
- Definition and Concept
- How Brute Force Attacks Work
- Types of Brute Force Attacks
- Common Targeted Systems
- Tools Used in Attacks
- Prevention and Mitigation Techniques
- Role of CAPTCHA and Rate Limiting
- Password Complexity and Security
- Real-World Incidents
- Best Practices to Defend
- Conclusion
Definition and Concept
A brute force attack is a trial-and-error method used by attackers to gain unauthorized access to accounts, networks, or encrypted data by systematically trying all possible combinations of passwords or encryption keys. Unlike more sophisticated hacking techniques that rely on software vulnerabilities or social engineering, Cyber Security Training equips professionals to defend against brute force attacks, which depend purely on computational power and patience. Though seemingly basic, these attacks can be highly effective, especially when weak passwords or poorly secured systems are involved. Because of their simplicity and widespread applicability, brute force attacks remain a common threat in the cybersecurity landscape. Brute force attacks involve attempting every possible password or key until the correct one is found. The concept is rooted in exhaustive search methods, where all potential options are tested without regard to efficiency. Attackers use automated tools to perform these attacks at high speeds, leveraging dictionary lists, precomputed password hashes, or even random character generation. The method requires minimal technical sophistication, making it accessible to a wide range of threat actors, from amateur hackers to advanced cybercriminal groups.
Interested in Obtaining Your Cyber Security Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
How Brute Force Attacks Work
In a brute force attack, the attacker selects a target login page or encrypted file and uses a software tool to guess passwords or encryption keys. Using a Virtual Private Network Enhancing Security can help obscure attack attempts. The software rapidly submits a series of potential credentials until the correct combination is discovered.
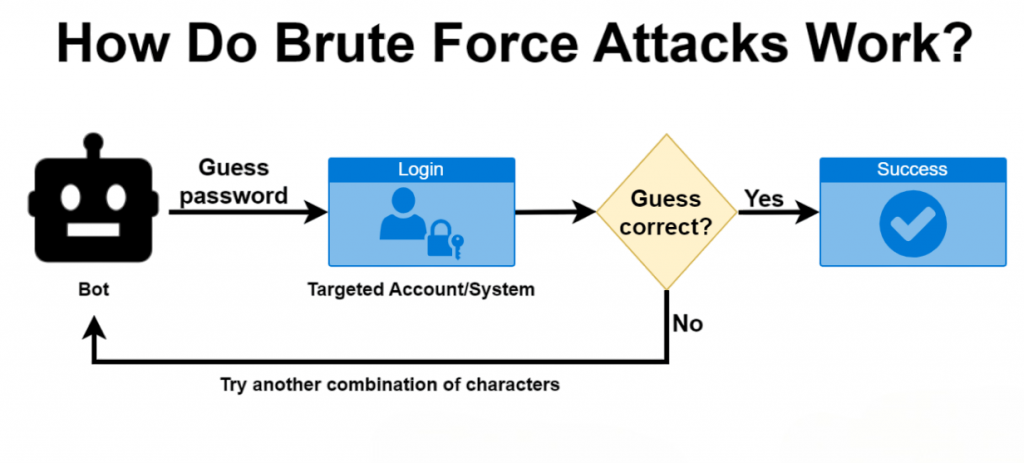
The speed and success rate of the attack depend on several factors, including the length and complexity of the password, the computing power available, and the presence of defensive mechanisms like account lockouts or rate limiting. Once a valid credential is found, the attacker can gain full access to the system, often with minimal detection.
Types of Brute Force Attacks
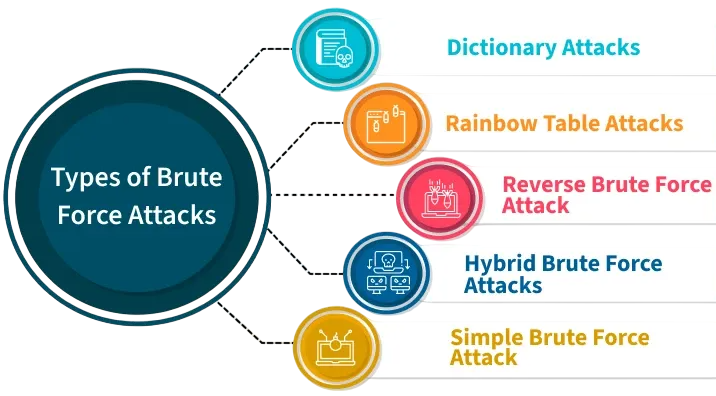
Brute force attacks come in various forms, each designed to increase efficiency or evade detection:
- Simple Brute Force Attack: Attempts every possible combination of characters until it finds the right one. This method is time-consuming and often used for short passwords.
