
- Introduction to CyberArk
- What is CyberArk?
- What is a Privileged Account?
- History of CyberArk
- Industries using CyberArk
- CyberArk Benefits
- CyberArk Architecture
- CyberArk Components
- CyberArk Implementation
- CyberArk Tools
- Capabilities
- Prerequisite
- Conclusion
- Administrator on a Windows server
- Root on a UNIX server
- Cisco Enable on a Cisco device
- Embedded passwords found in applications and scripts
- CyberArk is predominantly a security tool used for the safety of privileged accounts through password management. It protects the privileged accounts within the organizations by way of maintaining the passwords automatically. Using the CyberArk tool, you’ll store and maintain data by rotating the credentials of all the important accounts so that you’ll defend against malware and hacking threats efficiently.
- Being a highly protective tool, CyberArk is employed in industries like energy, healthcare, financial services, retail, etc. The importance of CyberArk is such it’s been operated by about 50% of the Fortune 500 organizations across the world.
- CyberArk is an Israeli company having its headquarters located at Petah, In Israel. Its USA office is located in Newton and it also features a company in EMEA, Asia Pacific, and Japan. It had been established in 1999 by Udi Mokady, an alumnus of Boston University’s Metropolitan College.
- Since its inception, the corporate has focused on helping organizations in protecting them from cyber-attacks and now it’s one of the foremost reputed cybersecurity companies within the world. From being a start-up, Cyber-Ark rose to the extent of a public Ltd. and was listed within the NASDAQ stock exchange.
- In the previous six years, it’s reached on an additional spree contracting corporations like Viewfinity, Conjur Inc, and Vaultive. Among these groups, Viewfinity and Conjur Inc are Massachusetts-based having shares in claim administration and application control software and cloud services, respectively. CyberArk has earnings of $343 million as of 2018 and an ahead capacity of 1,380 as of Q4 2019.
- Computer Software
- Information Technology and Services
- Financial Services
- Banking
- Insurance
- Hospital & Health Care
- Retail
- Utilities
- Computer Hardware
- Human Resources
- Digital vault
- Password Vault Web Access
- Central Policy Manager
- Privileged Session Manager
- Privileged Session Manager for SSH
- Privileged Session Manager for Web
- On-Demand Privileges Manager
- AD Bridge for NIX
- Privileged Threat Analytics
- SSH Key Manager
- Vault – Conjur Synchronizer
- Event Notification Engine
- Component Version
- 32 core processors (Intel compatible 2.1 GHz – 2.6 GHz)
- 32GB RAM.
- 2X 250GB SAS hot-swappable drives (15K RPM)
- RAID Controller.
- Network adapter (1Gb)
- DVD ROM.
Introduction to CyberArk:
CyberArk’s Privileged Access Security may be a full life-cycle solution for managing the foremost privileged accounts and SSH Keys within the enterprise. It enables organizations to secure, provision, manage, control, and monitor all activities related to all kinds of privileged identities, such as:
What is CyberArk?
What is a Privileged Account?
An account, which may be called a privileged account, is that one, which has access to information like Social Security numbers, MasterCard numbers, PHI information, etc. However, from a broader perspective, the definition of a privileged account depends on the sort of privileged data within the organizations. A number of the privileged accounts in organizations include local admin accounts, privileged user accounts, domain admin accounts, emergency accounts, service accounts, and application accounts, etc.
History of CyberArk:
Industries using CyberArk:
If we glance at which companies are using CyberArk the foremost, the pc software industry tops the list and therefore the least is human resources. Here is the complete list of industries that use the CyberArk tool.
CyberArk Benefits:
Being a pacesetter in cybersecurity solutions, CyberArk provides immense benefits to organizations. a number of these benefits include the following:
Ease of tracking credentials: With CyberArk Privileged Account Security Solution, you don’t get to keep track of the passwords manually. Instead, what you would like to try to do is to trace only CyberArk credentials. that might suffice. the remainder is going to be taken care of by CyberArk.
Increased time savings: Since CyberArk is powered with automated password management capabilities; there’ll be less time consumption in password management.
Absence of sameness in revising guidelines: Since CyberArk equips admins to work and correct privilege guidelines for users centrally; there won’t be any monotony in revising policies.
