
- What is an Intrusion Detection System (IDS)?
- Types of Intrusion Detection Systems
- Benefits of Intrusion Detection Systems
- Key Characteristics of Intrusion Detection Systems
- Challenges and Limitations of IDS
- How to Best Implement IDS
- Conclusion
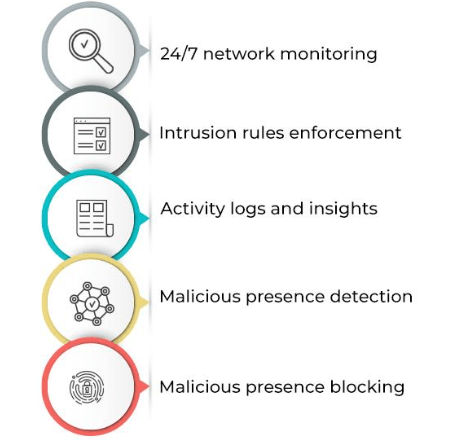
- Real-Time Monitoring: An IDS’s greatest strength lies in its real-time capability to monitor network traffic and system activities. This gives it access to anything suspiciously occurring, allowing it to respond promptly to probable threats.
- Alerts and Notifications: The IDS (Intrusion Detection Systems) generate alarms whenever they detect an intrusion. These alarms can be configured at various severity levels, enabling the organization to develop strategies for responding based on the nature of the threat. To enhance security and control access to critical resources, organizations often implement Network Access Control Lists.
- Packet Capture and Analysis: Most IDS solutions include packet capture, which forwards captured data packets to analyze malware content. This feature is quite useful in including the origin and nature of an attack in the incident response.
- Signature-Based Detection: Signature-based detection tests incoming traffic against a database of known attack signatures. As soon as it finds a match, the IDS can act, including blocking the traffic or alerting the administrators. This effectively detects known threats but may only work on something other than new or sophisticated attacks.
- Anomaly-Based Detection: Anomaly-based detection establishes a “normal” system behaviour baseline and then looks for a variance. This mode can detect new threats through abnormal patterns and activities.
- Log Analysis: Most IDS solutions offer log analysis, which scans the system logs for signs of malicious activity. This function helps detect system trends and weaknesses.
- SIEM Integration: Many contemporary IDS solutions can now be integrated into SIEM systems to strengthen monitoring capacity in general. This would involve central data collection, analysis, and reporting that helps enhance incident response capabilities.
- False Positives: The major issue with IDS (Intrusion Detection Systems) is false positives things deemed innocuous but wrongly identified as threats. High rates of false positives lead to alert fatigue, wherein security teams might ignore real threats. This is where a Security Operations Center (SOC) becomes crucial. The SOC is responsible for monitoring and responding to security incidents in real-time, often filtering out false positives and ensuring that genuine threats are addressed promptly.
- Resource-Intensive: IDS solutions are resource-intensive and require high processing power and large data storage for data analysis and logging. Organizations should ensure that all the required infrastructure is in place to support their IDS deployments.
- Evasion Techniques: Advanced attackers may use evasion techniques to evade IDS detection. These could include encryption or fragmentation, which would prevent traditional IDS from identifying the threats.
- Management Complexity: The administration of an IDS can be extremely sophisticated, especially in very large organizations with huge networks. It must be tuned and updated to maintain continuous effectiveness, which could demand full-time people and resources.
In the current era of mounting cyber attacks, organizations are persistently eyeing security solutions that adequately protect their sensitive data and systems. Under these circumstances, an Intrusion Detection System (IDS) has emerged as a vital component in most modern cybersecurity solutions. However, an Intrusion Prevention System (IPS) also plays a crucial role in actively blocking threats in real time. The following blog discusses what an IDS is, its types, prominent features, advantages, and implementation best practices, and how it works in tandem with an IPS to provide comprehensive network security.
What is an Intrusion Detection System (IDS)?
Intrusion detection systems can be hardware- or software-based applications that monitor network and host system activities for malicious activity or policy breaches. An IDS is a Cyber Security Training Courses measure that detects illegal or odd access within a network or host environment. When there is suspected threat identification, an IDS alerts security professionals so they can take proper measures in due time to reduce the risks involved.
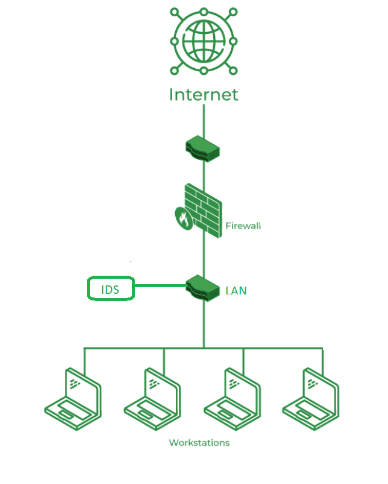
An IDS is crucial in the current world of sophisticated and complex cyber-attacks. In addition to malware and denial-of-service attacks, there are insider threats and data breaches. An IDS provides the oversight necessary to identify such threats early, enabling organizations to react promptly and minimize damage.
To Explore Intrusion Detection Systems in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Types of Intrusion Detection Systems
The major types of IDS are Network Intrusion Detection Systems and Host Intrusion Detection Systems, which focus on different deployment types and priorities. Both of these systems play a critical role in ensuring robust Network Security, as they help monitor and protect networks and hosts from unauthorized access and potential cyber threats.
1. Network Intrusion Detection System (NIDS)
It checks the networks for suspicious activities and scans incoming and outgoing data packets for patterns that may suggest an intrusion. NIDS is typically installed at strategic points of the network, such as the perimeter or critical servers. This type of IDS could detect a large number of attacks, such as DDoS attacks and network scanning.