- Dictionary Attack: Uses a predefined list of common words, passwords, or phrases in hopes that the target used one of them.
- Hybrid Attack: Combines dictionary attacks with brute force by appending or prepending numbers and symbols to dictionary words.
- Reverse Brute Force Attack: Starts with a known password and tries it across multiple usernames.
- Credential Stuffing: Uses previously stolen usernames and passwords to try to gain access to other accounts, capitalizing on reused credentials.
- Rainbow Table Attack: Utilizes precomputed tables of hashed passwords and their corresponding plaintext values to reverse-engineer hashed data.
- Account Lockout Mechanisms: Temporarily disable accounts after a set number of failed attempts.
- Rate Limiting: Restrict the number of login attempts within a given timeframe.
- IP Blacklisting or Geo-blocking: Prevent access from suspicious or known-malicious IP addresses.
- Multi-Factor Authentication (MFA): Requires an additional authentication method beyond the password.
- Strong Password Policies: Enforce the use of complex, long, and unique passwords.
- CAPTCHA Implementation: Use CAPTCHA to differentiate between human users and bots.
- Monitoring and Logging: Detects suspicious behavior through security event logs and alerts.
- Zero Trust Architecture: Validate all access attempts regardless of their origin.
- Minimum Length: At least 12 characters long.
- Character Variety: A mix of uppercase and lowercase letters, numbers, and special symbols.
- Avoid Predictable Patterns: Avoid common phrases, personal information, or keyboard patterns (e.g., “123456” or “qwerty”).
- Uniqueness: Use a different password for each account.
- Password Managers: Employ tools to store and generate strong passwords securely.
- Enforcement Strategies: Organizations can implement password complexity via policy settings and periodic audits.
- Yahoo Data Breach (2013–2014): Hackers used brute force and stolen credentials to access over 3 billion user accounts.
- Magento Sites (2020): Thousands of e-commerce websites were compromised via brute force attacks on admin panels.
- WordPress Attacks: Frequently targeted with brute force attempts on admin login pages, especially for sites with weak credentials.
- SSH Server Attacks: Automated tools are often used to brute force SSH credentials, allowing unauthorized server access.
- GitHub Account Takeovers: In some cases, brute force attacks have led to stolen login credentials and unauthorized access to repositories.
- Use Multi-Factor Authentication: Even if passwords are compromised, MFA can block unauthorized access.
- Implement Account Lockout Policies: Temporarily disable accounts after multiple failed login attempts.
- Adopt CAPTCHA Challenges: Prevent automated login attempts using human-verification tools.
- Monitor Login Activity: Track login attempts and alert on unusual patterns or geographic anomalies.
- Educate Users: Promote awareness about secure password practices and phishing threats.
- Regularly Update Systems: Patch vulnerabilities in software and platforms that may be exploited.
- Employ Network Security Tools: Use firewalls, intrusion detection systems (IDS), and endpoint protection.
- Limit Login Interfaces: Restrict administrative or remote access portals to specific IP ranges.
- Use Encrypted Communication: Ensure that login pages and credentials are transmitted securely.
- Audit and Review Access Logs: Regularly analyze logs for signs of brute force activity or anomalies.
- AES: Adopted by the U.S. government and widely used in public and private sectors.
- RSA: Standard for secure data transmission, especially in digital certificates and public key infrastructures (PKIs).
- TLS/SSL: Protocols that use encryption to secure internet communications.
- PGP (Pretty Good Privacy): Used for securing emails and files.
