
UNIX is a robust operating system that supports multiple users and multitasking. Its original design prioritized adaptability and flexibility. UNIX, which is renowned for its durability, features a modular architecture that lets users tailor the environment to their requirements. Widely used hardware platforms are supported by it, and it serves as the basis for numerous other operating systems, including Linux. Because of its characteristics, which include robust security and sophisticated networking capabilities, it is a well-liked option for workstations, servers, and complicated computer environments.
1. What are the introductory factors of a Unix system?
Ans:
The Unix system is erected on three main factors the kernel, the shell, and the train system. The kernel is the core part of the operating system, managing system coffers and tackle. The shell acts as an interface between the users and the kernel, interpreting commands and executing them. The train system organizes and manages lines and directories, allowing users to store and recoup data. Together, these factors give a robust and effective terrain for multitasking and multiuser operations.
2. What’s a process in Unix, and how do you manage it?
Ans:
A process in Unix is a case of a running program, which includes the program law and its current exertion. Processes are managed using commands like ps to list handling processes, kill to terminate a process, and top to view real-time system exertion. Each process has a unique Process ID( PID) and a parent process, creating a scale. Background and focus processes can be controlled using &, fg, and bg commands. Proper process operation is pivotal for maintaining system performance and stability, allowing users to handle multitasking effectively.
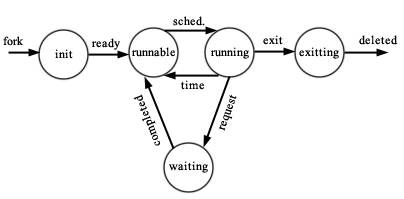
3. What’s the purpose of the’ chmod’ command in Unix?
Ans:
- The chmod( change mode) command in Unix is used to change the train access warrants for users.
- Warrants define the position of access users or a group has to a train or directory, similar to reading, jotting, or executing.
- The command uses emblematic or numeric modes to set these warrants, which are pivotal for system security and managing cooperative work surroundings.
- For illustration, chmod 755 filename subventions read, write, and execute warrants to the proprietor and read and execute warrants to others.
4. How does the’ grep’ command work in Unix?
Ans:
- The grep command in Unix is used for searching straight- textbook data for lines that match a regular expression.
- It stands for” Global Regular Expression publish.” users can specify patterns or strings to search for, and grep will affair the lines from the input that contain these patterns.
- It supports various options, similar to I for a case-asleep hunt,- r for a recursive hunt through directories, and- v to invert the match.
- Grep is an important tool for filtering textbooks and rooting applicable information from large datasets or log lines.
5. What are terrain variables in Unix, and how are they used?
Ans:
Environment variables in Unix are dynamic values that affect the processes and geste of the operating system. They give a way to impact the prosecution terrain of shell sessions and operations. Common terrain variables include PATH, which specifies directories for executable hunt paths; HOME, indicating the users’s home directory; and USER, denoting the current logged-in users.
6. Describe the process of train system mounting in Unix
Ans:
Mounting in Unix refers to the process of making a train system accessible at a certain point in the directory tree. The mount command attaches a train system to a specified directory, known as the mount point, allowing users to pierce lines and directories on different storehouse biases. For illustration, mount/ dev/ sda1/ mnt would attach the train system on the device/ dev/ sda1 to the directory/ mnt. Unmounting, done with the umount command, safely detaches the train system, ensuring that all changes are written to the storehouse device. Mounting is essential for managing and organizing storehouse bias and data in a Unix terrain.
7. Explain the difference between soft links and hard links in Unix.
Ans:
| Aspect | Soft Links (Symbolic Links) | Hard Links |
|---|---|---|
| Type of Link | Creates a separate file that points to the original file’s pathname. | Creates a direct reference to the original file’s inode. |
| Linking Across Filesystems | Can link across different filesystems. | Cannot link across different filesystems. |
| Creation | Created using the ln -s command. | Created using the ln command. |
| Storage | Takes up a small amount of additional storage for the link file. | Does not take up additional storage, just another reference to the existing inode. |
8. What are Unix signals, and how are they used?
Ans:
- Unix signals are software interrupts transferred to a process to notify it of an event, which can be handled or ignored by the process.
- Common signals include SIGINT( intrude, generally from Ctrl C), SIGTERM( termination request), and SIGKILL( forceful termination that can not be caught or ignored).
- Signals are used to control processes, manage exceptions, and applyinter-process communication.
- Commands like kill, trap, and signal are used to shoot and handle signals. Understanding and managing signals is essential for robust process control and graceful arrestment of operations.
9. Explain the purpose and operation of the’ cron’ daemon in Unix.
Ans:
The cron daemon in Unix is used for scheduling repetitious tasks at specified intervals. It reads configuration lines known as crontabs, where users define cron jobs with specific time and date formats. Each line in a crontab train includes timing information and the command to be executed. For illustration, 0 2 * * */ path/ to/backup.sh schedules a backup script to run daily at 2 AM. The cron system helps automate conservation tasks, backups, and other recreating jobs, ensuring they run without homemade intervention.
