
- Introduction
- What is a Dictionary Attack?
- How Does a Dictionary Attack Work?
- Mechanism of a Dictionary Attack
- Types of Dictionary Attacks
- Impact of a Dictionary Attack
- How to Protect Against Dictionary Attacks
- Best Practices for Creating Strong Passwords
- Conclusion
A dictionary attack is a method used in password cracking, where an attacker attempts to gain unauthorized access to a system by systematically trying a prearranged list of common words, phrases, and variations from a “dictionary.” This attack relies on the assumption that many users choose simple or easily guessable passwords. Cyber Security Training Courses emphasize the importance of strong, unique passwords and teach techniques to mitigate such attacks, helping users secure their accounts and data effectively. The mechanism involves using automated tools that rapidly test each word in the dictionary as a possible password. The impact of a dictionary attack can be significant, especially when users employ weak passwords, as it can quickly compromise accounts and systems, potentially leading to data breaches, identity theft, and unauthorized access to sensitive information.
To Earn Your Dictionary Attack Certification, Gain Insights From Leading Cyber Security Experts And Advance Your Career With ACTE’s Cyber Security Online Training Today!
Introduction
Password security is one of the most crucial aspects of safeguarding online accounts, personal data, and other sensitive information and authentication process in today’s world of digital interaction. Despite increased sophistication in the field of cybersecurity, most people have been using low-quality passwords vulnerable to cracking by cyber attackers. Dictionary attacks are among the most common attacks used by attackers to penetrate accounts. This type of attack targets simple, common, or predictable passwords. Key Skills Required for Cybersecurity Professionals include understanding these attack methods and knowing how to implement strong password management practices to protect accounts from unauthorized access. Such an attack becomes an effective and efficient method to gain unauthorized access. In this blog, we shall explore what is a dictionary attack how it works, what impact it would have, and how you could protect yourself against such an attack while ensuring your system security from the malicious threats. Beyond dictionary attacks, attackers are also known to use techniques such as brute-force attacks and phishing, which often complement dictionary attacks for greater success. Cybercriminals continuously adapt their strategies, exploiting weak points in passwords and authentication processes. This is why it is so essential to adopt a holistic approach to security. In this blog, we shall explore what a dictionary attack is, how it works, what impact it could have on your personal and organizational security, and how you can protect yourself against such an attack while ensuring your system security is fortified against malicious threats.
What is a Dictionary Attack?
A dictionary attack is one type of Cyberattack wherein an attacker uses lists and often used words, phrases, and passwords to guess the password that a victim may most likely use for the target account or system. The logic behind this type of attack relies on the fact that many users create passwords that are rather simple, predictable, or related to common words.This compromises system security as attackers exploit weak passwords to gain unauthorized access.
The list of passwords that will be used in a dictionary attack is typically composed of words that are found in dictionaries or word lists, which include combinations of simple phrases, numbers, and special characters. The Cyberattackis automated by the attacker’s system trying each word in the list as a password in hopes of finding the correct match.
How Does a Dictionary Attack Work?
A dictionary attack involves the following general steps by the attacker: The first step typically includes preparing a list of potential passwords often consisting of common words phrases names & variations. This list might also include modified versions of words with numbers or symbols or even personal data like birthdays or addresses that are likely to be used as passwords. Exploring the CIA Triad in Cybersecurity helps professionals understand the importance of confidentiality, integrity, and availability in safeguarding sensitive information, including preventing password-related vulnerabilities. After the attacker has their dictionary ready the next step is selecting a target which could be an account service or system that has a password based authentication process:
- Create or Obtain a Word List: The attacker will input the word list into an attack tool that uses specialized software or tools. The tool automatically tries to log in to the target system with each word on the list as a password.
