
The Unix shell is a command-line interpreter that provides a user interface for the Unix operating system and Unix-like systems. It allows users to execute commands, run programs, and manage system resources by typing commands into a text-based interface. The shell interprets these commands and translates them into actions taken by the operating system. Unix shells, such as the Bourne shell (sh), C shell (csh), Korn shell (ksh), and Bourne Again shell (bash), offer powerful scripting capabilities, enabling users to automate tasks through shell scripts.
1. What is the Unix command to list all files in a directory?
Ans:
To list all files in a directory in Unix, the ‘ls’ command is used, which displays the names of files and directories in the current directory. The output can be modified with options such as ‘-l’ for detailed information or ‘-a’ to include hidden files. The `ls` command is crucial for navigating and managing files in Unix. Combining options like `-la` provides a comprehensive, detailed list, making file management more efficient.
2. How is the contents of a file viewed in Unix?
Ans:
- To view a file’s contents, the `cat` command is typically used.
- By entering `cat` followed by the filename, it displays the entire file’s contents on the terminal.
- Other commands such as `more`, `less`, `head`, or `tail` can also be used to view files in sections or pages.
- These commands offer flexibility for examining large files.
- For instance, `less` allows backward navigation through the content.
3. What command is used to change the permissions of a file?
Ans:
Can change a file’s permissions using the `chmod` command. This command sets read, write, and execute permissions for the file owner, group, and others using symbolic (e.g., `u+r`) or numeric (e.g., `755`) representations. Adjusting permissions controls who can access and modify the file. Mastery of `chmod` is essential for system security and proper file access management, ensuring only authorized users can perform specific actions on files.
4. What command is used to find the current directory in Unix?
Ans:
- To determine the current directory, use the pwd (print working directory) command.
- It prints the full pathname of the current directory, helping verify the location within the file system.
- This command is particularly useful in complex directory structures.
- Knowing the exact directory can prevent mistakes like accidental changes or deletions in the wrong location.
5. Explain the difference between `cp` and `mv` commands.
Ans:
| Point of Comparison | `cp` Command | `mv` Command |
|---|---|---|
| Basic Function | Copies files or directories from one location to another, leaving the original files/directories intact. | Moves or renames files or directories from one location to another, removing the original files/directories from the source location. |
| Syntax | `cp [options] source destination` | `mv [options] source destination` |
| Usage Example | `cp file1.txt /backup/file1.txt` | `mv file1.txt /archive/file1.txt` |
| Data Preservation | The original data remains in the source location, creating an exact copy in the destination. | The original data is removed from the source location and only exists in the destination after the move. |
6. What method is used to search for a pattern in a file using Unix commands?
Ans:
To search for a pattern in a file, use the `grep` command. By typing `grep` followed by the pattern and filename, `grep` searches through the file and prints lines that match the pattern. It is particularly useful for finding specific text within large files. Additionally, `grep` offers options like `-i` for case-insensitive searches or `-r` for recursive directory searches, enhancing its functionality.
7. What is the purpose of the `chmod` command?
Ans:
- The `chmod` command changes file access permissions. It allows to modify permissions for the owner, group, and others using symbolic (e.g., `u+r`) or numeric (e.g., `755`) modes to specify the permissions.
- This command controls who can read, write, or execute a file, playing a critical role in maintaining system security and proper file access.
- Effective use of `chmod` ensures that only authorized users can perform specific actions on files.
8. What command displays the first 10 lines of a file in Unix?
Ans:
To display the first 10 lines of a file, use the `head` command. By default, `head` shows the first 10 lines, but you can specify a different number with the `-n` option. This command is helpful for quickly viewing the beginning of a file, such as checking headers or initial data. For example, `head -n 20 filename` displays the first 20 lines, making it useful for examining file content without opening the entire file.
9. Explain the use of the `ps` command.
Ans:
The `ps` command displays information about active processes. It provides details such as process IDs, statuses, and CPU usage, helping users monitor and manage system processes. The `ps` command can be combined with options like `aux` for detailed information about all processes. This command is essential for system administration, offering insights into the system’s current activity and aiding in troubleshooting.