10. What’s the difference between a chopstick and a superintendent system call in Unix?
Ans:
- The chopstick system call in Unix creates a new process by duplicating the calling process, performing in a parent- child process relationship.
- The new process, or child, gets a unique Process ID( PID) and a copy of the parent’s memory space.
- In discrepancy, the superintendent system call replaces the current process’s memory space with a new program, effectively transubstantiating it into a new process.
- Chopstick is frequently used to produce new processes, while superintendent is used to run different programs within the created processes.
11. What are pipes in Unix, and how are they used?
Ans:
Pipes in Unix are used for inter-process communication, allowing the affair of one command to be used as input for another. This is achieved using the|( pipe) symbol. For case, ls- l| grep’ txt’ lists detailed information about lines and also filters the list for lines containing’ txt.’ Pipes grease the chaining of commands to perform complex tasks efficiently. They’re abecedarian in Unix for erecting important command- line workflows and scripting, enabling users to influence the capabilities of multiple commands in a flawless manner.
12. What’s the difference between a relative and an absolute path in Unix?
Ans:
- In Unix, an absolute path specifies a train or directory position in relation to the root directory, starting with/.
- For illustration,/home/user/docs/file.txt is an absolute path. A relative path, on the other hand, specifies a position relative to the current directory, similar to docs/file.txt if presently in/ home/ users.
- Absolute paths give a clear, unequivocal way to source any position in the train system, while relative paths are more accessible for short references within a known environment.
- Understanding both is pivotal for effective train system navigation and scripting.
13. How do you check fragment operation in Unix?
Ans:
Fragment operation in Unix can be checked using commands like df and du. The df command reports the quantum of fragment space used and available on train systems, furnishing an overview of the storehouse across all mounted filesystems. For illustration, df- h shows fragment operation in a mortal-readable format. The du command, on the other hand, reports the fragment operation of lines and directories, helping identify which directories are consuming the most space.
14. What’s the part of the’ init’ process in Unix?
Ans:
The init process in Unix is the first process started by the kernel at charge time and is the ancestor of all other processes. It has a PID of 1 and is responsible for initializing the system, setting up the terrain, and starting essential services. The init process reads configuration lines like etc inittab to determine which processes to start at different run situations. It plays a critical part in managing system incipiency, arrestment, and the overall lifecycle of processes.
15. What are Unix train warrants, and how are they represented?
Ans:
- Unix train warrants determine the position of access users have to lines and directories.
- They’re represented by a combination of read( r), write( w), and execute( x) warrants for the proprietor, group, and others.
- For illustration, the authorization rwxr- xr– allows the proprietor to read, write, and execute the train, the group to read and execute, and others to only read.
- These warrants are displayed using the ls- l command and can be modified with the chmod command.
- Proper train warrants are essential for system security and controlling access to coffers.
16. What’s the significance of the’ nohup’ command in Unix?
Ans:
- The nohup( no hang up) command in Unix allows a command to continue running in the background indeed after the user has logged out.
- This is particularly useful for long-handling processes that shouldn’t be intruded on by session termination.
- The command is used as a nohup command &, where the affair is generally diverted to a train named out.
- By precluding the dereliction geste of stopping processes when a session ends, nohup ensures that important tasks are completed successfully, making it a precious tool for managing background jobs and maintaining task durability.
17. Explain the use of the discovery command in Unix.
Ans:
The find command in Unix is incredibly protean and is used to search for lines and directories within a train system grounded on various criteria, such as name, size, revision date, and warrants, among others. For illustration, discovery/ home- name” *. txt” would detect all. Txt lines under the/ home directory. This command can also execute conduct on the setup particulars using- superintendent, like deleting lines or changing their warrants.
18. What’s the significance of the/ etc/ passwd train in Unix?
Ans:
The etc/ passwd train in Unix is a critical system train that contains a list of the system’s accounts, furnishing essential user information such as username, UID(user ID), GID( Group ID), full name, home directory, dereliction shell. This train is readable by all users on the system and plays a crucial part in users’ operation. It’s traditionally used for user authentication when paired with etc.
19. How do you manage services in Unix?
Ans:
- Managing services in Unix is generally handled through scripts located in etcinit.d/ or by using newer, more intertwined service operation systems like systems or arriviste.
- Commands like service, systemctl, or chkconfig are used to start, stop, renew, and check the status of services.
- For illustration, systemctl renew nginx would renew the Nginx service, ensuring it reloads its configuration lines.
- Effective operation of services is pivotal for ensuring that the Unix system runs easily and that essential services are always available for users and operations.
20. Describe the part of exchange space in Unix.
Ans:
- Exchange space in Unix acts as a virtual memory extension of a computer’s physical memory( RAM).
- When RAM fills up, less constantly penetrated data can be moved to the exchange space, thereby freeing up RAM for other processes.
- This medium helps prevent the system from running out of memory. Still, penetrating exchange space is slower than penetrating RAM due to its reliance on fragment storehouses.
