
Because of its open-source nature, reliability, and security, Linux is a popular and adaptable operating system. Servers, supercomputers, cellphones, embedded systems—a wide range of gadgets—are powered by it. With Linux, users have more freedom and control over their computer environments thanks to its broad ecosystem of tools and software. For both home users and businesses looking for dependable and adaptable solutions, Linux is the favored option due to its collaborative development philosophy, which encourages innovation and guarantees continual improvement.
1. What is the Difference between UNIX and Linux?
Ans:
UNIX is an operating system first developed by AT&T’s Bell Labs; Linux is a free and open-source operating system kernel created by Linus Torvalds. UNIX systems are generally used in large enterprise surroundings and come with different personal performances like A.I.X., H.P. UX, and Solaris. In discrepancy, Linux has multitudinous distributions( distros) similar to Ubuntu, CentOS, and Fedora, which feed to different users’ requirements.
2. Define the Linux train system scale.
Ans:
The Linux train system scale is organized as a tree structure with the root directory( ) at the base. crucial directories include caddy( essential command binaries), etc( configuration lines), home( users home directories), var( variable data like logs), tmp( temporary lines), usr( users serviceability and operations), and lib( participated libraries). Each directory has a particular purpose, which helps maintain a standardized terrain and facilitates system administration.
3. What are inodes in Linux?
Ans:
- Inodes( indicator bumps) are data structures on a filesystem that save information about lines and directories, banning the train name and factual data content.
- Each inode contains metadata similar to the train’s size, warrants, power, timestamps, and pointers to the data blocks where the train’s contents are stored.
- When a train is generated, a unique inode is assigned to it.
- The train name is saved in a directory entry points to the corresponding inode.
4. How does the Linux kernel manage memory?
Ans:
- The Linux kernel manages memory through a combination of virtual memory and physical memory operation ways.
- It uses paging to produce an abstraction of an ample virtual address space, which is also counterplotted to physical memory through runner tables.
- This allows for effective memory operation and protection.
- The kernel employs a demand paging medium, where runners are loaded into memory only when demanded, and it uses a runner relief algorithm to change out runners to fragment( exchange space) when physical memory is exhausted.
5. What’s a Linux shell, and how does it work?
Ans:
A Linux shell is a command line interface that allows the users to interact with an operating system by codifying commands. It acts as a command practitioner, rephrasing users’ input into conduct performed by the system. Common types of shells include Bash( Bourne Again Shell), which is the dereliction on numerous Linux distributions, as well as other variants like Zsh, Ksh( Korn Shell), and Tcsh.
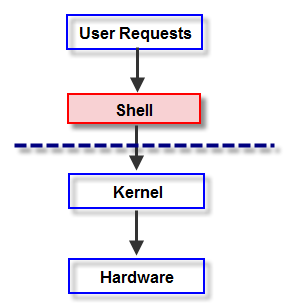
6. Explain the conception of a Linux distribution.
Ans:
A Linux distribution( distro) is a packaged interpretation of the Linux operating system, which includes the Linux kernel, GNU tools, libraries, fresh software, attestation, and a package operation system. Distros are acclimatized for various purposes, ranging from general desktop use to technical garçon surroundings. Popular distributions include Ubuntu, Fedora, Debian, and CentOS, each immolation with unique features and support options.
7. What’s the purpose of the root account in Linux?
Ans:
- The root account in Linux is the super user account with unrestricted access to all commands and lines on a system.
- This account is used for system administration tasks, such as installing and configuring software, managing system settings, and modifying user warrants.
- Because of its expansive boons, using the root account requires caution to avoid unintentional system damage or security vulnerabilities.
- DirectorsDirectors frequently use the’ sudo’ command to perform executive tasks, granting temporary root boons to regular users to enhance security.
8. Describe the function and benefits of the package directory in Linux.
Ans:
- Package directors are essential tools in Linux for installing, streamlining, and managing software packages.
- They handle dependencies, ensuring that all necessary factors are present for software to serve rightly.
- Famous package directors include A.P.T. for Debian-grounded systems and YUM or D.N.F. for Red Hat-grounded systems.
- Package directors streamline the process of maintaining software, furnishing a centralized way to gain and modernize programs, enhancing security through managed updates, and reducing the threat of conflicts between packages.
9. What are some common train warrants in Linux, and how are they used?
Ans:
In Linux, train warrants determine the access position that users have to lines and directories. There are three types of warrants: read( r), write( w), and execute( x), which can be assigned to the train proprietor, Group, and others. These warrants are represented numerically(e.g., 755) or symbolically(e.g., rwxr xr x). Commands like’ chmod’ are used to modify warrants, while’ chown’ changes train power.