2. Host-based Intrusion Detection System (HIDS)
HIDS focuses on monitoring devices or hosts in the network. It monitors system files, logs, and processes for unauthorized modifications or anomalies. HIDS is effective against insider threats as it provides more information and awareness of system activities. For example, it monitors file integrity so that even critical files cannot be altered without notice.
Benefits of Intrusion Detection Systems
Implementing an IDS benefits any organization trying to buttress its cyitscurity defences. Here are some major advantages:
1. Enhanced Threat Detection
An Intrusion Detection System (IDS) provides an improved layer of Cyber Security Training Courses by continually scanning network traffic and system activities for possible attacks. The real-time mechanism allows organizations to trace and respond to threats even before they escalate into major incidents.
2. Enhanced Incident Response
Real-time alerts and notifications enable security groups to respond rapidly to attacks that may have been launched. This rapid response mechanism limits the damage and, consequently, the time attackers can spend exploiting vulnerabilities.
3. Enhanced Visibility
IDS solutions increase network and system traffic visibility, which gives an organization a realization of its security posture. From this visibility, an organization determines weaknesses and areas that require improvements in its security policies and practices.
To Earn Your Intrusion Detection Systems Certification, Gain Insights From Leading Cyber Security Experts And Advance Your Career With ACTE’s Cyber Security Online Training Today!
4. Compliance with Regulatory Requirements
Almost all industries today have rules regarding data protection and cybersecurity. IDS solutions can aid an organization in complying with such regulatory requirements through essential monitoring and reporting capabilities.
5. Fewer Data Breaches
IDS systems reduce the chance of data breaches by helping detect intrusions at an early stage. This protection is useful in securing private data and retaining the clients’ trust.
6. Historical Data Analysis
IDS solutions often retain historical data, which can help analyze past events and prevailing trends. Such data promotes better security measures that organizations should take and prepare for probable dangers.
7. Lower Security Cost
Although the initial investment in an IDS is a big deal, long-term savings from preventing data breaches and minimizing incident response will make this a cheaper solution in the long run. The financial losses associated with an effective cyber attack are many and go beyond the costs of implementing an IDS.
8. Facilitates Incident Investigation
If an incident occurs, an IDS can be very useful for providing actual forensic data to support an investigation. It, therefore, aids in determining the type of attack, its origin, and vulnerabilities that might have been used.
Key Characteristics of Intrusion Detection Systems
A good IDS consists of many features that allow it to monitor potential threats. Some of these include;
Are You Considering Pursuing a Master’s Degree in Cybersecurity? Enroll in the Cyber Security Expert Masters Program Training Course Today!
Challenges and Limitations of IDS
IDS solutions offer many advantages but also come with challenges. Understanding these limitations is essential for organizations considering setting up an IDS system.
How to Best Implement IDS
For effective operation of an IDS, the organization should follow these best practices:
1. Clear Objectives
Before deploying an IDS (Intrusion Detection System), it’s essential to define clear security goals that align with your organization’s priorities. These objectives will help determine the type and configuration of the IDS needed. For instance, if one of the key concerns is preventing Malware Attacks, the IDS should be tailored to detect malicious payloads, suspicious activity, or unauthorized access associated with malware.
2. Identify the Right Type of IDS
Choose between Network IDS (NIDS) or Host IDS (HIDS) based on your network’s specific needs and threat landscape. NIDS monitors network traffic, while HIDS focuses on individual devices or endpoints. A combination of both can provide layered protection across your network. This decision should be guided by factors like network configuration, potential threats, and scalability.
3. Update Signatures and Policies Often
Regularly update your IDS with the latest attack signatures and detection policies. This ensures the system can detect newly emerging threats and vulnerabilities. Keeping your IDS current helps maintain its relevance in an ever-changing security environment. Frequent updates will also improve detection accuracy and reduce false positives.
4. Integration with Other Security Controls
Integrating the IDS with other security systems, such as firewalls, SIEM platforms, and antivirus solutions, enhances overall protection. Coordination between security measures allows for a more holistic approach to threat detection and response. This integration streamlines incident management and enables faster remediation. It also helps reduce gaps in security coverage.
5. Train Security Personnel
Invest in regular training for your security team to properly analyze and respond to IDS alerts. Training ensures personnel can differentiate between false alarms and legitimate threats. It also improves their ability to quickly and effectively mitigate any detected incidents. Well-trained staff can also identify patterns and respond proactively to potential attacks.
6. Continuously Monitor and Tune
Continuous monitoring is critical to ensuring your IDS is performing optimally. Regular tuning helps adapt the system to new attack techniques and reduces false alarms. By adjusting configurations, you can fine-tune detection capabilities and system performance. Ongoing monitoring also allows for timely responses to emerging threats and vulnerabilities.
Go Through These Cyber Security Interview Questions and Answers to Excel in Your Upcoming Interview.
Conclusion
The swiftly digitalized world makes cybersecurity strongly needed. Intrusion Detection Systems are important tools that help organizations protect themselves from a range of Cyber Security Training Courses. IDS provides real-time monitoring, alerts, and detailed insights into network activities, helping an organization respond properly to breaches. Although the advantages of a network intrusion detection system (NIDS) are convincing, its limitations still need to be improved compared to its benefits. With best practices and a proper, complete NIDS configuration, which includes all the security mechanisms, an organization will have a holistic security approach to protect its sensitive data and systems. In this aspect, an intrusion detection system is not only a precaution but also an investment to ensure that an organization remains long-term secure and resilient against ever-changing cyberspace risks.