- Directors can define exchange space during system setup and modify it as demanded using commands like swapon and swapoff.
21. What’s the use of the tail command in Unix?
Ans:
The tail command in Unix is used to display the last part of lines. It’s particularly useful for covering logs in real-time with the f option, which keeps the command open for new lines added to the train, allowing administrators and users to watch the log as it grows. For illustration, tail fvarlogapache2access.log allows a user to see incoming requests on an Apache garçon. This command is necessary for troubleshooting and covering the system, making it an abecedarian tool in a Unix director’s toolkit
22. Explain the conception of job control in Unix.
Ans:
Job control in Unix is a point of the shell that allows users to manage multiple processes or jobs within a single shell interactively. It enables users to suspend the prosecution of a process( using Ctrl Z), renew it in the background( bg command), or bring it to the focus( fg command). This capability is particularly useful when dealing with processes that bear users’ commerce or when starting a long-handling process that the users may wish to detach from temporarily.
23. What are inode figures in Unix?
Ans:
- In Unix, an inode number is a unique identifier associated with each train and directory.
- It’s an essential element of the filesystem that stores metadata about a train or directory, similar to its size, warrants, revision times, and data block pointers.
- The inode number is pivotal for the filesystem as it actually links a train or directory name in a directory to its metadata and data blocks.
- Commands like ls can display inode figures, and understanding inodes is important for tasks similar to filesystem operation and data recovery.
24. How does the Unix train system scale work?
Ans:
The Unix train system is structured as a hierarchical tree where everything starts from the root directory, denoted by a single rent/. Directories can fan out from the root to various subdirectories, such as/ usr for users’ programs,/ caddy for double executables, etc, for configuration lines, and/ home for users’ directories. This structure allows for a systematized storehouse and easy navigation.
25. What are hard links and emblematic links in Unix?
Ans:
In Unix, a hard link is a fresh name for a being trained on the same filesystem, which points directly to the train’s inode. Hard links effectively produce multiple directory entries for the same train data, not enwrapping any fresh fragment space. Again, an emblematic link( or symlink) is a special type of train that points to another train or directory by storing its path. Unlike hard links, symlinks can cross filesystem boundaries and link to directories.
26. What’s the significance of the PATH terrain variable in Unix?
Ans:
- The PATH terrain variable in Unix is pivotal as it specifies directories where executable lines are located and allows users to run programs accessibly without demanding to specify their full paths.
- When a command is entered, the shell searches through the directories listed in PATH in the order they’re specified until it finds the executable.
- Proper operation of PATH can impact system security and users’ convenience, making it vital for system directors to configure it rightly to include all necessary directories and count insecure or gratuitous bones.
27. How can you deflect affairs and input in Unix?
Ans:
- In Unix, affair and input redirection are abecedarian for controlling where affair goes and where input comes from.
- This is done using redirection drivers for turning standard affair, for turning standard input, and for subjoining to a train rather than overwriting it.
- For this case, commandfile.txt will deflect the affair of command tofile.txt.
- These capabilities allow for protean manipulation of data flows in scripts and command-line operations, enabling complex operations similar to piping the affair of one command to another or landing crimes in a separate train.
28. Describe the use and functionality of SSH in Unix.
Ans:
SSH, or Secure Shell, is a protocol used in Unix for securely penetrating network services over a relaxed network. It provides a secure channel over a relaxed network by using a customer- garçon model to authenticate two parties and cipher the data between them. Common uses include logging into systems, executing commands ever, transferring lines using associated SCP or SFTP protocols, and managing networks.
29. What’s a shell script and how is it used in Unix?
Ans:
A shell script in Unix is a train containing a series of commands that the shell executes. It serves as a program for the shell to automate the prosecution of tasks, which could be as simple as diurnal backups or as complex as system monitoring. Shell scripts are written using textbook editors and must be made executable with the chmod command before they can be run. They’re important tools for automating routine tasks and simplifying complex operations into applicable scripts, which increases effectiveness and minimizes the eventuality of mortal error.
30. How do you view and set warrants in Unix?
Ans:
Unix training warrants control over who can read, write, or execute lines. They’re viewed with the ls- l command, which displays warrants in a 10- 10-character string(e.g.,- rwxr- xr–), where the first character indicates if it’s a train( ‘- ’) or directory( ‘ d’). The coming three sets of three characters represent warrants for the proprietor, group, and others independently.
31. How can you ameliorate security on a Unix system?
Ans:
- Perfecting security on a Unix system involves several ways. First, ensure that all users and groups are duly configured and streamlined.
- Regularly modernize the operating system and install software to ensure you have the most reliable security patches.
- Apply a strong word policy and enable multi-factor authentication.
- Use access controls similar to warrants and power to circumscribe access to sensitive lines and directories.
- Install and configure a firewall to block unauthorized network business.
32. How do you list lines in a directory?
Ans:
- To list lines in a directory, you can use the ls command followed by the name of the directory.
- For illustration, the ls path/ to/ directory will list all lines and directories in the specified directory.
