
- Introduction to VAPT (Vulnerability Assessment and Penetration Testing)
- VAPT Methodologies and Phases
- Types of VAPT (Black Box, White Box, Grey Box)
- Tools Used in VAPT (e.g., Nessus, Burp Suite)
- Common Vulnerabilities Identified Through VAPT
- Best Practices and Reporting in VAPT
- Conclusion
VAPT (Vulnerability Assessment and Penetration Testing) is a security testing process that identifies and mitigates vulnerabilities in systems, networks, and applications. It follows a structured methodology, including reconnaissance, scanning, exploitation, and reporting in Cybersecurity Training Courses . VAPT can be performed using Black Box, White Box, or Grey Box approaches. Common tools like Nessus, Burp Suite, and Metasploit help detect security flaws. Best practices include thorough documentation, risk assessment, and detailed reporting to enhance cybersecurity.
To become a certified cyber security, have a look at our Cyber Security Online Training right now.
Introduction to VAPT (Vulnerability Assessment and Penetration Testing)
Vulnerability Assessment and Penetration Testing (VAPT) is a security process designed to identify, evaluate, and exploit vulnerabilities in an organization’s IT infrastructure, systems, and applications. VAPT aims to discover security weaknesses, assess their potential impact, and provide solutions for mitigating risks. By combining the techniques of both Vulnerability Management assessment and penetration testing, VAPT helps organizations strengthen their defenses and ensure that they are well-prepared to protect sensitive data and resources from cyber threats. The process can be a crucial part of an organization’s overall security strategy. While a vulnerability assessment is more focused on identifying known vulnerabilities and weaknesses, penetration testing takes this a step further by attempting to exploit these vulnerabilities, simulating real-world cyberattacks. Together, they offer a comprehensive understanding of an organization’s security posture.
Although vulnerability assessment and penetration testing are often used together, they serve different purposes and follow distinct approaches.
Vulnerability Assessment:
- Purpose: The main goal of a vulnerability assessment is to identify potential security risks and vulnerabilities within an organization’s systems or network.
- Scope: It is typically broader, scanning a range of systems for known vulnerabilities.
- Methodology: Vulnerability assessments use automated tools to detect weaknesses such as outdated Firewall And Antivirus Software versions, missing patches, or misconfigurations.
- Outcome: The output is generally a list of vulnerabilities with associated risk levels. No attempt is made to exploit these vulnerabilities during the assessment.
- Frequency: It is usually performed regularly (e.g., weekly or monthly) to ensure that any emerging vulnerabilities are detected and addressed.
Penetration Testing:
- Purpose: The goal of penetration testing is to exploit identified vulnerabilities to simulate a real-world cyberattack and determine how far an attacker could penetrate an organization’s systems.
- Scope: It is more focused and often targets specific systems, applications, or vulnerabilities that are considered critical.
- Methodology: Penetration testing can be manual or automated and involves attempting to exploit vulnerabilities through techniques such as brute force What is a Phishing Attack , social engineering, or SQL injection.
- Outcome: The result is a detailed report outlining the exploited vulnerabilities, the access gained, and recommendations for mitigation.
- Frequency: Penetration testing is usually performed less frequently than vulnerability assessments, typically on an annual or semi-annual basis, or after significant changes to the infrastructure.
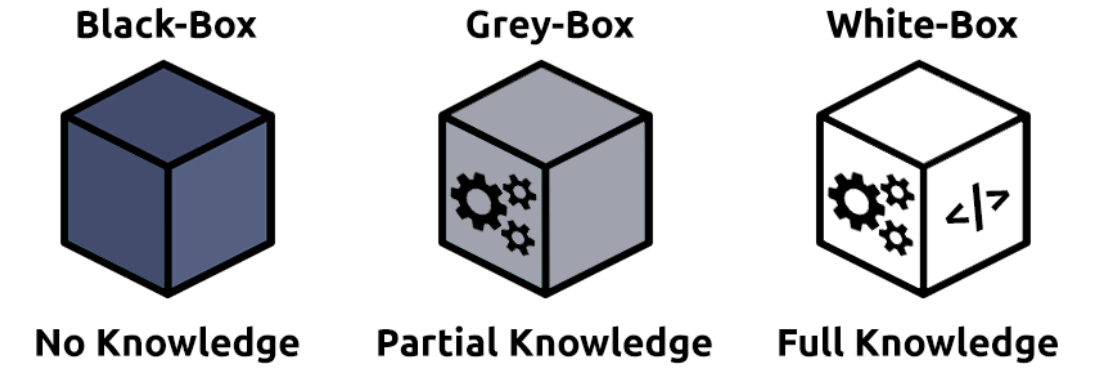
- Description: In black box testing, the tester has no prior knowledge of the system, network, or application being tested. This mimics the approach of an external attacker attempting to break into the system without any inside information.
- Objective:The aim is to identify vulnerabilities from an outsider’s perspective and assess the system’s security defenses without any insight into its architecture or underlying components.
- Challenges: Black box testing can be time-consuming because the tester has to gather information about the system without any internal knowledge.
- Description: White box testing, also known as “clear box” testing, provides the tester with complete access to the internal workings of the system. This includes access to source code, system configurations, and architecture diagrams.
- Objective:The goal is to identify vulnerabilities that could be exploited by insiders or attackers with detailed knowledge of the Intrusion Detection System .
- Challenges: White box testing is more comprehensive than black box testing because the tester can directly analyze the system’s design and code. However, it requires a deep understanding of the application’s internals.