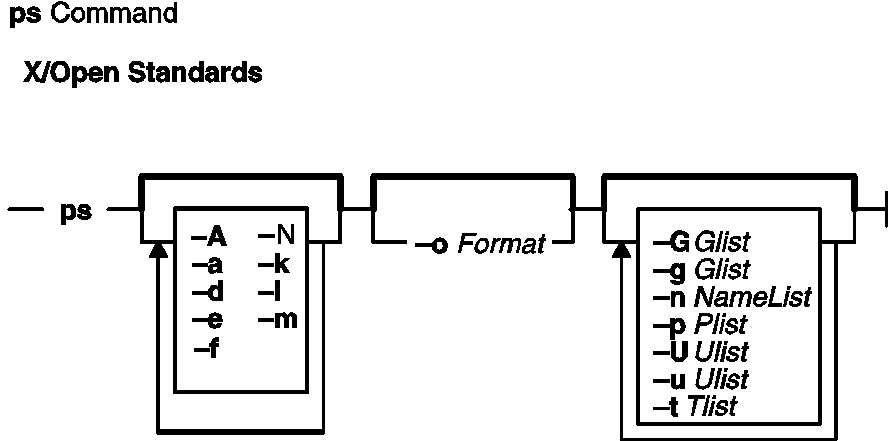
10. What command counts the number of lines in a file in Unix?
Ans:
To count the number of lines in a file, use the `wc -l` command. The `wc` (word count) command with the `-l` option counts and outputs the number of lines in the specified file. This command quickly determines a file’s length in lines, useful for tasks like counting lines of code in a source file. For example, `wc -l filename` returns the line count, aiding in various file management and analysis tasks.
11. What is a shell script?
Ans:
- A shell script is a file containing a series of commands for a Unix-based operating system’s shell to execute.
- It automates repetitive tasks and simplifies complex command sequences by grouping them into a single script.
- Shell scripts can include loops and conditionals, making them powerful tools for system administration and automation.
12. How is a simple shell script created in Unix?
Ans:
To create a simple shell script, open a text editor and write the commands. Begin with the shebang (`#!/bin/bash`) to specify the interpreter, followed by the commands. Save the file with a `.sh` extension. For instance:
- #!/bin/bash
- echo “Hello, World!”
- Save this as `hello.sh`.
13. Explain the significance of the shebang (`#!/bin/bash`) in a shell script.
Ans:
The shebang (`#!/bin/bash`) at the start of a shell script specifies the interpreter to execute the script. It tells the system to use the Bash shell for the script’s commands. This ensures the script runs in the correct environment, regardless of the user’s default shell. Additionally, using a shebang allows for greater portability, as scripts can be executed on different systems without modification. It also enables users to run the script simply by calling its name, without needing to explicitly invoke the interpreter.
14. What steps are taken to execute a shell script in Unix?
Ans:
To run a shell script, first make it executable using the `chmod` command:
- chmod +x scriptname.sh
Then, execute the script by typing `./scriptname.sh`. Alternatively, you can run it by specifying the interpreter directly:
- bash scriptname.sh
15. What is the difference between `.` and `source` when running a script?
Ans:
The `.` (dot) and `source` commands execute a script in the current shell environment rather than a new subshell. This means any variables set or modified in the script affect the current shell session. While both commands are similar, `source` is more explicit and readable, often preferred for clarity. It also enables users to run the script simply by calling its name, without needing to explicitly invoke the interpreter.
16. How are arguments passed to a shell script in Unix?
Ans:
To pass arguments to a shell script, include them after the script name when executing it. For example:
- ./scriptname.sh arg1 arg2
Inside the script, these arguments can be accessed using positional parameters `$1`, `$2`, etc.
17. Explain the use of `$1`, `$2`, …, `$n` in a shell script.
Ans:
In a shell script, `$1`, `$2`, …, `$n` represent the arguments passed to the script. `$1` is the first argument, `$2` the second, and so on. These parameters allow the script to utilize the arguments provided during execution. For example, running `./script.sh foo bar` makes `$1` equal `foo` and `$2` equal `bar`. Additionally, $# can be used to get the total number of arguments passed, while $@ provides all the arguments as a list. This functionality enhances the script’s flexibility by allowing it to process different inputs dynamically.
18. What is `$?` in Unix?
Ans:
- The special variable `$?` in Unix stores the exit status of the last executed command.
- An exit status of `0` usually indicates success, while a non-zero value indicates an error or specific condition.
- This variable is useful for error checking and controlling the script flow based on command success or failure.
19. How is file existence checked in a shell script?
Ans:
To check if a file exists in a shell script, use an `if` statement with the `-e` test operator. For example:
- if [ -e filename ]; then
- echo “File exists.”
- else
- echo “File does not exist.”
- fi
This checks for the file’s existence and prints a corresponding message.
20. How are two numbers compared in a shell script?
Ans:
To compare two numbers in a shell script, use the `-eq`, `-ne`, `-lt`, `-le`, `-gt`, or `-ge` operators within an `if` statement. For example:
- num1=5
- num2=10
- if [ $num1 -lt $num2 ]; then
- echo “$num1 is less than $num2”
- else
- echo “$num1 is not less than $num2”
- fi
This script compares `num1` and `num2` and prints a message based on the comparison.
21. What defines a function in shell scripting?
Ans:
In shell scripting, a function is a segment of code designed to perform a specific task. Functions help in organizing and reusing code, making scripts more modular and easier to manage. To define a function, you use the syntax: `function_name() { # commands }`. A function can be called by its name followed by parentheses. This structure allows for code reuse and better organization within scripts.
