
- What is Enumeration in Security
- Importance of Enumeration
- Phases of Ethical Hacking
- Types of Enumeration
- Techniques Used in Enumeration
- Tools for Enumeration (Nmap, Netcat, etc.)
- Risks of Enumeration
- Countermeasures Against Enumeration
- Real-world Scenarios
- Role in Penetration Testing
- Legal and Ethical Aspects
- Future of Enumeration Techniques
What is Enumeration in Security
Enumeration is a critical phase in ethical hacking and penetration testing that involves extracting detailed information about a target system, network, or application. It goes beyond simple scanning by actively probing the target to identify valid accounts, services, shares, and other valuable data that could be exploited in later stages of an attack. In simpler terms, enumeration is like the information-gathering step where an attacker tries to turn potential data into useful intelligence. To understand and counter such reconnaissance techniques, explore Cyber Security Training a comprehensive program that equips professionals with the skills to detect, analyze, and mitigate enumeration tactics used in real-world cyber threats. This process typically involves establishing active connections with the target and retrieving system details such as usernames, group memberships, running processes, services, and configurations. While often associated with malicious hackers, enumeration also plays a vital role in defensive security, as ethical hackers and penetration testers use it to uncover weaknesses before adversaries can exploit them.
Importance of Enumeration
The importance of enumeration in cybersecurity cannot be overstated. Without this phase, attackers would be operating blindly, relying only on assumptions or limited reconnaissance data. Enumeration allows hackers to identify the “doors” and “windows” of a system that can be pushed open. For defenders, the same activity highlights misconfigurations, unpatched vulnerabilities, or unnecessary services that may be leaking sensitive data. To strengthen protection at the device level and reduce exposure to such risks, explore Understanding Endpoint Security a comprehensive guide that explains how antivirus tools, EDR solutions, and access controls work together to secure endpoints across enterprise networks. Enumeration is often the step that bridges the gap between reconnaissance and exploitation; once critical data such as usernames, machine names, or open services are revealed, attackers can craft targeted exploits or brute-force attempts. From an organizational standpoint, identifying enumeration risks helps in tightening access controls, hardening services, and reducing the overall attack surface. In short, enumeration is where theory becomes actionable intelligence.
Interested in Obtaining Your Cyber Security Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Phases of Ethical Hacking
- Enumeration falls under the larger umbrella of ethical hacking, which is typically broken down into several key phases: reconnaissance, scanning, enumeration, gaining access, maintaining access, and covering tracks. Reconnaissance, the first step, is passive, focusing on collecting publicly available information about the target. Scanning, the second step, involves probing the network to identify open ports, services, and live hosts.
- Enumeration comes next, transforming the data obtained from scanning into structured and usable intelligence. After enumeration, the attacker proceeds to exploitation, using the gathered information to gain unauthorized access. Maintaining access ensures persistence in the compromised system, while covering tracks removes any evidence of the intrusion. Enumeration, therefore, is the pivotal middle stage, converting raw scanning data into meaningful assets that make exploitation possible.
- Enumeration can be classified into different types depending on the nature of the information being extracted. The most common form is network enumeration, which focuses on gathering details about active machines, services, and network shares. User enumeration is another common type, where the goal is to extract valid usernames or user IDs that can later be used in password attacks.
- Service enumeration involves probing specific protocols such as SNMP, SMTP, or NetBIOS to identify configuration details and weaknesses. To defend containerized environments against such reconnaissance techniques, explore Top Container Security Tools a curated guide to runtime protection, vulnerability scanning, image hardening, and orchestration-aware security platforms built for modern DevOps workflows.
- Application enumeration targets web applications and APIs to identify exposed endpoints or misconfigured settings. Each type has its own significance; for instance, user enumeration can lead to credential-based attacks, while service enumeration may expose outdated software vulnerable to exploits. By categorizing enumeration, security professionals can prioritize defense strategies more effectively.
- Although enumeration is critical in penetration testing, it also comes with significant risks when carried out improperly. For ethical hackers, overly aggressive enumeration can disrupt services, raise alarms, or cause denial-of-service conditions on fragile systems. For organizations, the risks are more severe when adversaries conduct enumeration; they can gather sensitive data such as employee names, login IDs, and internal infrastructure details, making targeted attacks far easier.
- Enumeration can expose critical systems running outdated software, unprotected shares, or default credentials. Since enumeration often relies on active probing, it is more likely to be detected by intrusion detection systems (IDS) compared to passive reconnaissance, but if undetected, the results can be devastating. This highlights the dual-edged nature of enumeration; it is both a powerful defensive tool and a dangerous offensive weapon.