10. Explain the difference between hard links and symbolic links in Linux.
Ans:
| Aspect | Hard Links | Symbolic Links |
|---|---|---|
| Definition | Multiple directory entries pointing to the same physical file location | Special files containing paths to target files or directories |
| Inode | Share the same inode with the original file | Have their own inode |
| Effect of Original File Deletion | Hard links remain intact as they directly reference the data | Symbolic links become broken if the target file is deleted |
| Cross-Filesystem Linking | Cannot span filesystems or partitions | Can span filesystems and partitions |
11. What are symbolic links in Linux, and how are they created?
Ans:
- Emblematic links, or symlinks, are particular types of lines in Linux that act as pointers to other lines or directories.
- They’re analogous to lanes in Windows and are created using the ln s command.
- For illustration, the ln s path to the original path to the link creates a symlink named” link” pointing to the original train or directory.
- Symlinks are helpful in simplifying train system navigation, managing train performances, and maintaining comity with scripts and programs awaiting lines in specific locales.
12. What methods manage services in Linux?
Ans:
In Linux, services( also known as daemons) are managed using various tools depending on the init system in use. For systems using systemd, the systemctl command is employed to start, stop, renew, enable, and turn off services. For this case, systemctl launch httpd starts the Apache web garçon, while systemctl enable httpd ensures it begins at a charge. Aged systems using SysVinit manage services with commands like service and chkconfig.
13. What’s the part of the etc directory in Linux?
Ans:
The etc. directory in Linux is pivotal as it contains systemwide configuration lines and directories. It hosts configuration lines for system services, operations, and the operating system itself. Exemplifications include:
- A password for users’ account information.
- A fstab for train system mounts.
- SSH sshd_config for SSH garçon settings.
The thickness and association of lines within, etc., ensure that system directors can fluently detect and modify configuration settings. Proper operation of this directory is essential for system stability, security, and smooth operation, as incorrect configurations can lead to system malfunctions or vulnerabilities.
14. What techniques check fragment operation in Linux?
Ans:
Fragment operation in Linux can be checked using various commands. The df command displays the fragment space operation of train systems, furnishing an overview of the available and habituated space in each mounted train system. The du command, on the other hand, reports the fragment operation of lines and directories, offering a detailed view of how space is being employed within a specific directory.
15. How does process operation work in Linux?
Ans:
Process operation in Linux involves creating, cataloging, and terminating processes. Each process has a unique Process ID(P.I.D.) and can be managed using commands like ps, top, top, kill, and friendly. The ps command lists running processes, while top and top give dynamic, real-time views of system exertion. To terminate processes, kill sends signals like S.I.G.K.I.L.L. or S.I.G.T.E.R.M. to a specified P.I.D.
16. What’s a cron job, and how do you manage it?
Ans:
- A cron job is a listed task in Linux that runs at specified intervals using the cron daemon.
- These tasks are defined in crontab lines, which determine the timing and the command to execute.
- Users can edit their crontab entries using the crontab e command.
- The format includes fields for nanoseconds, hours, day of month, month, day of week, and the command. For illustration, 0 2 * * * path to the script.sh schedules a script to run daily at 2 AM.
17. What’s the significance of the var directory?
Ans:
- The var directory in Linux is critical as it stores variable data that changes as the system is running.
- This includes system logs( var log), packages and database storehouse( var lib), spools( var spool), and temporary lines demanded between reboots( var tmp).
- Unlike tmp, which is frequently cleared at charge, var tmp retains data longer.
- Var is essential for maintaining system logs that help in troubleshooting and auditing, storing patient data demanded across system reboots, and casing temporary lines used by ongoing processes.
18. What’s the purpose of the cron daemon in Linux?
Ans:
The cron daemon in Linux is a time-grounded job scheduler that allows users and directors to automate repetitive tasks. By defining jobs in crontab lines, users can record commands or scripts to run at specified intervals, similar to diurnal, daily, or yearly. Each user has a particular crontab train, and the system has its crontab for systemwide tasks. This robotization is essential for routine conservation tasks, backups, and system monitoring, enhancing effectiveness and ensuring tasks are performed constantly.
19. Explain the concept of runlevels in Linux.
Ans:
Runlevels in Linux define the state of the machine, specifying which services and processes should be running. Traditional SysVinit systems use run levels numbered 0 to 6, where 0 is for system halt, 1 is for single-user mode( conservation), 3 is for multi-user mode with networking, 5 includes a graphical interface, and 6 is for rebooting the system. With the arrival of systems, run levels have been replaced by targets, which give further inflexibility.
20. What approaches cover system performance in Linux?
Ans:
- Monitoring system performance in Linux involves using various tools to track resource operation and system health.
- Commands like top and htop give real-time views of CPU, memory, and process exertion. vmstat offers reports on system processes, memory, paging, block I.O., and CPU exertion.
- The iostat command is used to cover input affair statistics for bias and partitions. For network performance, netstat and ifstat are helpful.
21. What’s the purpose of the proc directory in Linux?
Ans:
- The proc directory in Linux is a virtual train system that provides a window into the kernel and system processes. It contains lines and directories representing system and process information, which are stoutly generated by the kernel.
- For illustration, proc cpuinfo provides details about the CPU; proc meminfo shows memory operation statistics, and proc ( pid) directories contain information about individual processes.
