Computer Security, also called cybersecurity, the protection of computer systems and information from harm, theft, and unauthorized use. Computer hardware is typically protected by the same means used to protect other valuable or sensitive equipment—namely, serial numbers, doors and locks, and alarms.
- Introduction of Computer Security
- Tools for Computer Security
- Features of Computer Security
- Types of Computer Security
- How does this work?
- Why do you want to be a Computer Security?
- Computer Security threats
- Benefits of Computer Security
- Conclusion
Introduction to Computer Security
Computer Security is largely the protection of pc systems and data from injury, stealing and unauthorised use. it’s a method to forestall and notice unauthorised use of your ADP system. There are varied varieties of pc security that are wide wont to defend necessary structure data. pc security, conjointly called cybersecurity, security of pc systems and data on injury, stealing and unauthorised use. PC systems are usually defended by equivalent strategies wont to protect different necessary or sensitive objects — that’s, serial numbers, doors and locks, and alarms.
- Computer hardware, virtual component of computer, such as system memory and disk drive
- Firmware, a software that is permanently installed in the device’s fixed memory and is generally invisible to the user.
- Software, a program that provides services, such as operating system, word processor, Internet browser for the user
- Confidentiality to ensure that information is only available to the intended audience
- Integrity protects information from being compromised by unauthorised parties
- Availability protects the information from being processed by unauthorised groups
The components of a computer system that needs to be protected are:
Computer Security is focused on three key areas:
In simple language, Computer Security ensures that computer information and components are usable but still secure from people or software that should not be accessed or modified.
Features of Computer Security:
Many firms run their businesses on-line. Even the epidemic has brought a brand new approach of engaging from home mistreatment the web and varied on-line applications. All of those activities produce opportunities for cyber criminals to interrupt the system. Therefore, each skilled and organisation ought to prepare the knowledge to know the key aspects of cybersecurity. I don’t understand how? IU International University of Applied Sciences offers a degree to boost your skilled skills – the Masters of Science program in Cyber Security is one in all the courses you ought to favour to solve cybersecurity issues as an expert. A decent set of cybersecurity options establishes the primary line of defence against attacks and lawlessness. Here may be a list to keep in mind.
1) Installation of external threats:
According to the PurpleSec 2021 report, twenty seventh of cyber attacks and incidents return from outside sources. External threats seem like phishing scams, Denial of Services, malicious net applications, malicious email attachments, etc. Therefore, security applications connected to the business system should monitor these external threats. M.Sc. Cyber Security at IU International University of Applied Sciences can offer essential steerage in addressing external threats.
2) shield yourself from internal threats:
Although several on-line threats return from external sources, from time to time, associate degree workers at intervals the organisation will still be a threat. in line with the twenty Cybersecurity business executive Threat Report 20, sixty eight p.c of organisations feel vulnerable by internal attacks. In several cases, internal threats occur as a result of workers errors, misconduct, or poor workers selections, or unhealthy players. However, a reliable security system and a team of extremely qualified on-line security consultants will minimise these threats from the organisation. If you wish to become a cybersecurity knowledgeable, selecting a Masters of Science in cybersecurity can assist you perceive security principles against internal threats.
3) Compliance with safety rules:
Information security is a crucial business for each company, be it health or money. Every organisation includes a totally different set of standards, processes, rules, and information sharing and knowledge assortment. Compliance with the principles conjointly includes rules, details, and tips for business processes. Cybersecurity officers should style security compliance in line with trade and placement necessities to forestall company information from entering into the incorrect hands. MS Cyber Security at IU International University of Applied Sciences guides you in making ready to fit business safety rules.
4) Cloud-based security services:
Cloud-based security services are the backbone of varied security systems. it’s several analytical tools and threatening skills. These services embrace storage areas for security and focus machine learning models to boost scanning for all-encompassing functions. Masters in Cyber Security focuses on cloud-based experience to master such skills.
