
- Introduction
- Static Application Security Testing (SAST) Tools
- Dynamic Application Security Testing (DAST) Tools
- Interactive Application Security Testing (IAST) Tools
- Software Composition Analysis (SCA) Tools
- Web Application Firewalls (WAFs)
- Runtime Application Self-Protection (RASP) Tools
- Vulnerability Scanners
- DevSecOps Integration Tools
- Monitoring and Logging Tools
- Conclusion
Application security tools are essential for identifying, preventing, and mitigating security vulnerabilities in software. The top 15 tools for application security include static analysis tools like Checkmarx and SonarQube, which review source code for potential flaws, and dynamic analysis tools like Burp Suite and OWASP ZAP, which simulate attacks on running applications. Other key tools include dependency management solutions such as Snyk and WhiteSource, which monitor vulnerabilities in third-party libraries, as well as security testing frameworks like Selenium and Fortify for automated vulnerability detection. Cyber Security Training Courses can help developers effectively use these tools to identify and mitigate vulnerabilities, enhancing overall security. These tools help developers and security professionals ensure that applications remain secure throughout their lifecycle, protecting against common threats like SQL injection, cross-site scripting, and unauthorized access.
Are You Interested in Learning More About Cybersecurity? Sign Up For Our Cyber Security Online Training Today!
Introduction
As the landscape of cybersecurity grows more complex, security in applications has become a very high priority for organizations. Applications lead the way for digital transformation, and cyberattacks primarily target them. Application security from vulnerabilities, data breaches, and other malicious activities requires proactive measures that engage specialized tools to identify and mitigate possible security risks in the lifecycle of software development. A key focus area is Web Application Security, which ensures that web-based applications are protected against various threats and vulnerabilities. This article reviews the top 15 tools for application security that cater to various solutions needed to be able to secure an application against threats like SQL injection, cross-site scripting, and insecure code. They come with static and dynamic code analysis, vulnerability scanning, penetration testing, and real-time monitoring.
Static Application Security Testing (SAST) Tools
Static Application Security Testing (SAST) tools are necessary to locate security vulnerabilities in an application’s source code before they are compiled or executed. Through source, bytecode, and binaries of the application, SAST tools identify those weaknesses that attackers could potentially exploit. Hence, SAST tools help developers get hold of issues early enough in the development lifecycle so the vulnerabilities can be fixed by the time the application has been deployed, thus ensuring a reduction in the expense and complexity of remediation.
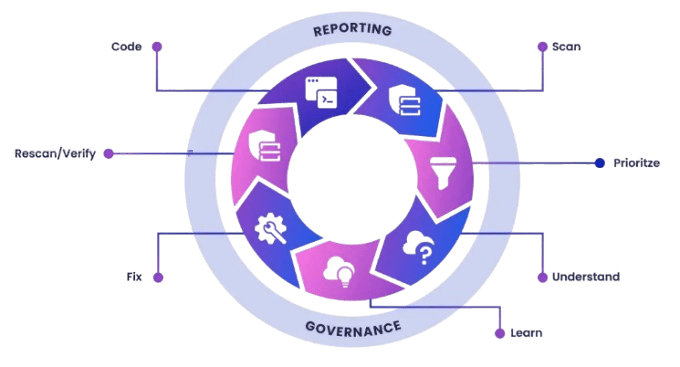
- Early Detection: SAST tools analyze code at an early stage of development, thereby identifying security vulnerabilities and correcting them before the code is compiled or executed. This approach prevents vulnerabilities from entering the production environment.
- Comprehensive Code Analysis: These tools scan the whole codebase, including custom code, libraries, and third-party dependencies, for potential security flaws such as SQL injection, cross-site scripting (XSS), and buffer overflows.
- Integration with CI/CD Pipelines: SAST tools can be integrated into Continuous Integration and Continuous Deployment (CI/CD) pipelines, allowing automated security checks during the build process. This ensures that vulnerabilities are detected early, enabling continuous security without disrupting the development flow.
- Compliance and Reporting: Most SAST tools offer detailed reports on the discovered vulnerabilities and remediation guidelines. They also ensure compliance with industry standards and regulations such as OWASP Top 10, GDPR, and PCI-DSS.
- Support for Multiple Languages: Modern SAST tools support a wide variety of programming languages (Java, C#, Python, JavaScript, etc.), which enables them to be used across different development environments and application types.
