
- Introduction to Social Engineering Attacks
- What is Spoofing?
- What is Phishing?
- Key Differences Explained
- Techniques Used in Spoofing
- Techniques Used in Phishing
- Examples and Case Studies
- Impact on Individuals and Organizations
- Detection and Prevention
- Legal Implications
- Response Strategies
- Summary
Introduction to Social Engineering Attacks
Social engineering attacks are manipulative tactics that exploit human psychology to gain unauthorized access to systems or information. Unlike technical hacking, In Cyber Security Training, learners are taught that while traditional attacks rely on exploiting system vulnerabilities, social engineering targets human weaknesses such as trust, curiosity, fear, and urgency. Spoofing and phishing are two of the most common and effective social engineering techniques used by cybercriminals to deceive individuals and compromise sensitive data. These attacks have been on the rise due to their high success rates and the increasing digital footprint of individuals and organizations.
Interested in Obtaining Your Cybercrime Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
What is Spoofing?
Spoofing is a type of cyberattack in which a malicious actor impersonates another person, device, or system to deceive victims and gain access to sensitive data, systems, or networks. Spoofing can occur in various forms, As covered in any comprehensive Guide to Web Security , spoofing can take many forms including email spoofing, IP spoofing, DNS spoofing, caller ID spoofing, and website spoofing each posing unique risks to users and systems.Get smarter responses, upload files and images, and more. The attacker falsifies information to appear trustworthy, tricking users or systems into taking actions they wouldn’t normally take if the true identity were known. The ultimate goal of spoofing is often to steal data, spread malware, or perform unauthorized actions under the guise of a trusted source.
What is Phishing?
Phishing is a fraudulent attempt to obtain sensitive information such as usernames, passwords, credit card details, cybersecurity and other personal data by pretending to be a trustworthy entity. It typically occurs through email, instant messaging, websites, or phone calls. Phishing messages are designed to look authentic and usually create a sense of urgency to prompt immediate action, such as clicking a malicious link or downloading a harmful attachment. Phishing is one of the most widespread cyber threats and serves as a gateway to more serious attacks like identity theft and financial fraud.,
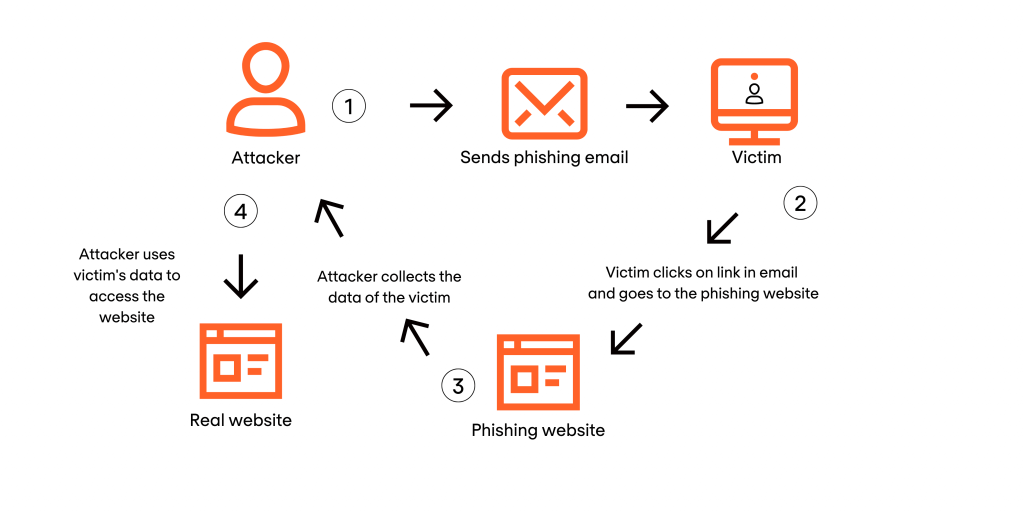
Key Differences Explained
- Intent: Spoofing is generally used to impersonate a trusted entity, while phishing aims to trick users into revealing confidential information.
- Method: Spoofing manipulates technical attributes (email headers, IP addresses, DNS records), whereas phishing focuses on psychological manipulation and social engineering.
- Medium: Spoofing can happen through emails, IP addresses, websites, or phone numbers; phishing primarily uses emails, websites, and texts.
- Outcome: In Cyber Security Training , it’s explained that spoofing may be a precursor to phishing, while phishing often leads to direct data theft or unauthorized access.
- Complexity: Spoofing usually requires more technical expertise, whereas phishing can be executed using basic tools and templates.
- Email Spoofing: Altering the sender’s address to make it look like the message comes from a trusted source.
- IP Spoofing: Changing the IP addresses header to disguise the origin of network packets, often used in denial-of-service attacks.
- DNS Spoofing: The Guide to Web Security highlights how corrupting DNS records can redirect users to malicious websites, a tactic that poses significant risks not only to traditional networks but also to Encryption and Decryption , where security breaches can have physical consequences.
- Caller ID Spoofing: Making a phone call appear as though it is coming from a legitimate number.
- Website Spoofing: Creating fake websites that closely mimic real ones to deceive users.
- MAC Spoofing: Changing a device’s MAC address to impersonate another device on the network.
