
- What Is Meterpreter for Ethical Hackers?
- Meterpreter Reverse TCP: What is it?
- How Is Meterpreter Operational?
- Meterpreter’s Operational
- How Do You Classify the Meterpreter Server?
- Various Meterpreter Commands
- Practical Uses for Meterpreter
- Conclusion
Meterpreter is a powerful payload for the Metasploit Framework, meaning it is developed and widely used in penetration testing tools and ethical hacking. It runs in memory, thereby leaving minimal traces on a targeted computer, thus allowing it to fly low under the radar of security software, making it a potent threat in the realm of Cyber Media . Once a system has been compromised, Meterpreter provides a full suite of post-exploitation tools file system access, network sniffing, and privilege escalation. Its architecture is extensible, hence enabling users to add custom scripts and plugins to tailor the functionality of Meterpreter according to the requirements of their specific test.
Interested in Obtaining Your Ethical Hacker Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
What Is Meterpreter for Ethical Hackers?
Within the Metasploit Framework, Meterpreter is a potent and sophisticated payload that is intended for use by ethical hackers in Cyber Security Training Courses assessments and network penetration testing. This sophisticated malware minimizes detection by computer security because it runs in memory, enabling it to carry out orders on hacked systems. Meterpreter provides a comprehensive post-exploitation suite of features for hackers, such as privilege escalation, file system access, and network sniffing, allowing for a thorough assessment of system vulnerabilities.
Meterpreter Reverse TCP: What is it?
One particular mode or configuration of Meterpreter, a potent tool for researching and managing hacked computer systems in ethical hacking, is called Meterpreter Reverse TCP. Reverse TCP, to put it simply, is a method by which Meterpreter can covertly and stealthily create a connection between the compromised system (the “victim”) and the attacker’s workstation (the “listener”). In the context of Cyber Defamation, this method can be used to gain unauthorized access to sensitive information, manipulate digital content, or launch attacks designed to damage reputations online while staying undetected.
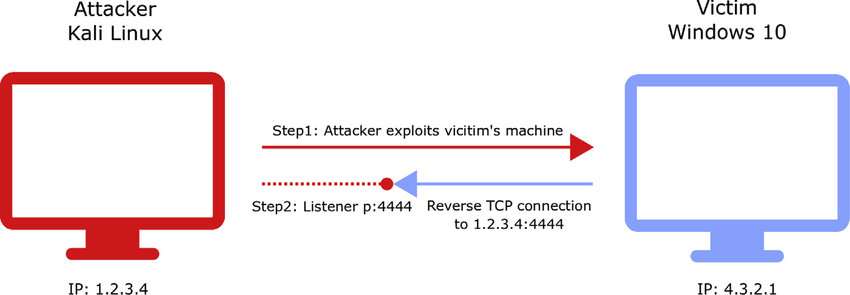
- Meterpreter:The renowned Metasploit Framework contains the Meterpreter post-exploitation framework. It offers an interactive shell environment via which skilled hackers can take command of a hacked system and carry out several tasks.
- Reverse Connection:In conventional hacking situations, the attacker connects to the victim’s computer in order to take control. In contrast, the victim’s computer establishes the connection with the attacker’s computer in the case of Reverse TCP. The attacker can get over some network security measures that may be in place with the help of this reverse connection, which makes it harder to find them.
- TCP:Transmission Control Protocol, or TCP for short, is a set of guidelines that control data flow across a computer network between devices.The hacked machine and the attacker’s computer establish a TCP connection through the use of Reverse_TCP by Meterpreter, enabling the exchange of data and commands.
- Stealth and Covert Operation:Reverse TCP is intended to function in a covert and stealthy manner. The infected system can make the connection and appear as regular network traffic, which makes it more difficult for security systems to identify any unusual activity.
- Remote Control: Meterpreter has the ability to let hackers access to and control over a compromised system from their own computer through its remote control features. For the targeted computer, Cyber Security Training Courses functions similarly to a virtual remote control.
- Information Gathering About the hacked System: Meterpreter gives hackers access to important details about the hacked system, including its architecture, current processes, network configurations, and operating system specifics. This data aids in deciphering the system and identifying any possible weaknesses.
- Privilege Escalation: Hackers can try to increase their level of access on the compromised system by using Meterpreter. This implies that they can attempt to obtain more power and access, which might enable them to carry out more complex tasks.
- Network Exploration: Meterpreter offers capabilities to search and find other systems and devices connected to the network, making it easier to explore the network. This aids in the mapping of the network infrastructure and the identification of possible targets for additional investigation by hackers.
- Sysinfo: Shows comprehensive system information about the compromised system, such as the hardware specifications, operating system, and network setup.
- shell:On the hacked system, this opens an interactive command shell that lets the hacker run commands as if they were being typed directly into the command prompt
- download:Enables the hacker to transfer files to their own computer from the hacked system.
- upload: Permits the hacker to transfer files to the hacked system from their computer.
- ls: Displays a list of the files and directories in the compromised system’s current directory. Techniques like Google Dorking can be used to find vulnerable systems or exposed files by leveraging advanced search queries on Google.
- migrate:Enables the hacker to move the Meterpreter session to a different compromised system process, aiding in persistence and avoiding discovery.
- screenshot:Takes a picture of the desktop of the compromised system, giving you a visual representation of its current status.
