- Introduction to Clickjacking
- How Clickjacking Works
- Types of Clickjacking Attacks
- Real-Life Examples of Clickjacking
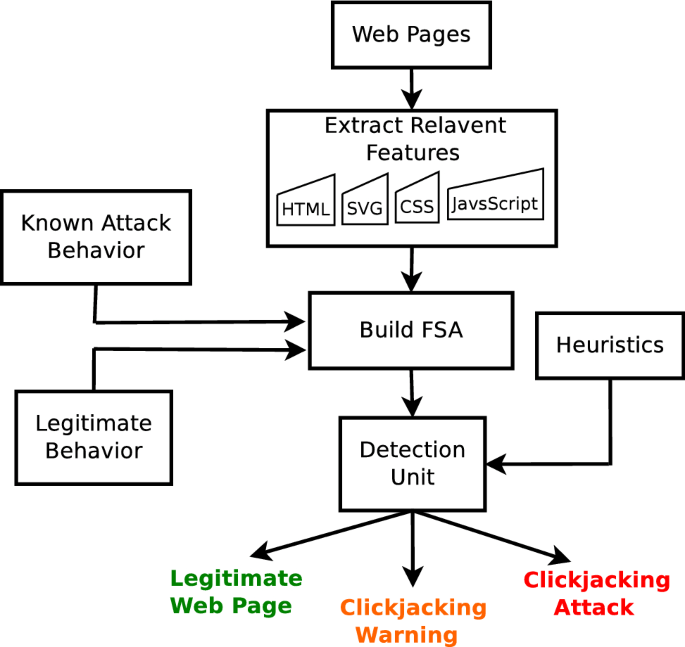
- How to Detect Clickjacking Vulnerabilities
- Mitigation and Prevention of Clickjacking
- Best Practices for Users
- Conclusion
Clickjacking is a deceptive technique used by attackers to trick users into unknowingly interacting with hidden or disguised elements on a webpage. It is a critical security concern that can lead to unauthorized actions, data theft, and account compromises. Detecting and preventing clickjacking is essential for safeguarding user interactions and maintaining web security, which is often covered in Cyber Security Training Courses . Cybercriminals use this technique to hijack clicks, redirect users, or execute unintended commands without their knowledge. Organizations must adopt security headers like X-Frame-Options and Content Security Policy (CSP) to defend against such threats. Regular security assessments and user awareness play a key role in minimizing clickjacking risks and ensuring a safer browsing experience. This blog will explore clickjacking, its significance, and effective ways to prevent it. We will also delve into various defense strategies, industry best practices, and security tools designed to mitigate clickjacking risks.
Are You Interested in Learning More About Clickjacking? Sign Up For Our Cyber Security Online Training Today!
Introduction to Clickjacking
Clickjacking is a cyber attack in which a user is deceived into clicking something that differs from what they see. This can, at times, lead to the release of secret information or allow malevolent actions. Most commonly, this is done by creating hidden or disguised layers on a legitimate webpage to fool the user into interacting with the evil element. This attack type is called “clickjacking” because it steals away clicks from the victim’s side without their notice. Hackers often use clickjacking to trick users into enabling webcam access, making unauthorized payments, or changing security settings, highlighting the growing need for Artificial Intelligence in Cybersecurity to detect and prevent such threats. Implementing security headers, such as X-Frame-Options and Content Security Policy (CSP), can significantly reduce the risk of these attacks. Raising user awareness and regularly testing web applications for vulnerabilities are crucial steps in preventing clickjacking threats.
How Clickjacking Works
Clickjacking works by embedding a malicious webpage or element inside a legitimate one, often through an iframe or similar method. A hacker overlays an invisible iframe with buttons or other clickable elements that appear as part of the actual content. When a user clicks something they believe to be harmless, they are unknowingly clicking on something else, such as clicking on a hidden button that makes a harmful action, perhaps transferring funds or changing settings, when clicking on a “Play” button on a video. Protecting against such attacks requires layers of security, including Firewall and Antivirus Software to help detect and block malicious activities.
