
- Introduction
- What is cyber security?
- What are cyber security tools?
- Why are cyber security tools important?
- Key Types of Cyber Security Tools
- Top 6 Cyber Security Tools
- The Future of Cyber Security Tools
- Benefits of Cyber Security Tools
- Conclusion
Introduction
Cyber threats are rapidly increasing in frequency and sophistication in today’s digital world. Organizations are becoming increasingly vulnerable to sensitive data compromise, operational disruption, and reputational damage, from large-scale data breaches to targeted attacks through Cybersecurity Training Courses. Because of the increasingly increasing onslaught of cyberattacks, protecting sensitive data and critical systems has become necessary and not a choice by any corporate organization. The main point of cybercriminals is to be proactive, as fraudsters are always inventing ways to get around security measures. Implementing strong cloud network security that will potentially help defeat and minimize the impact of these threats is the first step in dealing with the shifting tides. Thus, raising a strong security posture that protects all things about devices, networks, and data from exploitation, destruction, and unwanted access forms the aim.
Enroll in ACTE’S Cyber Security Online Training if you want to become an expert in cyber security field and have a prosperous career.
What is cyber security?
- Network Security Monitoring Tools: Administrators will have a proactive shot at detecting potential problems and ensuring excellent cloud network security performance with the help of network monitoring tools. It provides each item that is linked with an in-depth view. System managers, thanks to them, can monitor data flow to rapidly solve any problem that is likely to impair network performance or lead to an outage.
- Web Vulnerability Scanning Tools: Tools called vulnerability scanners are mostly used to identify weaknesses in an organization’s information technology infrastructure. Usually, most organizations use several scanners so that the complete threat can be analyzed.
- Network Defence Wireless Tools: The defense solutions of Wireless Antenna Types can enhance security much more than data protection, network integrity, and usability preservation. Hardware and software solutions are implemented together to regulate network access.
- Encryption Tools: Encryption protects the data by converting text into a format that unauthorized users cannot read. VeraCrypt, NordLocker, AxCrypt, TrueCrypt, Tor, and KeePass are a few instances of encryption software.
- Firewalls: Firewalls – they are forms of network security that monitor and manage incoming and outgoing data traffic. Using pre-set rules at their limits, they evaluate data traffic passing through and determine which of that data might be allowed to pass through.
- Packet Sniffers: Intercepting, recording, and analyzing data and network traffic is the purpose of a packet sniffer. Other names for this device are network analyzer, protocol analyzer, and packet analyzer. Examples include tools such as Windump, tcpdump, and Wireshark.
- Antivirus Software: The known attack profiles use antivirus software to find harmful apps on your system. With its help, you can identify and eliminate unwanted materials and consequently defend yourself against many of the most dangerous cyber threats.
- Managed Detection and Response Services: Vendor-managed third-party products, known as Managed Detection and Response (MDR), enable organizations to monitor, contain, and eradicate threats. They provide incident response and continuous security monitoring to deliver strong defense against cyber attacks.
- Penetration Testing: The cybersecurity technique known as penetration testing sometimes referred to as ethical hacking or a pen test mimics a Watering Hole Attack on a system. Finding weaknesses in the system and estimating the likelihood of a breach are the goals of this technique. It also aids cybersecurity experts in determining which system components are the most reliable and do not require urgent enhancement.
- Public Key Infrastructure (PKI) Services: PKI services help enable secure online communication by making it easy to distribute and identify public encryption keys as well as confirming the identity of the sender. It also enables encryption so that only those who are given permission can access sensitive data.
- Kali Linux: Kali Linux is one of the most popular and accessible cybersecurity products in circulation. Its capabilities are monitored by over 300 of its technologies to keep an eye out for vulnerability points within its network infrastructure. This is one of its biggest advantages, as it can be pretty flexible to accommodate different levels of experience among specialists. Compatibility for many devices and Sandbox Environment, open-source integration, remarkable usefulness in security auditing with a focus on penetration testing, and continued enhancements from a large user base are notable features.
- TrueCrypt: Although the application has been inoperable for a while, it is still one of the most commonly used encryption programs. TrueCrypt was specifically designed for ‘on the fly’ encryption, meaning it is strong and able to wholly encrypt a storage device. This solution also allows security experts to use two types of access control, each different, to encrypt layered content.
- Cain and Abel: It is one of the greatest password recovery tools out there. Despite being created and developed to function on a Microsoft Windows system, it can support password recovery techniques for other systems. It can recover passwords by sniffing the local network for passwords shared with other devices via SMTP, HTTP/HTTPS, POP3, and other protocols. To recover the password, it can also make use of a variety of techniques, such as brute force and network packet sniffing.
- Malwarebytes : Malwarebytes is one of the leading cyber security solutions that protect against malware, ransomware, malicious websites, and many more online threats. It detects and blocks threats that an antivirus cannot do. It is also a multi-functional network security ttoolthat can easily resolve issues quickly through troubleshooting and fixing. It is one of the most reliable and effective ways to handle cyber security while potentially safeguarding the systems at multiple levels.
- Forcepoint : These are cloud users, and this tool targets them primarily. According to Forcepoint, network security is simply a means of identifying and stopping Hacking in Cybersecurity attempts as well as preventing users from accessing unwanted content. This leads to the primary advantage of using this tool: several technologies have been integrated under one platform. This minimizes user friction while letting the IT security team examine, classify, monitor, and protect the data. This is the only customizable cybersecurity tool. These adjustments help in thwarting attempted cyberattacks.
