
- Introduction to Bug Bounty Programs
- Purpose and Importance
- How Programs Work
- Rewards and Incentives
- Platforms Offering Bug Bounties (HackerOne, Bugcrowd)
- Responsible Disclosure Guidelines
- Legal Considerations
- Benefits for Companies and Hackers
- Examples of Successful Bounties
- Program Management Best Practices
- Challenges and Criticism
- Conclusion
Introduction to Bug Bounty Programs
Bug bounty programs originated in the late 1990s, with Netscape being among the first companies to publicly offer rewards for bug discovery. These programs have evolved significantly, now being a common practice among tech giants and startups alike. The rise of digital services, ethical hackers, cloud computing, and remote access has increased the attack surface for most companies. Cyber Security Training highlights that this expanded landscape necessitates broader security coverage, which internal teams alone may not fully provide. Bug bounty programs supplement traditional security testing by tapping into the diverse skill sets of external researchers.A Bug Bounty Program is an initiative launched by organizations to incentivize ethical hackers and security researchers to identify and report security Common Vulnerabilities Targeted in their systems. Instead of exploiting these flaws maliciously, participants are rewarded for responsible disclosure. This collaborative approach to cybersecurity helps businesses fortify their digital infrastructure and respond proactively to potential threats. Over time, bug .
Ready to Start Your Cybercrime Certification? View Details Cyber Security Online Training Offered By ACTE Right Now!
Purpose and Importance
The core purpose of a bug bounty program is to improve cybersecurity by identifying and addressing Common Vulnerabilities Targeted before they can be exploited. It creates a structured and legal way for hackers to interact with systems and rewards them for their efforts.
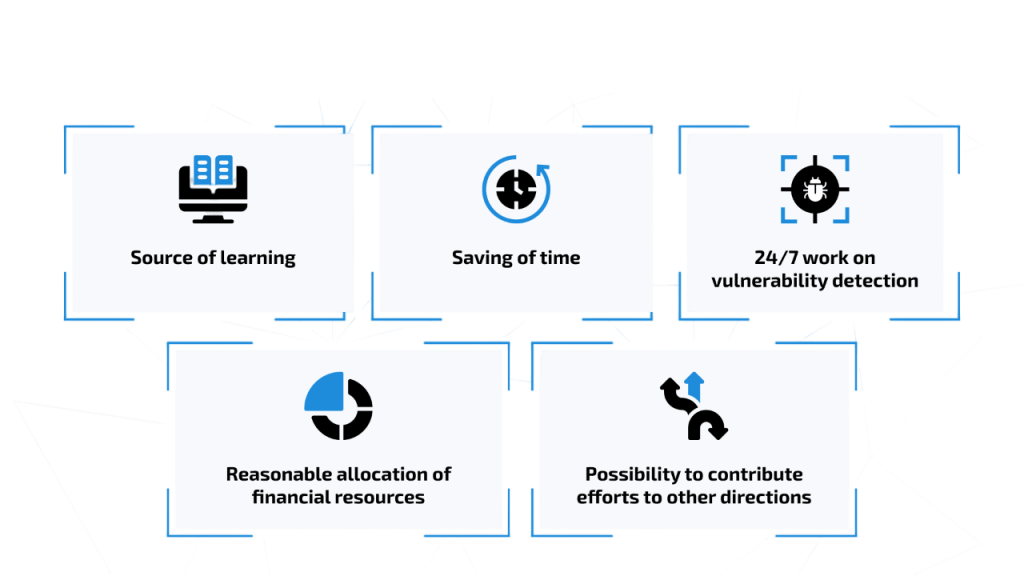
The importance of these programs is highlighted by the rise in cyberattacks, data breaches, and the growing value of digital assets.Cyber Safety emphasizes that by proactively identifying issues, companies reduce the risk of financial loss, reputational damage, and legal penalties. For researchers, it offers a legitimate and often lucrative way to put their skills to use.
How Programs Work
A typical bug bounty program begins with the organization defining its scope identifying which systems, applications, and services are open for testing. The rules of engagement specify what kinds of tests are allowed, how to report vulnerabilities, and the rewards associated with each severity level. Participants can sign up on bug bounty platforms or directly with the company, Benefits for Companies and Hackers, begin testing, and submit detailed reports of any vulnerabilities they discover. After review and validation by the As covered in Cyber Law Explained, a company’s security team issues rewards monetary or otherwise based on the impact and severity of reported vulnerabilities.
