
- Introduction
- What is Traceroute?
- How Traceroute Works
- Common Use Cases of Traceroute
- Understanding Traceroute Output
- Tools and Variations
- Variations of Traceroute
- Limitations of Traceroute
- Best Practices for Using Traceroute
- Conclusion
Introduction
Traceroute is the name of a network diagnostic tool used to trace data packets’ path from one computer to another over an IP network. It will give the network administrator or IT professional valuable insights to help troubleshoot performance problems on the network. By utilizing tools like , they can detect issues such as packet loss, delays, or misconfigured network devices, Web Security which are essential for maintaining a healthy and efficient network. Traceroute identifies the intermediate hops between the source and destination. This makes it an important tool for diagnosing routing issues, latency problems, and network congestion. Understanding how traceroute works and interpreting its output can significantly improve the management of network performance and reliability.
What is Traceroute?
Traceroute is the command-line network diagnostic tool with the function of tracing the path a packet takes to reach its final destination. It helps identify which each hop is, or how routers between the source and the destination, and displays IP address, response time information and sometimes additional details about a route. It works by sending packets with incrementally increasing time-to-live (TTL) values, which will force the routers to return error messages that the tool captures to track the whole route. This process can help network administrators troubleshoot and monitor routes effectively. Additionally, can be configured to limit which devices or users can access certain parts of the network, helping to enhance security while tracking network performance.
To learn about different Cybersecurity techniques, sign up for our Cyber Security Online Training now!
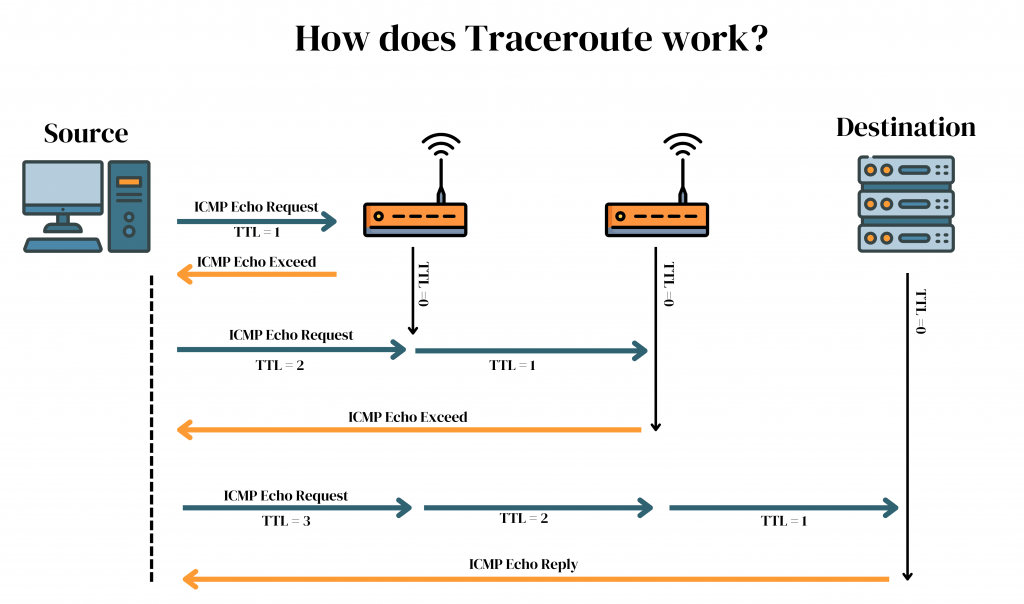
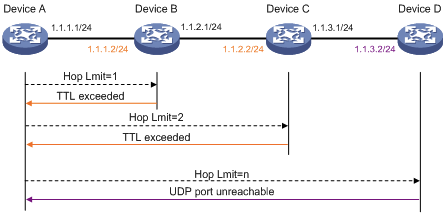
How Traceroute Works
Traceroute sends a series of specially crafted packets, each with a different TTL (Time-To-Live) value, to the destination. TTL determines how many hops the packet is allowed to take before being discarded. If the TTL value is set to 1, the first router sends back an error message (ICMP “Time Exceeded”) indicating that the packet has been discarded. Traceroute increases the TTL to 2 and repeats the process. Every router on the path sends back an error message, giving away its IP address and the time taken for the packet to reach that point. By incrementally increasing the TTL, Demilitarized Zone the traceroute builds a complete map of the route, showing each hop along the way.
Common Use Cases of Traceroute
- Network Troubleshooting traceroute is generally used to identify where in the network latency or packet loss occurs so that specific routers or segments can be identified and targeted.
- Route Analysis traceroute can help the network administrator understand the best paths that data takes over a network and whether detours or unnecessary hops might impact performance.
- It can be very useful in analyzing the performance of Internet Service Providers, especially when there is an attempt to determine the bottlenecks or routing inefficiencies affecting end-to-end performance.
- Traceroute may help identify delays or timeouts that indicate network congestion, Crytographic Techniques hardware malfunction, or service outage by measuring the round-trip time for each hop.
- Hop Number:This is the number that indicates the order of each router along the path.
- Router IP Address: The IP address of each router along the path is crucial for understanding the route data takes through the network. This information can be especially useful in where participants learn to monitor and secure network traffic, identify vulnerabilities, and protect critical infrastructure from cyber threats.