- You can also use the ls command without any arguments to list all lines and directories in the current working directory.
- However, similar to retired lines or lines with specific warrants, you can use options like- a or- l with the ls command.
33. How can you list lines with detailed information?
Ans:
To list lines with detailed information, you can use the ls command with the l option. This will display detailed information about each train, including its warrants, proprietor, group, size, and timestamp. For illustration, ls- l/ path/ to/ directory will list all lines and directories in the specified directory with detailed information. You can also use other options like- h to display mortal- readable train sizes or- d to display only directory entries.
34. How do you navigate to parent or root directories?
Ans:
To navigate to parent directories, you can use the cd command followed by the name of the parent directory. For illustration, cd. Will take you to the parent directory of the current working directory. To navigate to the root directory, you can use the cd command. You can also use the pwd command to print the current working directory and also use that information to navigate.
35. How do you view the contents of a train?
Ans:
- To view the contents of a train, you can use a textbook editor like Hardihood or Emacs.
- For illustration, hardihoodfile.txt will open the train in a textbook editor. You can also use a pager, like further or lower, to view the contents of a train one runner at a time, for illustration, furtherfile.txt or lowerfile.txt.
- Alternatively, you can use commands like cat or tail to view the contents of a train in a terminal window, for illustration, catfile.txt or tailfile.txt.
36. How do you navigate to parent or root directories?
Ans:
- To navigate to the parent directory, you can use the cd command followed by the. Memorandum, which refers to the parent directory.
- For illustration, if you’re presently in the/ home/ users/ documents directory, you can navigate to the/ home/ users directory by running cd.
- To navigate to the root directory, you can use the cd command followed by a single rent/, which will take you to the root of the train system
37. How can you cancel a train?
Ans:
In Unix language, there is not a conception of” canceling a train,” as” train” is not a standard Unixterm. However, you can cancel or terminate a process using the kill command If we interpret” train” as a process. First, you need to find the process ID( PID) of the process you want to terminate, which can be done using commands like ps, top, or pgrep. Once you have the PID, you can use the kill command followed by the PID to terminate the process; for illustration, kill 1234. still, you can use kill-9 1234 to strongly terminate it If the process does not terminate with a standard kill command. This sends the SIGKILL signal, which can not be ignored by the process
38. How would you search for a specific pattern or word in a train?
Ans:
To search for a specific pattern or word in textbook data( which might be what you are referring to as a” train”), you can use the grep command. Grep stands for” Global Regular Expression publish,” and it’s used to search through textbooks using patterns. For illustration, to find the word” illustration” in a train named file.txt, you would use grep” illustration”file.txt. This command will return all lines infile.txt that contain the word” illustration.”
39. How can you search for lines by name in a directory?
Ans:
- To search for lines by name in lines within a directory, you can combine the grep command with find.
- However, you can use grep directly with the r( recursive) option If you are looking for lines that contain a specific word within lines in a directory.
- For illustration, grep- r” illustration” path/ to/ directory will search through all lines in the specified directory and subdirectories for lines containing the word” illustration.”
- Alternately, you can use discovery/ path/ to/ directory- type f- superintendent grep” illustration”{}, which finds all lines and also executes grep on each one.
40. How do you produce a directory in UNIX?
Ans:
- To produce a directory in Unix, you use the mkdir command followed by the name of the directory you want to produce.
- For illustration, mkdirmy_directory will produce a directory namedmy_directory in the current working directory.
- However, you can use the p option If you need to produce a nested directory structure.
- For illustration, mkdir- pparent_directory/child_directory will produce the parent directory if it doesn’t live and also produce the child directory inside it.
41. How do you remove a directory?
Ans:
To remove a directory in Unix, you use the rmdir or rm- r commands. The rmdir command is used to remove empty directories. For illustration, rmdirmy_directory will removemy_directory if it’s empty. However, you need to use the rm- r command, which stands for” remove recursively,” If the directory isn’t empty. For illustration, rm- rmy_directory will cancelmy_directory and all its contents, including subdirectories and lines.
42. How do you move or ingrain a train or directory?
Ans:
To move or brand a directory( or train) in Unix, you use the mv command. The mv command stands for” move” but is also used for renaming. For illustration, to brand a directory fromold_name tonew_name, you use mvold_namenew_name. To move a directory to a new position, you specify the current path and the new path mvmy_directory/ new/ path/my_directory. This command effectively changes the position or name of the directory or train.
43. How can you copy lines or directories?
Ans:
To copy lines or directories in Unix, you use the cp command. For copying lines, you use cpsource_filedestination_file. For illustration, cpfile1.txtfile2.txt will produce a dupe offile1.txt namedfile2.txt. To copy directories, you use the r( recursive) option cp- rsource_directorydestination_directory. This command will copy the source directory and all its contents, including subdirectories and lines, to the destination.
44. How would you find the size of a train or directory?
Ans:
- To find the size of a train or directory in UNIX, you can use the du( fragment operation) command.
- For a train, du- h filename provides a mortal- readable size of the train. For a directory, the du- sh directory name gives a summary of the total size of all lines and subdirectories within.