- Description: Grey box testing is a hybrid approach where the tester has partial knowledge of the system. This could include access to system documentation, some internal credentials, or other limited information, but not complete access.
- Objective:The aim is to assess the system’s security from the perspective of an attacker who might have some insider knowledge (e.g., a user with limited access or privileges).
- Challenges: Grey box testing strikes a balance between the depth of white box testing and the external viewpoint of black box testing. It can be particularly useful in identifying both external and internal vulnerabilities.
- Nessus: A widely used vulnerability scanner, Nessus scans systems for known vulnerabilities and misconfigurations. It identifies issues such as missing patches, open ports, and weaknesses in software versions.
- Burp Suite: Burp Suite is an integrated platform for performing web application security testing. It includes tools for scanning web applications, finding vulnerabilities like SQL injection, cross-site scripting (XSS), and session hijacking, and manually exploiting them.
- Metasploit: Metasploit is a penetration testing framework used to identify and exploit vulnerabilities. It provides a collection of exploits, payloads, and tools to test vulnerabilities in networks and systems.
- Wireshark: A network protocol analyzer that helps identify vulnerabilities in Network Security Keystraffic by capturing and analyzing packets. It is useful for detecting vulnerabilities related to insecure communications.
- OpenVAS: OpenVAS (Open Vulnerability Assessment System) is an open-source vulnerability scanner that helps organizations identify weaknesses in their network and systems. It is a comprehensive tool with a large database of known vulnerabilities.
- Clear Scope Definition: Ensure that the scope of the VAPT engagement is clearly defined to avoid unauthorized access or disruption.
- Comprehensive Reporting: Provide a thorough and clear report that outlines the vulnerabilities discovered, their potential impact, and practical recommendations for remediation.
- Risk Prioritization: Classify vulnerabilities based on their severity and potential business impact. Focus on high-risk vulnerabilities that could lead to significant damage.
- Remediation and Follow-up: Ensure that vulnerabilities are addressed promptly and perform follow-up testing to verify that the fixes are effective.
- Continuous Monitoring: VAPT should not be a one-time event. Implement continuous monitoring and regular security assessments to stay ahead of evolving threats.
Sign up for ACTE Cyber Security Online Training and get a head start in your career cyber security.
VAPT Methodologies and Phase
VAPT methodologies are typically carried out in a structured series of phases to ensure a comprehensive and effective testing process. Planning and Scoping This initial phase involves defining the scope and objectives of the VAPT engagement. It is important to understand the systems to be tested, the timeline, and any exclusions or limitations. The assessment method (black box, white box, or grey box) is also determined in this phase. Information Gathering During this phase, testers collect as much information as possible about the target system in Cybersecurity Training Courses . This includes scanning for open ports, identifying running services, gathering publicly available information, and conducting network mapping. Common tools used for information gathering include Nmap, Whois, and Shodan. Vulnerability Assessment Testers perform automated and manual scans to identify known vulnerabilities, such as outdated software, misconfigurations, and unpatched systems. Vulnerability scanning tools like Nessus, OpenVAS, and Qualys are often used to identify weaknesses. Exploitation (Penetration Testing) In this phase, testers attempt to exploit identified vulnerabilities to gain unauthorized access to systems or data. Exploitation may include activities such as gaining remote access, escalating privileges, and attempting to bypass security measures. Tools such as Metasploit, Burp Suite, and Hydra can assist in this phase. Post-Exploitation Once access has been gained, the tester explores the depth of the compromise, examining how far the attacker could penetrate the system. The tester will often attempt to maintain access, move laterally within the network, and extract sensitive information to understand the potential damage. Reporting and Remediation After testing, a detailed report is created that outlines all identified vulnerabilities, the methods used for exploitation, and the potential impact. Recommendations for remediation are provided to help the organization address the identified risks and strengthen its security posture.
Types of VAPT (Black Box, White Box, Grey Box)
VAPT can be classified into three main types based on the level of information provided to the tester before the testing process begins:
Black Box Testing:
Want to Take the Lead in Cyber Security ? EnrollCybersecurity Expert Masters Program Training Course
White Box Testing:
Grey Box Testing:
Preparing for Cyber Security job interviews? Check out our Cyber Security Interview Questions and Answers now
Tools Used in VAPT (e.g., Nessus, Burp Suite)
Best Practices and Reporting in VAPT
Conclusion
In conclusion, Vulnerability Assessment and Penetration Testing (VAPT) is a crucial process for identifying and mitigating security weaknesses within an organization’s infrastructure. By conducting regular VAPT assessments, businesses can stay ahead of potential threats and reduce the risk of data breaches, cyber-attacks, and other malicious activities. VAPT helps organizations understand the vulnerabilities within their systems, applications, and networks, allowing them to take proactive measures to protect sensitive information. The combination of vulnerability scanning and penetration testing provides a comprehensive approach to Cybersecurity Training, offering both automated and manual evaluation. Implementing VAPT as part of an ongoing security strategy ensures a robust defense against evolving cyber threats. Furthermore, VAPT offers valuable insights for compliance with industry regulations and standards, strengthening an organization’s overall security posture. By addressing vulnerabilities promptly, businesses can enhance their reputation, trust with clients, and avoid financial losses due to security incidents. In today’s digital landscape, VAPT is no longer optional but essential for any organization focused on maintaining a secure environment. Adopting VAPT regularly ensures a proactive approach to cybersecurity, minimizing potential risks before they can be exploited. Ultimately, VAPT is a cornerstone of modern cybersecurity practices, helping organizations stay resilient against emerging threats.





