
- Banner grabbing: What is it?
- Why is grabbing necessary?
- Grabbing Attack Types
- Grabbing Features
- Main Ideas Behind Grabbing
- Grabbing Methods and Tool
- Conclusion
Grabbing involves pulling a remote system or service’s information from a server while connecting to the same over a network and retrieving its Cybersecurity Training Courses information. A banner usually refers to a text-based message provided by a server whenever a client connects to it in a service, generally exposing the software and version and sometimes the other system details. This method is used by both the security personnel and the attackers to gather valuable information about the configuration of a system. For example, a web server might expose that it is running Apache version 2.4.41 or an FTP server that shows a banner with its version number.
Enroll in ACTE’S Cyber Security Online Training if you want to become an expert in cyber security field and have a prosperous career.
Banner grabbing: What is it?
Hackers and protection groups use the approach of banner grabbing to find out information about a pc device related to a community and the offerings going for walks on its open ports. A banner is a textual content that a number server shows that consists of facts approximately the software program model and sort. This is presently going for walks on a device or server. The welcome shows we deliver hackers a head beginning whilst attacking the community through disclosing software program model numbers and different device info on community hosts.
Getting facts from a software program banner, which includes the call and model, is referred to as grabbing. Banner snatching may be completed through hackers both manually or mechanically with the use of an OSINT tool. One of the essential levels in each offensive and protective penetration checking out eventualities is grabbing a banner. A banner-grabbing assault desires to observe 3 steps. The attacker begins offevolved by deciding on the carrier that ought to be attacked. Then, she or he sends a request to the device or application that is the target. He or she examines the reaction from the software program or tool whilst it responds to determine which to take advantage of to make use of for the assault.
Why is grabbing necessary?
- Identifying Vulnerabilities: By amassing information, including software program variations and running machine types, protection experts can test for recognized vulnerabilities unique to those variations. This permits well-timed patching or hardening to mitigate risks.
- Assessing Security Posture: Grabbing banners enables groups to comprehend what offerings are seen and probably handy to outsiders. This visibility test allows directors to make sure the most important offerings are exposed to the internet.
- Incident Response and Forensics: In the event of a Web Security incident, Grabbing a banner can help profile the structures affected, facilitating quicker diagnosis and response.
- Compliance and Auditing: Some compliance requirements and policies require everyday tests of community protection. Grabbing banners is a powerful way to report and confirm the safety posture of structures in accordance with those requirements.
- Threat Intelligence: For moral hacking and penetration testing, grabbing offers a manner to apprehend the goal surroundings earlier than deeper analysis. It enables moral hackers and analysts to anticipate the sorts of assaults the structures may face, guiding similar testing.
Grabbing Attack Types
- Active Grabbing Banner: A person sends a packet to a far-off host on this Grabbing banner and waits for a response. The facts are, in the end, analyzed via way of means of him or her. A Transmission Control Resolution Protocol or similar connection have to be set up between a nearby laptop and a faraway machine so as for the manner to work. The reality that the hyperlink logs into the remote system makes it lively. As a result, state-of-the-art intrusion detection systems (IDSs) or different answers that especially maintain a watch out for unauthorized connections often choose up on a lively banner-snatching attempt.
- Passive Grabbing banner: Users can reap equal statistics even by warding off publicity via way of means of passively taking pictures of banners. Different intermediate applications and systems can act as gateways in attacks that appoint the method to save you from connecting immediately to the goal system. In this manner, the relationship is hidden even as the attacker obtains the desired facts. Passive banner-snatching assaults often contain networks, tools, or offerings supplied via way of means of 1/3 parties, together with site visitors’ sniffers or seek engines.
- Service Identification:
Grabbing banner-famous information about offerings going for walks on open ports, such as HTTP, FTP, SSH, and others, by extracting banner facts from every service. This facilitates discovering what software programs and offerings are active in the community.
- Operating System Detection
Banners frequently include facts about the working device and Cybersecurity Training Courses model, which is beneficial for community profiling and assessing compatibility or ability vulnerabilities.
