
- Importance of Cloud Security
- Categories of Cloud Security Tools
- Tool 1: AWS Security Hub
- Tool 2: Microsoft Defender for Cloud
- Tool 3: Google cloud protection Command Center
- Tool 4: Prisma Cloud by Palo Alto
- Tool 5: Trend Micro Cloud One
- Tool 6: Check Point CloudGuard
- Tool 7: CrowdStrike Falcon
- Tool 8: Tenable.io for Cloud
- Tool 9: Orca Security
- Tool 10: Lacework
- Comparison and Use Case Scenarios
Importance of Cloud Security
With the rising dependence on cloud computing services, securing digital assets stored in the cloud has become a business-critical priority. Organizations today use cloud environments to store sensitive data, run business applications, and manage day-to-day operations. However, these environments are constantly targeted by cyber threats, including data breaches, account hijacking, and denial of service attacks making the deployment of an Intrusion Prevention System essential for real-time threat detection and prevention. Cloud security tools have emerged as a crucial part of enterprise cybersecurity strategies to mitigate risks, ensure compliance, and maintain operational continuity. They provide visibility, enforce policy compliance, detect anomalies, and protect against malware, unauthorized access, and misconfigurations. Given the shared responsibility model in cloud computing, both cloud providers and users must implement robust security measures to ensure a secure environment.
Categories of Cloud Security Tools
- Cloud Security Posture Management (CSPM): Helps identify and remediate misconfigurations.
- Cloud Workload Protection Platform (CWPP): Secures workloads like virtual machines and containers.
- Cloud Infrastructure Entitlement Management (CIEM): In Cloud Computing environments, it manages identity and access controls to ensure that only authorized users can access sensitive resources and services.
- Security Information and Event Management (SIEM): Monitors and analyzes security events in real time.
- Cloud Access Security Broker (CASB): Acts as a control point between cloud service users and providers.
- Data Loss Prevention (DLP): Prevents sensitive data exposure. Each tool might specialize in one or more of these areas, providing a comprehensive or focused security approach depending on organizational needs.
A Interested in Obtaining Your Cloud Computing Certificate? View The Cloud Computing Training Offered By ACTE Right Now!
Tool 1: AWS Security Hub
AWS Security Hub centralizes security findings from various AWS services and third-party tools into a single dashboard. It provides a unified view to automate compliance checks and security alerts, and works in tandem with Network Penetration Testing to identify and remediate vulnerabilities before attackers can exploit them. AWS Security Hub integrates with Amazon GuardDuty, AWS Config, and AWS Firewall Manager, offering threat detection, configuration management, and firewall rule auditing. Its capability
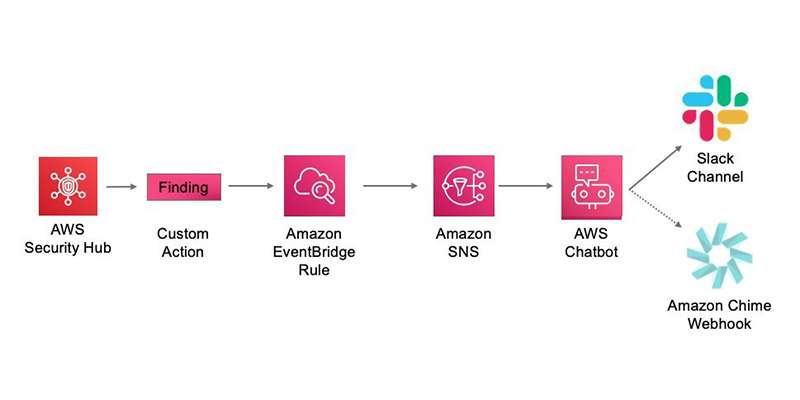
to apply security standards like CIS AWS Foundations Benchmark makes it a popular choice for organizations using AWS services extensively.
Tool 2: Microsoft Defender for Cloud
Microsoft Defender for Cloud (formerly Azure Security Center) offers advanced threat protection for workloads in Azure, on-premises, and other cloud platforms. In Cloud Computing , it continuously assesses security configurations, recommends improvements, and applies security policies. Features include Just-in-Time VM access, adaptive application control, and other tools that enhance overall cloud security and integrated threat intelligence. Defender for Cloud supports hybrid cloud environments and provides deep integration with Microsoft Sentinel for extended SIEM functionalities.
Tool 3: Google cloud protection Command Center
- Google Cloud protection Command Center (SCC) is a comprehensive risk management and data security platform that helps detect and respond to threats across Google Cloud assets.
- Understanding Cybercrime and its Implications is crucial, as it provides visibility into vulnerabilities, misconfigurations, and compliance violations that could be exploited by malicious actors
- SCC integrates with services like Cloud Armor, Forseti, and Event Threat Detection to enforce security policies and respond to incidents in real time.
- Its native support for GCP workloads makes it an essential tool for organizations leveraging Google Cloud services.
Tool 4: Prisma Cloud by Palo Alto Networks
Prisma Cloud delivers a broad set of cloud-native security capabilities across the entire application lifecycle. It provides CSPM, CWPP, CIEM, and As part of , it’s essential to understand platforms like Prisma Cloud, which offer container security features in a single platform. Prisma Cloud supports AWS, Azure, GCP, and Kubernetes, making it ideal for securing multi-cloud and hybrid cloud environments. It offers runtime protection, vulnerability management, compliance enforcement, and network visibility for cloud-native applications. Organizations seeking an integrated solution often favor Prisma Cloud for its deep security coverage.
To Earn Your Cloud Computing Certification, Gain Insights From Leading Blockchain Experts And Advance Your Career With ACTE’s Cloud Computing Training Today!
