
Cognizant interview questions cover a wide range of topics, including technical skills, problem-solving, and behavioral traits. Candidates can expect questions related to software development, data analysis, and systems design, along with scenarios that test their critical thinking. Preparation should focus on core technical concepts, industry knowledge, and demonstrating strong communication skills. Practicing common interview questions and understanding Cognizant’s work culture can help boost confidence for a successful interview.
1. What are the testing types in software development?
Ans:
Software development includes various types of testing for delivering high-quality, fully functional, high-quality applications. The three primary types are:
- Unit testing, checking the rightness of the individual components.
- Integration testing, checking the interaction among the integrated components.
- System testing, checking the whole and integrated application.
2. Describe the waterfall model in the process of software development.
Ans:
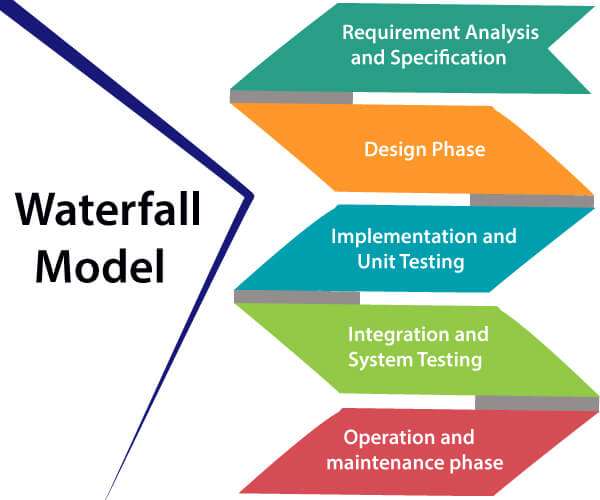
The waterfall model is a linear and sequential approach to software development. In this Model, one phase must be completed before the next phase begins. It usually involves requirements gathering, system design, implementation, testing, deployment, and maintenance. It insists on extensive documentation and phased systematic planning, thus making it efficient for projects with well-defined requirements.
3. What is Agile methodology, and how does it differ from the waterfall model?
Ans:
Agile methodology is an iterative and incremental approach to software development that emphasizes flexibility, collaboration, and customer feedback. Unlike the waterfall model, which has rigid and linear phases, Agile calls for adaptive planning and emphasizes continuous improvement through short development cycles known as sprints. Agile teams involve stakeholders throughout all stages of development. Requirements are gathered along the development journey, and changes and refinements can be made when necessary.
4. What is Continuous Integration, and why is it important for DevOps?
Ans:
- CI automatically integrates individual developers’ contributions into a shared mainline of the software, typically every few hours or more often.
- Each integrated version has automated tests applied to catch any bug as early as possible in the development cycle.
- The DevOps practice is significant as it promotes rapid feedback, reduces integration problems, and enables faster delivery of high-quality software.
- CI also fosters collaboration between team members and streamlines the deployment process.
5. How does Git do version control?
Ans:
- Version control in Git is a system for tracking changes to files over time so that one can retrieve particular versions of source files whenever needed.
- Git maintains a record of all modifications done on the project as committed. Each commit has a unique identifier, a timestamp, and an optional message describing the changes.
- There are many ways that developers can create branches for working independently on new features and merge those back into the main code base when they are ready.
6. What is DevOps, and how does it benefit?
Ans:
- DevOps is an approach of culture and technology that delivers efficiency, agility in IT service creation and management between development and operation teams across the entire software development lifecycle.
- DevOps maintains a culture of responsibility, communication, and collaboration, ultimately continuing to shorten development cycles, make deployments more frequent, and result in higher-quality software.
- Adopting DevOps practices benefits an organization with faster time-to-market, improved efficiency through automation, and increased IT and business alignment.
7. What is the difference between Agile and Waterfall methodologies in software development?
Ans:
| Aspect | Agile | Waterfall |
|---|---|---|
| Approach | Iterative and incremental | Sequential and linear |
| Flexibility | Highly flexible, accommodating changes easily | Rigid, changes are difficult and costly |
| Development Cycle | Short development cycles (sprints) | Long development cycles with distinct phases |
| Customer Involvement | Continuous collaboration with stakeholders | Limited involvement until project completion |
| Testing | Continuous testing throughout the development process | Testing occurs after the build phase |
8. Describe the MVC pattern.
Ans:
The Model-View-Controller (MVC) pattern is a software architecture pattern providing structured development by decoupling concerns in application development. The Model represents the data and the business logic, acting as a hub that performs data-related operations and manages the state. The View displays the data to the user and receives input from the user, essentially writing a user interface. The Controller is an intermediary that acts on user input by processing it, updating the Model, and then refreshing the View.
9. What are database transactions and what do we have ACID?
Ans:
Databases define a transaction as a series of operations considered one unit of work that would ensure data integrity and consistency. Every transaction must maintain the ACID properties Atomicity, Consistency, Isolation, and Durability. Atomicity guarantees that either all the operations under a transaction are accomplished or none of them; in other words, no partial updates occur. It ensures that the transaction takes the database from a state and transfers it to another valid state.
