
- Essentials of Network Scanning
- Why Network Scanning is Important
- Types of Network Scanning
- Port Scanning Basics
- Vulnerability Scanning
- Popular Network Scanning Tools (Nmap, Nessus, etc.)
- Features of Network Scanning Tools
- Risks of Improper Scanning
- Legal Considerations
- Best Practices for Network Scanning
- Future Trends in Network Scanning
- Conclusion
Essentials of Network Scanning
Network scanning is one of the most fundamental and essential activities in the domain of cybersecurity and network management. It refers to the process of systematically probing computer networks to identify active devices, open ports, services running, operating systems, and potential vulnerabilities. Security analysts, administrators, and penetration testers use scanning as a first step in Cyber security training to map the network, understand its structure, and identify possible weaknesses that attackers might exploit. At its core, scanning bridges the gap between reconnaissance and exploitation, providing valuable intelligence that can either protect systems or, in the hands of malicious actors, compromise them. Scanning is not inherently malicious network administrators regularly perform scans to ensure their networks are configured securely. However, because the same tools and techniques can also be used by attackers, scanning often sparks debates about ethics and legality. Nonetheless, network scanning remains indispensable for assessing security posture, enabling preventive measures, and preparing defenses against cyberattacks.
To become a certified cyber security, have a look at our Cyber Security Online Training right now.
Why Network Scanning is Important
The importance of network scanning lies in its ability to reveal visibility gaps within IT infrastructures. Organizations today rely on complex networks that span on-premises servers, cloud platforms, IoT devices, and mobile endpoints. Without proper visibility, it is impossible to secure all assets. Scanning provides that visibility by identifying:
- Active hosts: Ensuring only authorized devices are connected to the network.
- Open ports:Highlighting entry points for communication and possible exploitation.
- Services and versions:Allowing administrators to detect outdated or vulnerable software.
- Vulnerabilities:Providing actionable data to patch weaknesses before attackers exploit them.
- Compliance checks (PCI DSS, HIPAA, ISO standards).
- Patch management to prioritize critical updates.
- Risk management to understand overall network exposure.
- Host discovery – Identifying active devices in the network.
- Service enumeration – Determining which applications and versions are running.
- OS fingerprinting – Identifying the operating system of target machines.
- Customizable scanning profiles – Allowing administrators to tailor scans.
- Automation and scheduling – For continuous monitoring.
- Detailed reporting – With charts, severity ratings, and remediation steps.
- Network Disruptions: Aggressive scanning can overload systems, leading to performance issues or downtime.
- Detection by Intrusion Detection Systems (IDS): Scans can trigger alerts, flagging the activity as malicious.
- Unintended Exploitation: Some vulnerability scans may crash poorly configured services.
- Legal Consequences: Scanning systems without permission is often considered illegal and may result in fines or lawsuits.
- Computer Fraud and Abuse Act (CFAA) in the United States.
- IT Act (2000) in India.
- GDPR compliance requirements in Europe.
- AI and Machine Learning Integration: Automating detection of anomalies and predicting vulnerabilities.
- Cloud and Container Scanning: Expanding coverage beyond traditional infrastructure.
- IoT Security Scanning: Protecting billions of connected devices from vulnerabilities, including threats such as What is DoS And DDoS Attack which can overwhelm and disrupt network operations.
- Continuous and Real-time Scanning: Moving from periodic assessments to always-on monitoring.
- Integration with SOAR (Security Orchestration, Automation, and Response) platforms for automated remediation.
In cybersecurity, the principle of “you cannot secure what you cannot see” holds true. New Login to Niche Technologies emphasizes that network scanning gives defenders a complete picture of their environment, ensuring compliance with security standards, preventing breaches, and minimizing the risk of data theft.