- Organizations must implement robust countermeasures to minimize the risks of enumeration. One of the most effective strategies is to harden services and disable unnecessary ones, thereby reducing the attack surface. Properly configuring protocols such as SNMP, NetBIOS, and LDAP is essential, ensuring that they do not reveal excessive information without authentication. Strong authentication mechanisms, account lockouts, and monitoring of login attempts can mitigate brute-force enumeration attacks.
- Intrusion detection and prevention systems can be tuned to detect unusual probing behavior indicative of enumeration. Additionally, penetration testing and red team exercises allow organizations to proactively identify enumeration weaknesses in their environments. Training administrators and developers to avoid information leakage in error messages or default settings also goes a long way in countering enumeration risks.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Types of Enumeration
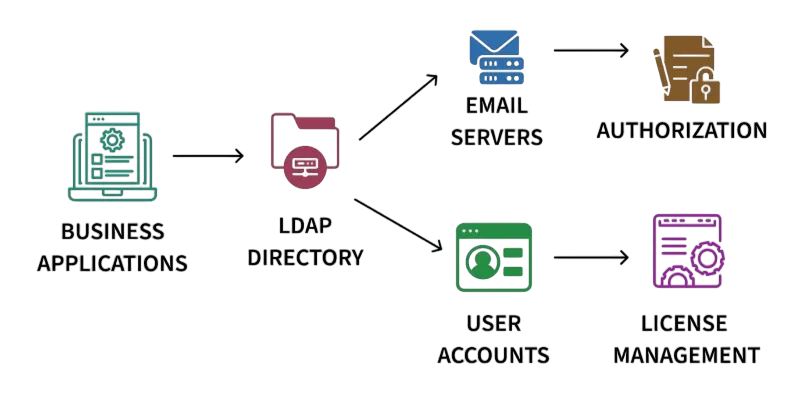
Techniques Used in Enumeration
A variety of techniques are used in enumeration, each tailored to exploit specific weaknesses in network protocols and system configurations. SNMP enumeration involves querying devices that use the Simple Network Management Protocol, often revealing system details, running processes, and network configurations if community strings are misconfigured. NetBIOS enumeration, common in Windows environments, helps in identifying shares, groups, and user accounts. To learn how to detect, mitigate, and ethically simulate such techniques, explore Cyber Security Training a hands-on course that equips professionals with the skills to analyze enumeration methods, secure network protocols, and strengthen system defenses against reconnaissance threats. LDAP enumeration targets directory services to extract usernames and organizational data. SMTP enumeration involves probing mail servers to validate users. Additionally, DNS enumeration helps uncover subdomains, mail records, and other critical domain-related data. Brute-force enumeration is another technique where attackers attempt to guess credentials systematically. These techniques demonstrate how enumeration leverages both misconfigurations and legitimate services to extract sensitive details.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Tools for Enumeration (Nmap, Netcat, etc.)
To carry out enumeration efficiently, security professionals and attackers rely on a wide range of tools. Nmap, one of the most widely used, not only scans networks but also provides service version detection and scriptable interactions for enumeration. Netcat, often called the “Swiss army knife” of networking, is used for banner grabbing and establishing connections that reveal service information. To understand how attackers leverage such tools to guess credentials and gain unauthorized access, explore Explain Brute Force Attacks a tactical guide that breaks down password-guessing techniques, automation tools, and countermeasures used to detect and prevent brute-force intrusions across systems and networks. Enum4linux is a dedicated tool for enumerating Windows systems through SMB and NetBIOS. SNMPWalk is used to extract SNMP data from misconfigured devices. DirBuster and similar tools help in enumerating web applications by brute-forcing hidden directories and files. Metasploit Framework, while primarily an exploitation tool, also provides numerous auxiliary modules for enumeration tasks. Each tool has strengths in specific contexts, and penetration testers often use them in combination to build a comprehensive picture of the target system.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Risks of Enumeration
Countermeasures Against Enumeration
Real-world Scenarios
Real-world attacks often demonstrate the importance of enumeration as a precursor to compromise. For example, in many ransomware incidents, attackers begin by enumerating the network to identify critical file shares and accessible servers, maximizing the impact of encryption. Similarly, in phishing campaigns, attackers often enumerate email servers and valid user accounts to craft convincing spear-phishing emails. In web application breaches, enumeration of directories or API endpoints often reveals hidden administrative panels or test environments that are less secure. To understand how these weaknesses are exploited and how to defend against them, explore Cybersecurity Vulnerabilities a comprehensive guide that covers common attack vectors, risk assessment strategies, and mitigation techniques essential for securing modern digital ecosystems. Even high-profile breaches such as those involving healthcare or financial data have involved extensive enumeration phases, where attackers used basic tools like Nmap to map internal infrastructures before exploiting vulnerabilities. These scenarios show how enumeration is not a theoretical concept but a practical step seen in nearly every real-world attack chain.