10. How does memory management work in Python?
Ans:
Memory management in Python involves a combination of automatic garbage collection and reference counting to handle memory allocation and deallocation. While an object is being created, Python instantiates its memory in the heap. Python keeps track of the number of references pointing to each object through a mechanism known as reference counting. When the reference count goes to zero, which means no more references point to the object and it is not in use, its memory can be recovered.
11. What are the types of testing in software development?
Ans:
- Software testing encompasses several types, all aimed at different objectives.
- Unit testing targets individual components or functions to ensure they work correctly in isolation.
- Integration testing refers to checks on interactions between combined components to detect issues in their interfaces.
- System testing assesses the overall system’s compliance with specified requirements.
12. What is the waterfall model in software development?
Ans:
- The waterfall software development model follows a linear and sequential process wherein each phase is completed sequentially before moving on to the next.
- This development model stresses clear documentation and planning at every phase of it such that changes become easier and trackable at each stage.
- Its structure needs to be more flexible, though by the time the project is started. The waterfall model is best suited for a project with well-defined requirements and few expected changes.
13. What is Agile methodology, and how does it differ from the waterfall model?
Ans:
- Agile methodology is an iterative and incremental approach for developing software with flexibility mixed with teamwork and collaboration joined with customer input.
- Unlike the waterfall model, where phases are very rigid in terms of sequence, Agile allows the overlap of phases and provides a reassessment of the project goals.
- This approach promotes adaptive planning and challenges teams to respond to changing conditions rapidly, delivering working software in much shorter timeframes.
14. What is continuous integration, and why is it important in DevOps?
Ans:
Continuous integration (CI) involves the changes made to the code being incorporated into a common repository frequently at or near several times a day. As a result, every time integration is made, it automatically checks through builds and tests, allowing problems to be detected and resolved much earlier in the development process. The use of CI reduces integration problems while reducing code quality and the pace of software delivery. CI promotes the spirit of teaming up and owning the entire codebase.
15. How does Git’s version control work?
Ans:
Version control in Git is all about maintaining changes to files and coordinating work amongst multiple contributors. Git makes changes to the source code repository through commits with a unique identifier and a snapshot of the project’s state. With a feature or fix, each developer can work individually without impacting the final codebase. Git’s distributed nature allows for local repositories so that developers work offline and may use a client tool to sync the changes with remote repositories where needed, hence improving collaboration and reducing conflicts.
16. Describe what DevOps is and its advantages.
Ans:
DevOps, in reality, is a social and technical movement that heavily focuses on collaboration between teams in development and operations to improve the delivery and performance of software. DevOps takes practices from both fields to automate and optimize the software development lifecycle, fostering a culture of shared responsibility. Some advantages obtained with DevOps include rapid go-to-market, high deployment frequency, and excellence in product quality within continuous feedback and testing.
17. Describe how to manage a merge conflict with Git.
Ans:
- If there is a merge conflict with Git, first identify files with disputes after trying to merge the branches.
- Open these files, where Git will highlight the conflicting areas so may go through those changes both branches brought about.
- Then, manually edit that file, ensuring the file has the result want to be. Save changes.
- Stage the changes of the resolved files with `git add`, and then commit the resolution, specifying in the commit message that conflicts were resolved.
18. Explain the MVC pattern.
Ans:
- MVC is a software architecture design that separates an application into three interrelated components Model, View, and Controller.
- The Model represents the application’s data and business logic, handling data and responding to requests for information.
- The Controller will mediate, update the Model as needed, and refresh the View when necessary.
- This separation of concerns will make the application more modular and easier to maintain, test, and scale.
19. What are database transactions, and what’s meant by ACID properties?
Ans:
- A transaction in a database is described as an ordered sequence of operations performed under one unit of work, keeping in mind the integrity of the data.
- Atomicity ensures that all or no operations under the transaction are completed to avoid partial updates. Consistency ensures that the transaction should bring the database from one valid state to another.
- Isolation prevents concurrent transactions from interfering with each other, and Durability ensures that once a transaction is committed, its effects are permanently recorded in the database.
20. How do Python memories work?
Ans:
Memory management in Python uses a combination of automatic garbage collection along with a memory allocation strategy. Memory management in Python is object-oriented, where each piece of data is treated as an object. The memory manager in Python deals with the allocation and deallocation of memory from an object or tracking of the memory occupied by objects to optimize performance, Python’s garbage collector automatically frees the memory so that don’t suffer from memory leaks.
21. What are collections in Java, and describe some types?
Ans:
Collections in Java are data structures that facilitate the storage, retrieval, and manipulation of groups of objects. Java defines interfaces and classes that enable developers to work with each collection type efficiently. Each type of collection offers certain benefits, so the developer must decide which type to implement based on the usage requirement.