5) Threat detection, prevention, and response:
According to a study printed in CISO magazine, thirty five p.c of CISO consultants ask for a comprehensive security set up which will stop most (95 out of 100) attacks. In addition, they require the bowl to trace associate degreed issue associate degree automatic warning of an attack that would not be stopped. MS Cyber Security or M.Sc. Cyber Security seekers receive coaching to trace down suspicious activities and complete them. They use tools like hardware and computer code firewall, network analysts, SSL / TLS hosting servers, and different applications to find and stop breaches.
6) Integrated Solutions:
Cybersecurity resolutions ought to conjointly offer an entire solution to forestall the system (business / individual) from varied threats. For this reason, security consultants ought to have skills and wherever to use anti-spam, anti-virus, anti-malware, content filters, wireless security, etc. Such complete protection can stop the system from attackers whereas guaranteeing the confidentiality and security of information and business. actions. IU International University of Applied Sciences teaches these tools and adds the Masters of Science program in Cyber Security.
7) Acceptable Protection Statistics:
Every trade uses one thing productive with sensible statistics – thus the protection trade. It’s straightforward to point the finger at insensitive and inevitable threats. a decent security analysis conjointly helps to watch the danger and respond quickly to matters before it happens.
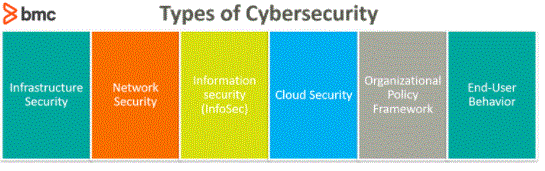
The different types of cybersecurity:
Application security
Application security is the implementation of assorted protections among business code and services to guard against a range of various threats. This kind of cybersecurity needs the look of secure applications to attenuate unauthorised access and modification.
Network Security
Network security focuses on protecting business from external and internal threats through hardware and code programs specifically designed to guard the business network and infrastructure from misuse, disruption, and unauthorised access.
Mobile Security
Businesses that use mobile devices, like mobile phones, laptops, and tablets, ought to use cellular security measures to guard the data held on those devices from a variety of threats.
Cloud Security
Most cloud applications — AWS, Google, Microsoft, etc. — use cloud security to guard users from varied threats.
Examples for Computer Security:
Computer Security risks can be caused by malware, that is, malicious software, which can infiltrate your computer, corrupt your files, steal your data, or allow the attacker to access your system without your knowledge or authorization. Examples of malware programs include viruses, worms, ransomware, spyware, and Trojan horses.
Examples of Computer Security include Antivirus programs and Antispyware, Firewall that blocks unauthorised access to the network and VPNs (Visible Private Networks) used for secure remote access.
Working principle of Computer Security:
Cybersecurity may be a hi-tech technology tool that uses several tools. It starts with protecting rings designed into computer-enabled chips. Basic hardware rules enforce complicated security policies. Security additionally depends on however the package is employed and used. Hackers try to exploit errors within the security system to avoid or get into the goals of their access to essential services. This chapter describes a number of the fundamental tools and principles utilised in secure pc systems.
Cybersecurity is intended to supply multiple layers of protection across all computers, networks, and applications utilised by businesses. so as to form a combined defence against potential cyber attacks, it’s necessary that business, employees, processes, and technologies square measure designed to figure along seamlessly. Effective Cybersecurity systems are going to be ready to observe, investigate, and resolve potential vulnerabilities and vulnerabilities within the system before they’ll be exploited by a cyber criminal or malicious package.
Why is Computer Security Important?
Computer Security is a process to prevent and detect unauthorised use of your computer. Preventive measures help you prevent unauthorised users (hackers) from accessing any part of your computer system. They usually want to take control of your computer so that they can use it to attack other computer systems. In this digital age, we all want to keep our computers and personal information secure and that is why Computer Security is essential to keep our personal information secure. It is also important to maintain the safety of our computer and its overall health by preventing viruses and malware that may affect system performance.