Types of Network Scanning
Based on the techniques and goals, network scanning can be divided into many sorts, including ping sweeps, vulnerability scanning, and port scanning. Each kind aids in locating open ports, running services, active devices, and possible network security flaws. Network scanning can be broadly classified into three major types:
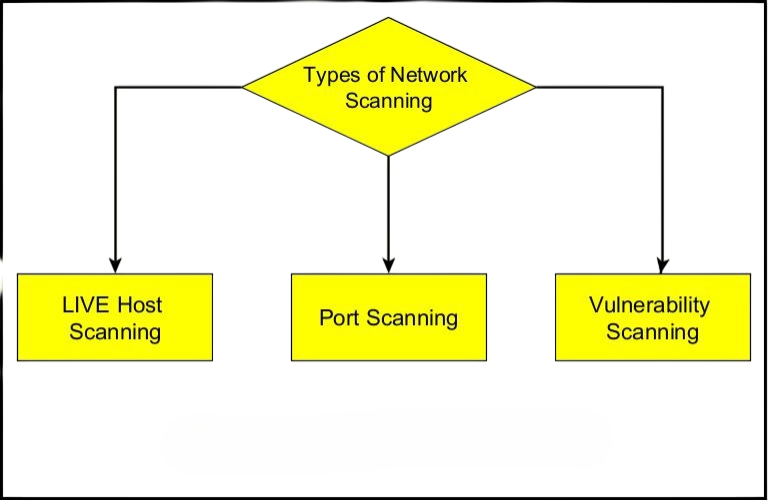
Port Scanning – This technique identifies open or closed ports on a target system. Each port represents a potential communication channel, and What is DOS And DDOS Attack scanning helps determine which ports are active and what services are listening.
Vulnerability Scanning – Vulnerability scanning goes a step further by not just identifying open ports but also checking for known vulnerabilities associated with the services running on those ports.
Network Mapping (Ping Sweeps) – Network mapping involves discovering all active devices on a network. This helps administrators build a topology of the network and understand its architecture.
Each type plays a different role in strengthening network defense, but together they create a comprehensive security assessment.
Port Scanning Basics
The most popular type of network scanning is port scanning; each service (such as HTTP, FTP, or SSH) is given a unique port number, and a port acts as a virtual door that lets data enter and exit a system. An open port means a service is actively listening and can accept connections; a closed port means no service is listening even though the host is reachable; and a filtered port is obscured by firewalls or filters, making it difficult to determine its state. Port scanners probe a variety of ports, Secret Key Cryptography , to ascertain their status. The following are common methods: UDP scans, which check for open UDP ports but are typically slower and less dependable; FIN, Xmas, and Null scans, which try to take advantage of peculiarities in TCP/IP implementations to get around some defences; SYN (half-open) scans, which send SYN packets without finishing the handshake for a stealthier footprint; and TCP Connect scans, which complete a full TCP connection to determine a port’s state. In order to identify, mitigate, and secure exposed services, defenders need to be aware of port scanning techniques because attackers employ the same strategies to find possible entry points.
Vulnerability Scanning
Vulnerability scanning builds on port scanning by identifying misconfigurations, missing patches, or insecure services that might allow exploitation, often using metrics like Receiver Operating Characteristic (ROC) to evaluate detection accuracy. Vulnerability scanners maintain databases of known vulnerabilities (such as CVEs Common Vulnerabilities and Exposures) and compare scanned systems against these databases. For example, if a server runs an outdated version of Apache HTTP Server with a known vulnerability, a vulnerability scan would detect it and provide a risk rating. Organizations use vulnerability scanning for:
While vulnerability scanning is powerful, it is not foolproof. False positives (detecting a vulnerability that doesn’t exist) and false negatives (missing actual vulnerabilities) are common challenges, making human verification important.