- This pseudo-filesystem is essential for system monitoring and debugging, allowing directors and tools to pierce real-time system data without demanding to pierce tackle directly.
22. What steps manage user accounts in Linux?
Ans:
Managing user’s accounts in Linux involves using various commands and tools to add, modify, and cancel users. The useradd command creates new user accounts, while usermod modifies being bones. The passwd command sets or changes users’ watchwords, ensuring account security. Users’ information is stored in etc. passwd, while word hashes are in etc. shadow. The groupadd, groupmod, and groupdel commands manage user groups, easing authorization control.
23. What’s the function of the grep command in Linux?
Ans:
The grep command in Linux is used for searching textbooks within lines grounded on patterns. It stands for” global regular expression print” and is protean mainly due to its support for regular expressions. For illustration, grep” error” var. Log. yslog quests for the word” error” in the syslog train. Options like i for case-insensitive hunt, r for recursive hunt through directories, and v for flipping the match enhance its functionality.
24. What are Linux train warrants, and how do they work?
Ans:
- Linux train warrants determine the position of access users have to lines and directories.
- Each train has three sets of warrants: proprietor, Group, and others, each with read( r), write( w), and execute( x) warrants.
- These warrants are displayed using ls l and can be modified with chmod.
- For illustration, chmod 755 train sets the train to be readable and executable by everyone but writable only by the proprietor.
25. What procedures set environment variables in Linux?
Ans:
- Environment variables in Linux are used to define settings that affect the geste of processes.
- They can be set temporarily using importVARIABLE_NAME = value for the current session or permanently by adding the import statement to shell configuration lines. bashrc or. Profile.
- Environment variables similar to PATH, HOME, and USER are essential for system operations, impacting where the system looks for executables, the users’s home directory, and the current user’s name.
26. What’s the ps command used for in Linux?
Ans:
The ps command in Linux is used to display information about active processes. By dereliction, ps shows processes running in the current terminal session, but it can be customized with options like ps aux to display all processes along with their CPU and memory operation. The command provides:
- Details similar to process I.D.s (P.I.D.s).
- The users are running the process.
- CPU and memory operation.
- The command that started the process.
27. What’s the difference between the cp and mv commands in Linux?
Ans:
The cp( dupe) and mv( move) commands in Linux are used for train manipulation—the cp command clones lines or directories from one position to another, leaving the original complete. For illustration, cpsource.txtdestination.txt clonessource.txt todestination.txt. The mv command, on the other hand, moves lines or directories to a new position, effectively renaming or shifting them. For this case, mvoldname.txtnewname.txt renames the train.
28. How does the find command work in Linux?
Ans:
The find command in Linux is an important tool for searching for lines and directories grounded on various criteria, such as name, size, revision time, and warrants. The introductory syntax is find( path)( options)( expression), where the path specifies the directory to search in. For illustration, find the home name” *. txt” quests for all textbook lines within the home directory. Advanced options allow conduct to be taken on set-up lines, similar to deleting( cancel), executing commands( superintendent), or publishing paths( print).
29. Explain the function of the chmod command in Linux.
Ans:
- The chmod command in Linux is used to change the warrants of lines and directories.
- Warrants can be modified symbolically(e.g., chmod u x train to add execute authorization for the proprietor) or numerically(e.g., chmod 755 train to set read, write, and execute warrants for the proprietor, and read and execute warrants for others).
- Rightly setting warrants is pivotal for system security, as it controls who can read, write, or perform a train.
30. What’s the sudo command, and why is it essential in Linux?
Ans:
- The sudo command stands for superuser do and allows the users to execute a command as the superuser or another user, as specified by the security policy.
- This is pivotal for performing executive tasks without logging in as the root users, therefore minimizing the pitfalls associated with root access.
- For illustration, the sudo apt-get update updates the package lists for packages that need elevation.
- The use of sudo is logged, furnishing an inspection trail of executive conduct.
31. What’s the purpose of the navigator command in Linux?
Ans:
The navigator command in Linux is used to produce, maintain, modify, and excerpt lines from libraries. The name stands for” tape recording library,” and it supports various operations on tarball lines( compressed library lines). Joint operation includes navigator cvfarchive.tar path to the directory to produce a library and navigator xvfarchive.tar to prize it. Tarballs can also be compressed using flags like z for gzip, which is essential for backup, distribution, and association of lines, enabling effective storehouse and transfer of multiple lines in a single library.
32. What commands search for a specific text in lines using Linux?
Ans:
The grep command is extensively used to search for specific textbooks within lines in Linux. Grep stands for global regular expression print and can search through lines and directories for lines matching a given pattern. For case, grep error var log syslog quests for the word error in the syslog train. Options like r for a recursive hunt in directories and I for a case-insensitive hunt extend its capabilities.
33. What’s the df command used for in Linux?
Ans:
- The df command in Linux stands for” fragment filesystem” and is used to display the quantum of fragment space available on the train system.
