
- Definition and Purpose
- Symmetric And Asymmetric Encryption
- Key Generation and Management
- Common Encryption Algorithms
- Encryption Process Explained
- Decryption Mechanism
- Data in Transit vs Data at Rest
- Real-Life Applications
- Legal and Ethical Considerations
- Importance in Cybersecurity
- Encryption Standards (AES, RSA, etc.)
- Challenges and Future Outlook
Definition and Purpose
Encryption and decryption are fundamental processes used to protect sensitive information from unauthorized access. Encryption is the process of converting readable data, known as plaintext, into an unreadable format called ciphertext. This transformation ensures that only those with the correct decryption key can access the original information. Decryption, conversely, is the process of converting ciphertext back into its original plaintext form. Cyber Security Training equips individuals with the skills needed to safeguard sensitive information. These processes are crucial in maintaining data confidentiality, integrity, and security in both personal and enterprise-level communications. The primary purpose of encryption and decryption is to safeguard digital data from cyber threats, unauthorized access, and breaches. Encryption ensures that even if data is intercepted during transmission or accessed without authorization, it remains unintelligible. Decryption restores the encrypted data to its original form for use by authorized parties. These techniques are widely applied in areas such as online banking, e-commerce, email communications, secure messaging apps, and enterprise-level file storage.
Interested in Obtaining Your Cyber Security Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Symmetric And Asymmetric Encryption
Encryption can be broadly categorized into symmetric and asymmetric types: Symmetric and asymmetric encryption are two crucial styles for securing digital dispatches. Symmetric encryption uses one key for both encryption and decryption. This system is effective and fast, with well- known norms like AES and DES. Still, it faces challenges in participating keys, which can affect security. On the other hand, asymmetric encryption uses a more advanced system involving a public-private crucial brace. Data is translated with a public key and deciphered with a corresponding private key. NoSQL is the Ultimate Solution for Database Management continues to gain recognition. This system greatly improves network security, especially when transferring sensitive information over potentially unsafe channels. Important asymmetric encryption ways like RSA and ECC give strong protection by creating a complex fine link between the crucial dyads. This helps reduce the sins of traditional encryption and offers better defense against unauthorized data access. Each method has its advantages and is often used in combination to enhance both performance and security.
Key Generation and Management
The security of encryption relies heavily on the strength and management of cryptographic keys. Types Of SQL Indexes offer a foundational understanding of database optimization. Key generation involves creating a random and unique key using algorithms or secure hardware modules. In symmetric encryption, the same key must be securely shared between parties, whereas in asymmetric encryption, only the public key is shared openly. Key management practices include:
- Secure storage of keys
- Regular key rotation
- Access control
- Backup and recovery procedures
- AES (Advanced Encryption Standard): A symmetric encryption algorithm recognized for its efficiency and security. It supports key sizes of 128, 192, and 256 bits.
- RSA (Rivest-Shamir-Adleman): An asymmetric encryption algorithm that is widely used for secure data transmission.
- Blowfish and Twofish: Symmetric encryption algorithms known for their speed and adaptability.
- ECC (Elliptic Curve Cryptography): Offers similar security to RSA but with shorter key lengths, making it ideal for mobile and embedded devices.
- DES and 3DES: Older symmetric algorithms, now largely replaced by more secure options like AES.
- Data in Transit: Refers to data actively moving from one location to another, such as across the internet or a private network. Secure protocols like HTTPS, SSL/TLS, and VPNs ensure data in transit is encrypted.
- Data at Rest: Refers to data stored on physical or cloud storage devices. Full-disk encryption, file-level encryption, and encrypted databases are commonly used to secure data at rest.
- Online Banking: Protects financial transactions and personal data.
- E-Commerce: Secures payment and customer information.
- Email and Messaging: Prevents unauthorized access to communication.
- Cloud Storage: Ensures data stored remotely is accessible only by authorized users.
- Healthcare: Safeguards electronic health records (EHRs).
- Government and Military: Secures classified and confidential information.
- AES: Adopted by the U.S. government and widely used in public and private sectors.
- RSA: Standard for secure data transmission, especially in digital certificates and public key infrastructures (PKIs).
- TLS/SSL: Protocols that use encryption to secure internet communications.
- PGP (Pretty Good Privacy): Used for securing emails and files.
- IPSec: Encrypts data at the network level for secure VPNs.
- Key Management Complexity: Maintaining and securing encryption keys can be difficult, especially at scale.
- Performance Overhead: Strong encryption can slow down systems, particularly in resource-limited environments.
- Legal Constraints: Some governments limit the use of strong encryption, complicating global deployment.
- Quantum Computing Threats: Quantum computers could potentially break existing encryption algorithms, prompting research into post-quantum cryptography.
Without proper key management, even the strongest encryption algorithms can be rendered ineffective.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Common Encryption Algorithms
Several encryption algorithms are widely used in modern cryptographic applications:
The choice of algorithm depends on the specific use case, performance needs, and security requirements.
