
- Introduction
- What is Penetration Testing?
- Types of Penetration Testing
- Steps in the Penetration Testing Process
- Importance of Penetration Testing
- Tools Used in Penetration Testing
- Challenges in Penetration Testing
- Penetration Testing vs. Vulnerability Assessment
- Choosing the Right Service
- Conclusion
Penetration testing, or ethical hacking, is a cybersecurity practice that simulates real-world attacks to identify vulnerabilities in systems, networks, and applications. It includes various types such as black-box, white-box, and gray-box testing. The process involves planning, reconnaissance, scanning, exploitation, reporting, and remediation.Penetration testing is crucial for strengthening security, ensuring compliance, and preventing breaches. Additionally, Cyber Security Training Courses are essential in equipping individuals with the skills and knowledge necessary to understand the risks and effectively support penetration testing efforts. Popular tools like Metasploit, Nmap, and Burp Suite aid in testing, though challenges like evading detection and staying updated with evolving threats exist. Unlike vulnerability assessments, penetration testing actively exploits weaknesses. Choosing the right service depends on organizational needs, security goals, and compliance requirements.
To Earn Your Penetration Testing Certification, Gain Insights From Leading Cyber Security Experts And Advance Your Career With ACTE’s Cyber Security Online Training Today!
Introduction
Penetration testing (also known as ethical hacking) is a crucial practice used by organizations to assess the security of their systems, networks, and applications. This proactive approach allows companies to identify potential vulnerabilities before malicious actors exploit them. As cyber threats continue to evolve and grow in sophistication, penetration testing becomes essential in maintaining a robust security posture and safeguarding sensitive data. Additionally, Cyber Security and Ethical Hacking play a key role in equipping professionals with the necessary skills to identify vulnerabilities and defend against emerging threats. In this article, we will explore what penetration testing is, its types, processes, tools, and the reasons why it is important for businesses of all sizes.
What is Penetration Testing?
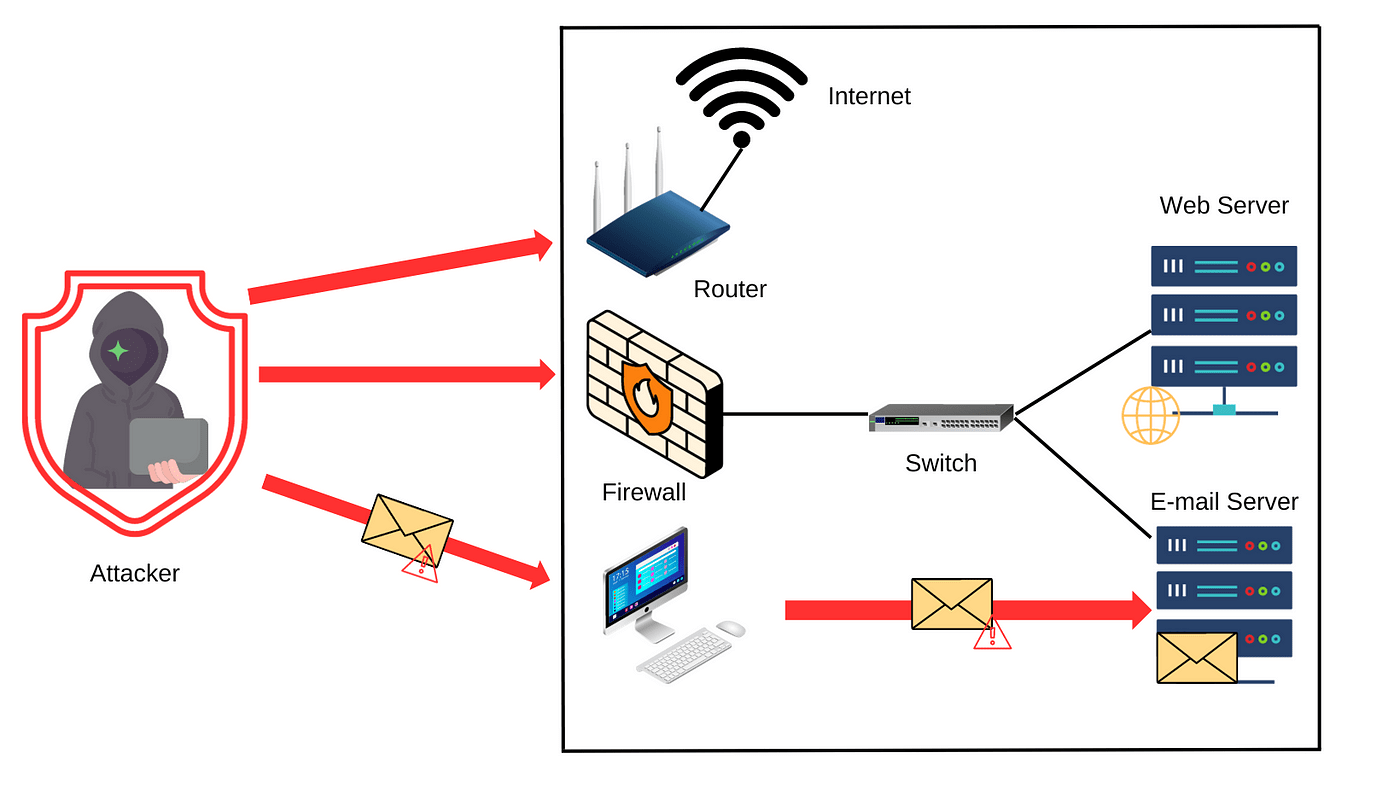
Penetration testing is a simulated cyberattack performed by ethical hackers to evaluate the security of an organization’s IT infrastructure. The purpose is to discover weaknesses that real attackers could exploit. Unlike vulnerability assessments that merely identify vulnerabilities, penetration testing goes a step further by exploiting these weaknesses to understand how a system or network can be breached. Penetration testers, or ethical hackers, use the same tactics, techniques, and procedures as malicious hackers but do so with the organization’s permission. The outcome is a detailed report outlining security flaws, the methods used to exploit them, and recommendations for fixing them.
Types of Penetration Testing
Penetration testing comes in several types, each with its specific focus:- External Testing: External testing focuses on assets visible on the Internet, such as web applications, firewalls, and external networks. The goal is to simulate an attack by a hacker who has external access to the organization’s systems and is attempting to breach its defenses remotely.