22. Explain the use of loops in shell scripting.
Ans:
- Loops in shell scripting are essential for running a sequence of commands multiple times.
- They are used for tasks that require repetition, such as processing lists or performing operations until a certain condition is met.
- Common loop types include `for`, `while`, and `until`, each serving different purposes in iteration.
- These loops enhance the script’s capability to handle repetitive tasks efficiently.
23. What is the difference between `for`, `while`, and `until` loops?
Ans:
The `for`, `while`, and `until` loops each have distinct iteration methods in shell scripting. A `for` loop iterates over a list of items, executing commands for each item. A `while` loop continues to run as long as a specified condition remains true, making it useful for condition-based repetition. An `until` loop is similar to a `while` loop but runs until a specified condition becomes true. These different loops provide flexibility in handling various iteration needs within scripts.
24. What methods are used for string manipulation in shell scripting?
Ans:
String manipulation in shell scripting involves techniques and commands for handling strings, such as extracting substrings, determining string length, and replacing parts of strings. For example, extract a substring using `${string:position:length}`, find the length of a string with `${#string}`, and replace substrings using `${string/old/new}`. These operations are crucial for processing and managing textual data within scripts.
25. How is user input read in a shell script?
Ans:
To read input from a user in a shell script, the `read` command is used. This command prompts the user for input and stores the input in a variable. For instance, using `read -p “Enter your name: ” name`, the script displays a prompt and waits for the user to input a value, which is then stored in the variable `name`. This approach allows for interactive scripts that can respond to user input dynamically.
26. Explain the use of arrays in shell scripting.
Ans:
- Arrays in shell scripting allow for the storage of multiple values in a single variable, simplifying the handling of collections of related data.
- An array is defined, and its elements are accessed using indices.
- For example, `array=(value1 value2 value3)` defines an array, and access its elements with `${array[0]}` to get `value1` and `${array[@]}` to get all elements.
- This capability is useful for managing and processing lists of data within scripts.
27. How are errors handled in a shell script?
Ans:
Handling errors in a shell script involves checking the exit status of commands and taking appropriate actions if errors occur. This is typically done using conditional statements and the special variable `$?`, which holds the exit status of the last executed command. For example, after running a command, The command ‘if [ $? -ne 0 ]; then echo “An error occurred”; fi’ can be used to check if an error occurred and respond accordingly. This approach ensures that scripts can handle failures gracefully and take corrective actions when necessary.
28. What are positional parameters in shell scripting?
Ans:
Positional parameters in shell scripting are special variables that store the arguments passed to the script. These parameters, such as `$1`, `$2`, …, `$n`, represent the first, second, and subsequent arguments, respectively. They enable the script to handle input dynamically based on the arguments provided during execution. For instance, running `./script.sh foo bar` makes `$1` equal to `foo` and `$2` equal to `bar`, allowing the script to process these values as needed.
29. How is a temporary file created in Unix?
Ans:
- To create a temporary file in Unix, the ‘mktemp’ command can be used, which generates a unique temporary file and returns its name.
- For example, `tempfile=$(mktemp)` creates a temporary file and stores its name in the variable `tempfile`, ensuring that the file does not conflict with existing files.
- This approach is useful for creating temporary storage that can be safely used and later removed without affecting other files.
30. Explain the use of `trap` in a shell script.
Ans:
The `trap` command in a shell script is used to catch signals and execute specific commands when those signals are received. It is useful for cleaning up resources or handling interruptions gracefully. For example, `trap “echo ‘Interrupt signal received’; exit” SIGINT` sets up a trap that prints a message and exits the script when an interrupt signal (such as Ctrl+C) is received. This allows scripts to handle unexpected interruptions in a controlled manner.
31. How are two files concatenated in Unix?
Ans:
In Unix, two files can be merged into one using the ‘cat’ command. This command concatenates the contents of the specified files. For instance, running `cat file1.txt file2.txt > combined.txt` will combine the contents of `file1.txt` and `file2.txt` into a new file named `combined.txt`. This technique is particularly useful for combining data from multiple sources into a single file for easier handling and analysis.
32. Explain the use of `awk` command.
Ans:
The `awk` command in Unix is a powerful tool for processing and analyzing text files. It allows you to search for patterns and perform actions on matching lines. For example, the command `awk ‘{print $1}’ file.txt` prints the first column of each line from `file.txt`. `awk` can handle complex tasks such as arithmetic operations, text manipulations, and condition-based processing, making it an essential utility for handling structured text data.
33. What command sorts the contents of a file in Unix?
Ans:
- To sort the contents of a file in Unix, the ‘sort’ command is used.
- This command organizes the lines of a file according to specified criteria. By default, `sort file.txt` sorts the lines alphabetically.