- Running df h provides a human-readable format showing the size, use, and available space on each training system.
- This command is pivotal for covering fragment operations, helping directors manage storehouses, and helping fragment space prostration.
- Regular use of df aids in visionary conservation, ensuring sufficient space for operations and users and precluding issues related to entire disks, which can lead to system performance declination or service outages.
34. What methods compress and decompress files in Linux?
Ans:
- In Linux, lines are compressed and mellowed using various commands like gzip, bzip2, and zip. The gzip command compresses lines into.
- X format, with gzip train creatingfile.gz and gunzipfile.gz relaxing it. bzip2 works also, producing. bz2 lines, while bunzip2 decompresses them.
- The zip command compresses lines into. Zip format, suitable for transferring multiple lines together, and unzip excerpts them.
- These tools are essential for effective storehouse, transfer, and operation of lines, especially when dealing with large datasets or demanding to conserve fragment space.
35. What’s the iptables command, and how is it used?
Ans:
The iptables command in Linux is a userspace mileage program that allows directors to configure the I.P. packet sludge rules of the Linux kernel firewall. It’s used to set up, maintain, and check the tables of I.P. packet sludge rules. The rules are organized into chains and tables, where each chain corresponds to a specific point during packet processing(e.g., INPUT, Affair, FORWARD).
36. What’s the purpose of the top command in Linux?
Ans:
- A dynamic, real-time view of the system’s processes.
- Showing information similar to CPU operation.
- Memory operation.
- Process details.
By dereliction, it lists the most CPU-intensive tasks at the top. It’s helpful in covering system performance and relating processes that consume inordinate coffers. The interface is interactive, allowing users to sort processes, kill processes, and change display options.
37. What is the process for using the ‘scp’ command to transfer files between Linux systems?
Ans:
The scp( secure dupe) command in Linux is used to transfer lines and directories between hosts over a network securely. It utilizes S.S.H. ( Secure Shell) for data transfer and provides encryption for both the training content and login credentials: txtuser@remote, host path to destination clonesfile.txt to the specified directory on the remote host. Also, scpuser@remote, the host path tofile.txt, the original destination, clones a train from the remote host to the original machine.
38. What’s a Linux kernel module, and how can you manage it?
Ans:
A Linux kernel module is a piece of law that can be loaded into the kernel at runtime to extend its functionality, similar to device motorists or system calls. These modules can be managed using commands like insmod to fit a module, rmmod to remove it, and lsmod to list all presently loaded modules. For illustration, sudo insmodmymodule.ko loads a module named module.
39. What’s the awk command, and how is it used?
Ans:
- The awk command in Linux is an essential text-processing tool used for pattern scanning and processing.
- It can be used to prize and manipulate data from textbook lines and strings.
- For illustration, awk'{ publish$ 1,$ 3}’ file.txt prints the first and third fields of each line infile.txt.
- Awk scripts can perform complex data manipulations, making them ideal for tasks like report generation, data birth, and metamorphosis.
40. How does the rsync command work, and what are its advantages?
Ans:
- The rsync command in Linux is used to transfer and coincide lines and directories between two locales efficiently.
- It uses a delta transfer algorithm, which only transfers the changed corridor of lines, reducing data transfer and perfecting speed.
- The introductory syntax is rsync avz source destination, where a is for library mode, conserving warrants and timestamps, v for the circumlocutory affair, and z for contraction during transfer.
- Rsync supports remote and original synchronization, making it ideal for backups, mirroring, and incremental train transfers.
41. What’s the netstat command used for in Linux?
Ans:
The netstat command in Linux displays network statistics, including active connections, routing tables, affiliate statistics, feint connections, and multicast enrollments. For illustration, netstat turn lists all harkening anchorages and their associated services. This command helps directors monitor network performance, troubleshoot network issues, and ensure that the system’s network interfaces and services are performing correctly.
42. What’s the vi editor in Linux, and how is it used?
Ans:
The vi editor in Linux is a vital textbook editor that’s extensively used for editing configuration lines and writing law. It operates in two primary modes: command mode for navigating and manipulating textbooks and fit mode for editing textbooks. Users can switch between these modes by pressing keys similar to I to enter insert mode and Esc to return to command mode. Basic commands include w to save changes, q to quit, and wq to save and quit.
43. Explain the use of the chown command in Linux.
Ans:
- The chown command in Linux is used to change the power of lines and directories.
- It allows users to modify both the proprietor and the Group associated with a train.
- For illustration, the chown user group filename changes the proprietor of the train to users and the Group to Group.
- Power operation is pivotal for security and access control, ensuring that only authorized users can pierce or modify sensitive lines.
44. What steps produce new users in Linux, and which files are modified?
Ans:
- Creating a new user in Linux involves using the useradd command, followed by a password, to set the user’s word. For illustration, a user adds a new user, creates a new user named a new user, and passes the new user their word.
- This process updates several lines, including Passwd for storing users’ account information, Shadow for storing word hashes securely, and Group for managing group enrollments.