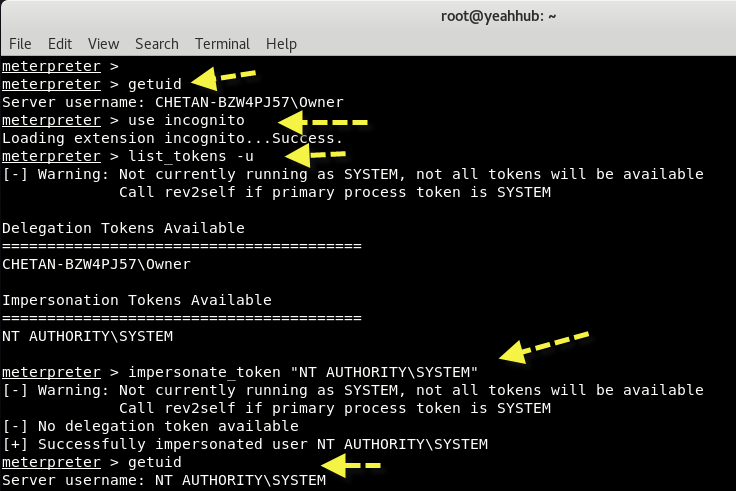
- getuid:Retrieves the infected system’s current user’s ID and privileges.
- hashdump:Retrieves password hashes from the hacked system so that they may be cracked or subjected to additional examination.
- portfwd:Configures port forwarding, allowing the hacker to divert network traffic to their own computer from the hacked system.
- Penetration testing:To evaluate the security of their computer systems, businesses and organizations frequently employ hackers to carry out penetration testing. In order to find vulnerabilities, exploit them, and take control of the systems in order to assess how resilient they are to external attacks, Meterpreter is frequently used in penetration testing.
- Vulnerability Assessment: Security experts can conduct vulnerability evaluations with the help of Meterpreter. Through the use of Payloads, attackers can deliver the necessary code that enables them to interact with the system, escalate privileges, and gather crucial information.
- Incident Response: Meterpreter can be used by cybersecurity teams to look into affected systems in the case of a security incident or breach. They can obtain remote access, gather forensic evidence, examine the attack vector, and determine the scope of the breach thanks to it.
- Malware Analysis: To examine and evaluate malware samples, security experts utilize Meterpreter. They can see how the malicious code behaves, learn about its capabilities, and gather important data for additional investigation and removal by running it in a controlled environment.
- Evaluation of Network Security: Meterpreter helps in evaluating the infrastructure security. From the hacked system, hackers can move to other networked devices and find possible weaknesses, misconfigurations, or lax access constraints.
To Explore Ethical Hacking in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
How Is Meterpreter Operational?
Exploitation
In order to use Meterpreter, an ethical hacker must first identify a gap or flaw in the system they are targeting. This can be an issue with the pentest software, an incorrect setup, or another security hole.
Payload
Tools like the Google Hacking Database are often used to find potential vulnerabilities that can be exploited to deliver such payloads.
Communication
Between the victim’s compromised system and the hacker’s PC, the Meterpreter creates a secret communication channel (the attacker). To safeguard the information shared between the two, encrypted methods are frequently used for this kind of communication.
Command and Control
The hacker now has access to a potent command and control interface since the communication link has been established. It is comparable to controlling the compromised system from a distance.
Post-Exploitation
Depending on their objectives and permissions, the hacker can take a variety of activities once they have taken over the compromised system.
Persistence
Meterpreter gives hackers the ability to maintain access even if the original vulnerability they used to gain access to the system is fixed or rectified.Their tenacity guarantees that they can carry on with their evaluation and experimentation without being quickly discovered or losing control of the system.
Meterpreter’s characteristics
How Do You Classify the Meterpreter Server?
Depending on how the payload is sent to and processed by the target system, there are two types of Meterpreters: staged and non-staged. It is noteworthy that once properly delivered and deployed on the compromised system, both staged and non-staged Meterpreter servers offer the same fundamental functionality and features. The manner of distribution and assembly serves as the main basis for categorization. In the context of Cyber Awareness, understanding how malware is distributed and assembled is crucial for identifying potential threats and preventing attacks. The Meterpreter server is sent to the compromised machine in stages when it is given in this type. Sending a little initial payload to the target, which serves as a loader, is how it operates. Ethical hackers server is sent to the compromised system as a single, comprehensive package under the non-staged category. There is no need for any further steps or independent parts to be sent. Although this method makes delivery easier, cyber security systems could be able to identify it more readily.
Are You Considering Pursuing a Cybersecurity Master’s Degree? Enroll For Cyber Security Expert Masters Program Training Course Today!
Various Meterpreter Commands
Practical Uses for Meterpreter
Are You Preparing for Cyber Security Jobs? Check Out ACTE’s Cyber Security Interview Questions and Answers to Boost Your Preparation!
Conclusion
To sum up, Meterpreter provides a strong and adaptable framework for post-exploitation duties, making it a vital tool for penetration testers and Cyber Security Training Courses experts. Ethical hackers love it because of its many features, including file modification, network exploration, and privilege escalation, as well as its ability to function covertly in memory. In order to fortify defenses and improve overall security, Meterpreter is essential since it makes thorough examinations of system vulnerabilities easier. But because of its potential for abuse, it’s even more crucial for cybersecurity professionals to follow moral standards and use technology responsibly.