Explore Cybersecurity Thoroughly Through Our Complete Resource Cyber Security Online Training To Gain Insights From Our Experts!
Common Vulnerabilities Targeted
Bug bounty programs commonly focus on web applications, APIs, mobile apps, and cloud infrastructure. Some of the vulnerabilities frequently reported include:
- Cross-Site Scripting (XSS): Injecting malicious scripts into trusted websites.
- SQL Injection: Inserting malicious SQL commands to access or alter databases.
- Cross-Site Request Forgery (CSRF): Forcing authenticated users to perform unintended actions.
- Remote Code Execution (RCE): Running unauthorized code on a server or application.
- Broken Authentication: Gaining unauthorized access due to flaws in authentication mechanisms.
- Information Disclosure: Accessing sensitive data not intended for public consumption.
- Privilege Escalation: Gaining higher access levels than permitted.
Rewards and Incentives
Rewards in bug bounty programs vary widely depending on the severity of the bug, the size of the organization, and the nature of the vulnerability. High-severity issues like remote code execution may earn ethical hackers thousands or even tens of thousands of dollars, and insights from these findings often contribute to improving the effectiveness of Top Container Security Tools .Low-risk issues may yield smaller rewards or recognition points. Besides monetary compensation, Benefits for Companies and Hackers many companies offer other incentives such as:
- Public recognition or inclusion in a Hall of Fame
- Swag and company-branded merchandise
- Job offers or internship opportunities
- Invitations to private or elite bug bounty programs
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Platforms Offering Bug Bounties
Several platforms facilitate bug bounty programs by providing the necessary infrastructure, legal framework, and communication tools. Prominent ones include:
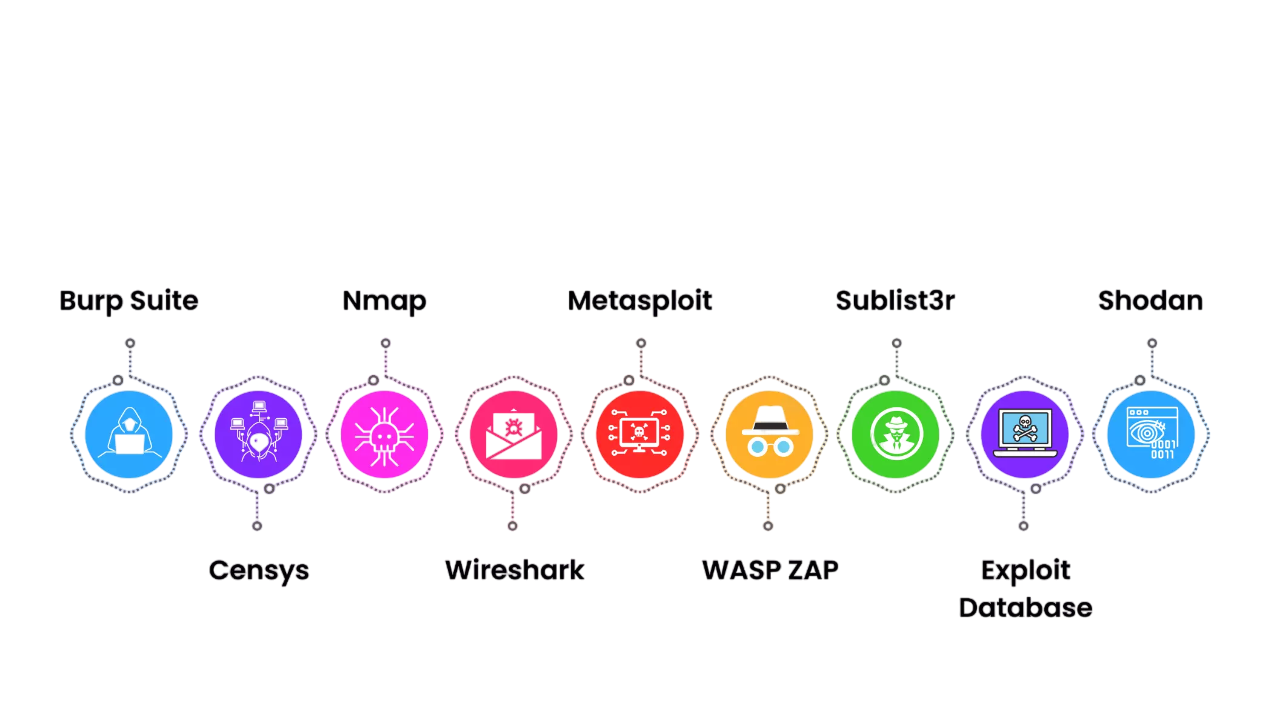
- HackerOne: In Cyber Security Training HackerOne is often highlighted as one of the most well-known platforms, serving clients like Uber, Twitter, and the U.S. Department of Defense.
