
What is QRadar?
IBM QRadar is an enterprise security information and event management (SIEM) product. It collects log data from an enterprise, its network devices, host assets and operating systems, applications, vulnerabilities, and user activities and behaviors.

IBM QRadar Security Information and Event Management (SIEM) helps security teams accurately detect and prioritize threats across the enterprise, and it provides intelligent insights that enable teams to respond quickly to reduce the impact of incidents. By consolidating log events and network flow data from thousands of devices, endpoints and applications distributed throughout your network, QRadar correlates all this different information and aggregates related events into single alerts to accelerate incident analysis and remediation. QRadar SIEM is available on premises and in a cloud environment.
Key Features:
- Ingest vast amounts of data from on-prem and cloud sources
- Applies built-in analytics to accurately detect threats
- Correlate related activities to prioritize incidents
- Automatically parses and normalizes logs
- Threat intelligence and support for STIX/TAXII
- Integrates out-of-the-box with 450 solutions
- Flexible architecture can be deployed on-prem or on cloud
- Highly scalable, self-tuning and self-managing database
Feature spotlights:
Ingest vast amounts of data from on-prem and cloud sources
Provides insights into on-premises and cloud-based resources and applies business context to that data to maximize relevant threat and risk insights.
Applies built-in analytics to accurately detect threats
Analyzes network, endpoint, asset, user, vulnerability and threat data to accurately detect known and unknown threats that others miss. Built-in analytics help shorten time-to-value without requiring data science experts.
Correlate related activities to prioritize incidents
- Uniquely identifies and tracks related activities throughout the kill chain so analysts can have end-to-end visibility into a potential incident from a single screen.
- Threat intelligence and support for STIX/TAXII
- Includes threat intelligence from IBM X-Force and enables customers to integrate additional threat intelligence feeds of their choice via STIX/TAXII.
Integrates out-of-the-box with 450 solutions
Fosters an ecosystem by providing over 450 out-of-the-box integrations, APIs and an SDK to help customers ingest data faster, gain deeper insights and extend the value of existing solutions.
Flexible architecture can be deployed on-prem or on cloud
Offers multiple deployment options to meet a variety of needs. The solution can be delivered as hardware, software or virtual machines for on-premises or IaaS environments. Start with an all-in-one solution or scale up to a highly distributed model across multiple network segments and geographies.
Automatically parses and normalizes logs
Automatically makes sense of data from disparate sources and provides an easy-to-use editor to quickly on-board custom log sources for analysis.
Threat intelligence and support for STIX/TAXII
Includes threat intelligence from IBM X-Force and enables customers to integrate additional threat intelligence feeds of their choice via STIX/TAXII.
Highly scalable, self-tuning and self-managing database
Enables customers to focus on security operations instead of system management and helps reduce the total cost of ownership. A self-tuning and self-managing database can scale to support the largest organizations without requiring dedicated database admins.
How customers use it:
Complete visibility for traditional and cloud environments
- Problem: Lack of insight across multiple security environments.
- Solution: Gain centralized insight into logs, flow, and events across on premise, SaaS, and IaaS environments
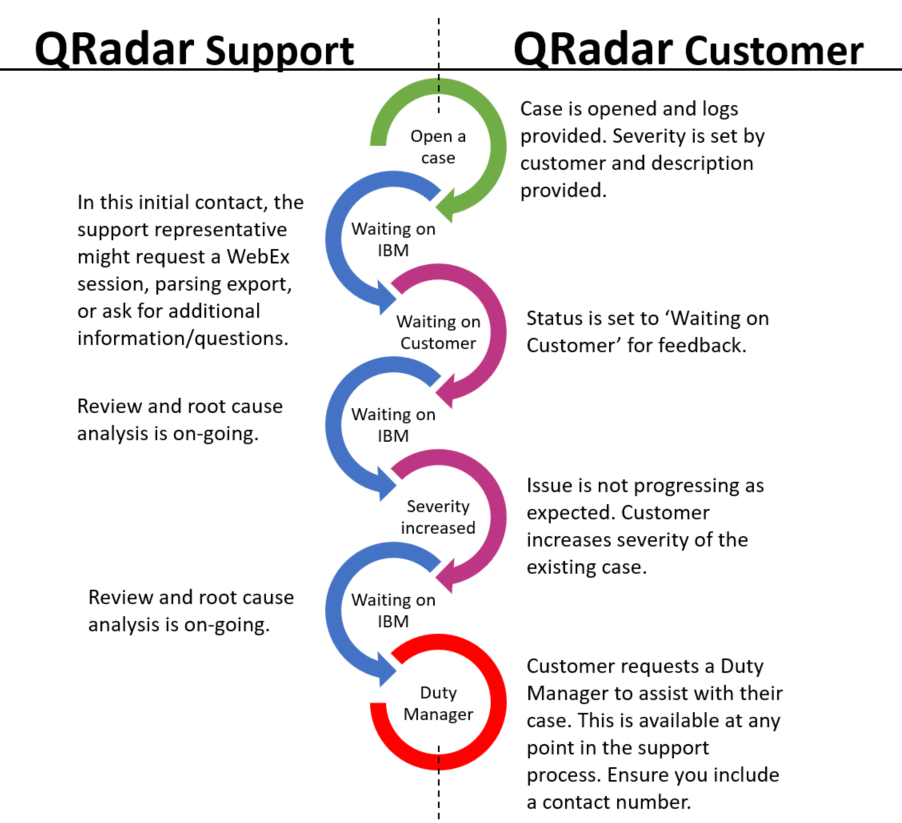
Eliminate manual tasks to empower analysts:
- Problem: Manual tracking processes take up valuable analyst time, and pull analysts away from doing other work.
