
- What is Ransomware
- Types of Ransomware
- History of Ransomware Attacks
- How Ransomware Works
- Famous Ransomware Attacks
- Ransomware Delivery Methods
- Ransomware in Enterprises
- Preventive Measures
- Role of Backups in Recovery
- Conclusion
What is Ransomware
In the constantly evolving landscape of cyber threats, ransomware has emerged as one of the most notorious and destructive forms of attack. Unlike traditional malware that simply disrupts systems or steals information, ransomware goes a step further by holding an individual’s or organization’s data hostage until a ransom is paid. This malicious software encrypts files or locks users out of their systems, effectively paralyzing businesses, hospitals, government agencies, and individuals alike. To learn how to defend against such high-impact threats, explore Cyber Security Training a specialized course that covers ransomware mitigation, incident response, and proactive defense strategies to protect critical infrastructure and sensitive data. The rise of ransomware is a testament to how cybercriminals have shifted toward financially motivated attacks, often demanding payment in cryptocurrency to avoid detection. Understanding ransomware is not just important for IT professionals, but also for anyone who interacts with digital systems, as its impact can be devastating both personally and professionally.
Types of Ransomware
Types of Ransomware, each varying in how it attacks systems and extorts victims. The two most common types are crypto-ransomware and locker ransomware. Crypto-ransomware encrypts valuable files such as documents, photos, and databases, making them inaccessible until the ransom is paid. To understand how these threats often begin with unauthorized access attempts, explore Explain Brute Force Attacks a foundational guide that details how attackers use automated tools to guess passwords, breach systems, and pave the way for ransomware deployment and data compromise.
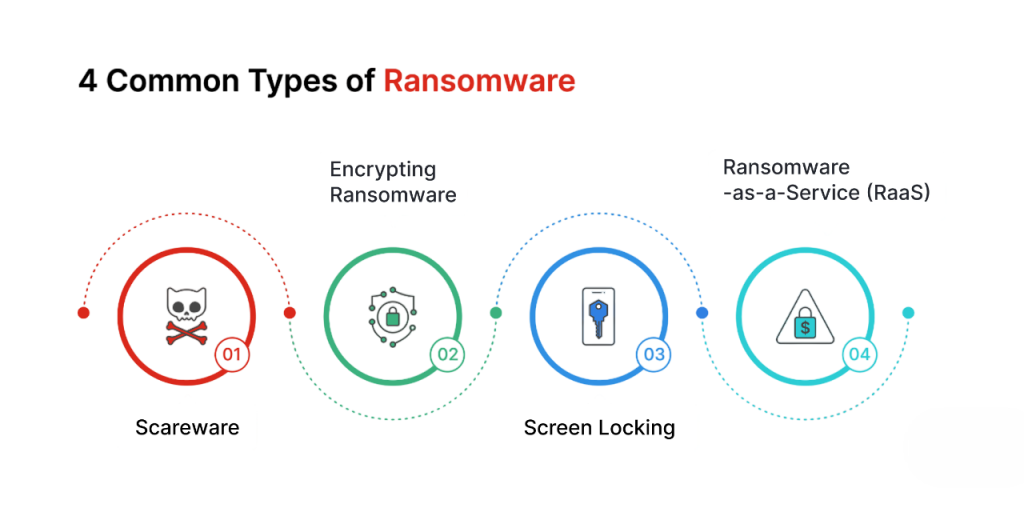
Locker ransomware, on the other hand, locks users out of their devices entirely, preventing access to the operating system. There are also more advanced versions like doxware (or leakware), which threaten to publish sensitive data online if the ransom isn’t paid. Ransomware-as-a-Service (RaaS) has also become popular in underground markets, where developers lease ransomware to less-skilled criminals in exchange for a cut of the profits. Each type underscores the adaptability of attackers in finding new ways to exploit victims.
Interested in Obtaining Your Cyber Security Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
History of Ransomware Attacks
- Ransomware is not a new phenomenon; it has evolved over the last three decades. The first known ransomware attack, known as the AIDS Trojan or PC Cyborg, appeared in 1989. Distributed via floppy disks, it encrypted file names on infected systems and demanded a ransom to unlock them. Over time, ransomware became more sophisticated.
- In the mid-2000s, ransomware began using stronger encryption algorithms, making it nearly impossible to recover data without paying the ransom. High-profile attacks like CryptoLocker (2013) and WannaCry (2017) brought ransomware to global attention, as they infected hundreds of thousands of computers worldwide.
- WannaCry alone affected hospitals, transportation systems, and enterprises, exploiting a vulnerability in Microsoft Windows. Over the years, ransomware has evolved into targeted attacks on enterprises, often demanding multi-million-dollar payments.
- At its core, ransomware relies on encryption to deny users access to their data. Once installed on a system, it scans for valuable files, such as documents, images, or databases, and encrypts them using advanced algorithms. Victims are then presented with a ransom note, often demanding payment in Bitcoin or other cryptocurrencies.
- To proactively identify and patch vulnerabilities before ransomware can exploit them, explore Bug Bounty Programs a collaborative security model where ethical hackers help organizations uncover flaws, strengthen defenses, and prevent costly breaches.
- The attack typically follows a cycle infection, encryption, ransom demand, and sometimes decryption if the ransom is paid. Ransomware often spreads through malicious email attachments, infected software downloads, compromised websites, or vulnerabilities in outdated systems.
- More advanced variants use worm-like behavior, allowing them to spread automatically across networks, magnifying their impact. For businesses, this means not just data loss but also downtime, financial damages, and reputational harm.