Propagation of password discrepancies across the applications: CyberArk provides management of database passwords centrally and ensures propagation of password change across all the dependent applications and services. This leads to the elimination of the danger of broken processes. It also leads to preventing the danger of revenue loss with every password change.
Apart from the overhead, a digit of the contrasting uses of CyberArk includes – management and security of all privileged accounts and SSH Keys, managing access to privileged accounts, creating and monitoring privileged sessions, working application and repair credentials, enabling compliance with audit and regulatory requirements, and seamless integration with enterprise systems, etc.
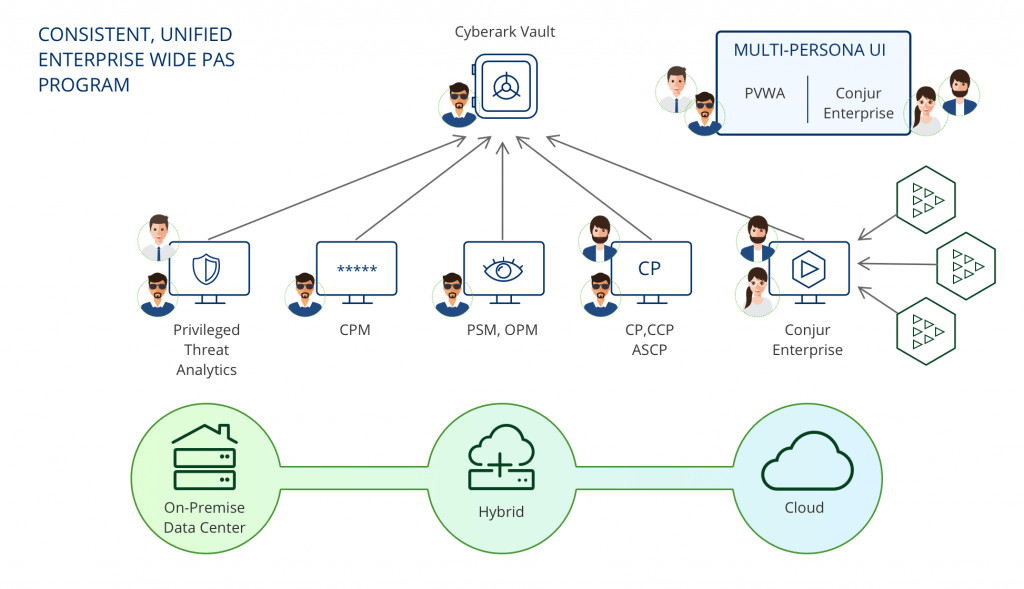
CyberArk Architecture:
At the heart, the CyberArk Privileged Access Security solution includes numerous layers delivering highly secured keys for keeping and sharing passwords within the communities. These coatings include – Firewall, VPN, Authentication, Access control, Encryption, etc.
The architecture consists of the following major elements:
Storage Engine: The storage engine, which is additionally called a server or vault, holds the info. It also ensures securing the info and authenticated and controlled access.
Interface: The responsibility of the interface is to speak with the storage engine and also provide access to users and applications. The communication between the storage engine and therefore the interface occurs through the vault protocol, which may be a secure protocol of CyberArk.
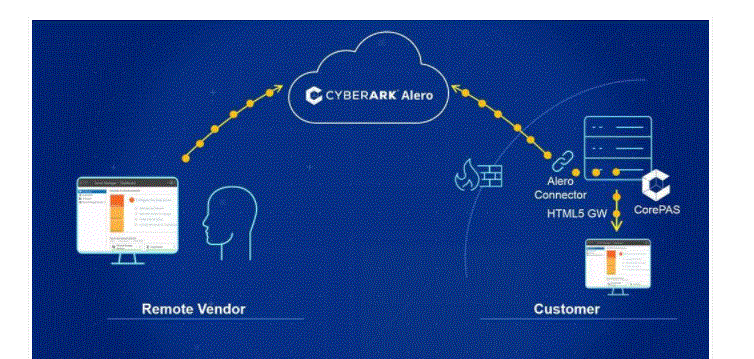
CyberArk Components:
The following are the components of CyberArk:
Digital Vault: The Digital Vault is the most secure place within the network where you’ll store your confidential data. Since the pre-configured, it’s readily usable.