22. What are error handling and management in a microservices architecture?
Ans:
Error handling in a microservices architecture can be attained through multiple strategies to provide system resilience and maintainability. Each service must have complete measures toward effective error handling, logging, and monitoring mechanisms for identification and reaction to failure. General practices include retries for short-duration errors, circuit breakers to prevent cascading failure, and graceful degradation to continue some functionality during an outage.
23. What is dependency injection?
Ans:
- Dependency Injection is an applied design pattern at the heart of software development; it promotes loose coupling among components.
- That is, it allows an object to get its dependencies from outside rather than to create them inside.
- Injecting dependencies makes components more reusable and maintainable because it reduces tight binding to a particular implementation.
- Several frameworks, such as Spring for Java, incorporate dependency injection it becomes much easier to have efficient lifecycle management of objects, encouraging cleaner architectures.
24. How does Java implement multithreading?
Ans:
- Java is designed so the multithreaded application can execute several threads together in a single program, better utilizing the CPU.
- Java provides built-in multithreaded programming via classes and interfaces `Thread` and `Runnable`.
- Extensive control of threads in Java is supported, and developers can manage their threads efficiently.
- Access checks to shared resources by multiple threads are supported via the synchronized blocks and locks.
- Proper multithreading usage makes Java applications run much more effectively, specifically in scenarios requiring parallel processing.
25. Define functional and non-functional testing?
Ans:
- Functional testing checks whether the application software behaves as expected against its requirements. It is done through unit testing, integration testing, and system testing.
- Non-functional testing involves checking aspects that affect the user’s experience with the system but have nothing to do with any specific function.
- This entails performance, security, usability, and reliability testing. Both tests must ensure the resulting software product is good enough and meets functional requirements and user expectations.
26. Explain the servlet lifecycle.
Ans:
The servlet lifecycle is governed by the servlet container, which comprises several significant stages. It starts with loading the servlet into the memory by the container, which invokes the `init()` method to initialize the servlet and allocate the essential resources. The servlet then serves the client requests through its `service()` method. When the servlet has performed its duty, it may be forced out of memory, so the container will now invoke the `destroy()` method to release these resources.
27. What is the main difference between ArrayList and LinkedList in Java?
Ans:
ArrayList and LinkedList are two of the most used implementations of the List interface in Java; they have different characteristics. ArrayList uses a dynamic array to hold elements internally, so elements can be accessed fairly quickly with direct indexing, but it could be slower for sequential accesses, like iteration. LinkedList is implemented as a doubly-linked list, in which insertion and deletion are efficient at both ends but carry slower access times since elements must be traversed sequentially.
28. How do web applications manage sessions?
Ans:
Session management for web applications tracks user interactions by preserving the state between multiple requests. Whenever someone accesses the application, a session is created automatically, often stored server-side, and managed through a unique session ID. This ID is typically returned to the client as a cookie, which the server can use to look up and retrieve the appropriate session data upon subsequent requests. Session management is critical to enabling user-specific experiences, ensuring user authentication, and temporarily storing information.
29. Outline what SOLID principles in software design are.
Ans:
- SOLID is a set of five design principles that intend to make software designs more scalable and maintainable.
- A class should have just one reason to change, meaning it should have only one responsibility.
- Software entities should be open for extension but closed for modification.
- Subtypes should be substitutable for their base types without affecting the program’s correctness.
- Clients should not be forced to depend on interfaces they do not use, thus promoting smaller, more focused interfaces.
30. What is a deadlock in a system? How would one go about avoiding one?
Ans:
- A deadlock occurs in a system when two or more processes cannot move forward as each waits for the other to relinquish resources.
- This situation may lead to a complete execution deadlock in which the system performance and productivity severely deteriorate.
- A variety of strategies are available for avoiding deadlock resource ordering, so the resources are always requested in a fixed order.
- All these strategies can be factored into the system to maintain very high levels of performance and reliability.
31. What is inheritance in OOP?
Ans:
Inheritance is the most basic concept of OOP, where a new class or derived child class acquires characteristics, properties of another existing class referred to as the base or parent class. This promotes code reusability, and developers can design a hierarchy of classes sharing common functionalities while permitting specific features in the derived classes. Inheritance may be single or multiple, depending on whether one class or several classes inherit from another or other courses.
32. What is database normalization?
Ans:
- First Normal Form (1NF): This eliminates any form of duplicating information and ensures that each column contains atomic values.
- Second Normal Form (2NF): This eliminates partial dependencies, coupled with the fact that non-key attributes depend on the whole primary key.
- Third Normal Form (3NF): This eliminates transitive dependencies, ensuring that the non-key qualities do not rely on other attributes that are not even part of the key.
33. What is the difference between DELETE, TRUNCATE, and DROP statements in SQL?
Ans:
In SQL, the DELETE statement is used to remove specific rows from a table based on the specified condition; therefore, fine-grained control can be employed by the users over which record to delete. TRUNCATE deletes all rows from a table in the minimum time with no record of individual row deletions. The DROP is the most extreme statement that has eliminated a table and its structure from the database, including all associated data, indexes, and constraints hence, it’s irrecoverable without a backup.