- Bugcrowd: Offers managed bug bounty programs with flexible engagement models.
- Synack: Uses vetted researchers and provides a hybrid model with traditional pen-testing and crowdsourcing.
- YesWeHack: A European-based platform that supports private and public programs.
- Open Bug Bounty: Allows disclosure of vulnerabilities without requiring prior registration.
Responsible Disclosure Guidelines
Responsible disclosure is the ethical framework within which bug bounty programs operate. Researchers are expected to:
- Report findings exclusively to the organization or platform.
- Avoid accessing, altering, or deleting data during testing.
- Provide detailed documentation of their findings.
- Refrain from exploiting the vulnerability beyond proof-of-concept.
- Respect the rules and scope defined by the program.
Legal Considerations
Legal ambiguity can deter participation in bug bounty programs. To address this, clear terms of service and safe harbor provisions are critical—especially when considering the Definition of a Bot and how automated tools may be used during security testing or malicious activities. These ensure that researchers won’t face legal consequences for ethical behavior within the program scope. Key legal elements include:
- Terms of engagement outlining authorized testing activities
- Confidentiality agreements to protect company data
- Non-disclosure of vulnerabilities until officially patched
- Agreements that limit liability for unintended consequences
Some countries are also enacting legislation to formalize protections for ethical hackers, further legitimizing bug bounty programs.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Benefits for Companies and Hackers
Bug bounty programs offer mutual benefits:
For Companies:- Gain access to a wide range of testing skills and perspectives
- Identify vulnerabilities missed during in-house assessments
- Cost-effective model: pay only for verified findings
- Enhance reputation and security maturity For Hackers:
- Legal and rewarding outlet for technical skills
- Access to real-world systems and applications
- Earn financial rewards and career opportunities
- Contribute to global cybersecurity improvement
Examples of Successful Bounties
Many high-profile Common Vulnerabilities Targeted have been responsibly disclosed through bug bounty programs, and integrating these findings into Security Information and Event Management (SIEM) systems helps organizations detect and respond to threats more effectively. Examples include:
- A 17-year-old hacker earned $30,000 from Google for discovering a critical Gmail bug.
- Apple paid $100,000 for a vulnerability in its Sign in with Apple feature.
- A security researcher reported a Facebook vulnerability allowing account takeover and received $40,000.
- Microsoft awarded $200,000 for a remote code execution bug in Windows 10.
These cases highlight how impactful bug bounty programs can be in enhancing digital security.
Program Management Best Practices
Running a successful bug bounty program requires planning, communication, and resource allocation. Best practices include:
- Clearly Define Scope: Outline what is and isn’t eligible for testing.
- Establish a Severity Rating System: Use industry standards like CVSS to assess risk.
- Maintain Transparent Communication: Keep researchers informed throughout the process.
- Offer Timely Payouts: Prompt reward distribution builds trust.
- Create a Hall of Fame: Acknowledge top contributors publicly.
- Use Automation Tools: Streamline triage and response efforts.
- Collect Feedback: Improve the program based on researcher and stakeholder insights.
Challenges and Criticism
Despite their benefits, bug bounty programs are not without criticism:
- Triage Overload: High submission volumes can overwhelm security teams.
- Duplicate Reports: Multiple researchers may report the same vulnerability, just as multiple attackers might independently target specific individuals in Spear Phishing campaigns
- Low-Quality Submissions: Some reports may lack actionable details.
- Scope Misunderstanding: Ambiguities in scope can lead to unintended legal or ethical issues.
- Researcher Frustration: Delayed payments or lack of recognition can deter participation.
To mitigate these issues, organizations must invest in clear communication, process automation, and dedicated program management.
Conclusion
Bug bounty programs have become an essential component of modern cybersecurity strategies. By incentivizing ethical hackers to uncover vulnerabilities, Cyber Security Training teaches that through platforms like HackerOne, organizations can secure their assets more effectively and cost-efficiently, benefiting both companies and ethical hackers. The success of these programs hinges on mutual trust, transparent processes, and a commitment to continuous improvement. As cyber threats evolve, bug bounty programs will continue to grow in significance, Common Vulnerabilities Targeted bridging the gap between businesses and the global security community.