- Solution: Centrally see all events related to a particular threat in one place, eliminating manual tasks so analysts can focus on investigation and response.
Real-time threat detection:
- Problem: Not enough resources or hours to be constantly watching for threats.
- Solution: Out-of-the-box analytics automatically investigate logs and network flows to detect threats and generate prioritized alerts as attacks progress through the kill chain.
Scalable, centralized and flexible platform:
- Problem: Scaling out your security operations program over time, without requiring major infrastructure changes.
- Solution: Leverage the QRadar ecosystem to easily integrate with other solutions and quickly update capabilities.
Technical details:
Software requirements
Java SDK: IBM Runtime Environment Java Technology edition 7.0.8 Security management: Tivoli Directory Integrator 7.1.7 Browser requirements:
- Google Chrome 43 and future fix packs
- Microsoft Internet Explorer 10 and future fix packs
- Mozilla Firefox ESR 38 and future fix packs
- Hardware requirements
- There is no specific hardware requirements page for this product.
Technical specifications:
QRadar SIEM requires Red Hat Enterprise Linux (RHEL) Server 6.
Evolution of IBM QRadar:
According to IBM, the QRadar Security Information and Event Management is an essential tool that would aid the security teams in prioritizing the threats across the enterprise and detecting them accurately. The tool offers the necessary intelligent insights that would help the teams to respond as quickly as possible and reduce the impact of the incidents. Network flow data and log events from thousands of endpoints, devices, and applications over the network are consolidated.QRadar then correlates all the different information and these related events are compiled to produce single alerts so that remediation and incident analysis can be accelerated. QRadar and SIEM are available on premises and cloud environments.
Significance of IBM QRadar:
IBM QRadar is revolutionizing security integration and is helping organizations all around the world to protect their data. Today product deployments can take place in lots of different scenarios and it is hard for companies to track every pathway. This is where IBM QRadar comes in to help the organizations stabilize their security and protect themselves against potential threats.The following is the significance of IBM QRadar – why it has stood out, despite all the different services offered across the world.
- Comprehensive visibility – The product helps to gain a centralized insight into the data flows, events, and logs on the SaaS (software-as-a-service) and IaaS (infrastructure-as-a-service) environments and on-premises.
- Elimination of manual tasks – All the events in a certain threat can be centrally seen in one place and the expensive manual tracking can be eliminated. Analysts can focus on investigating the matter (security threat), followed by a proper response.
- Easily cater to the compliance protocols – It becomes easier to comply with the international policies and the external regulations that are achieved by leveraging the pre-built reports and templates.
- Real-time threat detection – Out-of-the-box analysis is leveraged that analyzes the network flows and logs automatically and generates proper alerts and the attacks are then directed via the proper kill chain.The IBM QRadar offers the necessary compliance support and situational awareness. A combination of security event correlation, flow-based network knowledge, and assessment-based vulnerability assessment is used by QRadar SIEM.
Aspects of IBM QRadar SIEM:
Let us look at an overview of the important aspects of the IBM QRadar SIEM.
- Log activity – Network events can be monitored and displayed in real time and advanced searches can be performed through the IBM Security QRadar SIEM.
- Assets – QRadar SIEM automatically constructs the asset profiles by using the vulnerability data and passive flow data to discover the hosts and network servers.
- Network activity – The communication sessions between two hosts can be investigated with IBM Security QRadar SIEM.