- Understanding these lines is essential for system administration, as it allows directors to manage users’ accounts and warrants effectively, ensuring system security and user association.
45. What’s the nohup command, and how is it used?
Ans:
The nohup command in Linux stands for no hang-up and allows processes to continue running in the background indeed after the users have logged out. This is useful for long-running tasks that need to persist singly in user sessions. For illustration, nohup commands & runs the command in the background, turning its affair Donohue out by dereliction.
46. What commands are used with the `kill` command in Linux?
Ans:
The kill command in Linux is used to terminate processes. It sends signals to processes linked by their process I.D.s (P.I.D.s). The most common signal is S.I.G.T.E.R.M. ( dereliction), which gracefully asks a process to terminate, and S.I.G.K.I.L.L., which firmly stops it. For illustration, kill 1234 sends the S.I.G.T.E.R.M. signal to the process with PID 1234, while kill 9 1234 sends the S.I.G.K.I.L.L. signal.
47. What’s the mount command, and how is it used in Linux?
Ans:
- The mount command in Linux is used to attach train systems to a specified directory, making them accessible to the users.
- For this case, mount dev sdb1 mnt mounts the train system on dev sdb1 to the mnt directory.
- This command supports various train system types and options, enabling the integration of different storehouse biases and network shares.
- Proper use of the mount command is pivotal for penetrating the external storehouse, managing fragment partitions, and ensuring the system’s inflexibility in handling different train systems.
48. What commands check the running kernel version in Linux?
Ans:
- The name r command is used to check the kernel interpretation of the running kernel in Linux.
- This command labors the kernel release number, similar to 5.4.042 general, which provides information about the specific kernel interpretation presently in use.
- Understanding the kernel interpretation is essential for system administration tasks similar to troubleshooting, ensuring comity with software and tackling, and applying applicable security patches and updates.
49. What methods handle package management in Debian-based systems?
Ans:
In Debian-based systems, package operation is handled using the apt and dpkg tools. The apt( Advanced Package Tool) suite, including commands like apt-get and apt, provides a high-level interface for installing, streamlining, and removing packages. For illustration, sudo apt-get update updates package lists, and sudo apt-get install package name installs a new package. dpkg works at a lower position and is directly manipulated.
50. What’s the systemctl command, and how is it used to manage services?
Ans:
The system command in Linux is used to manage system services, which are responsible for starting, stopping, and working system services and daemons. For illustration, systemctl launch httpd starts the Apache HTTP garçon, while systemctl stop httpd stops it. systemctl enable httpd ensures the service starts automatically at a charge, and systemctl status httpd checks its status.
51. What techniques check for fragmented files in Linux?
Ans:
- To check for fragment crimes in Linux, the fsck( train system check) command is used.
- This mileage checks and repairs train system inconsistencies and crimes on disks.
- For illustration, sudo fsck dev sda1 checks and repairs the train system on the dev sda1 partition.
- It’s important to unmount the train system or run the check-in single-user mode to help prevent data corruption.
52. What’s the purpose of the journalctl command in Linux?
Ans:
- The journalctl command in Linux is used to query and display logs from the systemd journal, which is a centralized logging system.
- It allows users to view logs for the entire system, specific services, or time frames.
- For illustration, journalctl you ssh displays logs for the S.S.H. service, and journalctl since” 1 hour ago” shows logs from the one hour.
- This command provides necessary filtering and searching capabilities, enabling effective troubleshooting and monitoring of system events.
53. What procedures manage disk partitions in Linux?
Ans:
Managing fragment partitions in Linux can be done using tools like fdisk, parted, and gparted. Fdisk is a command line mileage for creating and modifying partitions on a hard drive. For illustration, sudo fdisk dev sda opens the partition table for dev sda, allowing users to produce, cancel, or modify partitions. Parted is another command line tool that supports both MBR and G.P.T. partition tables.
54. Explain the purpose and operation of the diff command in Linux.
Ans:
The diff command in Linux is used to compare the contents of two lines line by line. It highlights the differences between the lines, showing which lines have been added, deleted, or changed. For illustration, difffile1.txtfile2.txt labors the differences betweenfile1.txt andfile2.txt. This command is essential for inventors and system directors to identify changes in configuration lines, source law, or any textbook lines.
55. What’s the umask command, and how is it used in Linux?
Ans:
- The mask command in Linux sets the dereliction train creation warrants for new lines and directories.
- It specifies which authorization bits should be masked out or removed. For illustration, unmask 022 means new lines will have warrants 644( rwrr) and directories 755( rwxrxrx).
- The mask value is decreased from the dereliction warrants( 666 for lines and 777 for directories).
- Setting umask rightly is essential for security and access control, ensuring that new lines and directories have the applicable warrants to protect sensitive data from unauthorized access.