- Also, ls- lh can display the sizes of individual lines in a directory in a mortal-readable format.
- These commands help manage fragment space by relating large lines and directories.
45. How are UNIX train clearances represented?
Ans:
- UNIX train warrants are represented by a combination of characters indicating the read( r), write( w), and execute( x) warrants for the proprietor, group, and others.
- This is frequently seen in a string of ten characters, similar to rwxr- xr–, where the first character indicates the train type(e.g., for a regular train, d for a directory), and the posterior sets of three characters represent the warrants for the proprietor, group, and others, independently.
- Each set of three characters indicates whether read, write, and execute warrants are granted.
46. How do you change train clearances?
Ans:
To change train warrants in UNIX, the chmod command is used. Warrants can be modified using emblematic or numeric( octal) representations. For emblematic changes, chmod u x filename adds execute authorization for the users( proprietor). For numeric changes, chmod 755 filename sets read, write, and execute warrants for the proprietor and read and execute warrants for the group and others. The chmod command provides inflexibility to alter warrants precisely as demanded.
47. How can you change the owner or group of a train?
Ans:
To change the proprietor of a train in UNIX, the chown command is used, followed by the new proprietor’s username and the filename,e.g., the chown new owner filename. To change the group power, chgrp is used also,e.g., chgrp newgroup filename. Alternately, the chown newownernewgroup filename can change both the proprietor and the group in a single command. These commands bear superuser( root) boons to execute.
48. What is the significance of the’ sticky bit’ in clearances?
Ans:
The’ sticky bit’ in UNIX warrants is significant for directories. When set on a directory, it ensures that only the train’s proprietor, the directory’s proprietor, or the root users can cancel or brand the lines within that directory. This is generally used on directories like/ tmp, where multiple users have write access, to help users from deleting or renaming each other’s lines. The sticky bit is represented by a t in the authorization string,e.g., drwxrwxrwt.
49. How can you set the setuid, setgid, and sticky bits using chmod?
Ans:
- To set the setuid, setgid, and sticky bits using chmod, you use numeric canons or emblematic styles.
- The setuid bit is set with chmod 4755 filename, setgid with chmod 2755 filename, and the sticky bit with chmod 1755 filename.
- Symbolically, these can be set with chmod u s filename for setuid, chmod g s filename for setgid, and chmod t filename for the sticky bit.
- These bits modify the prosecution environment of lines and warrants within directories
50. How can you view running processes?
Ans:
- The ps command is generally used to view running processes in UNIX.
- Ps aux provides a detailed list of all running processes with information such as the users, PID, CPU and memory operation, and the command that started the process.
- For a real-time view, the top or top commands can be used, showing active processes and system resource operation stoutly.
- These tools help cover system performance and manage processes effectively.
51. How can you shoot signals to processes?
Ans:
In UNIX, signals are a form of inter-process communication that can be used to control processes. To shoot signals to a process, you use the kill command followed by the signal and the process ID( PID). For illustration, kill- SIGKILL 1234 sends the SIGKILL signal to the process with PID 1234. You can also use signals similar to SIGTERM to request a graceful termination or SIGHUP to renew a process.
52. Explain’ focus’ and’ background’ processes.
Ans:
In UNIX, a” focus” process is one that interacts directly with the users via the terminal. It takes input from the keyboard and sends affair to the screen, generally enwrapping the outstation until it completes or is suspended. A” background” process, on the other hand, runs singly of the outstation’s input and affair. Background processes are initiated by subjoining an ampersand( &) to the command, allowing the users to continue using the terminal for other tasks.
53. What is the’ nice’ value in process operation?
Ans:
- The’ nice’ value in UNIX systems determines the precedence of a process. It’s a numerical value ranging from 20 ( loftiest precedence) to 19( smallest precedence).
- By dereliction, processes start with a nice value of 0. An advanced nice value means the process will get lower CPU time, making it” nicer” to other processes, while a lower value means it’ll get further CPU time.
- The nice command is used to start a process with a specified nice value,e.g., nice- n 10my_command, and the renice command can change the nice value of a formerly running process.
54. How can you change the priority of a running process in UNIX?
Ans:
- In UNIX, you can change the precedence( priority) of a handling process using the renice command.
- The precedence is acclimated by altering the process’s nice value. For case, renice- n 5- p 1234 changes the nice value of the process with PID 1234 to 5, making it less prioritized.
- You need superuser boons to set negative nice values, which increase process precedence.
- Also, processes can be started with a specified nice value using the nice command, like nice- n-10my_command, which startsmy_command with advanced precedence.
55. How can you view running processes?
Ans:
To view running processes in UNIX, you can use the ps command, which displays a shot of current processes. For a more detailed and nonstop update, the top command provides a dynamic real-time view of system processes, including CPU and memory operation. The htop command, an enhanced interpretation of top, offers a more users-friendly interface. Another useful command is pgrep, which searches for processes by name and returns their PIDs. For listing all processes, including those not associated with a terminal, ps aux is generally used.