Dynamic Application Security Testing (DAST) Tools
DAST focuses on identifying vulnerabilities in running applications during testing, unlike SAST, which analyzes source code. It tests applications in runtime, simulating real-world attacks to uncover security flaws that could be exploited in production. Key features of DAST tools include real-time application testing, where they simulate attacks to detect vulnerabilities like SQL injection, cross-site scripting (XSS), and configuration weaknesses. Vulnerability Scanning is an essential component, helping identify and address potential security risks in applications before they can be exploited. Since DAST does not require access to source code, it is useful for web applications, APIs, and service testing. Automated security scanning allows these tools to continuously scan applications to identify potential risks that could lead to data breaches. By simulating external attacks, DAST helps assess how an attacker might exploit vulnerabilities in a production environment. Some common DAST tools include OWASP ZAP, an open-source tool used for web application security testing at runtime, offering automated scanners and penetration testing capabilities. Burp Suite is a comprehensive security testing platform that provides both active and passive scanning, along with a web vulnerability scanner to detect common flaws. Acunetix is an automated DAST solution known for its extensive scanning capabilities, detecting SQL injection, XSS, and other vulnerabilities while providing in-depth reporting and risk assessment.
To Earn Your Cyber Security Certification, Gain Insights From Leading Cyber Security Experts And Advance Your Career With ACTE’s Cyber Security Online Training Today!
Interactive Application Security Testing (IAST) Tools
IAST tools combine the best features of SAST and DAST and offer real-time feedback on an application’s security as it runs. IAST tools are integrated into the application server and continuously monitor code and runtime behaviour to provide insights into vulnerabilities and potential threats.
Key Features of IAST Tools:- Real-Time Monitoring: IAST tools run during runtime and analyze both the source code and the application’s execution in real time.
- Contextual Vulnerability Detection: The IAST tool monitors runtime behaviour and thus gives more accurate vulnerability detection. It detects risks based on actual application behaviour rather than just the code structure.
- Faster Remediation: IAST tools give developers immediate feedback so they can address vulnerabilities as they arise without the need for separate testing cycles.
- Comprehensive Coverage: By utilizing static and dynamic testing, IAST tools can carry out an in-depth, detailed analysis far beyond the scope of any traditional DAST. Popular IAST Tools:
- Contrast Security: Contrast Security provides real-time interactive security that integrates with the application’s code to present automated vulnerability detection at runtime, boosting both security and development effectiveness.
- Seeker by Synopsys: Seeker is an IAST solution that directly integrates into the runtime environment and provides continuous feedback on vulnerabilities. It supports most application frameworks and gives detailed insights into vulnerabilities.
- Veracode: Veracode offers both static and interactive application security testing solutions. Their IAST tool is real-time and deeply integrated into CI/CD workflows.
- Vulnerability Detection: These SCA tools scan an application’s open-source components to identify known security vulnerabilities and prevent weak or outdated components from entering the system.
- License Management: The tools scan for licenses on the open-source components to check whether the licenses comply with organizational and legal requirements.
- Dependency Mapping: The tools present a detailed report about dependencies among the components, risk potentialities and outdated packages.
- Automated Remediation: Most SCA tools recommend or automatically apply fixes, including updating to a newer version of a vulnerable package. Popular SCA Tools:
- Snyk: Snyk is one of the widely used SCA tools. It continuously scans open-source libraries for vulnerabilities and monitors their open-source libraries for vulnerabilities. Snyk also integrates into CI/CD pipelines and provides automatic patching for known security issues.
- WhiteSource: WhiteSource automates open-source component management by scanning libraries for vulnerabilities, licensing issues, and outdated versions. It also integrates with popular development tools and workflows.
- Sonatype Nexus Lifecycle: Nexus Lifecycle manages open-source security and compliance in teams. It automatically scans for vulnerabilities and provides actionable insights to mitigate risks associated with open-source components.
- Traffic Filtering: WAFs examine incoming traffic and block malicious requests while allowing legitimate traffic to pass through.
- Protective capabilities against OWASP Top 10: WAFs usually protect against web application vulnerabilities such as SQL injection, XSS, and CSRF.
- Custom rules: Many WAFs offer customized security rules that can be tailored to an application’s unique needs, ensuring the correct protection.
- DDoS: Some WAFs are equipped to protect against DDoS attacks, which helps maintain the application’s availability during large-scale attacks. Popular WAF Tools:
- AWS WAF: AWS WAF is a cloud-based firewall service that helps protect web applications hosted on Amazon Web Services (AWS) from common web exploits. It provides customizable rules for filtering HTTP requests.
- Cloudflare WAF: Cloudflare’s WAF provides comprehensive protection against various web threats. Its built-in rules are based on the OWASP Top 10. The WAF also integrates with Cloudflare’s content delivery network (CDN) for improved performance and protection.
- F5 BIG-IP ASM: F5’s Advanced Web Application Firewall (ASM) provides full web application security by protecting its customers from a wide range of application-level threats, including zero-day vulnerabilities.
- Real-Time Threat Detection: RASP tools always monitor the applications during runtime and detect anomalous behaviours such as trying to exploit vulnerabilities or escalating privileges.
- Automated Attack Mitigation: RASP automatically blocks malicious activity and prevents attacks with minimal security teams’ intervention.
- Deep Integration with Application Logic: RASP tools are embedded into the application code for better context-aware, granular security than traditional methods.
- Minimal Performance Impact: Modern RASP tools have been designed to offer the most secure application performance with the least impact on performance.