56. What’s the uptime command, and what information does it give?
Ans:
The uptime command in Linux provides information about how long the system has been running, along with the current time, number of users logged in, and system cargo pars for the history 1, 5, and 15 twinkles. The affair format iscurrent_time up days, hhmm, users, cargo average. xx,y.yy,z.zz. For illustration, uptime might display 123456 up 10 days, 345, 5 users, cargo normal0.10,0.20,0.30.
57. What’s the alias command, and how is it used in Linux?
Ans:
- The alias command in Linux is used to produce lanes for constantly used commands, simplifying command line operation.
- For illustration, alias ll = ‘ ls la’ creates an alias ll for the ls la command. Aliases can be defined in shell configuration lines like bashrc to make them patient across sessions.
- Aliases enhance productivity by reducing the quantum of codifying and precluding common typing crimes.
- Understanding and using aliases effectively can streamline workflows, facilitate effectiveness, and make the command line experience more user-friendly.
58. What approaches cover memory usage in Linux?
Ans:
- Memory operation in Linux can be covered using commands like free, top, top, and vmstat.
- The free h command provides a summary of the memory operation in a human-readable format, showing total, used, accessible, and available memory.
- The top and top commands offer real-time monitoring of processes, including their memory consumption. vmstat gives detailed statistics about memory, processes, and system performance.
- Effective tracking of memory operations helps diagnose performance issues, identify memory leaks, and ensure that operations have sufficient memory coffers to serve efficiently.
59. What methods change the hostname of a Linux system?
Ans:
To change the hostname of a Linux system, the ‘hostnamectl’ command can be used or the ‘/etc/hostname’ file can be edited manually. For example, ‘sudo hostnamectl set-hostname new-hostname’ sets the hostname to the new value. Additionally, the ‘/etc/hosts’ file should be updated to associate the new hostname with the appropriate IP address. Changing the hostname is crucial for network identification, ensuring unique identification, and effectively managing network services.
60. What’s the navigator command, and how is it used in Linux?
Ans:
The navigator command in Linux is used to combine library lines and directories into a single train, frequently for backup or distribution purposes. It can also compress libraries using options like z for gzip or j for bzip2. For illustration, navigator czvfarchive.tar.gz path to the directory creates a gzip-compressed library, while navigator xzvfarchive.tar.gz excerpts the contents. The navigator command is essential for managing backups, transferring large collections of lines, and conserving directory structures.
61. What is the process for using the ‘scp’ command to transfer files securely between systems?
Ans:
- The scp( secure dupe) command in Linux is used to transfer lines between hosts over a network securely.
- It uses S.S.H. for data transfer, ensuring encryption of both train content and login credentials.
- The introductory syntax is scpsource_fileuser@remote, the host path to the destination, which clonessource_file to the specified path on the remote host.
- Again, scpuser@remote, the host path to the file’s original destination, clones a train from the remote host to the original machine.
62. What’s the purpose of the echo command in Linux?
Ans:
- The echo command in Linux is used to display a line of textbooks or variables to the standard affair.
- For illustration, echo” Hello, World!” and print” Hello, World!” on the terminal.
- It can also be used to display the value of terrain variables, similar to echo$ PATH.
- Also, echo can deflect affairs to lines or be used in scripts to give feedback to the users.
63. What commands view network information in Linux?
Ans:
Viewing tackle information in Linux can be done using several commands, similar to lshw, lscpu, lsblk, and lspci. For illustration, lshw provides detailed information about tackle factors, lscpu displays CPU armature details, lsblk lists block bias, and lspci shows PCI machine details. These commands help diagnose and tackle issues, indicate tackle configurations, and understand system capabilities.
64. What’s the purpose of the ssh command in Linux, and how is it used?
Ans:
The S.S.H. ( Secure Shell) command in Linux is used to establish a secure, translated connection to a remote machine over a network. The introductory syntax is sshuser@hostname, where the user is the username on the remote machine and the hostname is the remote host’s name or I.P. address. S.S.H. is pivotal for remote administration, allowing users to execute commands, transfer lines, and manage servers securely.
65. What techniques check fragment operations by directories in Linux?
Ans:
- To check fragment operation by directories in Linux, the du( fragment operation) command is used.
- For illustration, the du sh path to the directory provides a summary of the fragment operation of the specified directory in a human-readable format.
- Adding the option includes lines in the affair, and d specifies the depth of directories to display.
- The du command helps in relating which directories are consuming the most space, easing effective fragment space operation.
66. What’s the name command, and what information does it give?
Ans:
- The name command in Linux displays system information.
- For illustration, name a provides comprehensive details, including the kernel name, network knot hostname, kernel release, kernel interpretation, machine tackle name, processor type, tackle platform, and operating system. name r displays the kernel release, and name m shows the machine tackle name.
- This command is helpful for snappily reacquiring essential system information for troubleshooting, system administration, and attestation purposes.
67. What methods compress and decompress files using ‘gzip’ and ‘gunzip’?
Ans:
The gzip command in Linux compresses lines, reducing their size for storehouse and transfer. For illustration, gzipfile.txt compressesfile.txt tofile.txt.gz. The gunzip command decompresses lines compressed with gzip. For case, gunzipfile.txt.gz restores the originalfile.txt. These commands are essential for effective storehouse operation and data transfer, especially for large lines or across networks.