- Software Version Detection
Banners regularly encompass the precise model of the software program going for walks (e.g., Apache 2.4.49), bearing in mind focused vulnerability scanning primarily based totally on regarded troubles with unique variations.
- Network Profiling
Through the Grabbing banner, safety experts can create an in-depth profile of the community infrastructure, including devices, applications, and configurations, that’s crucial for determining susceptible factors in a community.
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Today!
- Passive and Active Reconnaissance
Grabbing banners may be done both passively (gazing community traffic) and actively (sending requests to offerings), giving safety groups flexibility in how they collect facts without being detected.
- Automation Friendly
Equipment like Nmap, Netcat, and Telnet may be computerized, making it green to experiment with more than one IP and ports throughout huge Network Topology .
- Support for Penetration Testing
Grabbing banners is frequently one of the first steps in penetration testing because it affords a starting point for mapping ability assault vectors.
- Efficiency in Vulnerability Management
Because it quickly has famous variations and configurations, the Grabbing banner streamlines vulnerability control by stating which structures might also need updates or patches.
- Grabbing banner Telnet:Hackers and pen-testers can interface with remote offerings to grab the use of this conventional cross-platform client. To locate pertinent data, pen-testers and attackers can telnet to hosts using the usual telnet port (TCP port 23). Other extensively used ports, such as SMTP, HTTP, and POP3, are prone to assault through telnet.
- What web:This system identifies websites and assists hackers and protection professionals in grabbing the net program banner by revealing server data, including the IP address, version, Demilitarized Zone , and active running system.
- Nmap Banner Grab:This easy Nmap banner grabber connects to an open TCP port and prints out info sent using the listening provider within seconds.
- Dmitry: The Deepmagic Information Gathering Tool can amass the most host data. Dmitry offers attackers access to a distant host’s entire records set, along with open ports, subdomain mapping, DNS enumeration, and more.
- Wget Banner Grab:The banner-grabbing device can direct visitors to the banner of remote or close by servers. Wget makes use of a trustworthy script to suppress the predicted output and print the HTTP server headers.
Are you curious to know more about Banner Grabbing? Take advantage of our comprehensive online Cyber Security Course !
Grabbing Features
Main Ideas Behind Grabbing
This is the response that a server sends back when a client initiates a connection. Many times, it reveals the service or protocol the server is running (such as HTTP, FTP, SSH), the version of the software, and sometimes even what OS it is running. Banners might come as a text message or any other form of data during the establishment of a connection to the service. Protocols are several protocols which could display banners; HTTP Servers using the Web Application Security often tend to give information regarding the server software used and its version when a query is sent. File Transfer Protocol servers usually display a welcome message, which comes along with versioning information. Shell servers may show the software and version details within their banner. A simple Mail Transfer Protocol might display the identity of the mail server.
Get interview-ready with our collection of Cybersecurity Interview Questions and Answers Questions.
Grabbing Methods and Tool
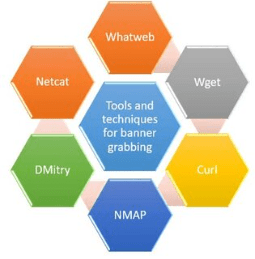
Hackers grab banners using several methods. They use this gear to hook up with a goal net server, after which they ship HTTP requests. During the process, the attacker gets a reaction with information about the provider being utilized by the host.
Conclusion
We hope this weblog is insightful, as one of the maximum famous strategies applied throughout the reconnaissance level of any penetration check or real assault situation is banner snatching. Grabbing banners is a beneficial approach in cybersecurity that includes retrieving metadata from community offerings to gain insights into gadget configurations, software program versions, and ability vulnerabilities. Often hired with the aid of safety professionals, Cyber Security Training lets them evaluate a gadget’s safety posture and become aware of weaknesses proactively. However, it’s also utilized by malicious actors for reconnaissance, making it important for companies to take preventive measures.





