
- What is cybersecurity?
- Types of cyber security
- What are the cybersecurity threats?
- Cybersecurity Threats and Security Risks
- Types of cybersecurity threats
- Conclusion
These different types of cyber security must be understood to secure digital infrastructures and protect sensitive data in this ever-evolving digital world. To defend against these breaches, as cyber threats continue to rise, the implementation of diverse cybersecurity solutions is necessary. Each form of Cybersecurity Training Courses, be it cloud security, endpoint security, network security, or information security, is crucial to minimizing cybersecurity risks and protecting individual and corporate information. Even the wrongful exploitation of software and apps is protected with application security and counter-attack mechanisms. Understanding how to safeguard different digital assets is critical in reducing vulnerabilities while ensuring safety in all sectors since threats have multiplied in today’s linked world.
To become a certified cyber security, have a look at our Cyber Security Online Training right now.
What is cybersecurity?
Computer security, sometimes referred to as cybersecurity, digital security, or information technology (IT) security, is designed to protect a computer’s software, systems, and networks against threats that can lead to the disruption or diversion of the services offered, theft or damage in hardware, software, or data, or illegal disclosure of information. This field is important because of the increased use of computers, the Internet, and wireless network protocols for How to become cybersecurity analyst . The same reason is further added due to the proliferation of smart devices such as televisions, smartphones, and many other devices making up the Internet of Things (IoT). The society supported by information systems and their complexity brought forth cybersecurity as one of the greatest new issues the modern world is facing. Systems that control extensive systems with far-reaching physical impacts require extra security.
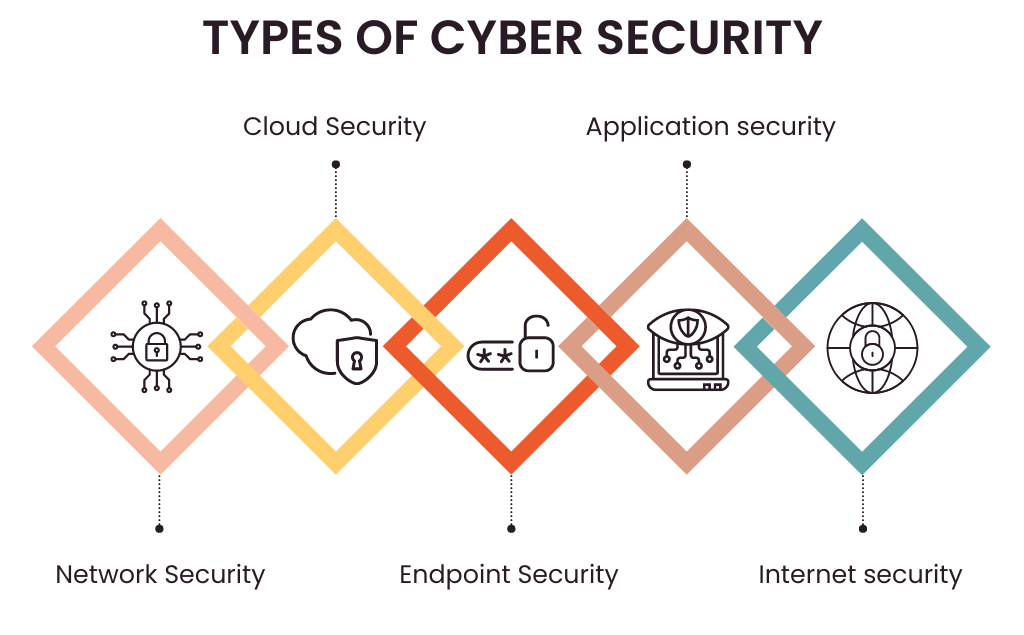
Types of cyber security
All of the organization’s resources are the outcome of multiple systems. Due to the strong cybersecurity posture of all these systems, all have to function in unison. Hence, the following sub-domains can be used to classify cybersecurity:
Are you curious to know more about Cybersecurity ? Take advantage of our comprehensive online Cyber Security Online Training .
- Network Security: Network security guards against intrusions, which range from malicious software to targeted attackers. This type of security ensures that your network is available, confidential, and intact. Intrusion prevention systems, intrusion detection systems, and firewalls are key components of network security.
- Cloud Security :As cloud computing has increased in utilization and popularity, there is a growing need to protect data kept on cloud servers. By using policies, tools, and controls, Advantages of Cybersecurity cloud security seeks to protect cloud data, apps, and infrastructure against threats.
- Endpoint Security: The ultimate objective of endpoint security is to keep end-user devices, such as laptops, desktop computers, and even mobile phones, safe from cyberattacks. Since they are portals through which cyberattacks enter, their security is very important.
- Application Security: Application security is simply the process of protecting software programs from vulnerability at all life cycle stages, starting from design to development. The need to protect these apps is due to their frequent handling of sensitive data and susceptibility to attack.