Are you curious to know more about Cybersecurity ? Take advantage of our comprehensive online Cyber Security Online Training
Popular Network Scanning Tools
To improve network administration and cybersecurity, a plethora of potent open-source and proprietary network scanning technologies have been created over time. Nmap (Network Mapper), the most popular open-source network scanner, is one of the most used. With the help of its Nmap Scripting Engine (NSE), Nmap can carry out advanced scripting automation, operating system fingerprinting, service version identification, and thorough port scanning. It is an essential tool in Cyber security training for penetration testers and network administrators alike. Nessus, a reputable vulnerability scanner renowned for its vast vulnerability database, is another top tool. Nessus is a vital tool for vulnerability management since it prioritises threats, generates thorough reports, and provides practical repair guidance. An excellent open-source substitute for Nessus is OpenVAS (Open Vulnerability Assessment System), which provides efficient scanning features and frequent vulnerability database updates. Because of how easy and quick it is to find active hosts in a network, Angry IP Scanner is used for lighter, faster scanning activities. The cloud-based vulnerability management tool QualysGuard, on the other hand, combines remediation procedures, compliance evaluations, and scanning into a single, centralised solution. Because of their dependability, adaptability, and broad use, Nmap and Nessus continue to be the industry standards for port and vulnerability scanning, respectively, despite the fact that each of these programmes offers special advantages.
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Today!
Features of Network Scanning Tools
Features including port discovery, service identification, OS fingerprinting, and vulnerability evaluation are available with network scanning software. To assist businesses in proactively safeguarding their networks, they frequently incorporate automation, reporting, and integration features, helping teams Understand Random Forest Algorithm for enhanced threat analysis.
These features empower security teams to manage risks effectively, prioritize resources, and strengthen overall security posture.
Risks of Improper Scanning
While scanning is a critical security function, improper or careless scanning can introduce risks:
For this reason, organizations must establish clear policies, use scanning responsibly, and always gain authorization before scanning the network, while also encouraging teams to Get To Know Deep Learning for advanced security insights.
Legal Considerations
Legal and ethical concerns are among the most critical aspects of network scanning. While scanning one’s own network for security is acceptable, Scanning external networks without consent can be considered a Hacking from Scratch violation of computer security laws such as:
Penetration testers and auditors always obtain written authorization (Rules of Engagement) before performing scans. This ensures transparency and protects both the tester and the organization from legal repercussions.
Preparing for a job interview in cybersecurity ? Examine our blog post about Cybersecurity Interview Questions and Answers to get the most of your employment experience!
Best Practices for Network Scanning
In order to optimise network scanning efficacy and mitigate associated risks, organisations ought to adhere to a set of clearly established best practices. Along with prioritising crucial assets in their scanning protocols, organisations should pay particular attention to systems that store sensitive data or are essential to company operations. Maintaining the accuracy of detection and keeping vulnerability databases up to date require routinely upgrading Cybersecurity Project Ideas scanning technologies. Teams must thoroughly examine and validate scan results when they are finished in order to prevent false positives and make sure that remediation efforts are focused in the right direction. To build a multi-layered defence strategy, network scanning should also be combined with other security measures like firewalls, intrusion detection and prevention systems (IDS/IPS), and endpoint monitoring tools. In order to preserve accountability, monitor advancements, and direct repair efforts, it is imperative that all discoveries be recorded and reported. Organisations may guarantee that network scanning stays a proactive and beneficial instrument for bolstering cybersecurity defences rather than a cause of interruption by following these guidelines.
Future Trends in Network Scanning
As networks evolve, so does the field of scanning. Some emerging trends include:
The future of network scanning lies in greater automation, intelligence, and adaptability to secure increasingly complex digital ecosystems.
Conclusion
Network scanning tools play an indispensable role in both offensive and defensive cybersecurity. They provide the critical visibility needed to secure assets, ensure compliance, and prevent attacks. While tools like Nmap and Nessus have become industry standards, new trends such as AI-driven scanning and cloud-native assessments are shaping the next generation of capabilities. At the same time, Cyber security training ensures that ethical and legal considerations remain front and center, so scanning is conducted responsibly. By adopting best practices, leveraging the right tools, and staying ahead of emerging threats, organizations can use network scanning to transform their cybersecurity posture from reactive to proactive. Regular network scanning also lowers the chance of expensive breaches by assisting organisations in identifying vulnerabilities before they are exploited. A strong and resilient cybersecurity framework for the future is ensured by competent staff, rapid remediation, and ongoing monitoring.