34. What is load balancing, and why is it so important?
Ans:
Load balancing is the distribution of network traffic or workloads across multiple servers to ensure that resources are utilized to their best advantage so that response time can be minimal while no single server becomes a bottleneck. It plays an essential role in enhancing the availability and reliability of applications by routing requests to the least busy server, which improves user experience and ensures service continuity. Besides managing traffic, load balancers can also perform health checks to evaluate servers’ performance and send traffic away from failed servers.
35. What is the difference between a process and a thread?
Ans:
A process is an independent program in execution that has its own memory space, system resources, and execution context, thereby allowing it to run independently of other processes. However, a thread is an even smaller process unit and can run concurrently with the others; it shares the same memory space and resources of the parent process, making communication between threads more efficient. Processes are isolated, which enhances security and stability, this isolation means that communication between processes requires more overhead.
36. How does Docker containerization work?
Ans:
- Docker containerization is a technology that allows developers to package an application and its dependencies into lightweight, portable containers that will run uniformly across different environments.
- Each container encapsulates the application with all the libraries and configurations required so that the same application behaves the same way, local, cloud, or off-premise.
- Docker uses a layered file system where any change is realized as an individual layer, which makes efficient storage and sharing of images feasible.
37. Describe Big-O notation and why it’s useful in algorithm analysis.
Ans:
- It provides an upper bound on an algorithm’s running time or space usage, letting developers classify algorithms based on the scaling and performance characteristics.
- Big-O notation is important for comparing algorithms and determining which would most appropriately solve a problem when performance is critical.
- Using Big-O, developers can analyze algorithms, identify potential bottlenecks, and therefore write more efficient code. Big O is an integral part of good algorithm analysis and system design.
38. What is a binary search tree, and how does it work?
Ans:
- A BST is a data structure that keeps elements in sorted order so they may be searched, inserted, and deleted efficiently.
- In a BST, each node has at most two children: the left child contains values smaller than the node’s value, whereas the right child holds values greater than the node’s value.
- Each comparison helps eliminate half of the elements left in the tree, resulting in an average time complexity of O(log n) on any search operation.
- Binary search trees provide a balanced data storage and retrieval treatment while optimally utilizing memory.
39. How to improve the performance of a web application?
Ans:
Improvement of the performance of a web application is feasible through various techniques and best practices. The front-end resources can be optimized by compressing images, minifying CSS and JavaScript files, and lazy loading images, among others, to reduce the load times. On the server side, the response time can be improved and managed by using mechanisms to optimize caching, load balancing, and database techniques. Using Content Delivery Networks reduces latency because server placement is often in geographically closer locations.
40. What is Data modelling?
Ans:
Data modelling represents designing an abstract representation of the modelled business operation. It is very important because it offers a usable model of the real world upon which a developer can build and create his program. Data modelling produces a conceptual model of the data structure, relationships, and constraints in a database system. It offers a plan of how data would be organized and defined and how it should be stored, accessed, and managed to ensure clear interaction between stakeholders in and out of the development camp, including business users, data analysts, and developers.
41. What is unit testing, and which tools are most commonly used?
Ans:
Unit testing is a software test type where individual units or functions of a software application are tested in isolation to ensure that the output follows the expected behaviour. In this manner, bugs can be detected early in the development cycle. This will make fixing problems easier before integrating into a larger system. Unit testing frameworks are provided as widely accepted standard tools to perform unit testing. These frameworks provide structures for writing and running tests and typically provide tools for automating testing.
42. What is NoSQL compared to relational databases?
Ans:
- NoSQL databases are mostly different from relational databases since their data models are designed for processing unstructured or semi-structured data rather than a fixed schema.
- NoSQL is generally good for the use of applications which must be highly scalable and high-performance, where one needs to process real-time data and big data analytics at its best.
- NoSQL databases provide horizontal scaling, making the distribution on multiple servers easier than some relational databases that go for vertical scaling.
43. What’s the role of an API gateway in a microservices architecture?
Ans:
- It centralizes request routing, composition, and protocol translation, which makes communication between clients and multiple services easier.
- With rate limiting and caching alongside, authentication is one of the main features an API gateway can deliver in improving security and performance without increasing complexity for client applications.
- The level of abstraction away from cross-cutting concerns frees up specific microservices to focus on their core functions without having some additional responsibility.
44. How will security concerns in web applications be addressed?
Ans:
- Security concerns in web applications will be met through best practices, frameworks, and tools designed to thwart various threats.
- One of the ways this can be achieved is through secure coding practices such as input validation and output encoding.
- They minimize common vulnerabilities, like SQL injection and cross-site scripting (XSS).
- Periodic security assessments- for example, penetration testing and vulnerability scanning- can determine weaknesses needing remediation.