Password Vault Web Access: this is often an internet interface, which allows the management of privileged passwords. As a part of password management, you’ll use this component to make new privileged passwords. The interface features a dashboard, which provides you to look at the activity within the security solution. It also shows the collected passwords in graphical form.
Central Policy Manager: This feature adjusts the overall passwords automatically and returns them with new passwords. It also supplies validation and reconciliation of passwords on small machines.
Privileged Session Manager: The Privileged Session Manager feature delivers the key to select accounts from a central point. It also allows an effect point to create privileged sessions.
Select Session Manager for Web: This feature allows companies to have a cohesive approach to ensure access to numerous applications, services, and cloud platforms.
Privileged Threat Analytics: The Privileged Hazard Analytics component continually watches how the secret accounts are used in the CyberArk Privileged Access Security (PAS) platform. Along with side this, it also monitors the accounts not controlled by CyberArk and checks if there’s any movement of threats.
Password Upload Utility: It creates the vault performance cycle faster and automatically by uploading numerous passwords to the Secret Access Security solution.
SDK Interfaces: The SDK interfaces form – Application Password SDK, Application Password Provider, and Application Server Certificate Provider. Among these, the machine Password SDK eliminates the need of keeping passwords in applications and enables them to keep centrally within the Secret Access Security solution. Whereas the device Password Provider may be a local server, which gets passwords once they’re saved from the vault and produces immediate access to them. The device Server Credential Provider interface automatically and securely controls the appliance server certificates that are held inside XML files.
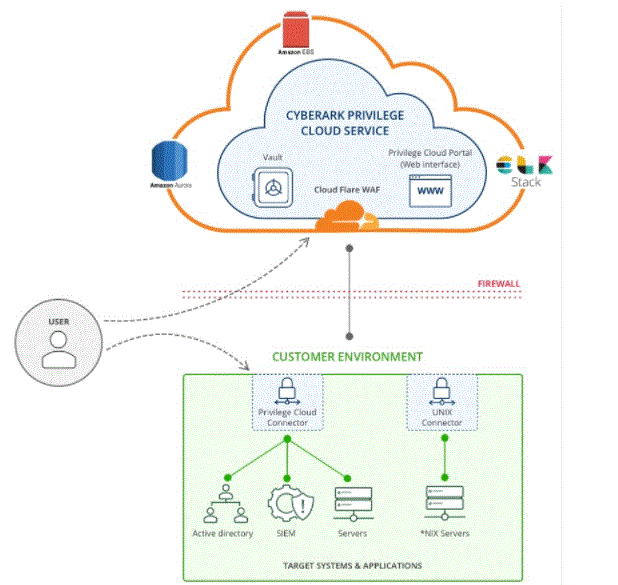
CyberArk Implementation:
The implementation of CyberArk is often wiped out in a phased manner. a number of the suggested phases include Business and security requirements analysis, Scope definition, Solution launch and execution, Risk mitigation plan, and Companywide execution. the subsequent gives a quick insight into these phases:
Business and security requirements analysis: during this first phase, you would like to spot the precise security requirements and also analyze the risks and description of the controls. you furthermore may get to identify the privileged accounts, prioritize the privileged accounts, identify the high value and important assets, and specify the controls and timelines.
Scope definition: As a part of this second phase, you would like to specify the scope and also define who the stakeholders are and what their responsibilities are.
Solution launch and execution: during this third phase, the project kick-off meeting should be followed by architectural design, solution design, and solution implementation.
Risk mitigation plan: during this phase, small group accounts need to be made as a pilot and issues need to be identified.
CyberArk Tools:
The following are the components of CyberArk. They are:
Digital vault: The Digital Vault is probably the foremost secure location on the network for storing sensitive data. it’s easily usable because it’s pre-configured.
Password vault web access: This is a web-based interface for controlling confidential passwords. You’ll use this part as a part of password management to get new confidential passwords. The interface contains a dashboard that enables you to watch the movement within the security solution. It also graphically shows the collected passwords.
Central Policy Manager: This component randomly assigns existing passwords and wishes to exchange them with new passwords. It also serves password verification and reconciliation on small machines.