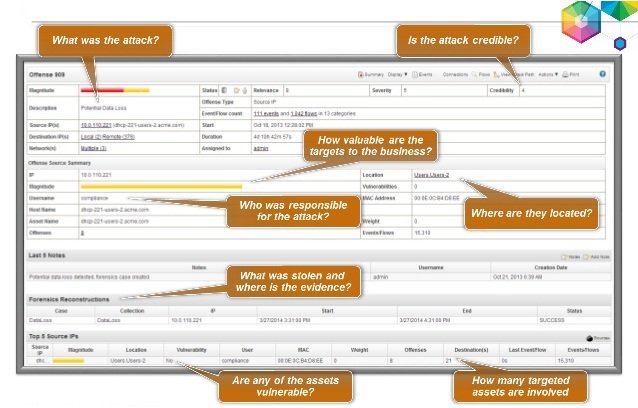
- Offenses – Offenses for security issues can be investigated by QRadar.
- Data collection – Information in various formats is accepted by the QRadar SIEM from a vast category of devices that include network traffic, security events, and scan results.
- Reports – Custom reports and use default reports can be created in IBM Security QRadar SIEM.
- Supported web browsers – A supported web browser needs to be used to access all the features of the IBM Security QRadar.
- Rules – The QRadar SIEM rules are performed on the events, offences, and flows. A response is generated by the rule if all the conditions of a test are met.
What does QRadar SIEM mean?
IBM Security Operations QRadar is an enterprise security information and event management (SIEM) product that can be integrated easily for supervising security workflows. The two workflows that are included in the base system include – Run Enrichment for IP and Security Incident Enrichment.If the Source IP, Configuration Item or Destination IP are modified in a security incident, The REST calls to the second workflow are caused by a business rule. A call would be made for each of the modified fields. Following this, the Security Incident Enrichment workflow would make calls to QRadar depending on the modified fields. QRadar then sends the enriched data to the security incident and populates the work notes with a summary of the event flows and offences related to the IP addresses. The data can be viewed on the QRadar console through the links included in the summary.
IBM QRadar is an enterprise security information and event management (SIEM) product. It collects log data from an enterprise, its network devices, host assets and operating systems, applications, vulnerabilities, and user activities and behaviors.IBM® QRadar® Security Information and Event Management (SIEM) helps security teams accurately detect and prioritize threats across the enterprise, and it provides intelligent insights that enable teams to respond quickly to reduce the impact of incidents.QRadar SIEM is licensed based on Events Per Second (EPS). The starting price for an all-in-one virtual appliance with 100 EPS is $10,700, and the starting price for QRadar on Cloud with 100 EPS is $800/month.Best SIEM Solutions & SIEM Tools. The best Security Information and Event Management (SIEM) vendors are Splunk, LogRhythm NextGen SIEM, IBM QRadar, Securonix Security Analytics, and Netsurion EventTracker. Splunk is the top solution according to IT Central Station reviews and rankings.IBM QRadar is an enterprise security information and event management (SIEM) product. It collects log data from an enterprise, its network devices, host assets and operating systems, applications, vulnerabilities, and user activities and behaviors.
Advantages:
IBM QRadar Security Intelligence Platform advantages
- Provides real-time visibility to the entire IT infrastructure for threat detection and prioritization.
- Reduces and prioritizes alerts to focus security analyst investigations on an actionable list of suspected, high probability incidents.
- Enables more effective threat management while producing detailed data access and user activity reports.
- Operates across on-premises and cloud environments.
- Produces detailed data access and user activity reports to help manage compliance.
- Offers multi-tenancy and a master console to help managed service providers provide security intelligence solutions in a cost-effective manner.
- As an option, this software incorporates IBM X-Force® Threat Intelligence which supplies a list of potentially malicious IP addresses including malware hosts, spam sources and other threats. IBM QRadar SIEM can also correlate system vulnerabilities with event and network data, helping to prioritize security incidents.
- IBM QRadar Security Intelligence Platform advantagesProvides real-time visibility to the entire IT infrastructure for threat detection and prioritization. Reduces and prioritizes alerts to focus security analyst investigations on an actionable list of suspected, high probability incidents.
IBM QRadar Security Intelligence Platform (SIEM)
IBM QRadar SIEM is a highly scalable, enterprise solution that consolidates log source event data from thousands of devices distributed across a network, storing every activity in its database, and then performing immediate correlation and
application of analytics to distinguish real threats from false positives. QRadar SIEM deploys quickly and easily, providing contextual and actionable surveillance across the entire IT infrastructure, helping organizations detect and remediate threats often missed by other security solutions. These threats can include inappropriate use of applications; insider fraud and theft; and advanced, “low and slow” threats easily lost in the “noise” of millions of events.