- Also use options like `-n` for numerical sorting or `-r` for sorting in reverse order.
- This command is vital for organizing and managing data in a file efficiently.
34. What is the `grep` command used for?
Ans:
The `grep` command in Unix is used to search for specific text patterns within files. It scans each line of a file and prints the lines that match the given pattern. For example, `grep “pattern” file.txt` will search for the word “pattern” in `file.txt` and display all matching lines. `grep` is a powerful tool for finding specific information within large files, and it supports various options to customize the search, such as case-insensitivity with the `-i` option.
35. How are duplicate lines removed from a file in Unix?
Ans:
To remove duplicate lines from a file in Unix, use a combination of the `sort` and `uniq` commands. First, sort the file to ensure duplicate lines are adjacent, then use `uniq` to remove them. For instance, `sort file.txt | uniq > unique.txt` sorts `file.txt` and removes duplicate lines, saving the unique lines to `unique.txt`. This method ensures that each line in the output file is unique.
36. Explain the use of the `sed` command.
Ans:
- The `sed` command in Unix is a stream editor used for basic text transformations.
- It allows to search for patterns, replace text, and perform other text manipulations on an input stream or file.
- For example, `sed ‘s/old/new/g’ file.txt` replaces all occurrences of “old” with “new” in `file.txt`.
- `sed` is very flexible and can handle complex text processing tasks with its powerful scripting capabilities.
37. How is the size of a file determined in Unix?
Ans:
To find the size of a file in Unix, you can use either the `ls -l` or `du` command. The `ls -l file.txt` command provides detailed information about `file.txt`, including its size in bytes. Alternatively, `du -h file.txt` displays the file size in a human-readable format, such as kilobytes or megabytes. These commands are useful for quickly determining the size of files for storage management and analysis.
38. What command displays the last 10 lines of a file in Unix?
Ans:
To display the last 10 lines of a file in Unix, use the `tail` command. By default, `tail file.txt` shows the last 10 lines of `file.txt`. Also specify a different number of lines using the `-n` option, for example, `tail -n 20 file.txt` to display the last 20 lines. This command is particularly useful for viewing the most recent entries in log files or other sequential data files.
39. Explain the use of `cut` command.
Ans:
The `cut` command in Unix is used to extract specific sections from each line of a file, such as columns or fields. For instance, `cut -d, -f1,3 file.csv` extracts the first and third fields from `file.csv`, using a comma as the delimiter. This command is particularly useful for processing and analyzing structured text files, where isolating and working with specific columns is necessary.
40. How is a file split into multiple files in Unix?
Ans:
- To split a file into multiple smaller files in Unix, use the `split` command.
- This command divides a file based on specified criteria, such as the number of lines.
- For example, `split -l 1000 largefile.txt` splits `largefile.txt` into smaller files, each containing 1000 lines.
- The resulting files are named sequentially with a prefix and suffix, like `xaa`, `xab`, and so on. This method is helpful for breaking down large files into more manageable parts for easier handling.
41. What command checks the running processes in Unix?
Ans:
Monitoring active processes in Unix involves using the `ps` command, which provides detailed information about running processes. For example, `ps aux` displays user ownership, process IDs (PIDs), CPU and memory usage, and the command that initiated each process. Additionally, `top` offers a real-time view of system processes and resource utilization, making it effective for dynamic system monitoring.
42. What is the use of `kill` command?
Ans:
In Unix, the `kill` command terminates processes by sending signals. By specifying a process ID (PID), you can send a signal to instruct the process to terminate. Typically, `kill` sends a `SIGTERM` signal (signal 15), prompting a graceful shutdown. For instance, `kill 1234` sends `SIGTERM` to the process with PID 1234, facilitating orderly termination of unwanted or malfunctioning processes.
43. Explain the difference between `kill` and `kill -9`.
Ans:
- The difference between `kill` and `kill -9` lies in the type of signal sent to a process.
- While `kill` sends a `SIGTERM` signal (signal 15), encouraging the process to gracefully terminate and clean up resources, `kill -9` transmits a `SIGKILL` signal (signal 9), forcing immediate termination without allowing the process to perform any cleanup tasks.
- `kill -9` is typically used as a last resort for unresponsive processes.
44. How is a process run in the background in Unix?
Ans:
To execute a process in the background in Unix, append an ampersand (`&`) to the command. This allows the command to run independently while freeing up the terminal for other tasks. For example, `./script.sh &` launches `script.sh` in the background, enabling simultaneous use of the terminal for additional commands or operations. This functionality is particularly useful for long-running processes that do not require immediate user interaction.