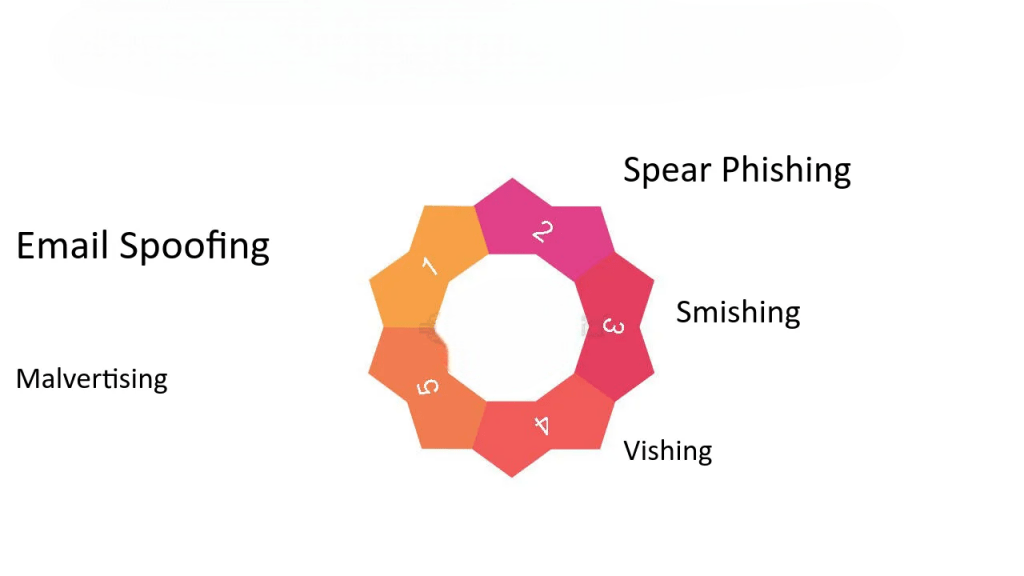
- Email Phishing: The most common form, involving fraudulent emails that prompt users to click malicious links or open attachments.
- Spear Phishing: Targeted phishing attacks directed at specific individuals or organizations, often using personalized information.
- Whaling: Phishing attacks aimed at high-profile targets like executives or decision-makers pose serious risks, making Non-Repudiation in Cyber Securityessential to ensure that actions and communications cannot be denied or falsified.
- Smishing: Phishing attempts conducted through SMS or text messages.
- Vishing: Voice phishing attacks conducted via phone calls.
- Clone Phishing: Using a legitimate email message that has been altered with malicious content.
- Individuals: Victims of spoofing and phishing may suffer financial loss, identity theft, and reputational damage. Recovery can be difficult and time-consuming, often involving legal, financial, and emotional stress.
- Organizations: Businesses face severe consequences including data breaches, regulatory penalties, financial losses, and damaged trust. Cyber Security Books often highlight that phishing is frequently the entry point for advanced persistent threats (APTs) and ransomware attacks, making it a critical concern for cybersecurity teams.The overall impact extends to loss of customer confidence, disruption of services, and significant recovery costs.
- Monitoring unusual email activity and source IP addresses.
- DNS monitoring and filtering.
- Use of anomaly detection systems.
- Employee reporting and phishing simulations. Prevention Techniques:
- Implement SPF, DKIM, and DMARC to protect against email spoofing.
- Use multi-factor authentication (MFA) to reduce account compromise risk.
- Regularly update antivirus and anti-malware tools.
- Conduct employee training on identifying phishing attempts.
- Use secure web gateways and endpoint protection solutions.
- Contain the Threat: Disconnect affected systems from the network to prevent further spread.
- Notify Stakeholders: Inform internal teams and external partners as necessary.
- Conduct a Forensic Investigation: Identify the source and impact of the attack.
- Report the Incident: Notify regulatory bodies and, if necessary, law enforcement.
- Remediate Systems: Remove malware, reset credentials, and update security protocols.
- Review and Improve: Conduct a post-incident review to strengthen security measures.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Techniques Used in Spoofing
Techniques Used in Spoofing comes in several forms, each using a specific tactic to achieve deception:
Techniques Used in Phishing
Phishing attacks also come in various forms, each tailored to exploit specific vulnerabilities:
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Examples and Case Studies
Spoofing Example: In a notable case, attackers spoofed a major bank’s website by using a nearly identical URL and appearance. Users who clicked the link in a fake email were led to this fraudulent site, cybersecurity where they unknowingly entered their login credentials. The attackers used these details to access and drain accounts.
Phishing Example: One high-profile phishing incident involved a fake email sent to a corporate HR department. The email appeared to come from the In a common social engineering scenario, an attacker impersonated the CEO and requested the W-2 tax information of all employees. Trusting the sender, the HR team complied, leading to a massive data breach and identity theft. Understanding Jailbreaking in Cyber Security can help professionals recognize how attackers exploit device vulnerabilities to facilitate such breaches. These examples demonstrate how convincing spoofing and phishing attacks can be, and the significant consequences they can have when successful.
Impact on Individuals and Organizations
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Detection and Prevention
- Detection Techniques:
Legal Implications
Spoofing and phishing are illegal in most jurisdictions and can lead to criminal charges, fines, and imprisonment. Regulations Regulations like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) mandate organizations to implement robust Vulnerability Management practices to safeguard personal data and report breaches promptly. Failure to comply can result in significant legal and financial consequences.Law enforcement agencies such as the FBI, Interpol, Social Engineering Attacks, Techniques Used in Spoofing and local cybercrime units investigate and prosecute cybercriminals involved in these activities. Reporting such attacks not only aids in legal action but also helps in refining global cybersecurity measures.
Response Strategies
In the event of a spoofing or phishing attack, a quick and coordinated response is essential:
Summary
Spoofing and phishing are dangerous and prevalent forms of social engineering attacks that exploit both technical and psychological vulnerabilities. In Cyber Security Training, it’s emphasized that spoofing focuses on impersonation, while phishing targets the victim’s response through deception. Understanding their methods, analyzing IP addresses, and recognizing the warning signs are critical skills for identifying and preventing these attacks. and implementing robust detection and prevention strategies are critical for individuals and organizations alike. As technology evolves, so do these threats, making continuous vigilance, education, and improvement key components of a resilient cybersecurity posture.




