network (WAN)
It is a computer network that covers a city, country, or even the entire world. The Internet is an example of a WAN.
Storage Area Network (SAN)
SAN is a high-speed network of storage elements. It establishes direct and indirect connections between multiple servers and storage devices.
Gmail and Yahoo are an example of a SAN.
Campus Area Network (CAN)
It is a computer network that interconnects a few local area networks within a university campus or corporate campus.
Personal Area Network (PAN)
It is a wireless telecommunications network for device-to-device connection within a short range.
Bluetooth, USB is an example of a PAN.
What is Internetworking?
An internetworking is a collection of individual networks, connected by intermediate networking devices that function as a single large network.
Internetworking uses Internet Protocol.
The standard reference model for internetworking is Open Standard Interconnection (OSI)
Protocol
It is a set of rules and conventions for communication between network devices.
Example
- Hyper Text Transfer Protocol (HTTP)
- File Transfer Protocol (FTP)
- Address Resolution Protocol (ARP)
Types of Internetworking
There are three types of internetworking –
- Internet
- Intranet
- Extranet
Internet
The internet is an extensive network of computers across the world.
- It is an example of a Wide Area Network (WAN).
- It uses telephone lines and satellite lines to communicate.
- It allows activities such as messaging, shopping, and teaching takes place online.
- It allows data and resources to be shared.
Intranet
Intranet provides similar services to the internet –
- It is a private network.
- It is generally limited to one organization, such as a company or school.
- It is used to share company information and computing resources among employees.
Extranet
The extranet is a part of an intranet that can access by authorized people using the internet.
- It is a network that uses the internet to link the company’s intranet to enhance the business-to-business relationship.
- It allows clients, partners, and vendors to access a variety of information.
- It is a combination of both the internet and intranet.
Why do we need internetworking?
We need internetworking for following primary reasons–
- Data Sharing
It allows users to:
- Exchange information from one PC to another
- Use E-mail, Facebook, and other related platforms to communicate
- Route data from a user to another user
- Exchange folders
- Resource Sharing
It allows users to share peripheral devices such as –
- Printer
- Scanners
- Fax
- Hard Disks
- Connection Sharing
It enables users to share a connection, such as:
- Bluetooth
- Hotspot
- Wi-Fi
- Access to a remote database
It is easy for a person to access any remote database. For example, a database of trains, online universities, hotels can be accessed as per the requirements.
The remote-control program can be used to troubleshoot problems or guide new users on how to perform a task.
Internetworking Challenges
- Implementing an internetwork is a difficult task; many challenges must be faced, especially in the areas of connectivity, reliability, and flexibility.
- File security has to be taken care of, especially if connected to WANs.
- Loss of packets.
- Different addressing schemes.
- It is difficult to troubleshoot a large network.
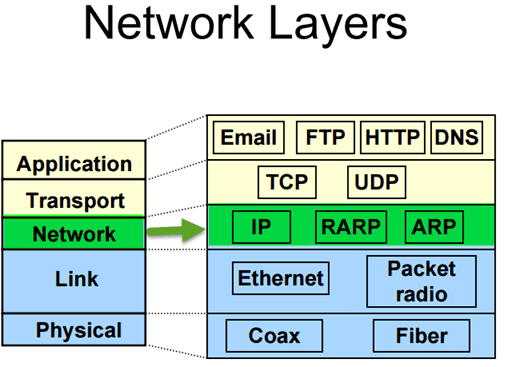
Understanding TCP/ IP layers
TCP/IP stands for Transmission Control Protocol/ Internet Protocol. It determines how a computer should be connected to the Internet and how data should be transmitted between them.
- TCP: It is responsible for breaking data down into small packets before they can be sent on the network. Also, for assembling the packets again when they arrive.
- IP (Internet Protocol): It is responsible for addressing, sending and receiving the data packets over the internet.
Below image shows TCP/IP model connected to OSI Layers..
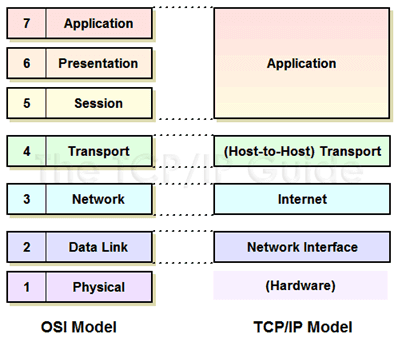
Understanding TCP/IP Internet Layer
To understand TCP/IP internet layer we take a simple example. When we type something in an address bar, our request will be processed to the server. The server will respond back to us with the request. This communication on the internet is possible due to the TCP/IP protocol. The messages are sent and received in small packages.
The Internet layer in the TCP/IP reference model is responsible for transferring data between the source and destination computers. This layer includes two activities
- Transmitting data to the Network Interface layers
- Routing the data to the correct destinations
So how this happen?