45. What is the difference between stack and heap memory?
Ans:
Stack and heap are two different types of memory allocation spaces used in programming. Stack Memory This memory region stores local variables and information related to the function calls it automatically manages them in a Last In, First Out structure. Even though stack memory is faster than heap memory when it comes to allocation or deallocation, its size is limited, and an overflow of the stack can occur. Assign space to objects and data structures whose size cannot be determined during compile time.
46. What are design patterns?
Ans:
A design pattern is a reusable solution to a commonly occurring problem in software design that provides a template of a solution for a particular situation that an individual faces when trying to get their work done during the design phase of a software system. Design patterns are known best practices that encapsulate a solution to a frequently occurring problem, such as maintainability, scalability and reusability of code. One of the common patterns is the Singleton pattern.
47. How are large datasets handled in Python?
Ans:
Working with big data in Python usually involves applying specific libraries and tools that optimize for performance and memory. Pandas is another library that allows to efficiently manipulate data for analytic purposes, with data frame operations optimized for memory usage. Techniques such as chunking are applied where very large data sets are large enough to exceed the memory limits. Dask offers parallel computing on larger-than-one-machine size datasets.
48. What are SOAP and REST web services?
Ans:
- SOAP and REST are two different architectural styles that can be used to build web services.
- SOAP protocol uses XML to format messages and typically relies on HTTP or SMTP for message transmission.
- GET, POST, PUT, and DELETE, giving more flexibility as it supports multiple data formats like JSON, XML, and HTML.
- REST is easier to use and more efficient for web-based applications, while SOAP is an enterprise-level services.
49. What is Kubernetes, and how does it orchestrate?
Ans:
- This forms a great foundation for managing clusters of containers to ensure throughput and scalability are achieved by distributing workloads across multiple nodes.
- In Kubernetes, such features, which can be imagined as automatic load balancing and self-healing along with rolling updates, offer so much added resiliency for running applications in production.
- By this abstraction of the underlying infrastructure, developers no longer have to concern themselves with infrastructure and can rather focus solely on developing the application.
50. What are the differences between Angular and React?
Ans:
- Angular and React are popular frameworks for building web applications, but their design philosophies and usage differ.
- It has many built-in features like dependency injection, routing, and state management support, with a structured approach to development.
- React is just a library from Facebook that mainly deals with building user interfaces, and developers can make reusable UI components.
- Although Angular uses two-way data binding, React uses only one-way data binding for a controlled state management system.
51. How is memory management different between C++ and Java?
Ans:
Memory in C++ is manually allocated and deallocated, where developers need to use `new` and `delete` keywords. Therefore, developers have ultimate control over the memory but face an increased risk of memory leaks and segmentation faults if not utilized properly. In opposition, Java uses automatic garbage collection, periodically reclaiming unused memory. This takes the burden off developers but results in performance predictability since garbage collection pauses the application.
52. What are WebSockets, and how do they differ from HTTP?
Ans:
The conventional WebSocket creates a full-duplex communication channel over a single, long-lived connection to provide real-time data exchange between the client and the server. Compare this with HTTP or HTTP requests and responses, where every transactional interaction requires a new connection, but continuous data flow is permitted following the initial handshake in WebSockets. In addition, WebSocket connections consume lesser bandwidth due to the absence of overhead created by new HTTP connections for each request.
53. How does a distributed database system ensure consistency?
Ans:
A distributed database system uses consistency models, either strong consistency, eventual consistency, or causal consistency, for keeping consistency. Ensures all nodes reflect the most recent write operations before any read operations occur and often uses protocols like Paxos or Raft. Replication and consensus algorithms form a big part of the control mechanism over consistency to maintain information being in sync between nodes.
54. State CAP theorem and its meaning.
Ans:
- Consistency all nodes look at the same thing simultaneously. Availability that every request gets an answer. Partition tolerance that operation continues when the network partitions.
- The theorem implies that allocating two out of three attributes often means trade-offs, so the system sacrifices consistency for availability in the case of network trouble.
- Understanding CAP helps architects make informed decisions about system design from what an application needs.
55. What’s so special about indexing in databases? How does indexing improve the speed of a query?
Ans:
- Indexing is the database technique to improve query performance by a data structure that supports faster retrieval of records.
- It works like a book’s index. The database can find the needed data directly without scanning the whole table.
- Properly designed indexes, dramatically reduce the time complexity of searches, especially for large data sets, which means faster responses to queries.
- Indexing, brings trade-offs, such as increased storage requirements and overhead during writes because the indexes have to be updated.
56. Explain what is the structure of a JWT?
Ans:
A JSON Web Token (JWT) is a compact, URL-safe means of representing claims to be transferred between two parties. It contains three parts: the header, payload, and signature. The header will specify the type of token, which in this case is JWT, and the signing algorithm used. The payload will contain claims, statements about an entity, usually the user, and, depending on the use case, extra metadata. Exchange and is very common in the algorithms applied for authentication and authorization.