- Enterprises are prime targets for ransomware because of the high value of their data and the significant operational disruptions that result from attacks. Industries such as healthcare, finance, education, and energy are especially vulnerable.
- To understand how attackers tailor these threats using personalized deception tactics, explore Definition of Spear Phishing a targeted overview that explains how cybercriminals craft convincing messages to infiltrate high-value organizations, steal credentials, and deploy ransomware with precision.
- For example, ransomware attacks on hospitals can paralyze patient care, putting lives at risk. In enterprises, ransomware can halt business operations, disrupt supply chains, and cause irreparable reputational damage.
- Attackers often conduct double extortion schemes, not only encrypting data but also threatening to leak it online if the ransom isn’t paid. This puts additional pressure on organizations to comply with demands. Enterprises must therefore invest heavily in prevention, detection, and response strategies to minimize the risks associated with ransomware.
- Preventing ransomware requires a combination of technical safeguards and user awareness. Keeping operating systems, applications, and security patches up to date is crucial, as many attacks exploit known vulnerabilities. Organizations should deploy endpoint protection solutions, intrusion detection systems, and robust firewalls to detect and block ransomware before it spreads.
- Email filtering and sandboxing technologies help identify phishing attempts. Regular employee training is equally important, as human error is often the entry point for attacks. Implementing strong access controls, disabling unnecessary services, and restricting administrative privileges further reduces risks. A well-tested incident response plan is also essential to ensure quick containment and recovery in the event of an attack.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
How Ransomware Works
Famous Ransomware Attacks
Several ransomware incidents have made global headlines due to their scale and consequences. The WannaCry attack in 2017 remains one of the most infamous, spreading across 150 countries and crippling organizations such as the UK’s National Health Service. Another notable attack was Petya/NotPetya, which initially looked like ransomware but was later identified as a destructive cyber weapon. It targeted Ukrainian organizations and spread globally, causing billions of dollars in damage. To understand how to defend against such advanced threats and nation-state attacks, explore Cyber Security Training a specialized course that covers malware analysis, threat intelligence, and incident response strategies essential for protecting critical infrastructure and enterprise systems. The Ryuk ransomware has also been highly destructive, targeting hospitals, municipal governments, and enterprises with ransom demands often exceeding $1 million. More recently, the Colonial Pipeline attack in 2021 disrupted fuel supply in the United States, demonstrating how ransomware can affect critical infrastructure. These incidents highlight how ransomware is no longer just a nuisance but a serious threat to national security and economic stability.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Ransomware Delivery Methods
Cybercriminals employ a variety of tactics to deliver ransomware. One of the most common is phishing emails, which trick users into clicking malicious links or downloading infected attachments. Attackers also exploit unpatched software vulnerabilities, particularly in widely used platforms like Microsoft Windows or enterprise applications. Drive-by downloads, where malicious software is automatically installed when visiting compromised websites, are another vector. To understand how these threats impact personal and organizational data, explore Guide to Understanding Data Privacy a comprehensive resource that explains data protection principles, threat mitigation strategies, and best practices for maintaining privacy across digital platforms. Some ransomware is spread through malvertising, which uses legitimate ad networks to deliver infected ads to unsuspecting users. In corporate environments, weak Remote Desktop Protocol (RDP) connections are frequently exploited, giving attackers direct access to systems. The increasing use of supply chain attacks, where ransomware is delivered through compromised third-party vendors or software updates, further demonstrates the creativity of attackers.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Ransomware in Enterprises
Preventive Measures
Role of Backups in Recovery
Backups are the single most effective defense against ransomware. Having secure, regularly updated backups in recovery ensures that organizations can restore their data without paying the ransom. However, not all backups are created equal. Ransomware attackers increasingly target backups stored on network-connected systems, rendering them useless. To strengthen backup integrity and safeguard containerized environments, explore Container Security Tools a curated suite of solutions designed to protect container workloads, enforce runtime policies, and isolate critical assets from ransomware infiltration.
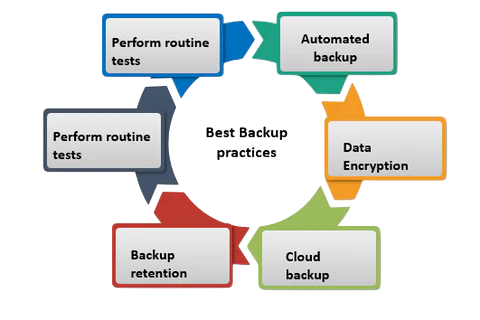
To counter this, organizations must follow the 3-2-1 backup rule: keep three copies of data, on two different media, with one copy stored offline or offsite. Immutable storage solutions, which prevent backups from being altered or deleted, are also gaining traction. While restoring from backups may still involve downtime, it eliminates the need to pay attackers, undermining their business model and reducing financial losses.
Conclusion
Ransomware has become one of the most pressing cybersecurity challenges of our time. From its humble beginnings in the late 1980s to the sophisticated, multimillion-dollar attacks of today, ransomware continues to evolve and threaten individuals, organizations, and even entire nations. Its ability to paralyze critical infrastructure and exploit human vulnerabilities makes it a unique and dangerous threat. However, with strong preventive measures, effective detection tools, regular backups, and international collaboration, the impact of ransomware can be mitigated. To build the expertise needed to implement these defenses, explore Cyber Security Training a comprehensive course that covers ransomware mitigation, threat intelligence, and proactive security strategies for safeguarding digital ecosystems. Ultimately, defeating ransomware requires a combination of technology, awareness, and resilience. By understanding how ransomware works and adopting best practices, individuals and organizations can better protect themselves against this ever-growing menace.