This technique is widely used to hijack social media accounts, tricking users into unknowingly liking, sharing, or following malicious pages. Cybercriminals may also use clickjacking to bypass security mechanisms, such as enabling a device’s camera or microphone without consent. To prevent this, web developers should enforce security headers like X-Frame-Options and Content Security Policy (CSP). Regular penetration testing helps identify vulnerabilities before attackers can exploit them. Educating users to be cautious about unfamiliar websites and unexpected pop-ups can further minimize the risk of clickjacking attacks.
Types of Clickjacking Attacks
- UI Redress, or UI Spoofing: In UI Readdress, The attacker disguises the appearance of an element-for example, a button or a link that becomes indistinguishable from, say, a harmless graphic. The user believes to be interacting with the page as it should be, and the hidden element triggers actions like submitting a form or clicking a dangerous link.
- Likejacking: In this likejacking, attackers overlay an invisible iframe with a “Like” button (for example, from Facebook). When the user interacts with the page, they unwittingly “Like” a page, post, or malicious content.
- Click-to-Call Clickjacking: This attack targets mobile devices. Attackers overlay hidden buttons to trigger a call to a specific number, often leading to premium-rate services or fraud.
- Pay-Per-Click Clickjacking: The attacker puts hidden elements over ads or links so that the user, without knowing, clicks on them and generates revenue for the attacker or infects the system with malware.
- Clipboard Hijacking: Attackers manipulate clipboard functions, replacing copied content with malicious links or commands that execute when pasted elsewhere.
- Cursorjacking: By misaligning the visual cursor with the actual clickable area, attackers trick users into clicking unintended elements, leading to security breaches.
- Scrolljacking: This technique manipulates scrolling behavior, making users believe they are navigating normally while hidden interactions are triggered in the background.
- Source Code Inspection: The most basic way to identify clickjacking is to inspect the webpage’s source code. Look for iframes with unusual parameters or properties that might indicate an invisible element overlay. Implementing Network Segmentation can also help limit the scope of potential damage from such attacks by isolating sensitive parts of the network.
- Clickjacking Testing Tools: Tools like the Clickjacking Attack Testing Tool or X-Frame-Options Test Tool can help detect vulnerabilities by simulating clickjacking attacks on a page.
- Behavioral Analysis: Suspicious behavior occurs when the user’s action may not match their intention, i.e., unexpected redirects by the application. This might indicate an existing clickjacking vulnerability.
- Security Audits: Regular security audits or penetration testing can identify such potential clickjacking vulnerabilities by attempting to exploit the site’s UI.
- Anti-Clickjacking Browser Add-ons: Some browser add-ons, such as NoScript or ScriptSafe, may be able to block any iframes or scripts considered dangerous and potentially used to attack using clickjacking.
- Allow Click-to-Play for Flash and Java: Turning off the automatic run of Flash or Java applets prevents malicious scripts from running undetected by the user.
- Do not click on suspicious links: Be wary of clicking links or buttons in unfamiliar websites or emails, especially if they seem out of place. Understanding Network Topology can help in identifying suspicious activity and potential threats in the network, offering better protection against such risks.
- Update Your Browsers and Plugins: One should regularly update browsers and plugins to avoid known security flaws, including clickjacking.
- Enable Browser Security Extensions: Installing security-focused browser add-ons like NoScript or ScriptSafe can help prevent malicious scripts and iframes from executing clickjacking attacks.
- Restrict Auto-Execution of Plugins: Disabling the automatic execution of Flash and Java applets ensures that harmful scripts do not run unnoticed in the background.
- Exercise Caution with Unfamiliar Links: Avoid clicking on links or buttons from unknown sources, especially in unsolicited emails or suspicious websites, to prevent unintentional actions.
- Keep Browsers and Plugins Updated: Regularly updating web browsers and plugins patches security vulnerabilities, reducing the risk of exploitation through clickjacking techniques.