56. How can you shoot signals to processes?
Ans:
Signals can be transferred to processes in UNIX using the kill command. Each signal has a name and number, like SIGTERM( 15) for termination or SIGKILL( 9) for forcing a process to stop. To shoot a signal, you use kill- SIGNAL PID; for illustration, kill- SIGTERM 1234 or kill-9 1234. The killall command can shoot signals to all processes matching a name, and the pkill command sends signals grounded on process attributes.
57. Explain’ focus’ and’ background’ processes.?
Ans:
- In UNIX, a process can either run in the focus or the background.
- A focused process is one that takes over the terminal, entering input directly from the users and blocking the outstation until it completes.
- This is common for commands that bear users’ commerce. In discrepancy, a background process runs singly of the terminal, allowing the users to continue using the terminal for other tasks.
- Background processes are generally initiated by subjoining an ampersand( &) to the command.
58. What is the’ nice’ value in process operation?
Ans:
- The’ nice’ value in UNIX determines the precedence of a process. It ranges from-20( loftiest precedence) to 19( smallest precedence).
- An advanced’ nice’ value means a lower precedence and vice versa. By dereliction, processes are started with a nice’ value of 0.
- Users can acclimate the’ nice’ value to impact the CPU allocation among processes, generally using the nice or renice commands.
- Conforming the’ nice’ value allows users to insure that further critical processes admit further CPU time.
59. How can you change the priority of a running process in UNIX?
Ans:
In UNIX, the priority( precedence) of a process can be changed using the renice command. This command allows users to acclimate the’ nice’ value of a living process. For illustration, renice 10- p 1234 changes the precedence of the process with PID 1234 to a lower precedence( nice value 10). Only the root users can set negative nice values to increase process precedence. This capability to modify process priority helps in managing system coffers efficiently, ensuring critical tasks have applicable access to CPU time.
60. What is a’ daemon’ in UNIX?
Ans:
A daemon in UNIX is a background process that generally starts at system charge and runs continuously, performing various tasks without direct user commerce. Daemons frequently handle system-position functions similar to logging, cataloging, and network services. Common exemplifications include cron for job scheduling and sshd for handling secure shell connections.
61. How does UNIX handle process operation, and what is a zombie process?
Ans:
- UNIX handles process operations through a structured life cycle, including creation, prosecution, and termination.
- When a process terminates, its exit status is held in a process table entry until the parent process retrieves it using the delay system call.
- However, the terminated process remains in the process table as a zombie’ process If the parent fails to call delay.
- Zombie processes have completed prosecution but still enthrall an entry in the process table.
62. What’ s’ IPC’ in UNIX, and why is it important?
Ans:
- Inter-Process Communication( IPC) in UNIX refers to mechanisms that allow processes to communicate and attend to their conduct.
- IPC is pivotal for the collaboration of multiple processes, enabling data exchange and resource sharing.
- Common IPC styles include pipes, communication ranges, semaphores, and participated memory.
- These tools are essential for developing complex operations where multiple processes must work together, similar to customer- garçon infrastructures and resemblant processing systems.
63. What is Kernel?
Ans:
The kernel is the core element of an operating system, acting as a ground between operations and the tackle. It manages system coffers, including memory, CPU time, and device access. The kernel handles low-position tasks similar to process scheduling, intrude running, and input/ affair operations. In Unix- suchlike systems, the kernel ensures that different programs and users can operate coincidently without snooping with each other.
64. What are the pivotal features of the Korn Shell?
Ans:
The Korn Shell( ksh) is a Unix shell developed by David Korn at Bell Labs. Pivotal features of the Korn Shell include its scripting capabilities, which are more advanced than the Bourne Shell( sh) but compatible with it. It supports erected-in computation operations, associative arrays, and job control. The Korn Shell also offers important command-line editing, with emacs and vi modes, as well as enhanced string manipulation functions.
65. What are some common shells, and what are their pointers?
Ans:
- Common Unix shells include the Bourne Shell( sh), the C Shell( csh), the Korn Shell( ksh), and the Bourne Again Shell( bash).
- The Bourne Shell is known for its simplicity and portability.
- The C Shell, with its C- suchlike syntax, introduces features like job control and history negotiation.
- The Korn Shell combines the features of both Bourne and C Shells, offering enhanced scripting capabilities.
- The Bourne Again Shell( bash) is extensively used in Linux and is compatible with sh while adding advancements like command completion and a rich set of erected- in commands.
66. separate multiuser from multitask.
Ans:
- Multiuser and multitasking are two distinct generalities in Unix systems.
- The multi-user capability allows multiple users to pierce and use the computer system contemporaneously, each with their own individual surroundings and warrants.
- This point is pivotal for waiters and participating systems. Multitasking, on the other hand, refers to the capability of the operating system to execute multiple tasks( processes) at the same time.
- This is achieved by fleetly switching the CPU among tasks, giving the vision of community.