68. What procedures manage software repositories in a Linux system?
Ans:
Managing software depositories in Linux involves configuring depository sources, generally set up in lines like apt sources. List for Debian-based systems or etc. yum.repos.d for Red Hat-based systems. You can add, remove, or update depository entries to control where the package director fetches software from. For illustration, adding a depository in a Debian-based system involves adding a line like deb httprepository.url ubuntu focal main to etc. apt sources.
69. Explain the purpose of the etc. shadow train in Linux.
Ans:
- The etc. shadow train in Linux stores secures users’ word information.
- It contains entries with fields for username, translated word, word growing information, and regard expiration dates.
- For illustration, john$ 6$ hash$ QWErty183580999997 represents users john with a translated word and word growing settings.
- The etc. shadow train enhances security by confining access to translated watchwords, which aren’t visible to regular users.
70. What’s the df command, and how is it used to check fragment space?
Ans:
- The df( fragment free) command in Linux reports the quantum of fragment space used and available on filesystems.
- For illustration, df h provides a human-readable affair with sizes in K.B., MB, or G.B.
- The affair includes filesystem, size, used space, available space, use chance, and mount point.
- This command is essential for covering fragment operation, ensuring sufficient free space, and precluding fragment space issues that could affect system performance.
71. What commands are used with the `kill` command in Linux?
Ans:
The coil command in Linux is an adaptable tool for transferring data from or to a garçon using various protocols, similar to HTTP, HTTPS, FTP, and more. For illustration, coil httpexample.com fetches the content of the specified URL. coil O httpexample.comfile.txt downloads a train, and coil X POST d” param1 = value1 & param2 = value2″ httpexample.com api sends a POST request with data.
72. Explain the clunk command and its operation in network troubleshooting.
Ans:
The clunk command in Linux tests the reachability of a host on a network by transferring ICMP echo request packets and staying for responses. For illustration, clunkgoogle.com sends packets to Google’s garçon and reports the response time. The command provides information on packet loss, roundtrip time, and network quiescence. A clunk is an abecedarian tool for diagnosing network connectivity issues, vindicating network configurations, and ensuring that a remote host is accessible.
73. Name some Linux Distros.
Ans:
- Linux distributions, generally known as distros, include a wide variety of choices depending on users’ requirements and preferences.
- Ubuntu is one of the most popular because of its user-friendliness and robust community support.
- Red Hat Enterprise Linux(R.H.E.L.) and CentOS are favored in commercial surroundings for their stability and long-term support.
- Debian is famed for its strict adherence to the free software gospel, and its secondary, Debian, offers a rolling release for those who prefer nonstop updates.
74. What are the significant differences between Linux and Windows?
Ans:
- Linux and Windows are unnaturally different in their design and user base.
- Linux is open source, meaning its source law is freely available for revision and distribution, fostering a community-driven development model.
- This results in a variety of distributions acclimatized for different requirements.
- In discrepancy, Windows is a marketable operating system developed by Microsoft, with a primary focus on personal, licensed software.
75. Explain LILO?
Ans:
LILO is a heritage charge for Linux operating systems that is used to load the Linux kernel into memory and start the operating system. It resides in the MBR( Master Boot Record) or the charge sector of a partition. Unlike newer charge payloads like GRUB, LILO doesn’t support on-the-fly configuration changes; it requires rewriting to the MBR whenever the configuration train is modified. This can make it less flexible, but some users appreciate its simplicity and plumpness.
76. What’s a root account?
Ans:
The root account in Linux is the superuser account with full access to all commands and lines on a Linux system. It has unrestricted boons and can perform conduct that is confined to regular users, similar to penetrating defended lines, installing software, and changing system configurations. This position of access is both critical and potentially dangerous, as crimes made with root boons can lead to system insecurity or security vulnerabilities.
77. Describe CLI and G.U.I. in Linux.
Ans:
- Linux supports both Command Line Interface( CLI) and Graphical Users Interface(G.U.I.) surroundings, feeding different users’ preferences and requirements.
- The CLI is a text-based interface where users interact with the system by codifying commands into a terminal.
- This interface is preferred by system directors and advanced users for its power, speed, and inflexibility.
- In discrepancy, the G.U.I. provides a visual interface with graphical rudiments similar to windows, icons, and menus, making it more user-friendly and accessible to general users.
78. What’s exchange Space?
Ans:
Exchange space in Linux is a form of virtual memory used to extend the quantum of physical memory( RAM) available on a system. When the system runs low on RAM, less constantly used data can be moved to change space, which is located on a hard drive or a separate partition. This allows for further RAM to be freed up for active processes, although penetrating data on exchange is slower than penetrating RAM.