57. What is a race condition, and how can we prevent it from occurring in multi-threaded applications?
Ans:
A race condition in multi-threaded applications is when multiple threads try to access shared resources to update them in parallel. Access to shared resources can also be controlled using synchronization mechanisms such as locks, semaphores or mutexes and risk reduction against race conditions is also possible using thread-safe data structures or through designs that minimize shared state. Careful design and implementation of concurrency controls are essential to ensure thread safety in multi-threaded applications.
58. How can caching enhance the performance of a web application?
Ans:
Caching enhances the performance of a web application by temporarily storing frequently accessed data in a fast-access storage layer, reducing the need to fetch data repeatedly from its source. This reduces latency and helps improve response time for users, especially in applications that deal with large datasets or high traffic volumes. The server and the database experience less stress because most of the load is carried forward through serving cache responses, it offers improved scalability and resource usage.
59. What is two-factor authentication, and why does it matter to security?
Ans:
- 2FA is a security process of authentication that requires distinct forms of verification for users to access an account can enhance the protection against unauthorized access.
- This layer of security is essential in that it addresses compromised password risks, the most common mode of attack.
- The two forms of identification necessary to access the account make it much harder for attackers to reach confidential information.
- That is why 2FA has spread widely across various platforms to protect users’ accounts and sensitive data.
60. How does OAuth 2.0 work, and what are its use cases?
Ans:
- OAuth 2.0 is an authorization framework that allows third-party applications access to user accounts on an HTTP service while keeping the user’s credentials secret.
- Its operation is based on an authorization process where the user grants permission to a given application to access the data hosted by a service provider.
- Applications of OAuth 2.0 come in handy, where users can use their existing accounts in services such as Google or Facebook to sign in and let applications securely access user data from APIs.
61. What is a load balancer, and how does it distribute traffic?
Ans:
- A load balancer is a device or software application which spreads the network or application traffic across multiple servers so that no server is overloaded with a single burden.
- It ensures optimized resource usage and improved responsiveness of an application and adds fault tolerance through intelligent routing of requests by any number of algorithms.
- This redundancy ensures high availability and reliability when such applications are needed hence, a load balancer is a primary component in present architecture with very high-traffic web applications.
62. How does an SQL injection attack work?
Ans:
SQL injection is the inclusion of injections of code into the server using flaws in an application’s software that enables an attacker to execute malicious SQL code at a database by inputting malicious SQL code in user input fields to allow them to access, modify, or delete database records improperly. To prevent SQL injection, developers should use parameterized queries or prepared statements, which separate SQL logic from user input, making it impossible for malicious data to alter the query structure.
63. Compare and contrast a monolithic architecture versus a microservices architecture.
Ans:
A monolithic architecture is considered a homogeneous structure of software in which all the components that constitute an application are integrated and run together as an entity. This might make development and deployment easier but can raise scalability and maintainability issues as the application scales. In contrast, the microservices architecture separates applications into smaller, independent services that could be developed, deployed, and scaled independently.
64. What are container orchestration tools, and why are they required?
Ans:
Container orchestration tools manage containerized applications’ deployment, scaling, and operation. They automate the scheduling of containers while ensuring optimal resource allocation, load balancing, and service discovery across clusters of machines. With such an orchestration, managing several containers by hand would be easier, especially in a production environment where it is necessary to ensure high availability. These tools ensure a smooth operation, increase resilience and consume resources efficiently.
65. What is a CDN (Content Delivery Network)?
Ans:
- A Content Delivery Network (CDN) is a network of servers that delivers web content directly to users based on locality.
- The distributed nature of CDNs cuts latency and permits faster loads for users through caching content like images, videos,eos, and static files on multiple servers worldwide.
- Serving content from its nearest edge server reduces the distance data needs to travel and thus gives a quicker response.
- CDNs are significantly enhancing performance and scalability for distributed websites all over the world.
66. Explain the function of environment variables in application setup.
Ans:
- Environment variables are run-time values stored externally from the application code. This means that environment variables make configuration possible without hard coding sensitive information.
- They provide a flexible mechanism to manage configuration settings, such as database credentials, API keys and service URLs, across environments-developing, testing, or production.
- Indeed, by using environment variables, without code modifications, make applications differ for different environments, thus easing deployment and maintenance activities.
- It supports better practices in DevOps like easier automation and containerization through managing configuration through environment variables.
67. How does TLS/SSL encryption help secure data transmission?
Ans:
- TLS (Transport Layer Security) and SSL (Secure Sockets Layer) are cryptographic protocols that help protect communication over networks like the Internet.
- It uses a combination of both symmetric and asymmetric encryption to ensure that it establishes a secure communication channel between a client and a server.
- The handshake process of the client and server authenticate to each other through digital certificates and produce a symmetric session key that encrypts the data during transit.
68. What are the advantages and disadvantages of serverless architecture?
Ans:
Serverless architecture enables developers to develop and operate their applications on the cloud without having concerns with infrastructure as a server. As such, this mode is associated with higher agility and lower overhead in running the operation. Its advantages include scalability, cost efficiency because of pay-as-you-go pricing models, and easier deployment processes since one has time to focus much on code writing and has less reason to worry about server management.
