
- How to Define Application Security
- The Value of Secure Applications
- Application Security Types
- How Can Secure Applications Be Increased ?
- Technologies and Tools for web Application Security
- Secure Applications Difficulties
- Application Security’s Future
- Conclusion
Application security is the approach and best practice designed to protect applications against security risks at every stage of their lifecycle. Software has increasingly become the lifeblood of enterprises; thus, there must be comprehensive security that shields against threats such as SQL injection and cross-site scripting. Key elements include threat modelling, secure coding practices, security testing, and effective access control to protect sensitive data and ensure compliance with relevant standards. Prioritizing Cybersecurity Training Courses will protect the organization’s data and systems and win its users’ trust. The outcome will be that the brand reputation will improve in such an ever-increasing digital landscape fraught with risk.
Sign up for ACTE Cyber Security Online Training and get a head start in your career cyber security.
How to Define web-Application Security
The process of defending applications from outside dangers, including illegal access, breaches of information, and other cyberattacks, is known as application security. It covers a range of methods and techniques to guarantee the privacy, availability, and integrity of software data and services. Protecting websites from attacks that aim to exploit flaws in web-based systems is the focus of application security. Web application safety is a subset of overall Secure Applications since it addresses the unique concerns related to safeguarding web-based applications.
Executing timely updates and patches to safeguard against known vulnerabilities is important. Educating users to understand possible risks and best practices further helps maintain a Internet Protocol Address. With IoT security, people and organizations will avoid risks associated with this highly interconnected world and guarantee the security of the connected data and devices.
The Value of Secure Applications
- Protect Sensitive Data:Applications frequently handle and store sensitive data, including financial and personal information. It is imperative that this data be kept secure to preserve user confidence and avoid trouble with the law.
- Prevent Downtime: Applications may experience outages due to cyberattacks, which could interfere with business operations and result in losses. Application security helps protect against these threats to keep your application running.
- Respect laws: Numerous sectors have implemented certain security laws to safeguard sensitive data. Your company may stay in compliance with these rules by implementing strong application security mechanisms.
- Preserve the reputation:A security breach can seriously harm a company’s reputation, resulting in a loss of clients and income. Investing in Secure Applications shows you are committed to protecting your users’ data and fostering trust and loyalty.
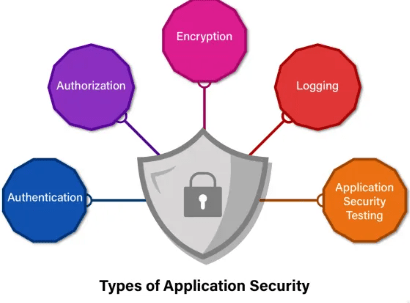
- Authorization and Authentication:
Thanks to this protection, only authorized users can access particular application resources. While authorization establishes the degree of access allowed to authenticated users, authentication confirms individuals’ identities.
- Encryption of Data:
Encryption transforms data into an unintelligible format to prevent unwanted access. Data encryption is very useful for protecting private data, including financial information and passwords.
- Validation of Input:
To prevent malicious input from jeopardizing the program’s security, input validation verifies the data that users enter. You may stop attacks such as SQL injection and Cross-Site Scripting (XSS) by verifying user input.
- Intrusion Detection Systems and Firewalls:
Intrusion detection systems and firewalls monitor Network Security Keys and stop questionable activities. These safety devices can assist in detecting attempted breaches and shielding programs from outside dangers.
- Safe Coding Techniques:
Secure coding methods include creating software that is immune to security flaws. By adhering to secure coding rules, developers can reduce the possibility of security vulnerabilities in their applications.
- Testing for Security:
Security testing includes finding and fixing flaws in programs using methods such as penetration testing, scanning for vulnerabilities, and code review.
- Encrypt sensitive data:
Using encryption techniques to safeguard sensitive information sent between users and the program. Additionally, think about encrypting the application’s sensitive data.
- Verify User Input:
To avoid security flaws like SQL injection and XSS attacks, ensure every user input is thoroughly verified and cleaned.
- Track and Examine Application Activity:
To identify and address possible security issues, examine application logs regularly and use real-time monitoring tools.
- Teach Users and Developers:
Your development team should receive instructions on secure coding techniques and security awareness for Cybersecurity Training Courses . Users should also be taught security standard practices like securing passwords and spotting phishing efforts.