45. How is a background process brought to the foreground in Unix?
Ans:
Bringing a background process to the foreground in Unix is achieved using the `fg` command followed by the job number. The `jobs` command lists active background jobs and their respective job numbers. For instance, if `jobs` shows `[1]+ Running ./script.sh &`, using `fg %1` brings `./script.sh` to the foreground, enabling direct interaction with the running process.
46. Explain the use of `nohup` command.
Ans:
The `nohup` command in Unix ensures a command continues running even after the user logs out or the terminal session ends. For example, `nohup ./script.sh &` executes `script.sh` in the background, preserving its execution beyond logout. Output typically redirects to `nohup.out` by default, making it suitable for uninterrupted execution of long-running processes.
47. How is memory usage of a process checked in Unix?
Ans:
- To check the memory usage of a process in Unix, employ the `ps` command with appropriate options or use `top`.
- For example, `ps aux | grep <PID>` provides detailed memory usage information for a specific process.
- Alternatively, `top` offers a real-time overview of system processes, including memory utilization.
- Additionally, `pmap <PID>` provides a detailed memory map for deeper analysis.
48. What is the `top` command used for?
Ans:
The `top` command in Unix provides a dynamic view of system processes and resource usage in real-time. It presents essential metrics such as CPU usage, memory allocation, process IDs, user details, and executed commands. This command is invaluable for monitoring system performance, identifying resource-intensive processes, and optimizing system resource allocation.
49. What methods are used to schedule a job in Unix?
Ans:
Scheduling tasks in Unix involves using commands such as `at` or `cron`. The `at` command schedules one-time tasks to execute at specified times, while `cron` manages recurring tasks. For instance, scheduling a task to run `script.sh` at 2 PM can be achieved with `echo “sh script.sh” | at 2pm`. `cron` uses the `crontab` configuration file to define tasks scheduled at regular intervals.
50. What is a cron job and how is one created in Unix?
Ans:
A cron job in Unix is a scheduled task designed to execute at specified intervals using the `cron` daemon. Creation involves editing the `crontab` file with `crontab -e`, where each entry specifies timing details and corresponding commands. For example, `0 2 * * * /path/to/script.sh` schedules `script.sh` to run daily at 2 AM, automating repetitive tasks and enhancing operational efficiency.
51. How is the IP address of a Unix machine checked?
Ans:
- To determine the IP address of your Unix machine, utilize the `ifconfig` command, which provides comprehensive network configuration details.
- For example, `ifconfig` displays IP addresses assigned to all network interfaces, aiding in network setup and troubleshooting.
- Additionally, `ip addr show` offers similar information, presenting IP addresses associated with each network interface on the system.
- These commands are invaluable for identifying the current IP address of your Unix machine and managing network connectivity effectively.
52. Explain the use of `ping` command.
Ans:
The `ping` command in Unix serves to assess the reachability of a host on an IP network by sending ICMP echo request packets. This command measures round-trip time and verifies connectivity, making it essential for network diagnostics. For instance, `ping example.com` tests connectivity to `example.com` and reports response statistics. `ping` plays a crucial role in troubleshooting network issues, ensuring network connectivity and verifying host availability.
53. How are files transferred between two Unix machines?
Ans:
- To transfer files between two Unix machines securely, utilize the `scp` (secure copy) command.
- For example, `scp file.txt user@remotehost:/path/to/destination` copies `file.txt` from the local machine to `remotehost` using SSH for encrypted transmission.
- `scp` guarantees data confidentiality and integrity during transfer, with authentication via SSH keys or passwords ensuring secure access.
- This method is efficient for exchanging files between Unix systems over a network, maintaining security and reliability.
54. What is SSH and how is it used in Unix?
Ans:
SSH (Secure Shell) is a cryptographic network protocol facilitating secure communication between two computers over an insecure network. To initiate an SSH connection in Unix, use `ssh username@hostname`, where `username` is your account on the remote machine and `hostname` is its IP address or domain name. SSH ensures encrypted data transmission and secure remote access management in Unix environments, protecting against unauthorized access and ensuring secure data exchange.
55. Explain the use of `scp` command.
Ans:
The `scp` command in Unix enables secure file transfer between local and remote Unix machines over a network. For instance, `scp file.txt user@remotehost:/path/to/destination` copies `file.txt` to `remotehost` using SSH for encryption and authentication. `scp` preserves file permissions and ownership during transfer, making it ideal for secure and efficient file copying in Unix environments.
56. How are open ports checked on a Unix machine?
Ans:
- To identify open ports on a Unix machine, use the `netstat` command with appropriate options. For example, `netstat -tuln` lists all listening (`-l`) TCP (`-t`) and UDP (`-u`) ports along with their numeric (`-n`) identifiers.
- This command provides insights into active network connections, listening ports, and associated services running on the Unix system, essential for network monitoring and security assessment.