69. Describe “eventual consistency” in distributed systems.
Ans:
Eventual consistency is a model of distributed systems where updates to data eventually propagate through the system and become available, eventually consistent, though only sometimes immediately. It benefits applications that stress the need for systems to continue operating despite network failures and other partial failures. Although eventual consistency does enable systems to scale and provide good performance, this mechanism requires a plan to address coincident updates from multiple nodes.
70. What is a message queue, and why is it important in distributed applications?
Ans:
A message queue is a communication technique in the distributed applications of asynchronous messages passing between the components or services. It enables the producers to send messages into a queue from which consumers take them at their convenience, thus decoupling senders and receivers, with reliability heightened through the absence of lost messages because the consumer is unavailable.It enables systems to perform at their respective paces while executing tasks, improving performance and scalability.
71. What is one way of resolving a challenge of a project?
Ans:
- To solve a project challenge, state clearly how the problem is happening and collect information related to the situation, enabling to understand its root causes.
- Ask stakeholders and people in the team to brainstorm to come up with possible solutions and assess their feasibility. Implement a solution by creating a structured plan, measurable goals, and a timeline.
- They have to monitor the progress accordingly; collecting feedback is important to know how effective the solution is or if there is a need for adjustments.
72. How do firms manage tight deadlines with unclear requirements?
Ans:
- Communication and flexibility should be prioritized when managing tight deadlines with unclear requirements. Break down the work items into smaller units that can be handled continually assessed.
- Begin by involving stakeholders to define basic features and identify the minimum viable product needed to start delivering.
- Monitor and update project timelines with the team so that the expectations are met and the team remains aligned to focus on delivering value under pressure.
73. If a bug occurs in production after release, how should one act?
Ans:
- Evaluate whether this bug is relatively severe, impacting users, not just. Communicate clearly with stakeholders about the problem and the anticipated timeframe until that point.
- Apply the solution but ensure that testing has been done to ensure the bug is indeed fixed and other problems are not introduced as a byproduct of the fix.
- Then, recreate the bug in a test environment identify the source of the bug, then devise a patch for the bug deploy the solution to production, keep an eye open for additional problems.
74. How to handle feature changes near the end of a development cycle?
Ans:
Treat every feature change like a potential requirement and measure its impact on timelines and resources. Gather the team with stakeholders for discussion – discuss the necessity and benefits of the change from the standpoint of risks of delaying the release. If it is judged to be essential, then prioritize it and scope or time arrange the project. Implement iterative, agile practices, such as sprints, to slowly integrate these changes with a concentration on core functionalities.
75. How to handle a team dispute over feature implementation? What is the procedure?
Ans:
Begin by holding an open discussion where each party can present his opinions and concerns. Encourage active listening to understand all perspectives. Identify the common goals and assess the merits of each approach to those goals. Share with a neutral third party or manager to help mediate the discussion so that the parties can reach a consensus for implementation. Finally, decide based on the project’s best interest and write down what has been agreed to avoid rehashing misunderstandings.
76. How to approach learning of new technologies expediently?
Ans:
Learning a new technology is approached through a structured plan by clearly setting goals and finding key resources such as online courses, documentation, and tutorials. Participate in forums or go to local meetups that would allow one to learn from experienced practitioners in the community and gain knowledge about applying skills learned. Finally, seek responses from colleagues or a mentor to seek insight into what can be done better and further.
77. What should be done when a critical system goes down outside working hours?
Ans:
- When outside of working hours, in case a critical system goes down, the process starts by immediately contacting the on-call support team or assigned personnel.
- One needs to analyze the situation and collect relevant information to know how grave the problem is and then diagnose it. Log in remotely to the system to identify a quick fix or workaround.
- Conduct postmortem analysis once the system has been returned to enhance diagnoses of root cause and implement proper prevention measures for the future.
78. How to mitigate a potential security vulnerability in an application?
Ans:
- Deal with an application vulnerability by first assessing the risk and impact of such vulnerability on the system and its data.
- Then, attempt to fix or mitigate as soon as possible, especially on highly risky vulnerabilities.
- This would require thorough testing to ensure the solution doesn’t expose a new vulnerability, which should be documented for auditing and compliance requirements.
- At the same time, stakeholders may need to be informed about the vulnerability and what remedial measures were taken.
79. How to lead unclear priorities of tasks in the absence of a manager?
Ans:
- Team members should collectively evaluate the workload and determine which activities are most crucial and relevant to the project.
- The team should meet to discuss prioritization and vote on what needs to be attended to first based on its urgency and importance.
- Open up a communication channel with the team for general updates and challenges. If impactful, discuss issues through higher management to find common ground on priority alignment.