To Explore Clickjacking in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Real-Life Examples of Clickjacking
In 2010, attackers used clickjacking to trick users into “liking” pages that were malicious websites. The overlay attack utilized Facebook’s Like button, which was overlayed over legitimate content, thus inadvertently making users endorse harmful content. One other example was YouTube videos: hackers placed an invisible iframe over the “Play” button so that users would add videos to their playlists or like the video that benefited the attacker.More dangerous attacks might include online banking sites where a user clicks what they believe is the correct button to act, such as transferring funds, but clicks something that does the opposite. Understanding and preventing such attacks is a key focus in Cyber Security Training Courses . Clickjacking attacks can also be used to trick users into enabling their webcams or microphones, compromising their privacy. Malicious actors have leveraged this technique to spread fake news by forcing users to unknowingly share or engage with deceptive content. To mitigate such threats, organizations should implement frame-busting techniques and use modern security headers. Users should be cautious when interacting with unfamiliar websites, especially those that ask for unexpected actions. Regular security awareness training can help individuals recognize and avoid clickjacking attempts more effectively.
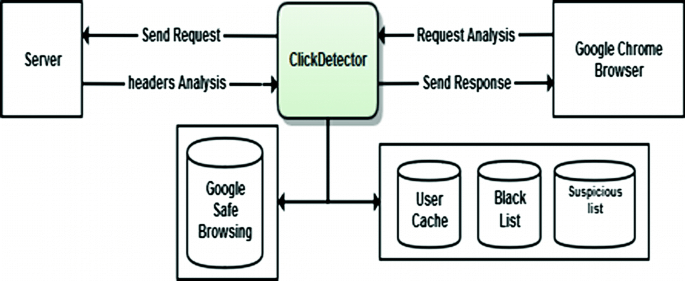
How to Detect Clickjacking Vulnerabilities
Are You Considering Pursuing a Cybersecurity Master’s Degree? Enroll For Cyber Security Expert Masters Program Training Course Today!
Mitigation and Prevention of Clickjacking
Use of X-Frame-Options Header: This is the most effective method to counter clickjacking. Set the `X-Frame-Options` HTTP header to `DENY` or `SAMEORIGIN.` In this way, the page will not be framed if loaded in an iframe by any other domain. Implement a Content Security Policy with a `frame-ancestors` directive that controls which domains can embed the page in a frame. This provides an additional layer of security by blocking potentially harmful domains. Developers can make use of JavaScript to identify whether their content is displayed within an iframe and automatically break out of the iframe. This practice is an important part of Cyber hygiene, ensuring that web applications are protected from vulnerabilities like clickjacking. This way, the page cannot be tricked into a clickjacking attack. Educate users to exercise caution when clicking on links or buttons. They should be especially cautious when such links or buttons appear suspicious or are placed in unusual areas of page. Ensure that critical actions, such as transferring funds or changing settings, require secondary authentication or confirmation to avoid accidental clicks. Attackers often refine their tactics to bypass traditional security measures, making continuous monitoring essential. Regular penetration testing helps identify new vulnerabilities before they can be exploited. Security teams should enforce multi-factor authentication (MFA) for high-risk actions to minimize unauthorized access. Web browsers are also introducing built-in security features to help prevent clickjacking, so keeping software up to date is crucial. Combining technical defenses with user education significantly strengthens protection against clickjacking threats.
Best Practices for Users
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Conclusion
Clickjacking is an important threat to security. It manipulates the elements people interact with on web pages to execute unintended actions from users. It may lead to large-scale effects, such as financial fraud and the spreading of malicious content. Detection and mitigation of clickjacking require a combination of technical solutions, user awareness, and proactive security measures. Developers should use X-Frame-Options, Content Security Policy headers, and regular security audits to protect their sites, while users should be cautious and informed about the threat, knowledge often gained through Cyber Security Training Courses. Attackers often exploit clickjacking to trick users into granting unauthorized permissions or making unintended transactions. Web developers must integrate frame-busting techniques to prevent malicious overlays from deceiving users. Strengthening browser security settings and educating users about suspicious web interactions can further reduce the risk of clickjacking attacks.





