Managing Identities and accesses within a network is critical for any organization. This task is performed by using different identity managers. This course teaches you how to manage users in an environment using Oracle identity manager. This course introduces the features of Oracle Identity Manager. The student will learn the terminologies and technology of the OIM. Start Learning with us ACTE Oracle Identity Manager Classroom and Online Training Course.
Presently as we know cloud is the future migration tools are being developed to migrate oim users to cloud it will take few years for successful migration and making all clients stable. So as developer prospective in future I guess oim won't have much to give but as a support or consulting there are many mnc’s to offer you.
Oracle Identity manager is highly customizable product and its implementation/solution requires highlevel of product understanding and understanding and designing solution for its customers which requires IDM analysts, IDM consultants or IDM arcitect.
Presently as we know cloud is the future migration tools are being developed to migrate oim users to cloud it will take few years for successful migration and making all clients stable. So as developer prospective in future I guess oim won't have much to give but as a support or consulting there are many mnc’s to offer you.
Whenever i tried for switch my job, i found almost no competition for me in interview and also i got on an average 100% + hikes, when i did my first switch my hike was 200% , given my one of the biggest MNC in India.
We are happy and proud to say that we have strong relationship with over 700+ small, mid-sized and MNCs. Many of these companies have openings for Oracle Identity Manager. Moreover, we have a very active placement cell that provides 100% placement assistance to our students. The cell also contributes by training students in mock interviews and discussions even after the course completion.
- STarget Resource Reconciliation
- Provisioning
- Trusted Source Reconciliation
- Basic Core Java and Linux will be a plus point, if you plan to move in developer role, otherwise for admin role nothing is required.
- we had started my career from OIM only and i never heard about this IAM technology before, but till now i had setup various project for my clients and worked on various MNCs.
- Learning OIM is really not a tough task,if you get a proper guidance.
- I am an online trainer on OIM and had given several live training, also i had uploaded lots of video on OIM on youtube for free, so you can check it out and learn about OIM from there
Let me assure you that you have really done a wonderful job and OIM does have high demand and let me also assure you all sorts of technologies and products do have demand of talented and dedicated people.
we would suggest you learn core java with beginer + level and learn advanced java concept theoritically.
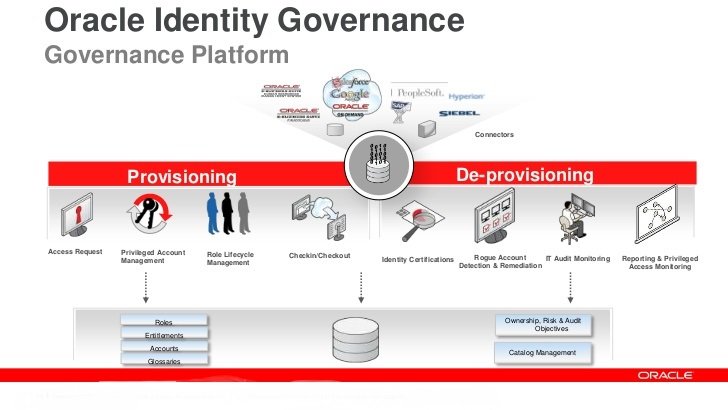
OIM offers wide level of fine grained solutions in Identity and infrastructure managment which includes access management, Audi reporting and lot more.
we will suggest you go through IDM terms and technology and try installing Oracle Identity manager using Oracle’s documentation.
Our course ware is designed to give a hands-on approach to the students in Oracle Identity Manager. The course is made up of theoretical classes that teach the basics of each module followed by high-intensity practical sessions reflecting the current challenges and needs of the industry that will demand the students’ time and commitment.
Yes It is worth , Future will be bright. Bright like a Sun. As I see “Security Domain” is really Biggest concern for any Organisation right from Small size to the Giant like IBM, Microsoft.
If you are looking for switch in domain like Java then you will be having a lot of competition out there. But, if you are having good knowledge in IAM domain then you are in a right path and keep learning more and more not only about the IAM but related technology also like PIM.
I really appreciate you for being carrer oriented and as you have got to this field you must have done lots of research. Yes Idntity and infrastucture management in IT is a emerging and promising fields and there are lots of oppurtinites avilable with handsom perks and there are many more to come.
Oracle Identity Manager, offer customers the first true cloud-based Enterprise class back-office platform for full accounting support leveraging the power of the Cloud Computing paradigm. The advantages are both subtle and significant as the market moves rapidly to embrace this compelling new platform. This eBook will highlight the top 10 factors you should consider when evaluating Oracle Enterprise Resource Planning (ERP) Cloud Financials verses traditional ERP applications such as Oracle E-Business Suite.