- Internal Testing: Internal testing simulates an insider threat, where the attacker has access to the internal network. This approach is often used in conjunction with testing the Demilitarized Zone to evaluate the security of systems that are exposed to external networks while maintaining a separation from the internal infrastructure. This type of test is vital for understanding how an attacker could exploit internal vulnerabilities to escalate their access and potentially exfiltrate data.
- Web Application Testing: Web application testing is specifically targeted at web-based applications, such as websites and mobile apps. Penetration testers focus on common vulnerabilities like SQL injection, cross-site scripting (XSS), and authentication flaws that could compromise the application’s security.
- Wireless Network Testing: Wireless network testing is performed to assess the security of an organization’s Wi-Fi networks. Penetration testers will attempt to gain unauthorized access to the network, exploiting weaknesses like poor encryption, weak passwords, or unsecured access points.
- Social Engineering Testing: Social engineering testing involves manipulating employees to gain unauthorized access to sensitive information. This can include phishing attacks, pretexting, baiting, or tailgating. Social engineering tests help identify vulnerabilities in human behavior that might lead to a breach.
- Planning and Reconnaissance: This initial phase involves gathering information about the target systems. This can be done through passive means, such as researching the target organization online, or active means, such as network scanning. The goal is to identify potential attack vectors.
- Scanning: In this phase, penetration testers identify and map out vulnerabilities in the system using automated tools and manual techniques. This includes network scans, port scans, and vulnerability scans to detect weaknesses, as well as assessing the strength of encryption protocols like the RSA Algorithm to ensure data protection.
- Gaining Access: Once vulnerabilities are identified, the tester attempts to exploit them to gain unauthorized access to the system. Techniques like SQL injection, buffer overflow attacks, or exploiting weak passwords may be used during this phase.
- Maintaining Access: After gaining access, the tester maintains a foothold within the system to simulate how an attacker could persist in the environment. This phase helps assess the potential impact of a security breach.
- Analysis and Reporting: The final phase involves documenting all the findings, including how the attack was conducted, what vulnerabilities were exploited, and the impact on the system. The penetration tester will also provide recommendations for improving security to close the identified gaps.
- Nmap: A network scanning tool used for network discovery and security auditing.
- Metasploit: A framework for developing and executing exploit code against a target.
- Wireshark: A network protocol analyzer that helps capture and inspect network traffic.
- Burp Suite: A set of tools for web application security testing.
- John the Ripper: A password-cracking tool used to assess password strength.
- Nessus: A vulnerability scanner that helps identify weaknesses in systems and applications.
- Vulnerability Assessment: This involves scanning a system for known vulnerabilities and providing a list of those vulnerabilities. It is more of an automated, broad assessment that identifies potential weaknesses.