- Information Security: Information security, or InfoSec, is the protection of data availability and confidentiality. It means that, through such protection, information is kept unmodified and available whenever it is needed; at the same time, only authorized people can access the given information.
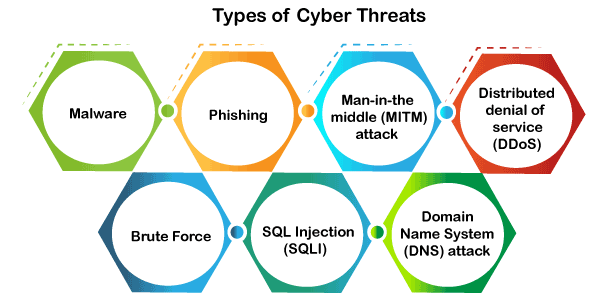
- Malware: The most common type of attack is malware, abbreviated as “malicious software,” which consists of viruses, worms, trojans, spyware, and ransomware. Malware typically enters a system through an untrusted website link or email and also through unsolicited software downloads.
- Phishing: Phishing is a type of cybercrime. In this, the sender sends the email while pretending to be a genuine company, such as PayPal, eBay, financial institutions, or friends and colleagues. They initiate contact with a target or targets by phone, Confidentiality in Cybersecurity email, or text message and offer them a link to click on.
- Man-in-the-middle (MITM) attack: A cybercriminal can intercept a conversation or data transfer between two people by employing a man-in-the-middle attack, which is a type of cyber threat—a type of eavesdropping assault. Once the cybercriminal enters this two-way conversation, they seem to be legitimate participants, and they have the potential to collect private data and give different answers.
- Distributed denial of service (DDoS): Cybercriminals use internet traffic to carry out legitimate requests to the target or its surrounding infrastructure, thus disturbing the usual traffic of the targeted servers, services, or networks. This is a form of cyber threat or hostile effort.
- Brute Force: Brute force attacks are cryptography hacks that guess every possible combination until the right information is found, much like a trial-and-error approach. Cybercrooks usually use this attack to obtain personal data such as encryption keys, PINs, login credentials, and targeted passwords.
- SQL Injection (SQLI): SQL injection is the most common form of attack when hackers use malicious SQL scripts to smuggle backend databases and compromise private data stored in the SQL database. When successful, the attack allows a malicious actor to view, manipulate, Ransomware in Cybersecurity and delete sensitive customer information, user lists, or company-related data.
- Domain Name System (DNS) attack: A DNS attack is one type of cyberattack in which hackers make use of flaws in the domain name system to redirect users toward harmful websites (DNS hijacking) and steal information from breached systems. Because of its critical role in internet architecture, this indeed spells out an acute cybersecurity threat.
What are cybersecurity threats?
Cybersecurity threats are malicious activities performed by other humans who want to take information, hurt, or interfere with computer systems. Malware, injection attacks, denial of service attacks, Cyber Defamation man-in-the-middle attacks, and social engineering are several common types of cyber threats; we go into greater detail on each of these types below. The sources of cyber threats vary from terrorist organizations and hostile nation-states to lone hackers to trusted persons, including contractors or workers, who abuse their powers for nefarious actions.
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Today!
Cybersecurity Threats and Security Risks
In the digital world, individuals, as well as organizations, need to be aware of cybersecurity threats and security risks. With the changing landscape of cybercrime, these attacks are changing and becoming more subtle and diverse. These risks have serious consequences, including money loss, data breaches, and damaging reputations for a company. It is essential to know and also be vigilant of many prevalent risks, along with the risks associated with them, to prevent them. From the very start, developing effective protection strategies is first dependent on the understanding of Cybersecurity Training Courses and security issues. The sophistication of cyberattacks has risen in both government and corporate as well as personal data
Types of cybersecurity threats
Understand cybersecurity threats to create effective defences. Cybercriminals are always developing new attack techniques to exploit weaknesses in systems, networks, and applications. The list below is some of the most current and destructive cybersecurity threats:
Preparing for a job interview in cybersecurity ? Examine our blog post about Cybersecurity Interview Questions and Answers to get the most of your employment experience!
Conclusion
The increasingly digital climate of today demands proper cybersecurity protection. Knowledge about various types of cyber security ensures that people and organizations can protect their networks, systems, and sensitive data from fast-evolving Cybersecurity Training threats. A wide field of cybersecurity includes diverse disciplines, such as network security, information security, endpoint security, application security, and cloud security. All these categories are focused on various aspects of security and provide targeted solutions to prevent cyberattacks, data breaches, and unwanted access. Building layered defences using integrated multiple cybersecurity solutions helps people and organizations protect themselves against threats from within or outside. Security risks continuously evolve to become sophisticated; hence, a safe online environment for both individuals and organizations requires matching the most recent cyber developments coupled with putting suitable cybersecurity measures in place to reduce risks.