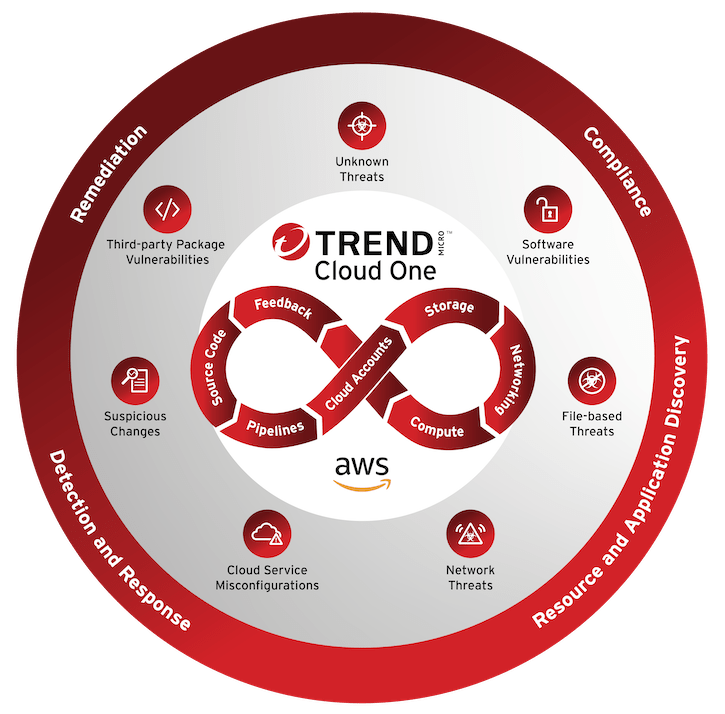
Tool 5: Trend Micro Cloud One
- Trend Micro Cloud One is a security services platform for cloud builders, providing automated security across file storage, containers, serverless environments, and cloud configurations.
- It includes components like Conformity (CSPM), Workload Security (CWPP), and File Storage Security.
- Trend Among modern Cyber Security Tools, Micro’s strength lies in its ability to integrate into DevOps pipelines, enabling security at the speed of development.
- Its vulnerability shielding, anti-malware, and log inspection features make it a strong contender in cloud-native security.
Tool 6: Check Point CloudGuard
CloudGuard by Check Point offers cloud-native security and compliance automation for public, private, and hybrid cloud environments. It includes features like posture management, threat intelligence, and application layer security. CloudGuard supports infrastructure as code (IaC) scanning, security blueprints, and workload protection. It also offers network security for cloud VPCs through threat prevention, intrusion detection and prevention systems (IDPS), and secure connectivity across cloud environments. Its strong firewall and segmentation capabilities make it ideal for large-scale enterprises.
Tool 7: CrowdStrike Falcon
CrowdStrike Falcon delivers endpoint protection through a lightweight agent that offers detection, prevention, and response capabilities across cloud workloads. In the Overview of Cybersecurity Threat , Falcon stands out as it leverages artificial intelligence and behavioral analytics to detect and stop threats. Its integration with AWS, Azure, and Google Cloud provides robust, cloud-native protection. vulnerability management, and threat intelligence in real time. Its dashboard offers visual insights and alerts, making it user-friendly and highly efficient in active threat hunting.
Tool 8: Tenable.io for Cloud
- Tenable.io provides visibility into cloud infrastructure and misconfigurations by offering continuous monitoring and compliance assessments.
- It supports multi-cloud environments and offers pre-configured policies for regulatory compliance such as GDPR, HIPAA, and PCI-DSS.
- Tenable.io integrates with DevOps tools and CI/CD pipelines, offering automated vulnerability detection and remediation tracking.
- It is favored by security teams that prioritize compliance and risk reduction across dynamic cloud infrastructures.
- AWS Security Hub is best for AWS-centric organizations needing centralized visibility.
- Microsoft Defender for Cloud excels in hybrid cloud scenarios with deep Azure integration.
- Google SCC is tailored for GCP-native security monitoring.
- Prisma Cloud and Trend Micro Cloud One provide all-in-one solutions for DevSecOps teams.
- Cloud Computing environments, CloudGuard is ideal for businesses focused on network and firewall protections
- CrowdStrike Falcon works well for real-time endpoint and workload protection.
- Tenable.io focuses on compliance and vulnerability management.
- Orca Security suits organizations seeking agentless, fast-deployment security.
- Lacework is optimal for teams needing automation, anomaly detection, and rich visualizations.
Tool 9: Orca Security
Orca Security provides agentless, context-aware security for AWS, Azure, and GCP environments. It scans cloud workloads, In the context of Protecting Sensitive Data , Orca scans workloads, configurations, and identities using a side-scanning technology that eliminates the need for installing agents. It offers comprehensive risk prioritization, malware detection, and real-time visibility across cloud environments. and sensitive data discovery. Its visual attack path mapping allows organizations to understand potential exploit routes and strengthen cloud security posture
Want to Pursue a Cloud Computng Master’s Degree? Enroll For Cloud Computing Master Program Course Today!
Tool 10: Lacework
Lacework is a security and compliance platform designed for cloud-native environments. It automates anomaly detection, behavioral analytics, and compliance tracking for containers, Kubernetes clusters, and multi-cloud infrastructures. Lacework employs polygraph technology to detect unexpected changes, file modifications, and risky behaviors. It excels in visualizing threat surfaces and reducing false positives, making it suitable for DevSecOps teams aiming to maintain security at scale.
Comparison and Use Case Scenarios
Ultimately, the choice depends on factors like existing cloud platforms, team expertise, compliance needs, Google cloud protection, integration capabilities, and budget constraints. Combining multiple cloud security tools often provides layered defense, creating a more secure and resilient cloud infrastructure.