Role in Penetration Testing
In penetration testing, enumeration plays a central role, often determining the success or failure of the engagement. A penetration tester relies on enumeration to build a profile of the target system that guides the exploitation phase. For example, discovering a misconfigured SNMP service during enumeration may directly lead to privilege escalation later.
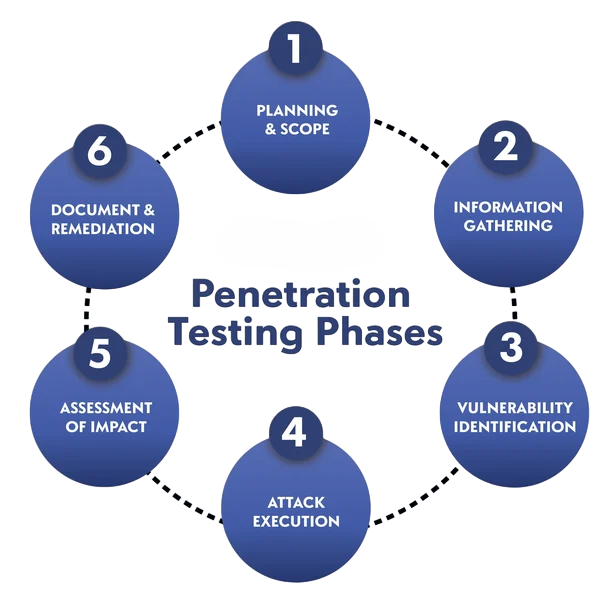
Similarly, enumerating usernames helps in password spraying attacks to gain valid access. Enumeration also allows testers to map trust relationships within networks, identify hidden services, and assess the depth of potential compromise. Since penetration testing is about simulating real-world attacks, enumeration provides the crucial context that mirrors how actual adversaries operate. Comprehensive enumeration, therefore, separates a surface-level test from a meaningful, security-enhancing assessment.
Legal and Ethical Aspects
While enumeration is essential for penetration testing, it comes with legal and ethical considerations. Unauthorized enumeration is illegal, as it involves actively probing systems without permission. Even if no exploitation is attempted, simply enumerating services or users without authorization can constitute a breach of cybersecurity laws such as the Computer Fraud and Abuse Act (CFAA) in the United States. To understand how online harassment intersects with legal boundaries and digital ethics, explore What Is Cyber Trolling a detailed guide that explains the tactics, motivations, and consequences of cyber trolling, along with strategies for prevention and legal recourse. For ethical hackers, obtaining explicit permission through scopes of work and contracts is critical before attempting enumeration. From an ethical standpoint, testers must balance thoroughness with caution, ensuring that their enumeration activities do not disrupt legitimate business operations. In academic and training environments, controlled labs and simulations are used to practice enumeration legally. The fine line between ethical and malicious enumeration underscores the importance of intent, authorization, and professional responsibility.
Future of Enumeration Techniques
As technology evolves, enumeration techniques will continue to advance, adapting to new systems and protocols. With the rise of cloud computing, enumeration is shifting toward cloud services, APIs, and containerized environments, requiring new tools and methods. Attackers are increasingly automating enumeration using artificial intelligence and machine learning to analyze large amounts of data quickly. To stay ahead of these evolving tactics and master cloud-native defense strategies, explore Cyber Security Training an advanced program that prepares professionals to secure cloud infrastructures, detect AI-driven reconnaissance, and implement resilient countermeasures across modern digital ecosystems. Defensive technologies are also evolving, with better anomaly detection and deception systems that can mislead attackers during enumeration. In the future, the focus will likely be on detecting enumeration earlier in the attack chain, preventing adversaries from gathering actionable intelligence in the first place. Ethical hackers will need to stay updated with modern enumeration tools and methodologies to continue providing value. Overall, while the core principles of enumeration will remain the same, its scope and complexity will grow alongside the technological landscape.