67. What is command concession?
Ans:
Command concession generally refers to the process used in network protocols, similar to Telnet, where the customer and garçon agree on a set of options and capabilities before establishing a communication session. In Unix- suchlike systems, this term can also relate to shell relations where command options and features are determined stoutly. This ensures that both ends of the communication or prosecution process understand and support the same set of commands and options, enabling smooth operation and comity.
68. What is Bash Shell?
Ans:
The Bash Shell( Bourne Again Shell) is an extensively- used Unix shell developed as a free software relief for the Bourne Shell( sh). It incorporates features from the Korn Shell( ksh) and C Shell( csh), furnishing a robust command-line interface for users. Bash offers advancements similar to command-line editing, history, job control, and a rich set of scripting capabilities. It supports command negotiation, functions, and aliases, making it protean for both interactive and automated tasks.
69. Separate the cmp command from the diff command.
Ans:
- The cmp command in Unix is used to compare two lines byte by byte.
- Unlike the diff command, which provides detailed line-by-line differences, cmp is more straightforward, reporting the first differing byte and its position in the lines.
- This makes cmp useful for vindicating whether two lines are identical or for relating the precise position of the first distinction.
- It’s a useful tool for low-position train comparison, especially in double lines where textual differences are less meaningful.
70. What is the use of- l when listing a directory?
Ans:
- The- l option in the ls command in Unix and Unix- suchlike systems stands for” long table format.”
- When you use ls- l, it provides a detailed view of the directory contents, displaying information similar to train warrants, number of links, proprietor, group, size, and the last revision date and time.
- This option is particularly useful for getting a comprehensive overview of train attributes, making it easier to manage and understand the lines within a directory.
71. Why is it not judicious to use root as the dereliction login?
Ans:
Using root as the dereliction login isn’t judicious due to the significant security pitfalls it poses. The root account has unrestricted access to all commands and lines on a Unix system, which can lead to accidental system damage or exploitation by vicious realities. By using privileged user accounts for everyday tasks and reserving root access only for necessary executive functions, the system’s security is enhanced, reducing the threat of unintentional crimes and limiting the implicit impact of security breaches.
72. What is the use of the tee command?
Ans:
The tee command in Unix is used to read from standard input and write to both standard affairs and one or further lines contemporaneously. This is particularly useful when you want to view the affair of a command while also saving it to a train for after analysis. For case, command| teefile.txt allows you to see the affair on the screen and store it in infile.txt. It’s a protean tool for logging, remedying, and covering command affairs without interposing the data inflow.
73. separate cat command from farther command.?
Ans:
- The cat command in Unix concatenates and displays the contents of lines.
- When you want to ensure that cat is executed independently from farther commands, you can use command partitions like; or & & in the shell.
- For illustration, catfile.txt;other_command runs cat first and alsoother_command anyhow of the success of cat.
- Using & &, as in catfile.txt & &other_command, ensures thatother_command runs only if cat succeeds.
74. What is parsing?
Ans:
Parsing in the environment of Unix and programming refers to the process of assaying a string or textbook and breaking it down into its constituent corridor to understand its structure and meaning. This is frequently done by practitioners or compilers to reuse commands, scripts, or data formats like JSON or XML. In Unix, shell parsers interpret and execute command lines entered by the users.
75. What is pid?
Ans:
PID stands for Process Identifier, a unique number assigned by the Unix operating system to every active process. This identifier is pivotal for managing processes, allowing users and the system to keep track of which processes are running, control them, and manage coffers. For illustration, the ps command lists current processes along with their PIDs, and commands like kill use PIDs to terminate specific processes.
76. How does the system know where one command ends and another begins?
Ans:
- In Unix, the shell interprets commands and uses specific characters and syntax to determine where one command ends and another begins.
- Common delimiters include the semicolon(;), which separates multiple commands on a single line, and the newline character, which indicates the end of a command when entered in an interactive shell.
- Also, drivers like & & and|| allow for tentative prosecution of commands grounded on the success or failure of antedating commands.
- The shell’s parsing medium recognizes these delimiters, ensuring correct successional or tentative prosecution of commands.
77. What are Virtual Stations?
Ans:
- Virtual Stations are a conception in UNIX and affiliated systems where software interfaces are used to pretend physical tackle bias.
- They allow systems to interact with virtualized peripherals or remote bias as if they were directly connected to the system.
- This is generally used in artificial robotization, where Virtual Stations can represent detectors, control units, or other tackle over a network.
- By using virtual interfaces, systems can manage and cover remote bias efficiently, reducing the need for physical tackle connections and easing easier conservation and scalability.
78. What is wild-card interpretation?
Ans:
Wildcard interpretation in UNIX refers to the use of special characters in commands to represent one or multiple other characters. The most common wildcards are *,?, and(). The * wildcard matches any number of characters,? matches any single character, and() matches any one of the enclosed characters. This point allows users to perform operations on multiple lines or directories that match a pattern, making train operations more flexible and effective.