79. What’s the difference between a process and a thread?
Ans:
- A process in Linux is a case of a program in prosecution, complete with its own address space, system coffers, and isolated terrain. It’s basically an independent reality to which system coffers( CPU time, memory) are allocated.
- A thread, on the other hand, is the lowest sequence of programmed instructions that can be maintained singly by the scheduler.
- Vestments are subsets of a process and partake in the same process coffers like memory and train descriptors, but each thread maintains its registers, mound, and prosecution sequence.
80. What’s RAID in Linux?
Ans:
A process in Linux is a case of a program in prosecution, complete with its own address space, system coffers, and isolated terrain. It’s basically an independent reality to which system coffers( CPU time, memory) are allocated. Vestments are subsets of a process and partake in the same process coffers like memory and train descriptors, but each thread maintains its registers, mound, and prosecution sequence.
81. What are the challenges of using Linux?
Ans:
Linux, while essential and flexible, presents particular challenges, especially for new users. The steep literacy wind is frequently mentioned, as Linux requires more commandline commerce compared to further visual interfaces of other operating systems. Tackle comity can be an issue, as some manufacturers don’t offer motorists for Linux. Also, there can be difficulties with software vacuity, particularly with personal or industry-standard operations that may need to have Linux performance.
82. What methods secure a Linux server?
Ans:
- Securing a Linux garçon involves multiple ways and stylish practices. Initially, keeping the system streamlined ensures all security patches are applied.
- Configuring and maintaining a firewall, similar to using iptables or firewalls, limits exposure to gratuitous network business.
- Turning off unused network services, removing gratuitous software, and managing users ’ warrants strain access control.
- Also, using tools like SELinux can help administer strict security programs. Regularly auditing the system with tools like Lynis or Assistant for security compliance and vulnerabilities is also pivotal.
83. What’s strace command?
Ans:
- The trace command in Linux is essential for individual debugging and educational mileage.
- It monitors and records the system calls made by a program and signals it receives.
- This command is invaluable for troubleshooting and understanding how a program interacts with the kernel.
- By furnishing a detailed log of system calls, the trace can help identify where a program may be encountering issues similar to access violations, failing system calls, or performance backups.
84. How to administer Linux servers?
Ans:
Administering Linux servers involves various tasks to ensure they’re running efficiently and securely. Crucial liabilities include:
- Installing and configuring software and services.
- Managing users’ accounts and warrants.
- Ensuring data integrity and security.
Regular updates and patches must be applied to keep the garçon secure. Monitoring tools similar to Top, Top, or Nagios can be used to track system performance and resource operation. Provisory strategies should be enforced to cover data.
85. What’s SMTP?
Ans:
MTP( Simple Correspondence Transfer Protocol) is the standard protocol used for transferring emails across the Internet. Correspondence servers use it to shoot and admit emails and guests to shoot dispatches to a correspondence garçon. SMTP only handles the transferring of emails; for reacquiring and storing incoming correspondence, other protocols similar to POP3 or IMAP are used. SMTP servers operate on TCP harborage 25, and secured SMTP, which encrypts the transmission, generally uses TCP harborage 465 or 587.
86. What’s L.V.M. in Linux?
Ans:
L.V.M. ( Logical Volume director) is a tool for managing fragment space in Linux. It allows for the creation, resizing, and omission of partitions on hard drives in a flexible manner without taking time out. L.V.M. workshop, by grouping one or more physical volumes into a volume group from which logical volumes can be allocated. This abstraction subcaste adds inflexibility and facilitates features like live resizing of train systems and snapshotting.
87. What techniques schedule recurring tasks in Linux?
Ans:
In Linux, recreating tasks are listed using the cron daemon, which reads crontab lines and executes scripts or commands at specified times and intervals. Each user can have their crontab trained, or tasks can be added to the systemwide crontab. To edit a user’s crontab, one would use crontab e and add lines that specify the schedule followed by the command to be executed.
88. What are the levels in Linux?
Ans:
- Runlevels in Linux are a state, or mode, defined by the services and daemons initiated at incipiency.
- Traditional SysV init systems classify levels with figures 0 through 6, where each number represents a different state: 0 for halt, 1 for single-user mode, 25 for various multiuser modes( with varying degrees of networking and user interfaces), and 6 for reboot.
- Managing run levels involves editing scripts in etc.d or using commands like telnet to change the run level.
89. What’s network-related in Linux?
Ans:
Network relating in Linux refers to the aggregation of multiple network interfaces into a single clicked interface to give redundancy or increase outturn. This configuration is also known as N.I.C. ( Network Interface Card) teaming. Linux supports different modes of relating, like cargo balancing, where business is distributed across the interfaces, or active, where one interface takes over if the active one fails.
90. How are lines organized in Linux?
Ans:
In Linux, lines are organized in a hierarchical directory structure starting from the root directory, denoted by””. This structure branches out into various subdirectories for system, operation, and user data. Crucial directories include caddy for double executables, etc., for configuration lines, home for user directories, use for user-related programs, and var for variable data like logs and emails.