- IPSec: Encrypts data at the network level for secure VPNs.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Common Targeted Systems
Brute force attacks target a wide range of systems, including: In today’s ever-changing cybersecurity landscape, hackers carefully look for weak points in various technology systems. Cyber Security Training is crucial in protecting email accounts, which are a common target due to the wealth of personal and work-related information they hold. Websites like online banking, shopping sites, and social media platforms also attract attackers due to the valuable data they hold. Remote access tools such as SSH, RDP, and VPNs are often hacked, allowing unauthorized users to enter important network systems. Databases and platforms like WordPress, Joomla, and MySQL are also vulnerable, making them easy targets for criminals. Even encrypted files and devices aren’t safe, as hackers keep trying to break into password-protected files and encrypted storage. With more people using cloud services, companies like AWS, Azure, and Google Cloud have become prime targets. This shows how important it is to have strong and layered cybersecurity defenses in our connected digital world.
Tools Used in Attacks
Several tools have been developed to automate brute force attacks. These tools can try millions of passwords per second: Understanding the Key Skills Required for Cybersecurity is vital. In cybersecurity, there are several strong tools used for checking network and password security. Hydra is a flexible tool that helps crack network logins and works with many different types of connections. John the Ripper is a complete tool for breaking passwords using methods like trying every possible combination or using word lists. Hashcat is special because it uses computer graphics processors to speed up password recovery and can handle advanced techniques like mixing different types of attacks. Aircrack-ng focuses on testing Wi-Fi networks and can check the security of older WEP and newer WPA encryption keys. Medusa is a quick and adaptable tool for trying many login combinations at the same time. Along with these, Burp Suite is a detailed tool for finding web security issues and includes features for testing login security through brute force. All these tools together make a powerful set for security experts who want to check for weak spots in networks.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Prevention and Mitigation Techniques
Prevention and mitigation To defend against brute force attacks, organizations and users must adopt layered security strategies. Common prevention and mitigation measures include:
Role of CAPTCHA and Rate Limiting
CAPTCHA and rate limiting are frontline defenses against brute force attacks. CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) prevents automated systems from submitting forms or login attempts by requiring user interaction. It is effective in blocking bot-driven brute force tools. Rate limiting, on the other hand, restricts how frequently requests can be made to a particular resource. For example, limiting login attempts to five per minute per IP address significantly reduces the effectiveness of brute force attacks. Both techniques slow down attackers and increase the chance of detection, making brute force attacks more difficult and less appealing.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Password Complexity and Security
Among today’s most pressing concerns are Cybersecurity Threats. Strong passwords are essential in defending against brute force attacks. Passwords that are short, common, or easily guessable can be cracked within seconds. Best practices for secure passwords include:
Real-World Incidents
Brute force attacks have led to numerous high-profile security breaches. Here are a few notable examples:
These incidents highlight the importance of strong security hygiene and the implementation of multi-layered protection strategies.
Best Practices to Defend
Network Penetration Testing when defending against brute force attacks, as it ensures a balanced approach between technology, policy, and awareness. Here are some best practices:
Encryption Standards (AES, RSA, etc.)
Encryption standards are established protocols that ensure interoperability, security, and performance. Key standards include:
These standards undergo regular reviews and updates to remain effective against evolving threats.
Conclusion
Brute force attacks are a persistent and dangerous cybersecurity threat due to their simplicity and effectiveness. While the method relies on exhaustive guessing, its success often hinges on human error, especially the use of weak or reused passwords. Cyber Security Training enables individuals and organizations to better prepare their defenses by understanding the nature of brute force attacks, the tools used, and the systems they target. Implementing strong authentication measures, enforcing password policies, and using advanced monitoring tools are crucial steps in mitigating the risk. As digital environments grow more complex, proactive security measures remain essential in combating brute force and other evolving threats. The success of these attacks often relies on human errors. When users create weak passwords, they provide hackers with an easy way in. Many people still pick simple passwords because they are easy to remember, but this puts their accounts at risk. Reusing passwords across different accounts increases the danger. If a hacker gains access to one site, they can attempt the same password on others and possibly reach important data. Attackers also use specific tools called “brute force software” that automate the guessing process. These tools can try thousands or even millions of password combinations quickly, making it easier to break into accounts with little effort.




