
- What is Enumeration in Ethical Hacking?
- Why Enumeration is Important in Ethical Hacking
- The Enumeration Process
- Enumeration Techniques
- Standard Enumeration Tools in Ethical Hacking
- Application of Enumeration
- Best Practices for Responsible and Effective Enumeration
- Challenges of Enumeration
- Conclusion
Enumeration is the most important phase of ethical hacking and penetration testing, as identifying vulnerabilities in any target system or occurs during this phase. Enumeration is an active probing and inquiry of systems for information extraction purposes, which could indicate weak points for later exploitation by an attacker. Enumeration is a fundamental aspect that any ethical hacker needs to master in exposing security flaws before being exploited by a malicious actor. Enumeration in Ethical Hacking This blog explores ethical hacking, its importance, various techniques used, popular tools, examples from the actual world and best practices to guarantee effective and responsible enumeration.
What is Enumeration in Ethical Hacking?
Enumeration gathers detailed information about a target system, hacking network, or application. Cybersecurity Training Courses, the ceh enumeration process happens after reconnoitres (a passive gathering phase) but before exploitation, where inferences of detected vulnerabilities are tested. Enumeration seeks to gather critical information about the target, including active services, open ports, system configurations, and usernames, among others that would present security risks.
Unlike passive surveillance, which is an activity by hackers to gather information available in public space without any interaction with the targeted site, enumeration is an active task in that ethical hackers send requests or probes to the targeted site to avail certain details, which may help find entry points or weaknesses in it.
Enroll in ACTE’S Cyber Security Online Training if you want to become an expert in cyber security field and have a prosperous career.
Why Enumeration is Important in Ethical Hacking
Enumeration forms the main phase of ethical hacking because of the following:
- Attack Vectors Revealed:Enumeration reveals surfaces the white-hat hacker could attack within the system or network open ports, running services, and available hacking network shares. These are possible entry points the attacker may utilize.
- Hidden Resources Found: Enumeration allows hackers to find resources not found by regular website vulnerability scan, such as user accounts, directories, or system services that might be vulnerable to attacks.
- Pre-emptive Security Breaches: Enumeration allows ethical hackers to discover vulnerabilities and weaknesses before cybercriminals can exploit them. Taking a pre-emptive approach to security strengthens organizations’ defences.
- Leading to Exploitation: : Enumeration data helps ethical hackers identify the best resources and methods for exploitation, such as identifying vulnerable services to target. It also provides insight into security measures like Whitelisting, which can affect exploitation strategies. By considering these factors, hackers can plan more efficient and targeted attacks.
- Supporting Compliance: Enumeration also has an important purpose in regulatory compliance. Some compliance frameworks-for example, HIPAA or PCI-DSS-require regular vulnerability detection assessments. Many such assessments rely on ceh enumeration to identify exposed services or misconfigured systems.
The Enumeration Process
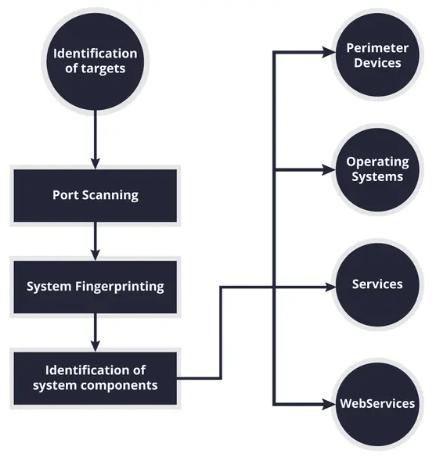
- Target Identification: From the perspective of an ethical hacker, the first step would be to identify a target system or hacking network. The targets are servers, workstations, applications, or even IoT devices.
- Information Gathering: This step tells how to make an identification of basic information about the target, making use of IP addresses, domain names, and services over the system.
- Active Scanning/Probing: The enumeration technique is engaged here. Hackers send specific queries or requests to the target to fetch sensitive information about system services, user accounts, and configuration details.
- Data Analysis: Once all such information is gathered, the ethical hacker analyses the data to extract potential vulnerabilities, such as exposed services, default credentials, outdated software, or misconfigurations.
- Exploitation: Armed with enumeration results, the ethical hacker attempts to exploit identified vulnerabilities to assess their impact. Sharing these findings through platforms like Cyber Media helps raise awareness and promote better security practices.
- Reporting: After conducting the vulnerability detection test, the ethical hacker prepares a concise report detailing the outcome, including observed vulnerabilities, exploited vulnerabilities, and recommendations for remediation.
- denim
- Fierce
- Nmap
- SNMP walk
- onesixtyone
- nbtstat
- NBTScan
- SMTP-user-enum
- Metasploit
Become an expert in cyber security. Enroll in this Cyber Security Online Training now to acquire the knowledge you need..
Enumeration Techniques
Ethical hackers use various techniques to gather specific system information through enumeration. These include some of the most common methods used:
DNS Enumeration
This means sending DNS queries to the target’s Domain Name System to fetch useful information such as subdomains, IP addresses, mail servers, and more related DNS information. Therefore, this is good for ethical hackers to be aware of other resources accessible through the target’s domain.
DNS Enumeration Tools
SNMP Enumeration
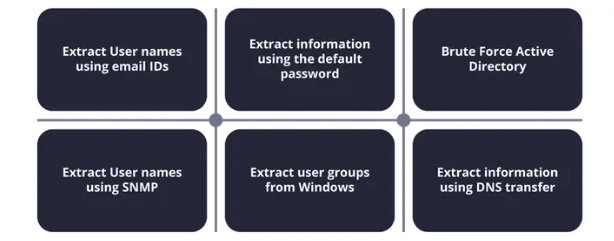
SNMP is management and monitoring software used for device-to-device and client-to-server communication on a network. Enumerating SNMP will reveal all the information involving the devices, ranging from their names to variations of hacking network configurations and even user credentials.