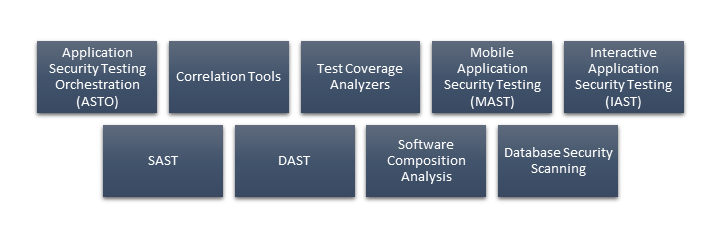
- Static Application Security Testing (SAST):To find security flaws, SAST tools examine the source code, byte code, or binary code of your application. You can identify problems early in the creation process using these tools.
- Dynamic Application Security Testing (DAST):Application security flaws are found using Dynamic Application Security Testing (DAST) technologies, which examine running programs. They replicate actual attacks, which helps spot problems that static analysis could miss.
- Interactive Application Security Testing (IAST):Interactive Application Security Testing (IAST) systems, which include aspects of SAST and DAST, provide real-time vulnerability management detection and repair during the development and testing stages.
- Web application firewalls: Web application Packet Filtering Firewall, often known as WAFs, monitor and filter incoming HTTP traffic to safeguard web applications. They can aid in thwarting common web application assaults like XSS and SQL injection.
- Security Information and Event Management (SIEM):SIEM systems help you identify and address security events more efficiently by combining and analyzing log data from several sources.
- Penetration Testing Tools:To find vulnerabilities and evaluate your security posture, penetration testing tools mimic cyberattacks on your application. These resources can assist you in identifying problems that automated testing methods might need to be detected.
- Resource Limitations:Many firms may not have the financial or human resources needed to implement thorough application security procedures.
- Lack of Awareness: Some firms might not prioritize application Application Security their safety strategy or need to comprehend its significance.
- Complexity:Application complexity increases the potential surfaces for attack and security flaws. Staying on top of these changing dangers might take a lot of work.
- Third-Party Dependencies:Applications frequently use third-party libraries or components, which, if improperly screened and maintained, might introduce security flaws.
- Fast Development Cycles:The necessity for quick application development may force security measures to be shortened, which could introduce vulnerabilities into the program.
- Security solutions that leverage these technologies can automate tasks related to vulnerability discovery and repair, allowing organizations to react more rapidly to security crises.
- As businesses realize they need to take an active approach to application security, integrating the implementation of safety procedures into the DevOps lifecycle, or DevSecOps, is becoming increasingly popular.
- As serverless computing becomes more popular, new security issues and approaches to protecting these extremely dynamic systems will surface.
- As privacy-related rules are implemented and worries about data privacy rise, application safety precautions will need to change to keep sensitive data safe.
Enroll in ACTE’S Cyber Security Online Training if you want to become an expert in cyber security field and have a prosperous career.
Application Security Types
Want to Take the Lead in Cyber Security ? Enroll in ACTE’s Cybersecurity Expert Masters Program Training Course Program to Begin Your Adventure Now.
How Can Secure Applications Be Increased?
Develop a Security First Mentality From the start of an application development process, give security a top priority. This entails using secure coding techniques, conducting frequent security audits, and keeping abreast of emerging security risks and industry best practices. Put in place robust authorization and authentication procedures. Use Role-Based Access Control (RBAC) and Multi-factor authentication (MFA) to improve the security of your application’s permission and authentication procedures. Encrypt Sensitive Data To safeguard sensitive information sent between users and the program, utilize Cipher Encryption. Additionally, think about encrypting the application’s sensitive data. Verify User Input To avoid security flaws like MySQL injection and XSS attacks, ensure every user input is thoroughly verified and cleaned. Track and Examine Application Activity To identify and address possible security issues, examine application logs regularly and use real-time monitoring tools. Teach Users and Developers: Your development team should receive instruction on secure coding techniques and application security awareness. Users should also be taught security standard practices like securing passwords and spotting phishing efforts. Update your dependencies and software. Update the dependencies and software in your application regularly to fix known security flaws.
Technologies and Tools for Web Application Security
Application Security Difficulties
Organizations still need help implementing efficient application security measures, even with the availability of technologies and best practices. Among these difficulties are the following:
Get interview-ready with our collection of Cybersecurity Interview Questions and Answers Questions.
Application Security’s Future
Conclusion
application security is an integral part of the modern software development process that cannot be ignored. Organizations must proactively protect their applications from these ever-evolving cyber threats. This can be achieved by incorporating security practices at each phase of the development lifecycle-from design to deployment and even post-deployment. However, by prioritizing secure coding, testing, and subsequent continuous monitoring, businesses can risk-mitigate, protect data, and maintain their user’s trust. Investing in the Cybersecurity Training is all about improving business operational resilience; however, it also creates more chances for long-term prosperity in the increasingly digital global landscape.