57. What is the `netstat` command used for?
Ans:
The `netstat` command in Unix serves to display network connections, routing tables, interface statistics, and multicast memberships. For instance, `netstat -a` shows active connections and listening sockets. `netstat` aids in monitoring network performance, diagnosing network issues, and analyzing network traffic in Unix environments, providing valuable insights into network operations and facilitating effective network management.
58. How is a firewall configured in Unix?
Ans:
Configuring a firewall in Unix usually involves using tools like ‘iptables’ or frontend applications such as ‘ufw’ (Uncomplicated Firewall). ‘iptables’ is a command-line utility for setting rules and chains for packet filtering and NAT in IPv4 and IPv6. For example, ‘iptables -A INPUT -p tcp –dport 22 -j ACCEPT’ permits incoming SSH connections on port 22. By filtering and managing network packets based on defined rules, ‘iptables’ enhances Unix system security and effectively mitigates network threats.
59. Explain the use of `iptables`.
Ans:
- `iptables` is a powerful command-line utility in Unix used for configuring firewall rules and managing network traffic.
- It manipulates packet filtering and Network Address Translation (NAT) rules within the Linux kernel’s networking stack, providing comprehensive network security.
- For example, `iptables -A INPUT -p tcp –dport 80 -j ACCEPT` permits incoming TCP traffic on port 80.
- `iptables` protects Unix systems from unauthorized access and network threats by allowing, denying, or forwarding packets based on predefined criteria, ensuring robust network security and performance.
60. What methods are used to monitor network traffic in Unix?
Ans:
Monitoring network traffic in Unix involves employing various tools and commands. For real-time monitoring, tools like `iftop` display bandwidth usage by network connections, while `tcpdump` captures and analyzes packets on a network interface. Additionally, `Wireshark` offers a graphical interface for detailed network traffic analysis. These tools enable administrators to monitor network performance, diagnose issues, and ensure efficient operation of Unix systems in diverse network environments, enhancing overall network management and security.
61. How is a new user created in Unix?
Ans:
To create a new user in Unix, utilize the `useradd` command with specific options to define parameters such as the username, home directory, and default shell. For example, `sudo useradd -m -s /bin/bash newuser` creates a new user named `newuser` with a home directory (`-m`) and `/bin/bash` set as the default shell (`-s`). After creating the user, set a password using `sudo passwd newuser` to enable access to the account.
62. Explain the use of `sudo` command.
Ans:
The `sudo` command in Unix enables users to execute commands with elevated privileges, typically requiring authentication with their own password. For instance, `sudo apt-get update` allows users to update system packages with superuser permissions. This command ensures security by limiting elevated access to authorized users, thereby enhancing control over system administration tasks.
63. What command changes the password of a user in Unix?
Ans:
- Changing a user’s password in Unix is accomplished using the `passwd` command followed by the username.
- For example, `sudo passwd username` prompts for a new password for the specified user.
- Users can change their own passwords without `sudo`, while administrative privileges are necessary to modify passwords for other users.
- This command ensures robust password management and user account security.
64. How is disk usage viewed in Unix?
Ans:
To view disk usage in Unix, employ the `df` command, which provides an overview of filesystem disk space utilization across all mounted filesystems. For instance, `df -h` displays disk space usage statistics in a human-readable format, detailing total, used, and available space. This command is essential for monitoring and managing storage capacity effectively within Unix systems.
65. What is the use of `df` and `du` commands?
Ans:
The `df` command in Unix offers a comprehensive overview of filesystem disk space usage, presenting information on total, used, and available disk space across mounted filesystems. In contrast, the `du` command calculates disk usage for specific files and directories. For example, `du -sh /path/to/directory` displays the total disk space consumed by the specified directory. `df` focuses on system-wide disk usage, while `du` provides detailed metrics for individual files and directories.
66. What steps are taken to mount a filesystem in Unix?
Ans:
- Mounting a filesystem in Unix involves using the `mount` command followed by the device or filesystem to be mounted and the target directory where it should be accessible.
- For example, `sudo mount /dev/sdb1 /mnt/data` mounts the `/dev/sdb1` partition onto the `/mnt/data` directory.
- Properly mounting filesystems enables access to their contents for reading and writing, seamlessly integrating additional storage into Unix environments.
67. Explain the use of `fstab` file.
Ans:
The `fstab` file in Unix, located at `/etc/fstab`, serves as a system configuration file that defines how and where filesystems are mounted during system startup. Each entry in `fstab` specifies details such as the filesystem, its mount point, filesystem type, mount options, and other parameters. Administrators edit `fstab` to automate filesystem mounting, ensuring consistent access to storage devices across system reboots and enhancing system reliability.
68. How is a symbolic link created in Unix
Ans:
Creating a symbolic link (symlink) in Unix utilizes the `ln` command with the `-s` option. For instance, `ln -s /path/to/original /path/to/link` creates a symbolic link named `link` that points to `original`. Symlinks function as pointers to files or directories, facilitating navigation and providing flexibility in managing Unix filesystems. They can also simplify access to frequently used files and enable multiple references to the same file without duplicating the data.