SNMP Enumeration Tools
NetBIOS Enumeration
NetBIOS Enumeration Techniques is used to gather information from Windows-based systems. It will reveal shared network resources, usernames, and system names that may be used later in exploitation. Knowing this is vital to improving web security because it lets the ethical hacker know which attack vectors to look for and vulnerabilities within a networked environment.
Tools for Enumeration of NetBIOS:
SMTP Enumeration
Emails are sent over the Simple Mail Transfer Protocol, or SMTP. SMTP ceh enumeration helps the ethical hacker discover valid email addresses and misconfigurations in mail servers that can be exploited in phishing or spam attacks. This information can also assist in identifying weak security controls, which could lead to further exploitation of the email system.
SMTP Enumeration Tools
LDAP Enumeration
LDAP is a protocol for querying any given directory service, such as Active Directory, about anything: users, groups, and the structure of an organization. Ethical hackers use LDAP Enumeration Techniques to map out a target’s directory structure.
LDAP Enumeration Tools
- LDAP search
- Enum4linux
- rpcclient
- enum4linux
- Nmap: This hacking network website vulnerability scan tool can identify running services, help determine operating systems, and indicate open ports. It also greatly supports enumerations.
- Netcat:This versatile networking tool is also known as the Swiss army knife. Enumeration is used in Netcat, especially when picking banners on services and testing services in Cybersecurity Training.
- MetasploitMetasploit is an example of a penetration testing framework that delivers several enumeration modules on different protocols, such as SMTP and DNS. It also includes implementing SNMP.
- Enum4linux: This is a Linux auxiliary tool that retrieves information from SMB and NetBIOS using Windows-based systems.
- Nikto: It is used to website vulnerability scan a web server for enumerating it and to detect vulnerabilities in web servers and applications; it is mainly used for HTTP-based enumeration.
- Nessus: It is used to website vulnerability scan a web server for enumerating it and to detect vulnerabilities in web servers and applications; it is mainly used for HTTP-based enumeration.
- Nessus: It performs a vulnerability detection website vulnerability scan. Enumeration and further vulnerability assessments are carried out, leading to powerful reports regarding discovered risks.
RPC Enumeration
Remote Procedure Call (RPC) enumeration gathers information regarding services running on other systems, including shared resources, running applications, and system configurations. By identifying these services, ethical hackers can pinpoint potential vulnerabilities that could be exploited for unauthorized access or further attacks.
Tools for Enumeration of RPC:
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Today!
Standard Enumeration Tools in Ethical Hacking
Enumeration in ethical hacking is one of the several tasks ethical hackers carry out as part of their work, among many others. Enumeration tasks can be performed by an ethical hacker using any of the following common tools:
Application of Enumeration
Enumeration is extensively followed in many various cybersecurity scenarios, such as,
- Penetration Testing: Enumeration plays a significant role in penetration testing engagements; the ethical hacker relies on it to enumerate vulnerabilities that might lead to system compromise or breaches.
- Vulnerability Assessments:Enumeration is one of the most vital composability assessments, assisting in finding potentially hazardous services and configurations. It is crucial for Vulnerability Management since it enables businesses to prioritize security weaknesses and fix them before exploitation.
- Social Engineering:The attackers may use enumeration techniques to collect email addresses or even the names of employees to launch social engineering attacks, such as phishing.
- Red Team Exercises:During the red team exercises, hackers perform real-world attacks, including ceh enumeration, to measure how good an organization is at detecting and responding.
- Firewall and IDS/IPS Evasion: Firewalls or IDS/IPSs may protect several systems and block ceh enumeration probes. Hackers need to use stealthy techniques or bypass them.
- Advanced security systems:Several defence measures for the selected target range from division networks to two-factor authentication and encrypted communications that cannot be enumerated.
- Legal and Ethical Issues: Enumeration is illegal without permission. Therefore, the ethical hacker must respect the code of ethics and obey the law. He should seek permission before any enumeration activity occurs.
Best Practices for Responsible and Effective Enumeration
For responsible and effective enumeration, some best practices from an ethical hacker should exist. The first would be to seek explicit, written permission before enumerating a target system or network. This would mean that all such processes are authorized and legal. Secondly, the least disruption to service should be caused with minimal disruption of services, as in the case of production, for its heavy trafficking or resource-intensive and impacts the system performance. All these and the results obtained are kept in detailed records for later analysis and reporting steps. As such, the final precaution requires that the ethical hacker merely choose the right tool to not trigger firewalls and intrusion detection systems from more aggressive website vulnerability scan
Preparing for a job interview in cybersecurity ? Examine our blog post about Cybersecurity Interview Questions and Answers to get the most of your employment experience!
Challenges of Enumeration
Enumeration is a highly effective process, but it comes with its challenges. One key obstacle is ensuring Cyber Awareness within an organization, as security teams must stay informed about emerging threats, tools, and techniques that can impact enumeration efforts.
Conclusion
Enumeration in ethical hacking is one of the crucial steps that goes hand in hand with the penetration testing process. It provides much-needed knowledge of the target system or network by extracting useful information that could reveal vulnerabilities that malicious hackers might exploit. By utilizing various methods of enumeration, the right tools, and following best practices, an ethical hacker can identify security gaps and improve an organization’s defense mechanisms more effectively. This stage is essential in ensuring the system’s vulnerabilities are identified and addressed before they can be exploited by Cybersecurity Training. As threats advance in cybersecurity, so does the need for enumeration. Organizations will be in a good position to battle some would-be attackers and thus avoid expensive security breaches if their ethical hackers understand and apply this technique correctly.