79. What is the affair of this command?
Ans:
The” affair” of a UNIX command refers to its function or purpose within the system. Each UNIX command has a specific part, similar to managing lines, recycling textbooks, or controlling system processes. Understanding the affair of a command involves knowing what it does, what arguments or options it accepts, and how it fits into larger workflows or scripts. For illustration, the ls command lists directory contents, grep quests textbook using patterns, and chmod changes file warrants.
80. How do you switch from any user type to a super user type?
Ans:
- To switch from any user type to a superuser type in UNIX, the su( cover users) command is generally used, followed by the username root, like this su- root.
- This command prompts for the superuser’s word and, upon successful authentication, grants the user superuser boons.
- Alternately, if the system is configured with sudo boons, users can execute commands with superuser rights using sudo followed by the asked command.
- For illustration, sudocommand_name executes the command with superuser boons.
81. What is wrong with this interactive shell script?
Ans:
- Determining what is wrong with an interactive shell script without seeing the specific script can involve several common issues.
- These can include syntax crimes, indecorous running of user inputs, lack of error checking, or incorrect operation of commands.
- An interactive script should precisely manage input and affairs, validate inputs to help unanticipated geste and give clear instructions to the users.
- Remedying an interactive shell script involves checking for these issues, ensuring that all variables are rightly assigned, and vindicating that control structures like circles and conditionals serve as intended.
82. What is a single-user system?
Ans:
A single-user system in UNIX is a mode of operation where only one user has access to the system, generally for conservation or troubleshooting purposes. This mode is frequently used during system repairs, updates, or recovery processes to ensure that no other users or processes can intrude. In single-user mode, the system generally thrills into a minimum terrain with essential services running, and the root users are automatically logged in.
83. What is the FIFO?
Ans:
FIFO, which stands for First In, First Out, is a type of special train in UNIX used for inter-process communication( IPC). It’s also known as a named pipe. Unlike regular pipes, which are unnamed and live only as long as the processes using them are running, FIFOs have a name in the filesystem and persist beyond the life of the process. They allow data to be read in the order it was written, ensuring orderly communication between processes.
84. What is meant by Super users?
Ans:
- Super users, generally known as root users, are privileged users with unrestricted access to all commands and lines in a UNIX system.
- They can perform any executive task, such as modifying system configurations, managing user accounts, and installing software.
- Super users have the capability to bypass train warrants, making them essential for system conservation but also posing a security threat if misused.
- Ensuring that only trusted individuals have super user access is pivotal for system security. The sudo command is frequently used to grant temporary super users boons to regular users.
85. What are the various IDs in UNIX processes?
Ans:
- UNIX processes have several identifiers the Process ID( PID), Parent Process ID( PPID), users ID( UID), and Group ID( GID).
- The PID uniquely identifies each process, while the PPID identifies the parent process that spawned it.
- The UID represents the users who own the process, and the GID indicates the primary group of users.
- These IDs are pivotal for process operation and security, ensuring that processes operate within the warrants and coffers allocated to their separate users and groups.
86. Explain the advantage of executing processes in the background?
Ans:
Executing processes in the background allows users to continue using the command line without staying for the process to complete. This is particularly useful for long-handling tasks, as it frees up the terminal for other commands. Background processes can be started by subjoining an ampersand( &) to the command. Users can cover and control these processes using commands like jobs, fg, and bg. This capability enhances multitasking and productivity, especially in a multi-user terrain.
87. What is the explanation for protection fault?
Ans:
A protection fault, also known as a segmentation fault or segfault, occurs when a process attempts to pierce a memory position that it’s not allowed to. This can be due to various reasons, such as dereferencing a null or invalid pointer, buffer overflow, or penetrating memory outside its allocated range. The operating system intervenes to prevent the process from corrupting memory or crashing other processes. Protection faults are critical for maintaining system stability and security, as they help insulate defective processes.
88. Describe the generality of “ Region ”?
Ans:
- In UNIX, a” region” refers to a conterminous block of virtual memory allocated to a process.
- Each process has regions for different parts like textbooks ( law), data, and mounds.
- These regions help in effective memory operation and protection, as each region can have different access warrants( read, write, execute). The operating system manages these regions through mechanisms like paging and segmentation.
- Regions also grease sharing of memory, similar as participated libraries among multiple processes.
89. What is meant by user area(u-area,u-block)?
Ans:
- The user’s area (u-area or block) is a data structure in UNIX that contains information specific to a process, similar to user credentials, open train descriptors, and process control information.
- It’s maintained in the kernel space but specific to each process, ensuring that each process has its own separateu-area.
- This structure is pivotal for process operation, as it allows the kernel to efficiently switch surrounds between processes and maintain process-specific state and data.
90. Explain Superblock in UNIX.
Ans:
The Superblock is a critical data structure in UNIX train systems, containing metadata about the train system, similar to its size, block size, and status. It’s located at a fixed position on the fragment, generally in the morning of the train system. The Superblock also holds information about the free space and inodes, enabling the train system to manage the storehouse efficiently. Corruption of the Superblock can render the train system unworkable, which is why backups of the Superblock are frequently maintained.