Privileged Session Manager: The Privileged Session Manager component provides centralized access to privileged accounts. It also allows an impact point to launch privileged sessions.
Web Privileged Session Manager: This component allows businesses to require a unified approach to secure access to multiple applications, services, and cloud platforms.
Privileged Threat Analytics: The Privileged Threat Analytics component of the CyberArk Privileged Access Security (PAS) platform continuously monitors how privileged accounts are used. additionally, it monitors accounts that aren’t managed by CyberArk to ascertain if there’s any indication of a threat.
Password Upload Utility: It accelerates and automates vault implementation by uploading multiple passwords to the Privileged Access Security solution.
SDK interfaces: Application Password SDK, Application Password Provider, and Application Server Credential Provider are the SDK interfaces. the appliance Password SDK, for instance, eliminates the necessity to store passwords in applications and allows them to be stored centrally within the Privileged Access Security solution.
The Application Password Provider, on the opposite hand, maybe a local server that obtains passwords from the vault and provides immediate access to them. the appliance Server Credential Provider interface manages application server credentials stored in XML files automatically and securely.
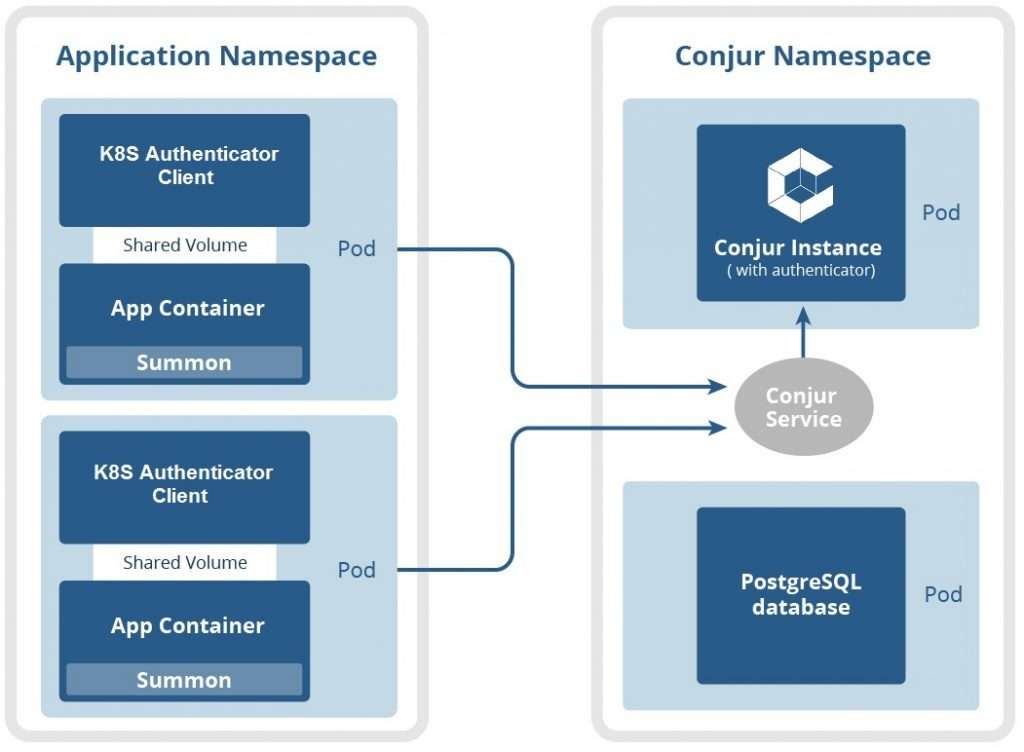
Capabilities:
CyberArk is a publicly-traded data security company delivering unique management. The company’s technology is employed especially in the financial services, energy, retail, healthcare, and country markets.
The main capabilities of Privilege Cloud are:

Prerequisite:
Core knowledge on Linux, network and security concepts is advisable for attending CyberArk training:
Conclusion:
In this blog post, we had covered all the key components of the CyberArk intimately. However, to be an expert professional in handling data threats or any data-related security, CyberArk acts because of the most prominent tool for the organization. Held any suspicions please drop your words below.