Encryption Process Explained
The encryption process typically follows these steps: In cryptographic processes, data encryption follows a clear method to ensure secure communication and protect information. How to Become an SQL Developer is a transformative path in data management. The journey starts with key selection. Here, a suitable cryptographic key is carefully chosen or generated to fit the specific encryption algorithm.
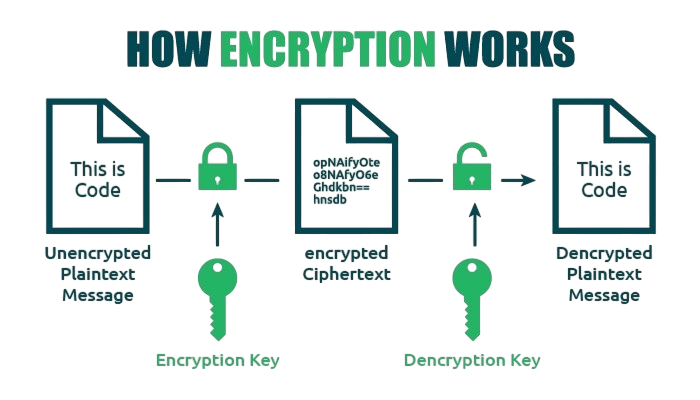
Once the key is set, the plaintext is prepared and formatted, paving the way for algorithmic transformation. In the crucial execution phase, the selected algorithm processes the prepared plaintext with the chosen key, turning the original information into ciphertext. The final step is to securely transmit the encrypted data. This can involve sending it over network channels or storing it in a protected environment, which helps keep sensitive information safe from unauthorized access and potential security threats. This process ensures that data remains protected from unauthorized viewing or tampering during transit or storage.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Decryption Mechanism
Decryption is the inverse process of encryption. It involves: In cryptographic processes, decryption starts with receiving the encrypted ciphertext, which is the first input. Once the system accesses this encoded data, it uses the correct decryption key, Cyber Security Training is an essential part that allows secure information retrieval and equips developers with critical data security knowledge. The decryption algorithm then carefully processes the ciphertext, changing the encrypted information back into its original, readable plaintext form. This mechanism keeps sensitive data safe during transmission while enabling authorized users to accurately restore and understand the underlying message. In symmetric systems, the same key is used for both processes, while in asymmetric systems, the private key is used to decrypt data encrypted with a public key.
Data in Transit vs Data at Rest
Encryption can be applied to two primary states of data:
Protecting both types of data is essential for comprehensive information security.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Real-Life Applications
Encryption and decryption are integral to many real-world applications:
In each case, encryption forms the backbone of data privacy and security.
Legal and Ethical Considerations
Guide to Choosing an Enterprise Data Strategy emphasizes the importance of secure data transmission practices. The use of encryption is often subject to legal regulations and ethical standards. Governments may require organizations to implement strong encryption for data protection, particularly for personal or financial information. Laws such as GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), and CCPA (California Consumer Privacy Act) mandate secure data transmission handling practices, including encryption. However, encryption can also complicate law enforcement efforts when used to hide illegal activities. The balance between privacy and public safety is an ongoing debate, leading to discussions around encryption backdoors and lawful access.
Importance in Cybersecurity
Encryption is a cornerstone of cybersecurity strategies. It prevents data breaches, ensures secure communications, and upholds privacy and trust. Without encryption, sensitive information such as passwords, credit card numbers, and personal communications would be vulnerable to interception and misuse. In a threat landscape characterized by ransomware, phishing, and nation-state attacks, encryption provides a critical line of defense. Organizations also use encryption to comply with industry regulations, avoid hefty fines, and maintain customer confidence. It’s integrated into broader security practices such as secure coding, identity management, and risk assessment.
Encryption Standards (AES, RSA, etc.)
Encryption standards are established protocols that ensure interoperability, security, and performance. Key standards include:
These standards undergo regular reviews and updates to remain effective against evolving threats.
Challenges and Future Outlook
Despite its benefits, encryption faces several challenges:
Looking forward, encryption will continue to evolve with the development of quantum-safe algorithms, homomorphic encryption (which allows computations on encrypted data), and AI-enhanced security systems. As data continues to grow in volume and importance, encryption will remain a foundational element of digital trust and security.
Conclusion
Encryption and decryption are essential processes for safeguarding digital data in today’s connected world. From basic text messages to classified government files, these technologies ensure that information remains confidential, authentic, and secure. Whether through symmetric or asymmetric methods, and whether applied to data in transit or at rest, encryption provides a robust defense against unauthorized access. Cyber Security Training highlights the importance of encryption and decryption as foundational elements of secure communication. As cybersecurity threats continue to evolve, so too will the technologies and strategies behind encryption, ensuring it remains a critical tool in protecting our digital lives. In summary, encryption and decryption are the backbone of secure communication today. They shield our everyday digital exchanges from unauthorized access and manipulation. They shield our everyday digital exchanges from unauthorized access and manipulation. Whether through simple or complex methods, encryption offers a reliable way to guard sensitive information. With cyber threats constantly changing, encryption must evolve too. It will remain a vital tool for safeguarding data, maintaining trust, and ensuring that our digital lives stay private and secure.