- Round-trip time (RTT): This is the time it takes for a packet to travel from the source to the router and back. It is usually shown in milliseconds (ms).
- Request Timings: By default, Traceroute sends several probes to each hop, and the output displays the time taken for each probe. If no response is received from a router, a timeout or asterisks (*) may also be shown.
- Traceroute (Linux/Unix): The most widely used tool in Linux and Unix-based systems, it provides a simple command-line interface to trace packet routes. Along with this can be employed to improve security by dividing the network into smaller, Session Hijacking isolated segments, making it more difficult for attackers to move laterally within the network and ensuring better control over traffic flow.
- Tracert (Windows): This is the equivalent of traceroute in Windows. It works similarly but uses slightly different syntax. For example, `tracert` is the command, and the output format is adapted to Windows.
- MTR (My Traceroute): MTR is an advanced network diagnostic tool that combines the functionality of both traceroute and ping. It provides a real-time, dynamic view of network performance and is available on Linux, Unix, and Windows.
- PathPing (Windows): PathPing is a Windows-based utility that combines features from ping and traceroute and delivers more detailed information about network latency and packet loss at every hop.
- Online Traceroute Tools: Websites such as GTrac” route and Ping. Eu delivers web-based traceroute tools for performing a traceroute test from different geographic locations without the need for a local command-line interface.
- Perform multiple traceroutes: As the network is dynamic, performing multiple traceroutes helps identify consistent patterns and avoid temporary issues. This is crucial in to pinpoint vulnerabilities and ensure security measures are effective.
- Use MTR for Real-Time Monitoring: MTR provides a dynamic view of route performance. It is ideal for tracking fluctuating network conditions and getting a live update of packet loss or latency across hops.
- Combine with Other Tools: Use traceroute in conjunction with other network diagnostic tools, such as ping, nslookup, or netstat, to get a more comprehensive understanding of network health.
- Verify Firewall and Router Settings: Check that firewalls and routers are properly configured so that filtering on ICMP, Vulnerability Management or TTL does not interfere with the outcome.
- Perform Traceroute from Other Locations: Perform traceroute from other geographic locations to identify where routing problems or bottlenecks are occurring within the network or at the ISP level.
Understanding Traceroute Output
Are you curious to know more about Cybersecurity ? Take advantage of our comprehensive online Cyber Security Online Training
Tools and Variations
Although the basic functionality of traceroute is the same across platforms, various tools and implementations have emerged to cater to specific needs, provide additional features, or enhance usability.
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Today!
Variations of Traceroute
TCP Traceroute helps identify network performance issues that are related to specific TCP traffic. It can bypass firewalls and routers that block ICMP traffic by using TCP packets, making it valuable in restricted environments. This method is especially helpful when diagnosing connectivity issues with web services, as HTTP traffic often relies on TCP. Additionally, TCP Traceroute can be configured to target specific ports, making it possible to trace routes for services like web servers, email servers, or DNS. IPv6 Traceroute functions similarly to its IPv4 counterpart but is designed for networks using the IPv6 protocol. It is crucial for understanding the performance and path of traffic across modern networks, especially as the world shifts towards IPv6. Given that IPv6 addresses are much larger than IPv4, the traceroute process must handle the differences in the address scheme while still providing accurate route information. It also provides insights into the routing of IPv6-enabled services like newer cloud applications or next-gen networking technologies.
Limitations of Traceroute
Traceroute results can be affected by several factors, leading to incomplete or misleading data. ICMP/TTL restrictions imposed by routers, especially firewalls and security devices, often block or rate-limit ICMP packets or restrict TTL to prevent attacks, resulting in incomplete traces. Network congestion and latency can also impact traceroute accuracy, as packet travel times vary due to changing network conditions or routing errors, which may not reflect the true status of the network. Firewall filtering is another challenge, as some networks block traceroute packets entirely to prevent network surveillance, causing timeouts or incorrect responses at certain hops in the Cybersecurity Training Courses . To mitigate such issues, play a crucial role in protecting the network from unauthorized access, while ensuring that legitimate traffic, including diagnostic tools like traceroute, can function properly when necessary for troubleshooting. Additionally, proxies or load balancers can produce misleading results by obscuring the actual network path or displaying incorrect IP addresses. Traceroute also assumes a direct path between two points, which can be inaccurate in complex networks that use dynamic routing or load-balancing strategies, leading to incorrect conclusions about the network topology.
Ready to pass the interview for cybersecurity ? Learn how to answer Cybersecurity Interview Questions and Answers
Best Practices for Using Traceroute
Conclusion
Traceroute is an essential network diagnostic tool that helps identify the path in which data packets are carried from source to destination. It can be an invaluable tool in diagnosing a network problem, including latency, packet loss, and inefficiency in routing. Still, with its limitations, it can only be used with security devices interfering, and sometimes it’s ingested in the network, leading to inaccuracies with complex network configurations. However Cybersecurity Training , professionals learn how to effectively handle these limitations, understand potential network security risks, and implement solutions to minimize inaccuracies and ensure a more secure and optimized network environment. Understanding traceroute, its variations, and best practices for implementation assists the network administrator in better applying the tool to achieve maximum network performance and solve connectivity problems.