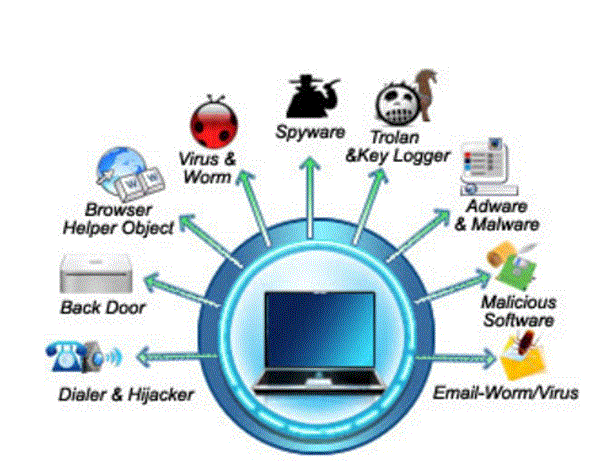
Computer Security threats:
Computer Security threats area unit threats that will disrupt the traditional operation of your laptop. During this fashionable age, cyberbullying threats still grow because the world becomes a lot more digital. the foremost dangerous varieties of laptop security are:
Virus
A bug could be a bug that’s downloaded to a user’s laptop while not the user’s data. It replicates and infects files and programs on the user’s laptop. The main goal of the virus is to confirm that the victim’s laptop can ne’er work properly. Computer Worm. Computer worm could be a computer code program that may copy itself from one laptop to a different, while not human interaction. The potential danger here is that it’ll spend your computer’s disc area as a result of the worm replicating with high volume and high speed.
The crime of stealing sensitive info
Pretending to be Associate in Nursing an honest person or a business person, fraudsters try to steal sensitive monetary or personal info via fallacious email or instant messages. The crime of stealing sensitive info sadly is extremely straightforward to use. you’ve been tricked into thinking that email is legal and you’ll be able to enter your personal details.
Botnet
A botnet could be an assortment of computers connected to the net that are compromised by a criminal employing a bug. Every laptop is named a ‘zombie computer’. The results of this threat to the victim’s laptop, which can be used for malicious activity and large-scale attacks like DDoS.
Rootkit
A rootkit could be a bug designed to grant a reasonably continuous access to a laptop whereas concealment its existence. Once the rootkit is put in, the rootkit controllers are ready to produce files remotely and modify system settings on the host machine.
Keylogger
Also referred to as keystroke loggers, keyloggers will track the user’s time period activity on his or her laptop. Keeps a record of all key clicks created by the user keyboard. Keylogger is additionally a really powerful threat to steal people’s login info like username and positive identification. These areas unit in all probability the foremost common security threats you may encounter. except for this, there are unit others like spyware, wabbits, scareware, bluesnarfing and far a lot of. fortuitously, there area unit ways that to guard ourselves from these attacks
Benefits of Computer Security:
Protection of your business – online security solutions provide digital protection to your business which will ensure that your employees are not exposed to potential threats such as Adware and Ransomware.
High productivity – viruses can slow down computers to crawl, and make work impossible. Effective internet security eliminates this possibility, maximising the impact of your business.
Promotes consumer confidence – If you can prove that your business is successfully protected from all forms of cybercrime, you can promote confidence in your customers that their personal data will not be compromised.
Protecting your customers – ensuring that your business is protected from online threats will also help to protect your customers, who may be at risk of being hacked online by a representative.
Stopping your website from going down – if you are the business that owns your website, internet infringement can be catastrophic. If your system becomes infected, your website may be forced to shut down which means you will lose money due to loss of sales.
Conclusion
According to IT experts, cybersecurity features ensure complete security of important business assets, actions, and data. Medium and large organizations need all seven functional security features to fully protect themselves by adding a few attributes. Those who will elect the M.Sc. Cyber Security or online masters at Cyber Security will encounter these many cybersecurity features. IU International University of Applied Sciences has a Masters program in Cyber Security that will provide courseware that incorporates all aspects of cybersecurity security and the concepts of aspirants and professionals. So, If you are a cyber-warrior hero who wants to improve your cybersecurity skills, get your Master’s Degree in Cyber Security at IU International University of Applied Sciences today.