Internet layer packs data into data packets referred as IP datagrams. It consists of source and destination IP address. Beside this, IP datagram header field consists of information like version, header length, type of service, datagram length, time to live, and so on.
In network layer, you can observe network protocols like ARP, IP, ICMP, IGMP, etc. The datagram are transported through network using these protocols. They each resemble some function like.
- The Internet Protocol (IP) is responsible for IP addressing, routing, the fragmentation and reassembly of packets. It determines how to route message on the network.
- Likewise, you will have ICMP protocol. It is responsible for diagnostic functions and reporting errors due to the unsuccessful delivery of IP packets.
- For the management of IP multicast groups, IGMP protocol is responsible.
- The ARP or Address Resolution Protocol is responsible for the resolution of the Internet layer address to the Network Interface layer address such as a hardware address.
- RARP is used for disk less computers to determine their IP address using the network.
Understanding TCP/IP Transport Layer
The transport layer also referred as Host-to-Host Transport layer. It is responsible for providing the Application layer with session and datagram communication services.
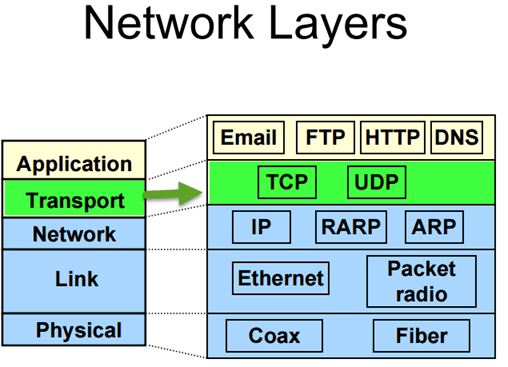
The main protocols of the Transport layer are User Datagram Protocol (UDP) and the Transmission Control Protocol (TCP).
- TCP is responsible for the sequencing, and acknowledgment of a packet sent. It also does the recovery of packet lost during transmission. Packet delivery through TCP is more safe and guaranteed. Other protocols that falls in the same category are FTP, HTTP, SMTP, POP, IMAP, etc.
- UDP is used when the amount of data to be transferred is small. It does not guarantee packet delivery. UDP is used in VoIP, Videoconferencing, Pings, etc.
Network Segmentation
Network segmentation implicates splitting the network into smaller networks. It helps to split the traffic loads and improve the speed of the Internet.
Network Segmentation can be achieved by following ways,
- By implementing DMZ (demilitarised zones) and gateways between networks or system with different security requirements.
- By implementing server and domain isolation using Internet Protocol Security (IPsec).
- By implementing storage based segmentation and filtering using techniques like LUN (Logical Unit Number) masking and Encryption.
- By implementing DSD evaluated cross-domain solutions where necessary
Why is Network Segmentation important?
Network Segmentation is important for following reasons,
- Improve Security- To protect against malicious cyber attacks that can compromise your network usability. To detect and respond to an unknown intrusion in the network
- Isolate network problem- Provide a quick way to isolate a compromised device from the rest of your network in case of intrusion.
- Reduce Congestion- By segmenting the LAN, the number of hosts per network can be reduced
- Extended Network- Routers can be added to extend the network, allowing additional hosts onto the LAN.
VLAN Segmentation:
VLANs enables an administrator to segment networks. Segmentation is done based on the factors such as project team, function or application, irrespective of the physical location of the user or device. A group of devices connected in a VLAN act as if they are on their own independent network, even if they share a common infrastructure with other VLANs. VLAN is used for data-link or internet layer while subnet is used for Network/IP layer. Devices within a VLAN can talk to each other without a Layer-3 switch or router.
The popular device used for segmenting are a switch, router, bridge, etc.
Subnetting
Subnets are more concerned about IP addresses. Subnetting is primarily a hardware-based, unlike VLAN, which is software based. A subnet is a group of IP address. It can reach any address without using any routing device if they belong to the same subnet.
Few things to consider while doing network segmentation
- Proper user authentication to access the secure network segment
- ACL or Access lists should be properly configured
- Access audit logs
- Anything that compromises the secure network segment should be checked- packets, devices, users, application, and protocols
- Keep watch on incoming and outgoing traffic
- Security policies based on user identity or application to ascertain who has access to what data, and not based on ports, IP addresses, and protocols
- Do not allow the exit of cardholder data to another network segment outside of PCI DSS scope.
Packet Delivery Process
So far we have seen different protocols, segmentation, various communication layers, etc. Now we are going to see how the packet is delivered across the network. The process of delivering data from one host to another depends on whether or not the sending and receiving hosts are in the same domain.