The Future of Oracle Identity Management
Identity Management is at the epicenter of digital transformation and the next generation of enterprise IT. The corresponding changes in identity systems and services over the next five years are expected to be as disruptive as the new business models, applications and ecosystems they are supporting
Internet of Things (IoT)
- The Internet is extending its web to include almost anything one can think of: from light bulbs to cars and refrigerators to traffic lights, to sensors monitoring our movements and medical devices.
- IoT will be pervasive in business with real time monitoring and sensors coupled with advanced workflow technologies providing greater efficiencies and responsiveness.
- Almost everything in the physical world can be tagged, accessed, analyzed, connected and, in theory, optimized. These devices can be connected to the Internet and to other individuals and organizations, but there are complex relationships to manage, personal information to protect and a plethora of challenging security concerns.
- Establishing identities for these items and enabling appropriate access for these identities throughout the connected ecosystem is stretching identity to new limits.
Big data and analytics.
- IoT, pervasive social media/data brokering and sophisticated predictive analytic engines drive the hunger for and availability of more and better user data.
- This is further supported by rapid growth of machine The Future of Identity Management Rowe, Nikols, Simmons 8 © 2018 TechVision Research, all rights reserved www.techvisionresearch.com learning to better analyze, correlate and use this data. Big data can also be used to help secure assets and detect anomalies.
- As more data is collected, it must be correlated in new ways to try to better understand trends and intent. This trend is accelerating with no end in sight
Privacy and regulatory controls.
- Both IoT and big data coupled with an increasing thirst to monetize “free” services will continue to push the envelope relative to privacy, which in turn will drive increased push back from individuals and government agencies.
- Legislative and regulatory controls such as GDPR in the EU are increasing the investment in better privacy and data controls.
- Major data breaches coupled with increased government regulations will increase the visibility of and enterprise investment in privacy. Areas such as self-sovereign identity can also support better privacy if properly governed.
Everything moving to the cloud.
- Cloud computing will continue to gain momentum and is the primary means of delivering applications and services to consumers and among businesses.
- Identities are being stored in the cloud and identity services are increasingly cloud-based. Cloud-based applications will also store identity information and will authenticate users.
- Cloud-based services are also supporting the movement to DevOps and microservices.
Wireless and Mobile
- Wireless access is increasingly an expectation in most parts of the world and is shaping the applications for both businesses and individuals.
- Access via mobile devices is becoming the first choice as intelligent phones, tablets and appliances proliferate.
- The advent of mobile has major ramifications for both identity management and security. These trends will accelerate over the next five years with smarter and more powerful mobile devices.
Bring Your Own Device (BYOD)
More and more employees are using their own personal devices rather than corporate-delivered systems to access company business and Internet-based applications and services. BYOD, wireless and mobile means that identification based on static location or a corporate device is no longer a given
Artificial Intelligence (AI) and Machine Learning (ML).
From machine learning to natural language processing, artificial intelligence and cognitive computing are elevating beyond speech recognition and rules-based systems to help organizations consume and derive value from big data and drive decision-making through powerful analytics.
Security Investment, Visibility and Intelligence
Given the increasing numbers of breaches, accessibility to personal data, sophistication of cyber-criminals and corporate risk aversion, security and risk programs are given higher and higher priorities in organizations and for individuals. This acceleration has occurred over the past several years and we expect it to continue to accelerate for the foreseeable future.
DevOps and Microservices.
- Many organizations are moving from the traditional monolithic approach to application development to more “Netflix” like DevOps and Microservices models in which applications are broken down into the most basic services and developers are responsible for not just the development, but also the operational support.
- This type of model is highly scalable and drives more continuous integration and delivery than the monolithic application model that has existed for much of the past 40 years.
- The goal is to provide updates on a daily or weekly basis (as needed) as opposed to waiting for annual (or worse) release cycles.
The Future of Identity Management; Identity as a Utility
- Identity Management needs to become an “Identity Utility”. Much like electricity and water in most modern cities; when you need or want it, the service is there…and it is simple, ubiquitous, and safe to use…like turning a faucet or plugging in an appliance.
- A simple and frictionless experience for the developer, employee, customer or administrator will be critical for the next generation of identity services. Identity as a Utility (IaaU) starts with a reliable and consistent means of collecting, organizing and disseminating data. Since enterprise data generally lives in a multitude of disparate silos, the sharing of data and the orchestration of the changes to the data across these silos has been the traditional cornerstone of many solutions and its roots can be seen in current IAM challenges such as user account provisioning.
- Event triggers, such as changes to authoritative sources of data like Human Resource Management Systems (HRMS), result in the automatic creation of user accounts, assignment of access privileges, and the propagation of user attributes for as many downstream target environments as can exist in an organization.

