69. What is the difference between hard link and soft link?
Ans:
The primary distinction between a hard link and a soft link (symbolic link) in Unix lies in their method of referencing files. A hard link directly points to the inode of a file on the filesystem, sharing the same inode number and storage space as the original file. In contrast, a symbolic link is a separate file containing the path to another file or directory. Symlinks can span filesystems and reference directories, offering versatility but requiring access to the original file for operation.
70. What command checks system logs in Unix?
Ans:
- Checking system logs in Unix involves using commands like `tail` or `less` to examine log files located in `/var/log`.
- For example, `sudo tail /var/log/syslog` displays the last few lines of the `syslog` file, which logs system messages and events.
- System logs provide valuable insights into system operations, errors, and security incidents, facilitating troubleshooting, performance monitoring, and maintaining system integrity within Unix environments.
71. What is `cron` and how does it work?
Ans:
`cron` is a time-based job scheduler in Unix-like systems that automates tasks at specified intervals. It operates by reading configuration files (crontabs) located in `/etc/crontab` and directories such as `/etc/cron.d`, `/etc/cron.hourly`, `/etc/cron.daily`, `/etc/cron.weekly`, and `/etc/cron.monthly`. Each user can manage their own scheduled tasks using `crontab` files in `/var/spool/cron/crontabs`.
72. How is a cron job written in Unix?
Ans:
Writing a cron job involves editing the crontab file associated with the user who will execute the scheduled task. To edit, use `crontab -e` to open the crontab editor. Each line in the crontab file specifies a job with fields for minute, hour, day of month, month, day of week, and the command to execute. For instance, `0 3 * * * /path/to/script.sh` runs a script daily at 3 AM.
73. Explain the use of `at` command.
Ans:
The `at` command schedules one-time tasks in Unix to execute at a specified future time. It reads commands from standard input or a file and executes them once. For example, `echo “command” | at 10:00` schedules `command` to run at 10:00 AM. Commands like `atq` list pending `at` jobs, and `atrm` removes scheduled tasks from the queue. This command is particularly useful for automating tasks that need to be performed outside of regular working hours.
74. How is a one-time job scheduled in Unix?
Ans:
- To schedule a one-time job in Unix using `at`, specify the time when the job should execute after the `at` command.
- For instance, `echo “command” | at now + 1 hour` schedules `command` to run one hour from the current time.
- Time can be specified in various formats (`HH:MM`, `now`, `noon`, `teatime`, etc.) to meet specific scheduling needs.
75. How are services managed in Unix?
Ans:
Managing services in Unix involves overseeing processes to ensure they start, stop, or restart as required. Use commands like `service`, `systemctl`, or scripts in `/etc/init.d`. For example, `service apache2 start` initiates the Apache HTTP server. Management tasks include configuring startup behavior, monitoring service status, and troubleshooting operational issues.
76. Explain the use of `systemctl` command.
Ans:
The `systemctl` command in Unix manages system services controlled by `systemd`, a system and service manager. It provides operations such as starting, stopping, restarting, enabling at boot, disabling at boot, and querying service status. For instance, `systemctl start apache2` initiates the Apache HTTP server. Additionally, systemctl status apache2 displays the current status and logs of the service, allowing for easier troubleshooting.
77. How is the status of a service checked in Unix?
Ans:
Checking the status of a service in Unix involves using `systemctl status` followed by the service name. For example, `systemctl status sshd` provides detailed information on the status of the SSH service (`sshd`). This includes real-time data on service uptime, running state, and recent logs, facilitating service monitoring and troubleshooting. Additionally, it helps identify any errors or issues affecting the service’s performance. This command can also be used with options like –no-pager to view the output without pagination for easier readability.
78. What is the `journalctl` command used for?
Ans:
The `journalctl` command in Unix accesses messages from the `systemd` journal, a centralized logging system that stores logs for services and system events. Use options like `-u` to filter by specific units (services) or `-b` for logs since the last boot. For example, `journalctl -u apache2.service` displays logs related to the Apache HTTP server. Additionally, journalctl -f can be used to follow log output in real-time, similar to tail -f.
79. How is data backed up and restored in Unix?
Ans:
- Backing up and restoring data in Unix involves using tools such as `tar`, `rsync`, or dedicated backup software.
- The `tar` command creates archives by bundling files into a single file, optionally compressing them using tools like `gzip` or `bzip2`.
- For example, `tar -czvf backup.tar.gz /path/to/directory` creates a compressed backup of `directory`. Restoring backups entails extracting files from the archive using `tar -xvf backup.tar.gz`.