A packet can be delivered in two ways,
- A packet destined for a remote system on a different network
- A packet destined for a system on the same local network
If the receiving and sending devices are connected to the same broadcast domain, data can be exchanged using a switch and MAC addresses. But if the sending and receiving devices are connected to a different broadcast domain, then the use of IP addresses and the router is required.
Layer 2 packet delivery
Delivering an IP packet within a single LAN segment is simple. Suppose host A wants to send a packet to host B. It first needs to have an IP address to MAC address mapping for host B. Since at layer 2 packets are sent with MAC address as the source and destination addresses. If a mapping does not exist, host A will send an ARP Request (broadcast on the LAN segment) for the MAC address for IP address. Host B will receive the request and respond with an ARP reply indicating the MAC address.
Intrasegment packet routing
If a packet is destined for a system on the same local network, which means if the destination node are on the same network segment of the sending node. The sending node addresses the packet in the following way.
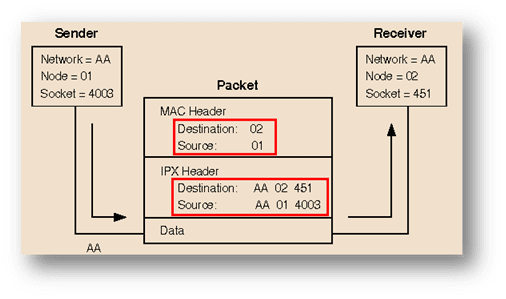
- The node number of the destination node is placed in the MAC header destination address field.
- The node number of the sending node is placed in the MAC header source address field
- The full IPX address of the destination node is placed in the IPX header destination address fields.
- The full IPX address of the sending node is placed in the IPX header destination address fields.
Layer 3 Packet delivery
To deliver an IP packet across a routed network, it requires several steps.
For instance, if host A wants to send a packet to host B it will send the packet in this ways
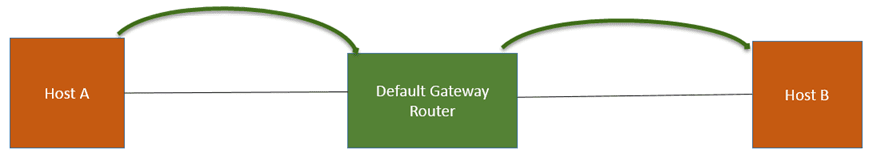
- Host A sends a packet to its “default gateway” (default gateway router).
- To send a packet to the router, host A requires to know the Mac address of the router
- For that Host A sends an ARP request asking for the Mac address of the Router
- This packet is then broadcast on the local network. The default gateway router receives the ARP request for MAC address. It responds back with the Mac address of the default router to Host A.
- Now Host A knows the MAC address of the router. It can send an IP packet with a destination address of Host B.
- The packet destined for Host B sent by Host A to the default router will have the following information,
- Information of a source IP
- Information of a destination IP
- Information of a source Mac address
- Information of a destination Mac address
- When the router receives the packet, it will end an ARP request from host A
- Now Host B will receive the ARP request from the default gateway router for the host B mac address. Host B responds back with ARP reply indicating the MAC address associated with it.
- Now, default router will send a packet to Host B
Intersegment packet routing
In the case where two nodes residing on different network segments, packet routing will take place in the following ways.
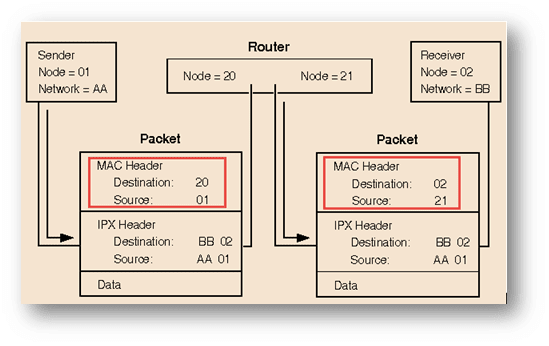
- In the first packet, in the MAC header place the destination number “20” from the router and its own source field “01”. For IPX header place the destination number “02”, source field as “AA” and 01.
- While in the second packet, in the MAC header place the destination number as “02” and source as “21” from the router. For IPX header place the destination number “02” and source field as “AA” and 01.
Conclusion
The content of the exams is proprietary. Cisco and its learning partners offer a variety of different training methods, including books published by Cisco Press, and online and classroom courses available under the title “Interconnecting Cisco Network Devices.
Fundamental knowledge is created and stockpiled in disciplinary environments, mostly at universities, and then used as required by (vertically integrated) industries to provide the products and services required by customers, including the military. This fundamental knowledge is different in kind from empirical knowledge gleaned during the development of technology and products. You get what you measure. Suppliers of fundamental knowledge measure publications, presentations, students supervised, awards received, and other metrics associated with individual investigators. The knowledge accumulates along traditional disciplinary lines because this is where the rewards are found.