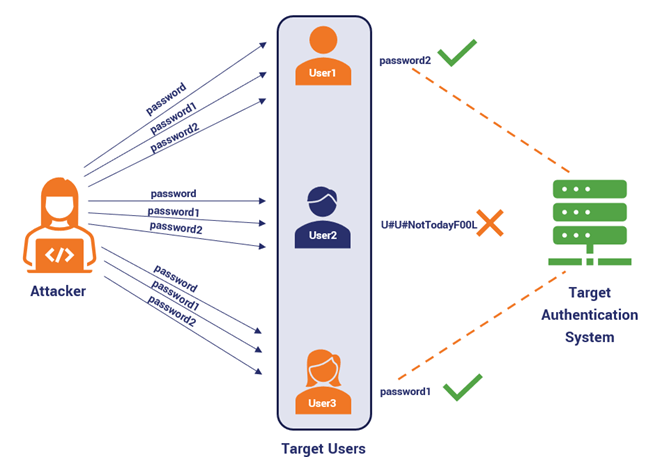
- Automate the Process: The attacker will input the word list into an attack tool that uses specialized software or tools. The tool automatically tries to log in to the target system with each word on the list as a password.
- Test Each Word: The tool will test each word on the list as a possible password for the target account or system. It will then try different combinations if necessary (e.g., adding numbers or special characters).
- Simple Dictionary Attack: In a simple dictionary attack, the attacker uses a basic list of common words, usually taken from an actual dictionary.This list may also include popular names, simple phrases, and predictable variations, such as “password123.” Simple dictionary attacks are quick and often effective when targeting weak passwords. Cyber Security Training Courses teach students how to defend against these attacks by implementing strong password policies and using additional layers of security like multi-factor authentication.
- Hybrid Dictionary Attack: A hybrid dictionary attack extends the simple dictionary attack by introducing variations to words in the dictionary list. This includes adding numbers and symbols, as well as case changes, such as “password1” and “P@ssw0rd”. Hybrid dictionary attacks are successful because they include consideration of passwords with common words combined with predictable modifications.
- Password Compromise: If an attacker correctly guesses a password using dictionary attacks, they could log in and get unauthorized access to the account they are trying to hack into. This access can be to email, social media accounts, financial, or other important personal data. Hackers may engage in malicious activity in the target’s account, such as identity theft, fraud, or even data theft.
- Security Vulnerabilities: The success of a dictionary attack often points to security vulnerabilities in the target system, such as weak password policies or inadequate account lockout measures. A system that allows unlimited attempts at passwords or fails to enforce complexity requirements is more vulnerable to attacks like dictionary attacks.
- Data Theft If the attackers gain access to sensitive information such as personal data, financial details, or private business information, then the consequences would be catastrophic. Data theft leads to financial loss, reputational damage, and legal consequences for the individual and organization.
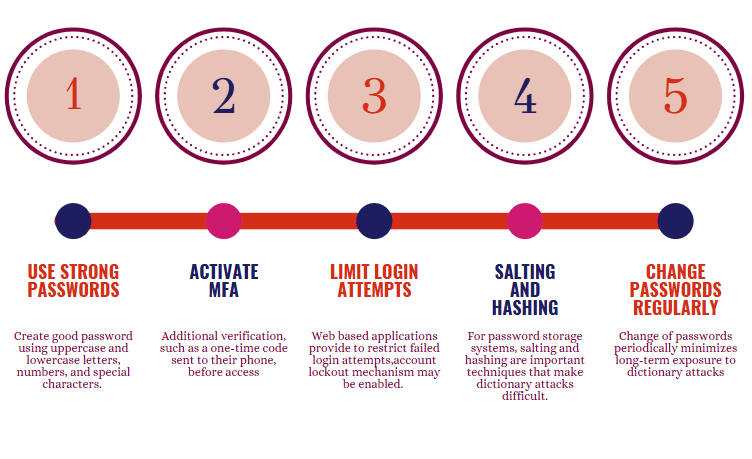
- Use Strong Passwords : A strong password is the first defense against a dictionary attack. Create a good password using uppercase and lowercase letters, numbers, and special characters. Do not use simple words or short phrases that can easily appear in a dictionary list.
- Activate MFA: Even if an attacker guesses your password, multi-factor authentication (MFA) adds a layer of System security. MFA requires users to provide additional verification, such as a one-time code sent to their phone, before access is granted, making it much harder for attackers to break in.