- Penetration Testing: Goes beyond identification and attempts to exploit vulnerabilities to gain unauthorized access, simulating a real-world attack. Penetration testing provides more actionable insights, as it shows how a vulnerability could be exploited.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
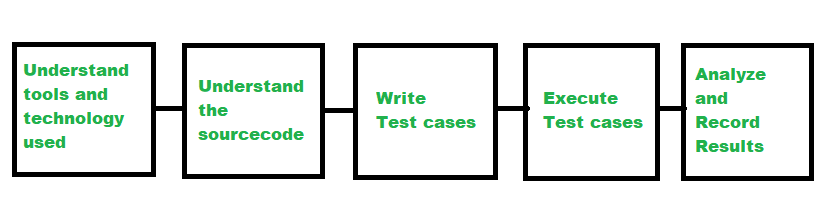
Steps in the Penetration Testing Process
Penetration testing follows a structured methodology, which can vary slightly depending on the testing framework used. However, most tests follow these general steps
Importance of Penetration Testing
Penetration testing is critical for several reasons Identifying Vulnerabilities The primary purpose of penetration testing is to uncover vulnerabilities in systems, networks, and applications. Identifying these weaknesses helps organizations patch them before malicious hackers can exploit them. Cyber Security Training Courses further empower employees to recognize potential vulnerabilities and implement proactive measures to prevent such exploits. Enhancing Security Posture Regular penetration testing improves an organization’s overall security posture. By identifying and addressing vulnerabilities, businesses can proactively strengthen their defenses and minimize the risk of a cyberattack. Ensuring Compliance Many industries are subject to regulatory requirements that mandate security measures.
Penetration testing helps organizations meet compliance standards, such as those set by GDPR, HIPAA, PCI-DSS, and others, ensuring they avoid penalties for non-compliance. Protecting Reputation Data breaches and cyberattacks can severely damage a company’s reputation. Regular penetration testing reduces the likelihood of successful attacks, thus helping businesses maintain customer trust and protect their brand image. Cost Savings By identifying vulnerabilities early, organizations can avoid the high costs associated with data breaches, fines, legal fees, and loss of customer trust. Prevention through penetration testing is a much more cost-effective approach than dealing with the aftermath of a breach.
Gain Your Master’s Certification in Cybersecurity by Enrolling in Our Cyber Security Expert Masters Program Training Course.
Tools Used in Penetration Testing
Penetration testers utilize various tools to perform their assessments.
Challenges in Penetration Testing
Penetration testing, while invaluable, does come with some challenges Complexity of Systems As systems and networks become more complex, it can be difficult to identify all potential vulnerabilities. Organizations with large, diverse IT infrastructures may require extensive testing, which can be time-consuming and resource-intensive. Time and Resource Constraints: Penetration tests can take time, especially for large organizations. Additionally, testing for vulnerabilities related to Distributed Distributed Denial of Service Attacks may require significant resources to simulate high-traffic scenarios and ensure the system’s resilience under stress. Testers need adequate time to plan, scan, exploit vulnerabilities, and report findings, which can be a challenge for organizations with tight budgets and schedules. Scope of Testing Determining the scope of a penetration test is critical. The test must focus on the areas most vital to the organization. Still, it can be difficult to define the right scope without comprehensive risk assessments and discussions between testers and stakeholders.
Penetration Testing vs. Vulnerability Assessment
While both penetration testing and vulnerability assessments aim to identify system weaknesses, they differ in scope and depth.
Choosing the Right Service
When selecting a penetration testing service, it’s essential to consider the following factors Expertise Ensure the service provider has experience and a proven track record in penetration testing. Customization Look for a provider that can tailor the test to your specific needs and environment, including assessing vulnerabilities related to Cryptojacking to ensure your systems are protected against unauthorized cryptocurrency mining activities. Reputation Choose a provider with positive reviews and recommendations from other organizations in your industry. Tools and Techniques Ensure the service uses advanced tools and techniques to conduct thorough tests. Reporting and Follow-Up Choose a provider that offers comprehensive reporting and follow-up support to help you address identified vulnerabilities.
Preparing for a Cyber Security Job Interview? Check Out Our Blog on Cyber Security Interview Questions and Answers
Conclusion
Penetration testing is a vital component of an organization’s cybersecurity strategy. By simulating real-world attacks, businesses can uncover vulnerabilities, assess the effectiveness of their security measures, and improve their overall security posture. The importance of penetration testing cannot be overstated, as it helps safeguard sensitive data, meet compliance requirements, and protect an organization’s reputation. Additionally, Cyber Security Training Courses play a crucial role in equipping employees with the knowledge and skills needed to understand and implement security measures, further enhancing the effectiveness of penetration testing. With cyber threats becoming more sophisticated, regular penetration testing is a necessary investment for businesses seeking to stay one step ahead of malicious hackers.