- Contrast Security: Contrast Security provides RASP capabilities that offer real-time protection from within the application, blocking attacks and vulnerabilities as they are detected at runtime.
- Arxan: Arxan’s RASP solution is on the protection of mobile and web applications from reverse engineering, tampering, and other real-time threats that could compromise security even after deployment.
- Immunio: Immunio is a RASP tool that focuses on application security at runtime. It prevents threats like SQL injection and cross-site scripting in real time and provides detailed reporting.
- Automated Scanning: Vulnerability scanners automatically scan systems, networks, or applications for known vulnerabilities, providing detailed reports on potential risks.
- Comprehensive Coverage: It identifies most vulnerabilities, such as misconfigured applications, unpatched patches, weak passwords, and software vulnerabilities.
- Automated Security Testing: This scans code and infrastructure automatically for security vulnerabilities in the CI/CD pipeline, reducing the risk of discovering issues too late in development.
- Continuous Monitoring and Alerts: DevSecOps tools will continuously monitor code repositories, build environments, and deploy applications for vulnerabilities or threats and alert about them.
- Real-Time Event Monitoring: These tools continuously monitor system, network, and application events to detect anomalies, errors, and suspicious activities as they occur.
- Centralized Log Collection and Analysis: They collect logs from a variety of sources, such as servers, applications, and security devices. They offer a central location where security auditing and troubleshooting may be conducted.
- Alerting and Incident Response: Monitoring tools will alert when abnormal or unauthorized activities are detected, enabling security teams to respond rapidly to potential incidents. Implementing The Most Effective Data Encryption Techniques alongside these monitoring tools ensures that sensitive data remains protected, even if a security breach occurs.
- Compliance and Reporting: Most of the tools ensure compliance with regulatory standards by keeping in-depth logs of all activity and generating reports as may be required by the various frameworks, including GDPR, HIPAA, and PCI-DSS.
Software Composition Analysis (SCA) Tools
Software Composition Analysis (SCA) tools help organizations identify, manage, and mitigate risks associated with the use of third-party and open-source software components. As modern applications rely heavily on open-source libraries and frameworks, SCA tools are crucial for ensuring that these components are secure, compliant with licensing requirements, and up-to-date. Cyber Security Training Courses can equip developers with the knowledge to effectively use SCA tools and follow best practices for secure development.
Key Features of SCA Tools:Web Application Firewalls (WAFs)
Web Application Firewalls (WAFs) are security solutions that protect web applications by filtering and monitoring HTTP/HTTPS traffic between the application and the outside world. WAFs detect and block malicious requests, such as SQL injection, cross-site scripting (XSS), and other types of application-layer attacks. Complementing this, Network Penetration Testing can further identify vulnerabilities in the broader network infrastructure, ensuring a comprehensive security strategy.
Key Features of WAFs:Runtime Application Self-Protection (RASP) Tools
Runtime Application Self-Protection tools provide applications with real-time security while they are running. As opposed to other security solutions, which concentrate on discovering attacks after the fact, RASP is integrated into an application to provide constant, from-within monitoring and protection that recognizes and prevents attacks during their execution.
Main Features of RASP Tools:
Gain Your Master’s Certification in Cybersecurity by Enrolling in Our Cyber Security Expert Masters Program Training Course.
Vulnerability Scanners
Vulnerability scanners are essential tools for identifying and assessing security vulnerabilities in applications, networks, systems, and infrastructure. They automate the process of detecting weaknesses and missing patches, reducing the chances of attackers exploiting them.
Key Features of Vulnerability Scanners:DevSecOps Integration Tools
DevSecOps integration tools help teams integrate security practices and tools into their DevOps pipeline, ensuring that security is an integral part of the development lifecycle. These tools automate security testing, vulnerability management, and risk assessments, making it easier to secure applications and infrastructure as they are developed. Additionally, Malware Analysis tools can be integrated into the pipeline to detect and mitigate potential threats early in the development process.
Key Features of DevSecOps Integration Tools:Monitoring and Logging Tools
Monitoring and logging tools are used to track and record events in real-time, starting from system activities, monitoring user behaviour, and security. These tools are very effective in detecting, diagnosing, and responding to security incidents toward maintaining operational integrity and compliance by organizations.
Key Features of the Monitoring and Logging Tools:Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Conclusion
Applications, networks, and data are being protected today like never before in the fast-moving world of digital. The main IAM tool, DevSecOps integration tools, and monitoring and logging solutions are part of an enterprise security strategy. Organizations can use all these solutions to enforce strict access controls, integrate security seamlessly with the development pipeline, and gain real-time visibility of their systems to detect and respond to potential threats. Cyber Security Training Courses can help employees understand how to effectively implement and manage these solutions to enhance overall security. Adopting a layered security approach that combines these tools is designed to help businesses safeguard their assets while meeting regulatory requirements and ensuring their chance of breaches and attacks.