- Limit Login Attempts: Many web-based applications provide a way to restrict failed login attempts. An account lockout mechanism may be enabled, or CAPTCHA can be enabled after some specific number of incorrect attempts so that dictionary attacks of an automated nature will fail. These measures are part of a broader Endpoint Security strategy, ensuring that individual devices are protected from unauthorized access and potential threats.
- Salting and Hashing: For password storage systems, salting and hashing are two important techniques that make dictionary attacks difficult. Salting adds a random value to Strong Passwords before they are hashed, so even if two users have the same password, each password will be unique. Hashing converts passwords into unreadable strings of characters, making it difficult for attackers to reverse-engineer the password.
- Change Passwords Regularly: The change of passwords periodically minimizes long-term exposure to dictionary attacks. Always use unique passwords for every account and you may also need a password manager to store and generate complex passwords.
- Use a password manager: A password manager will help you to generate and store complex passwords securely.
- Mix Characters: Use a combination of uppercase and lowercase letters, numbers, and symbols.
- Make It Long: The longer the password, the more secure it is. Try to have at least 12-16 characters.
- Avoid Personal Information: Avoid using easily guessable information such as birthdays, names, or addresses.
Are You Interested in Learning More About Dictionary Attack? Sign Up For Our Cyber Security Online Training Today!
Mechanism of a Dictionary Attack
Dictionary attacks rely on the fact that most users use weak, common, or easily guessed passwords that are included in a dictionary or an online database. The mechanism of a dictionary attack is very simple yet efficient .Dictionary attacks mainly focus on weak passwords. Common words include “password,” “123456,” “qwerty,” and “let me in.”.Unlike brute-force attacks that attempt every possible combination of characters, the dictionary attack is significantly faster since it tests only for words found in the word list. This makes it efficient to guess simple passwords.Attackers use automated tools like Hydra, John the Ripper, or Hashcat to speed up the attack process. These tools can input thousands or even millions of password combinations in a short time, increasing the likelihood of success.
Types of Dictionary Attacks
There are several variations of dictionary attacks, each with slightly different approaches:
Impact of a Dictionary Attack
A dictionary attack can have a serious impact, especially when the targeted password is weak or commonly used. Penetration Testing helps identify such vulnerabilities by simulating attacks, allowing organizations to address weak password practices and strengthen their overall security posture. Some of the key impacts of a successful dictionary attack include the following:
Gain Your Master’s Certification in Cybersecurity by Enrolling in Our Cyber Security Expert Masters Program Training Course.
How to Protect Against Dictionary Attacks
The good news is that there are many things you can do to prevent dictionary attacks against you and otherwise make your online accounts much more secure. Here are some best practices:
Best Practices for Creating Strong Passwords
Do not use dictionary words, phrases, or predictable patterns such as “123456” or “password”. These weak passwords make it easier for attackers to gain access, especially during a What is a Phishing Attack, where malicious actors trick users into revealing sensitive information like login credentials.
Go Through These Cyber Security Interview Questions and Answers to Excel in Your Upcoming Interview.
Conclusion
A dictionary attack is a highly effective method for cracking weak passwords, particularly those that consist of common words or predictable patterns. The impact of a successful dictionary attack can range from password compromise to data theft and security vulnerabilities. However, by using strong, complex passwords, enabling multi-factor authentication, and following best practices for password security, you can significantly reduce the risk of falling victim and protect your system security to such an attack. Cyber Security Training Courses is an ongoing effort, and taking proactive steps to secure your accounts and data is crucial in today’s increasingly digital world. Stay vigilant and ensure your Strong passwords are as secure as possible to protect your personal and professional information from malicious threats,especially when the target uses commonly found words or phrases. These tools work by automating the process, saving time and effort for the attacker while maximizing the number of potential password guesses they can test per second. Additionally, dictionary attacks are often more effective when the password list includes variations such as common names, sports terms, and even popular culture references.