Best Solution Software Partner Switzerland: InfoGuard gains the IBM Bestseller Award 2017 in the category Best Solution Software Partner Switzerland. We are proud of this award and appreciate IBM’s solutions, which have been surpassed in numerous projects.
QRadar Architecture Overview:
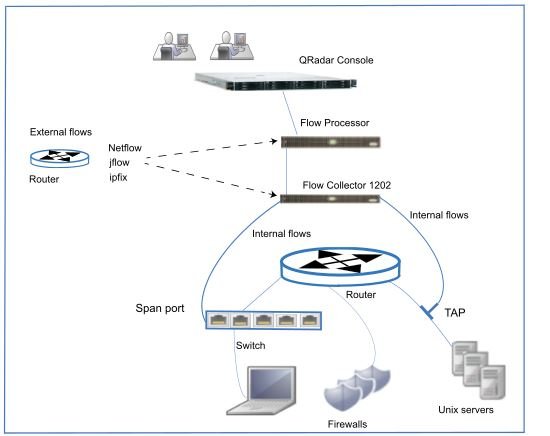
Data Collection:The first layer is data collection where data like flows or events are collected from the network. Direction collection through the All-in-One appliance is possible. Collectors like QRadar QFlow Collectors or QRadar Event Collectors can be used for the collection of event data. The data gets parsed and normalized, and then passed to the processing layer. The parsed data is normalized to present in a usable and structured format.The QRadar SIEM’s core functionality is based on a collection of data and flow. Event data represents those events that occur at a point in time in the environment like firewall denies VPN connections, user logins, emails, proxy connections and other events that should be logged.The flow data, on the other hand, represents network activity information between two hosts. QRadar translates them into flow records. QRadar would normalize and translate the data to IP addresses, packet counts, ports and other information in the flow records. It represents a session between two hosts. Full packet capture is available with the QRadar Incident Forensics in addition to collecting flow information with a Flow Collector.
Data Processing:In the second layer, event and flow data are run through the Customs Rules Engine or CRE. This generates alerts and offences which are written to storage. There are features like QRadar Vulnerability Manager, QRadar Risk Manager, and ORadar Incident Forensics to offer more functionality.
Data Searches:The data collected and processed by QRadar is available to the users for searches, reporting, analysis, and alerts of offence investigation. The users can search and manage the security admin tasks on the QRadar Console
What are the major/primary SIEM tools?:
10 Best SIEM Tools in 2020:
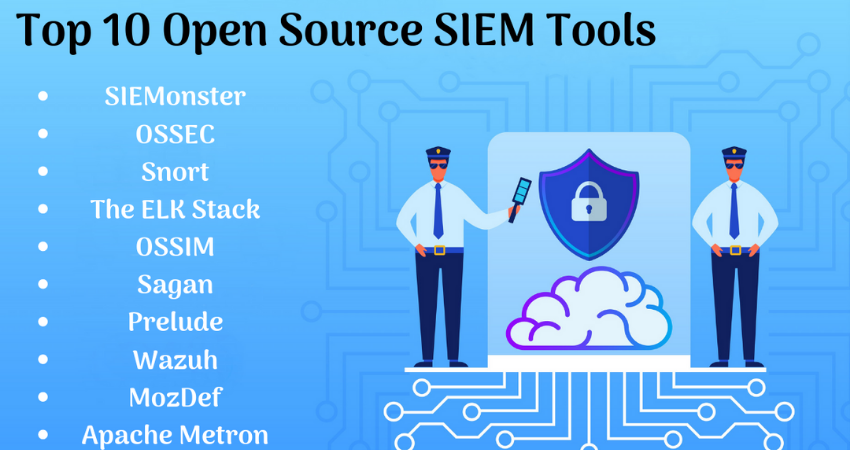
- SolarWinds Security Event Manager – The various tools under IBM QRadar help in the data processing. The major ones are as follows.
- QRadar Vulnerability Manager – The tool scans the process and network vulnerability data. This data is used to identify the security risks in the network.
- QRadar Risk Manager – QRadar Risk Manager collects the network infrastructure configuration and provides a map of the network topology. The data can be used to manage risk by the simulation of network scenarios by implementing rules and altering the configurations in the network.
- Radar Incident Forensics – This tool performs in-depth network forensics and replays full network sessions.
Conclusion:
A stimulating new approach to security, the QRadar Security framework rises to the occasion to provide the expertise, intelligence, and integration Corrington required to detect, set priorities for, and mitigate security breaches.Hope you have found all the details that you were looking for, in this article.