- Wireshark : It is a free, open-source cyber security software that was earlier referred to as Ethereal. It analyzes network traffic in real-time by gathering data packets from a network connection. It is commonly used for detecting and diagnosing network security issues and ranks among the best analysis network security tools for evaluating network protocols. It is available for network administrators to troubleshoot any problems that may occur. Wireshark scans through the network for real-time vulnerabilities and estimations of possible holes. Such a tool assures easy lookup of security flaws in the network.
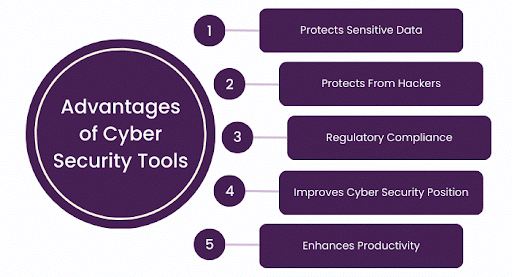
- IT Security Tools encrypt data, which provides another layer of protection against cyber-attacks; substantial damage is prevented from the data leak to the public or competitors.
- These network security tools add security because it is hard for hackers and cybercriminals to get access to systems and files.
- IT security tools ensure companies obey all regulations and laws, such as GDPR, to avoid severe penalties and maintain a good company image.
- These tools enhance overall cybersecurity, as they provide comprehensive digital protection, quick response to threats, and tracking activities to prepare for cyber-attacks.
- By protecting against cyber-attacks and reducing downtime, IT security tools help ensure that workflows and operations keep running, meaning better performance and attaining of goals.
Cybersecurity is defined as protecting computer systems, networks, and data from digital attacks by using a variety of technologies, procedures, and policies to mitigate cyber threats like malware, phishing scams, and ransomware attacks. The basic objective of cybersecurity practice is the protection of sensitive data on connected devices and services from malevolent actors.
What are cyber security tools?
Cyber security tools are software programs, hardware, or systems set up for specific use to protect the organization’s networks, devices, IT infrastructure, and sensitive data against several types of cyber attacks. These tools are inevitable in the fight against Cybercriminals since they prevent breaches, cyberattacks, and unauthorized access, all of which can inflict significant operational, financial, and reputational damage. With the complexity and sheer volume of the cyber threats that are targeting individuals, governments, and corporations, never has there been a greater urgent need for these tools. The core objective of cybersecurity products is to improve information security through the prevention of unauthorized access, modification, and/or destruction of sensitive data. Cloud network security provides the necessary measures required to prevent, identify, and settle possible security issues before they can cause any damage.
Why are cyber security tools important?
This is because cyber threats evolve rapidly, from ransomware and APTs to phishing attacks, and thus organizations have to resort to the appropriate cyber tools to be ahead of the rogue actors. These are the defenses needed to safeguard information, maintain business continuity, and mitigate the threats posed by hostile actors. Organizations must have multi-layered approaches to network security because fraudsters are continually refining their tactics. With the proper tool combination, a business can develop a comprehensive strategy that combats threats from within and outside its firm.
Key Types of Cyber Security Tools
Cybersecurity Training Courses are required to protect digital assets and ensure integrity in cloud network security systems. Organizations use the said tools to spot, halt, and address different cyber threats. With very advanced penetration testing frameworks to antivirus software, one single tool serves a unique purpose in the cybersecurity world. So, let’s peek at some important categories of cybersecurity instruments:
To become a certified cyber security, have a look at our Cyber Security Online Training right now.
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Today!
Top 6 Cyber Security Tools
Cybersecurity tools help identify vulnerabilities, prevent intrusions, and ensure compliance with security standards. The following ten are those that any enterprise should consider using in their arsenal:
The Future of Cyber Security Tools
As technology develops exponentially, so do the security tools designed to safeguard it. Threats are growing in complexity and volume, which motivates one to rethink every perceived traditional method. Traditional methods are no longer efficient. Cybersecurity tools should evolve and develop new systems to better combat such emerging challenges. Using technologies such as artificial intelligence, machine learning, and automation, the future of network security tools is destined to be smarter and more proactive against all forms of Overview of Cybersecurity Threats. With increasing scales and sophistication, the future of cybersecurity tools will define a marriage of innovation, automation, and integration. Tomorrow’s tools will no longer just be “smarter and more responsive,” but they also will be able to work in collaboration for the delivery of proactive, real-time defense across all layers of an organization’s digital environment.
Benefits of Cyber Security Tools
In the last few years, the field of cyber security has become of immense importance for companies. It will create robust IT systems for an organization and prevent cybercrimes against them by securing the data. Cybersecurity is imperative for companies now, as it saves considerable resources and helps to strengthen their position in the market. In consideration of the fact that Ethical Hackers and cybercriminals have advanced their ways to commit cyber attacks, a strong cybersecurity system is very essential for the companies. Some of the advantages of cyber security tools are as follows.
Preparing for a job Interview? Check out our blog on Cybersecurity Interview Questions and Answers !
Conclusion
Cybersecurity Training is the new warfare that has invaded the world, and cybersecurity tools are essential in the battle against cyber threats that target businesses, organizations, and individuals more and more. Computer security is so diverse that essential tools such as firewalls, antivirus software, and penetration testing provide the outline of great defense strategies. Tools like firewalls offer a basic blockade against unauthorized access, while antivirus software helps in looking out for malicious software that may bring down the systems. Penetration testing increases security even more by mimicking attacks, which reveal possible sources of entry for cybercriminals. The remaining tools, with a much lower search volume, play an equally crucial role in further developing the overall cybersecurity frameworks. These tools, in their capacities, complement and work hand-in-hand to secure networks and systems while ensuring that there is no stealing of sensitive data of all kinds. Increased dependence on these solutions underscores their significance in mitigating risks from cyber threats.