80. Explain the use of `tar` command.
Ans:
The `tar` command in Unix archives files and directories into a single file for storage or distribution. It supports options for creating (`-c`), extracting (`-x`), compressing (`-z` for gzip, `-j` for bzip2), and appending (`-r`) archives. For instance, `tar -czvf archive.tar.gz /path/to/directory` creates a compressed tar archive of `directory`. The resulting .tar.gz file can be easily transferred or stored, preserving the original file structure.
81. What methods are used to troubleshoot a failed shell script?
Ans:
- Review Logs: Check system logs (`/var/log/syslog` or `/var/log/messages`) for error messages related to the script’s execution.
- Debug Statements: Insert `echo` statements strategically within the script to track its flow and monitor variable values during execution.
- Debug Mode: Enable debugging mode at the beginning of the script with `set -x` to trace each command before execution, helping to pinpoint where issues occur.
- Syntax Validation: Validate the script’s syntax using `bash -n script.sh` without executing it to catch syntax errors early.
82. Explain the use of `strace` command.
Ans:
The `strace` command in Unix traces and displays system calls and signals made by a process, aiding in debugging and performance analysis. It provides detailed insights into how processes interact with the operating system, helping to diagnose issues and optimize software performance. For example, `strace -p <pid>` attaches to an existing process `<pid>` to monitor its system calls in real-time.
83. How are syntax errors checked in a shell script?
Ans:
To check for syntax errors in a shell script, use `bash`’s `-n` option. For instance, `bash -n script.sh` performs a syntax check on `script.sh` without executing it. Alternatively, use `shellcheck` (`shellcheck script.sh`), a tool that identifies common script issues and improves code quality by providing recommendations for improvements. Regularly utilizing these tools can help catch errors early in the development process, reducing debugging time.
84. What is the `ulimit` command used for?
Ans:
The `ulimit` command in Unix sets or displays user resource limits such as maximum file size, memory usage, and number of processes. It helps manage system resources efficiently by defining constraints that prevent resource exhaustion and improve system stability. For example, `ulimit -n` displays the maximum number of open file descriptors a user can have.
85. What steps are taken to optimize a shell script for better performance?
Ans:
- Minimize I/O Operations: Reduce the number of file read/write operations by storing data in variables whenever possible.
- Optimize Loops: Use efficient loop constructs (`for`, `while`) and minimize nested loops to reduce execution time.
- Avoid Subshells: Minimize the use of subshells (`$(…)`) to reduce overhead and improve script performance.
- Use Built-in Commands: Prefer built-in commands (`echo`, `printf`) over external commands to avoid spawning new processes.
86. Explain the use of `vmstat` command.
Ans:
The `vmstat` command in Unix reports virtual memory statistics including system processes, memory usage, paging activity, block IO, and CPU usage. It helps monitor and analyze system performance in real-time, providing valuable insights into resource utilization and system bottlenecks. For example, `vmstat 1` displays updated statistics every second, aiding administrators in identifying and resolving performance issues promptly.
87. How is a shell script debugged in Unix?
Ans:
- Debug Mode: Enable debug mode with `set -x` at the beginning of the script to trace each command’s execution sequence.
- Echo Statements: Insert `echo` statements strategically throughout the script to print variable values and verify the script’s flow.
- Syntax Checking: Validate the script’s syntax using `bash -n script.sh` to catch syntax errors before execution.
- Error Handling: Implement robust error handling mechanisms using `trap` or `if` statements to catch and manage script errors effectively.
88. How are large files handled in Unix?
Ans:
- Use of Commands: Utilize commands like `split`, `cat`, and `grep` for file manipulation tasks such as splitting large files into smaller parts, concatenating files, and searching within files.
- Optimization Strategies: Optimize file access patterns and disk space utilization to improve overall performance and reduce processing time.
- Text Processing Tools: Employ tools like `awk`, `sed`, and `grep` for efficient text processing and data extraction from large datasets.
89. What is the `dmesg` command used for?
Ans:
The `dmesg` command in Unix retrieves and displays kernel ring buffer messages, providing valuable information about system hardware, device initialization, and kernel events. It helps administrators diagnose hardware issues, track system changes, and troubleshoot boot problems by examining the kernel’s logged messages. For example, `dmesg | tail` displays the last few lines of kernel messages, aiding in real-time system monitoring and diagnostics.
90. What methods are used to monitor system performance in Unix?
Ans:
- Command-Line Tools: Use commands like `top`, `htop`, and `vmstat` to monitor CPU usage, memory consumption, and disk activity in real-time.
- Network Monitoring: Employ tools like `netstat`, `iftop`, and `nload` to monitor network connections, traffic, and bandwidth utilization.
- Log Analysis: Review system logs (`/var/log/messages`, `syslog`) and application logs to identify performance bottlenecks, errors, and system anomalies.