80. What are the action if a team is behind on deliverables.
Ans:
This may involve reviewing project timelines, resources, and probable setbacks that have stalled the work. There is a need to discuss with the team, get insight into what could have led to the slowing down, and brainstorm how to get back to the normal schedule. Then, tasks should be prioritized by emphasizing the essential deliverables and redistributing the responsibilities among the team members for efficiency. Ensure that an agile practice, such as daily stand-ups, is followed to keep stakeholders accountable and check regularly on the progress of activities.
81. How can frequent stakeholder requests for updates be managed to maintain productivity?
Ans:
Establishing a regular communication schedule, such as weekly or bi-weekly meetings, to provide status reports on project progress can manage frequent stakeholder requests for updates. Implementing project management tools like dashboards can also facilitate transparency, allowing stakeholders to access real-time information without disrupting the development process. Balancing communication with focused work periods can maintain productivity while keeping stakeholders informed.
82. How can coding standard issues with teammates be handled?
Ans:
- Initiating open discussions about the importance of coding standards can help emphasize their role in maintaining code quality and team cohesion.
- Regular code reviews and pair programming sessions provide opportunities for real-time feedback and reinforcement of standards.
- Creating a shared coding guideline document can serve as a reference for the team, promoting consistency in coding practices.
- Fostering a continuous learning and improvement culture encourages team members to address issues collaboratively rather than defensively.
83. What steps should be taken to address customer complaints regarding a feature?
Ans:
Addressing customer complaints about a feature involves a structured approach to understanding and resolving the issue. First, listening to the customer’s concerns and gathering detailed information about their experience is essential. This information should be analyzed to identify the root cause of the complaint, whether it’s a usability issue, a bug, or a misunderstanding of the feature’s functionality. Communicating transparently with the customer about the steps to resolve the issue and providing regular updates can help rebuild trust.
84. How should last-minute requirement changes be managed?
Ans:
Managing last-minute requirement changes requires flexibility and effective communication. First, assessing the impact of the change on the project timeline and resources is crucial to determine feasibility. Engaging stakeholders in discussions about the necessity and implications of the change helps ensure alignment and understanding. Re-prioritizing tasks and adjusting the project plan can accommodate the new requirements while minimizing disruption.
85. How can scope changes in a project be communicated effectively?
Ans:
Effective communication of scope changes in a project involves clarity, transparency, and engagement with all stakeholders. When a change is identified, it’s important to document the details, including its reasons, its implications on the project timeline and budget, and how it affects current tasks. Providing written communication, such as an updated project plan or scope document, reinforces the changes and serves as a reference for the team. Ensuring ongoing communication throughout the project about any further adjustments helps maintain alignment.
86. What support can be offered when a colleague struggles with workload?
Ans:
- When a colleague struggles with workload, offering support can help alleviate stress and improve team performance.
- First, initiating a private conversation to understand their challenges demonstrates empathy and provides an opportunity to identify areas where assistance is needed.
- This might include helping prioritize tasks, redistributing workloads among team members, or assisting with specific projects.
- A supportive environment where team members feel comfortable seeking help enhances collaboration and morale.
87. What should be done if a performance bottleneck is identified in an application?
Ans:
- Suppose a performance bottleneck is identified in an application. In that case, the first step is to conduct a thorough analysis to pinpoint the exact source of the issue, whether it’s related to database queries.
- Once the bottleneck is diagnosed, optimization strategies can be implemented, such as refining database queries, enhancing caching mechanisms, or optimizing code.
- Conducting load testing post-optimization helps ensure the improvements are effective under various conditions. Documenting the findings and solutions contributes to future maintenance and optimization efforts.
88. How can multiple high-priority tasks be managed when deadlines conflict?
Ans:
- Managing multiple high-priority tasks with conflicting deadlines requires effective prioritization and organization.
- Utilizing a prioritization framework like the Eisenhower Matrix helps distinguish between urgent and important tasks, allowing for strategic focus on what matters most.
- Communicating with stakeholders about the situation can help set realistic expectations and negotiate deadline extensions or adjustments.
- Employing time management techniques, such as time blocking, can aid in dedicating focused periods to each task, ensuring steady progress despite competing demands.
89. What steps ensure code quality in a critical project?
Ans:
Ensuring code quality in a critical project involves implementing best practices throughout the development lifecycle. First, establishing coding standards and guidelines provides a consistent framework for all developers. Regular code reviews foster collaboration and facilitate knowledge sharing, allowing team members to catch issues early and learn from each other. Incorporating automated testing, including unit and integration tests, helps validate code functionality and catch regressions before deployment.
90. What strategies ensure the successful integration of a legacy system into modern architecture?
Ans:
Integrating a legacy system into a modern architecture requires careful planning and execution. First, thoroughly assessing the legacy system’s capabilities, dependencies, and data flows is essential to understand its current functionality and limitations. Developing a phased integration strategy, which might include wrapping legacy components as services or gradually replacing them with modern alternatives, helps minimize disruption. Ensuring data migration is handled carefully, guarantees data integrity and continuity.




